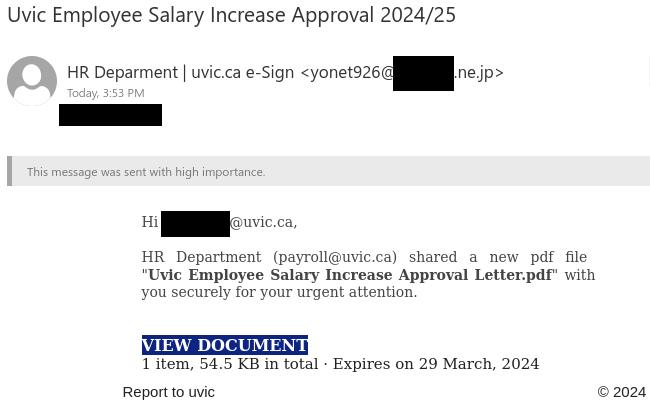
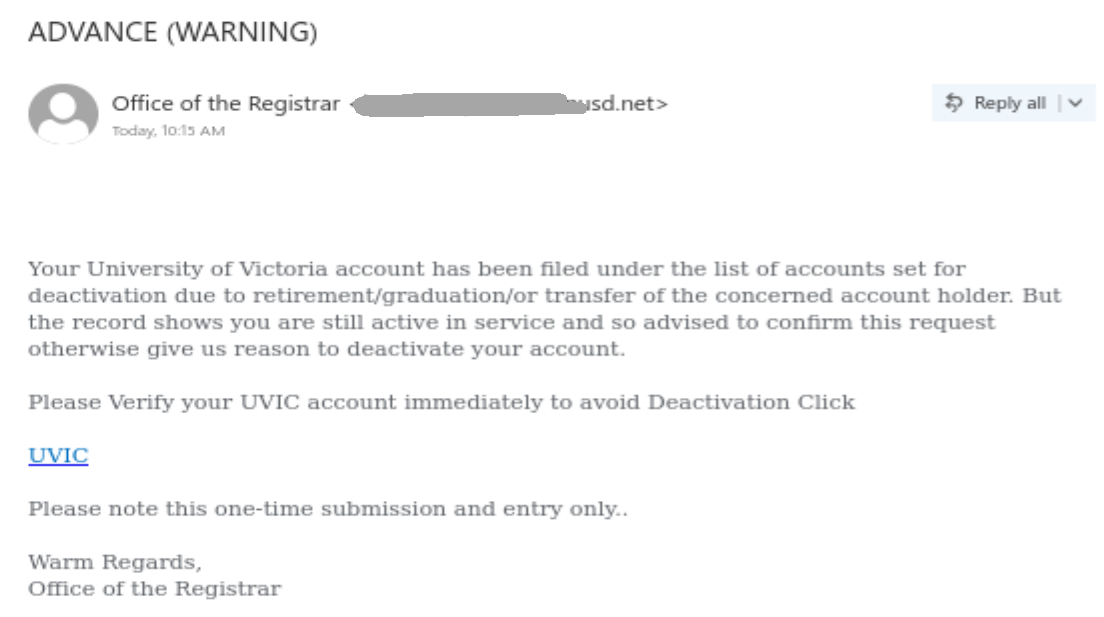
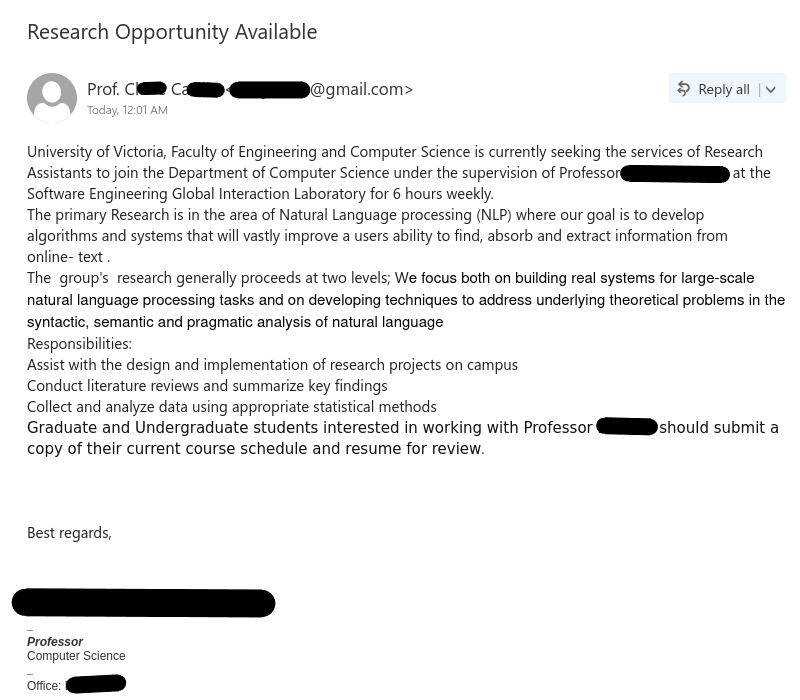
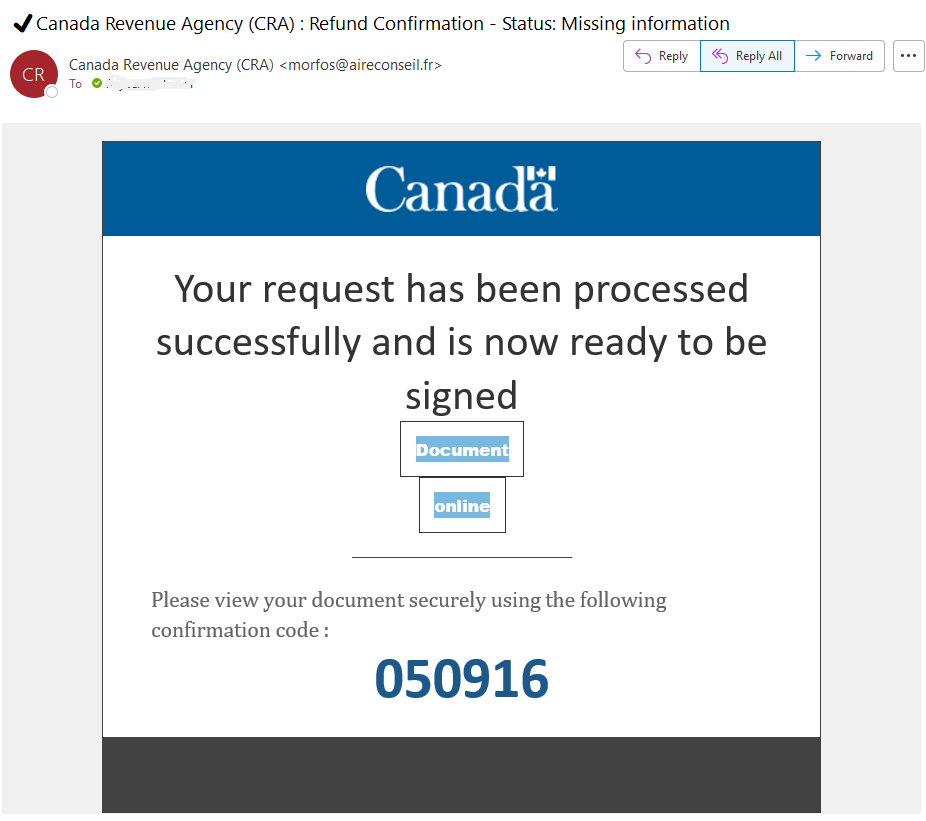
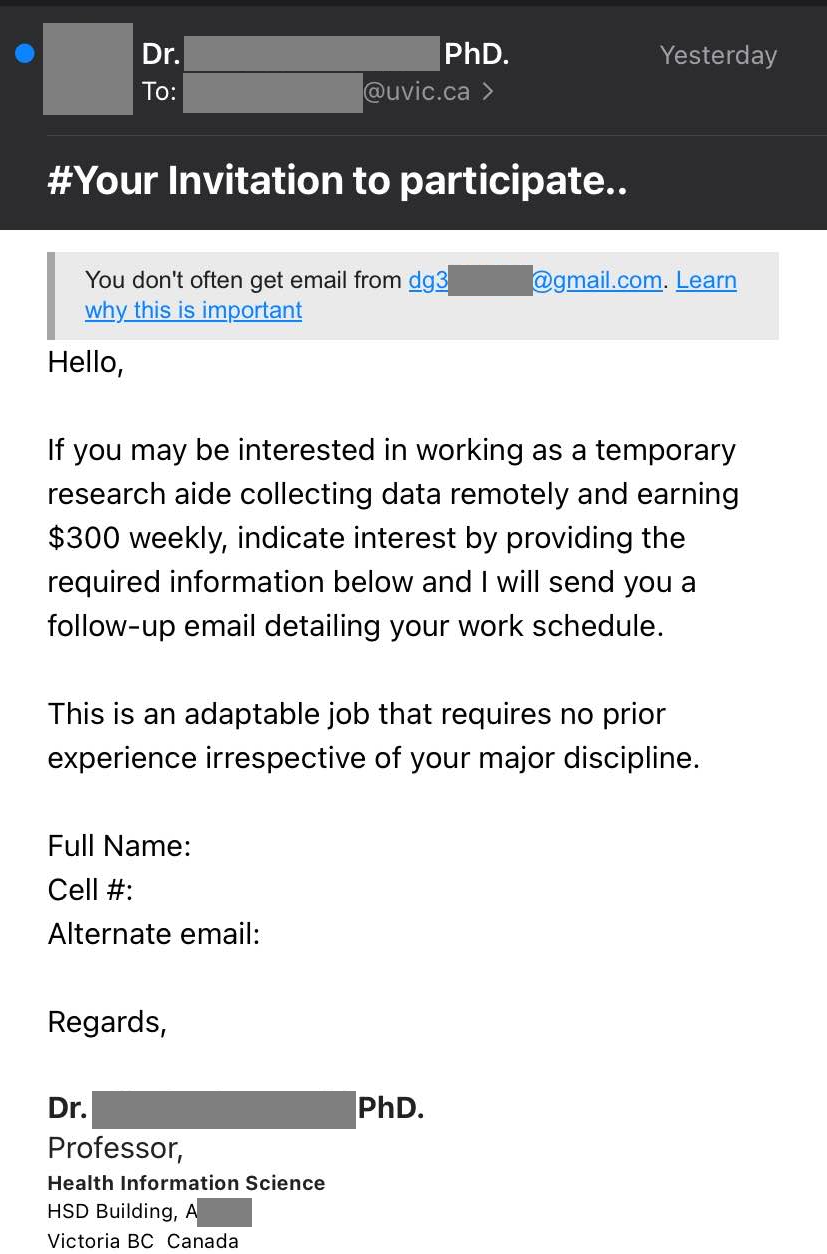
Job scams impersonating UNESCO and other UN agencies are something we see on a regular basis. By offering a generous salary for only a few hours a week of simple remote work tasks, these unscrupulous scammers prey on students looking for extra money to cover the cost of tuition, rent and other necessities. The red flags in the email message are the usual ones:
- The email did not come from a UNESCO or UN email address, nor did it come from a UVic sender.
- The salary is too good to be true for part-time remote work.
- The email contains grammatical errors and awkward wording.
- You are told to send replies to an Outlook.com email address. If a job offer asks you to contact an address from a free email provider, there is a very high chance that the offer is a scam.
- You are asked to reply from your personal email address. Scammers do this to shift the conversation away from UVic’s email security controls and avoid detection.
If you contacted the scammer, reach out to the Computer Help Desk or your department’s IT support person immediately for assistance. If you opened the attachment, update your computer’s antivirus and perform a full scan as a precaution.
If there is no job interview before you’re accepted into the position, or you never get to meet your supposed employer (either in person or by video call) before you start working, that is a very strong sign of a job scam. If any of the following occur, do not proceed!
- You are told to share your UVic or other login credentials–never share those with anyone!
- You are asked to purchase gift cards, then send photographs of them with the PIN revealed. Don’t do this even if you were given a cheque beforehand–that cheque will probably bounce and you’ll lose the money used to purchase the cards.
- You are given a cheque to deposit in your account and told to send part of the amount to someone else. This may be a cheque overpayment scam (the cheque you received would eventually bounce, meaning the money you sent would come from your own funds), or the scammer may be trying to use you as an unwitting money mule to launder money.
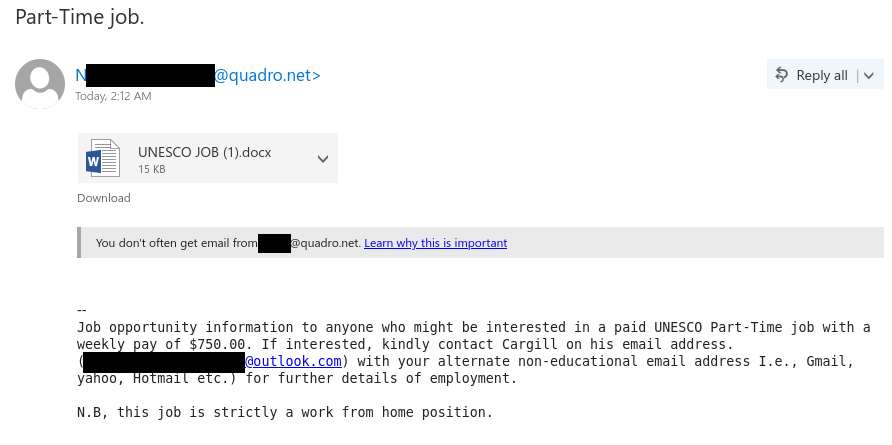
From: N****** <[redacted]@quadro.net>
Subject: Part-Time job.
Attachment: [Word document icon] UNESCO JOB (1).docxYou don’t often get email from [redacted]@quadro.net. Learn why this is important.
—
Job opportunity information to anyone who might be interested in a paid UNESCO Part-Time job with a weekly pay of $750.00. If interested, kindly contact Cargill on his email address. ([redacted]@outlook.com) with your alternate non-educational email address I.e., Gmail, yahoo, Hotmail etc.) for further details of employment.N.B, this job is strictly a work from home position.