If you get an email instructing you to click a link to update your account or password, and it came from a free email provider like Gmail or Outlook.com, you can be pretty certain it’s a phish.

If you get an email instructing you to click a link to update your account or password, and it came from a free email provider like Gmail or Outlook.com, you can be pretty certain it’s a phish.

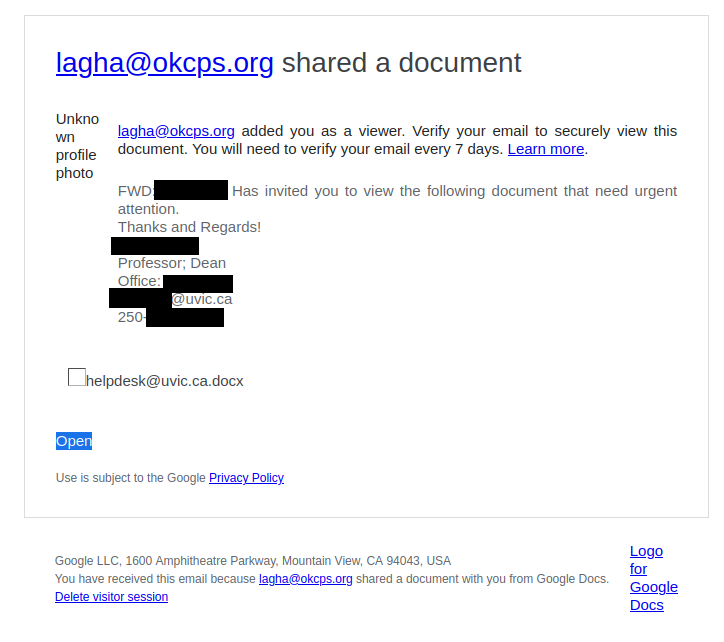
Phishers often abuse compromised Google accounts from other organizations to send file sharing phishes like the one below. Notice how this document claims to be associated with helpdesk@uvic.ca, so the fact that the sender is not from UVic is a major red flag.
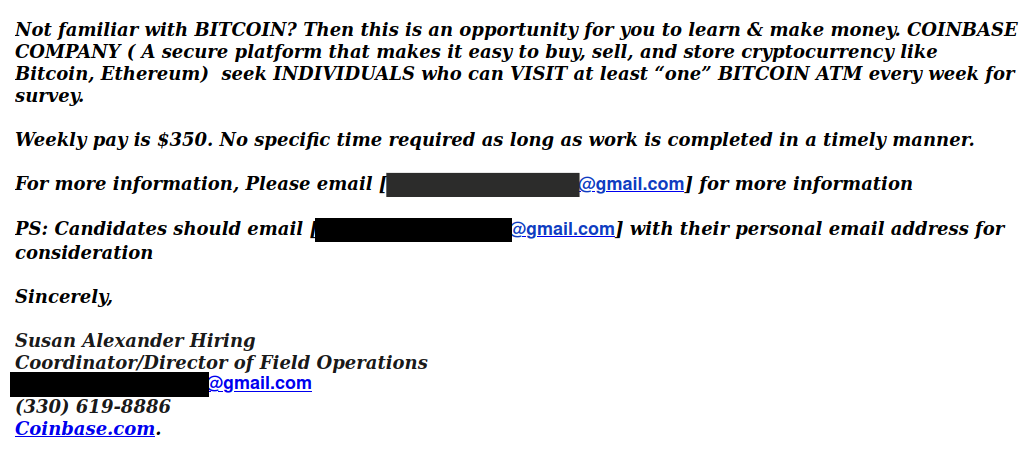
This Bitcoin scam email was sent from a compromised UVic account, and one red flag not included in the screenshot below would have been the mismatch between the name in the signature block and the name of the account used to send the email.
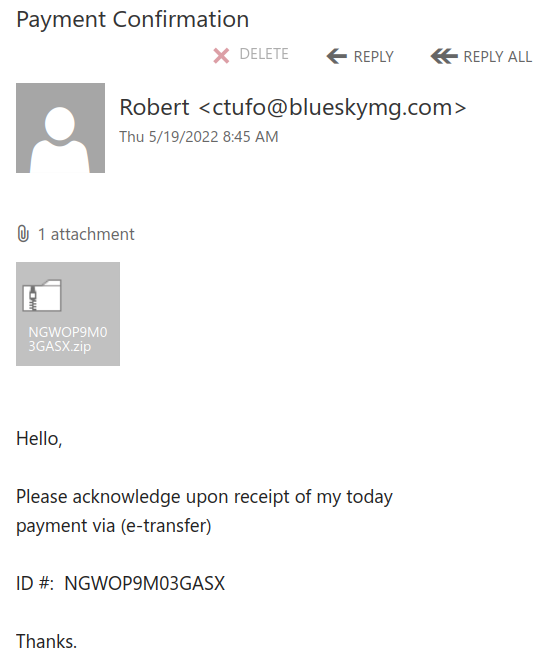
An email with a subject “payment confirmation” is circulating today. To avoid detection the malicious actors made a huge executable file (containing the malicious code) then put that executable file into a .iso file and then zipped that .iso.
The zip file is about 2Mb in size and attached in the email.
Please do not open these attachments! If in doubt, first ask your Desktop support person or the Helpdesk.
In the screenshot below it is shown the sender is an external one. As is usual for such campaigns they used many different sender addresses.
This phish is circulating since the early morning today. See a screenshot below.
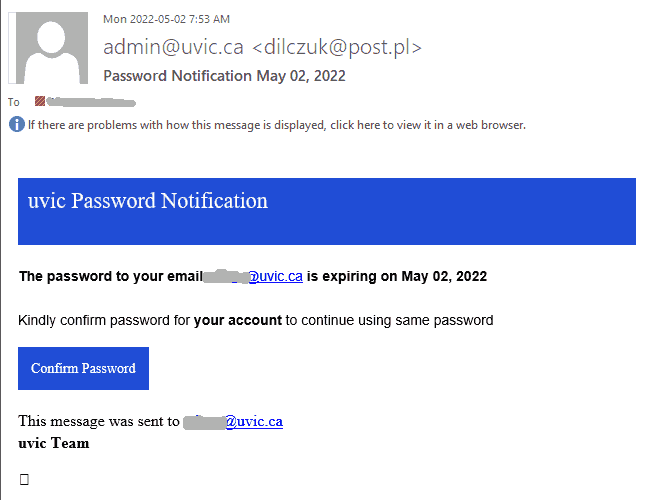
As usual you are expected to act fast. Your password expires in 3 hours, and if you don’t act your account will be deleted in 4 hours?!? Isn’t that ridiculous?
The sender pretends to be a “System administrator connected to Microsoft Exchange”. They are clearly using some external address somewhere in Germany. They put themselves as a recipient and all other recipients received bcc: copies.

——end of the first screenshot ——
The link is external of course, and points to a fake login page that’s created to steal your credentials.
Please never click on suspicious links, don’t be curious. Sometimes these pages may contain malware to infect your machine instantly. Our experts open these in a dedicated isolated environment.
This particular fake page looks like shown below:

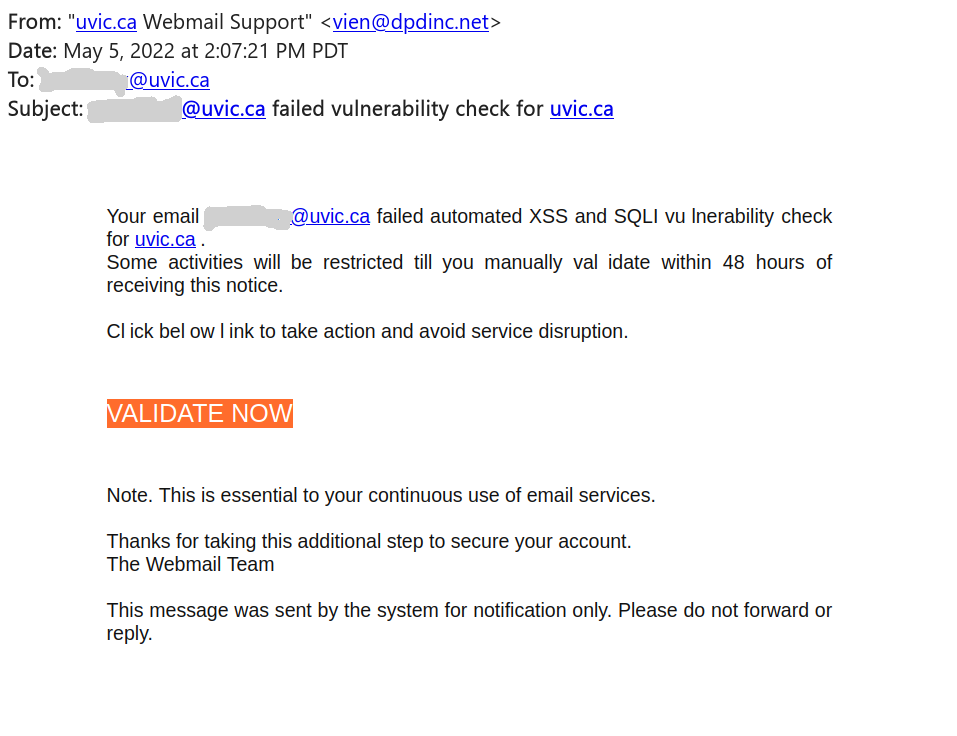
This phish is circulating around today. See a screenshot below.
Of course something must be wrong and of course you have to act fast. The sender pretends to be a “uvic webmail support” but clearly is using some external address. Note how the malicious actor deliberately put space in some words in the message body in order to evade automatic detection of phish, e.g. in the words “vulnerability”, “click”, “below”, “validate”
The link is external of course, and points to a fake roundcube mail page that’s created to steal your credentials.
Please never click on suspicious links, don’t be curious. Sometimes these pages may contain malware to infect your machine instantly. Our experts open these in a dedicated isolated environment.
Same old tactics – scary the user there is something wrong to deal with fast, navigate to a fake page, steal your UVic credentials.
A screenshot of the phish message is shown below. The link in fact points to an external site (that can be seen when hovering with the cursor above the link, without clicking).
A screenshot of the fake page is shown below
Please never click on suspicious links, don’t be curious. Sometimes these pages may contain malware to infect your machine instantly. Our experts open these in a dedicated isolated environment.
