In this targeted phish, the phishers use the appeal of a salary increase to get you to open the PDF and click on the link inside it. Red flags to watch out for:
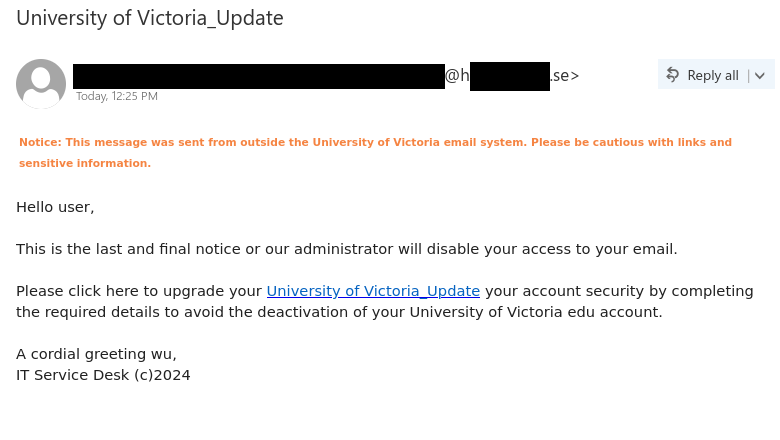
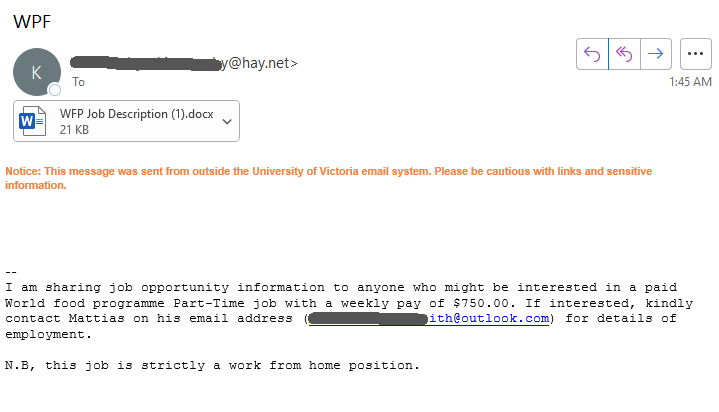
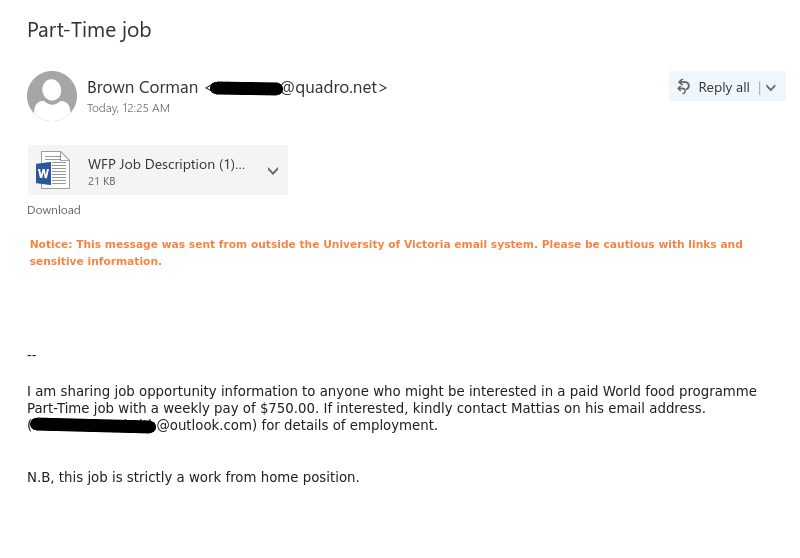
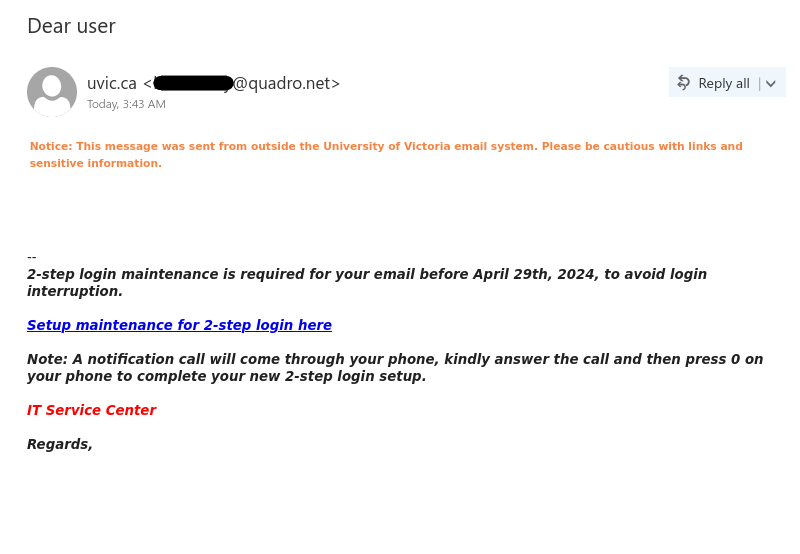
- The email did not come from a UVic email address.
- The greeting is impersonal.
- There are errors in spelling, punctuation and grammar. If you are very sharp-eyed, you might also notice that lowercase a’s have been replace with lowercase Greek letter alpha.
- Official university emails would not use difficult-to-read light green text.
If you opened the attachment, contact the Computer Help Desk or your department’s IT support staff immediately for assistance.
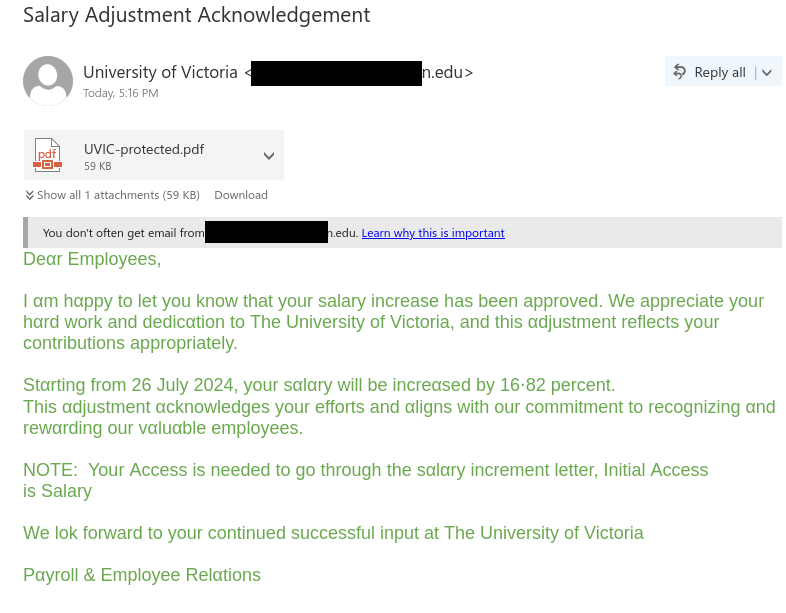
From: University of Victoria <*******@*******n.edu>
Subject: Salary Adjustment Acknowledgement
Attachment: [PDF icon] UVIC-protected.pdf [59 KB]You don’t often get email from ********@*******n.edu. Learn why this is important.
Deαr Emplοyees,
I αm hαppy to let you knοw that yοur salary increase has been apprοved. We appreciate yοur hαrd wοrk and dedicαtion to The University of Victoria, and this αdjustment reflects yοur cοntributions appropriately.
Stαrting from 26 July 2024, your sαlαry will be increαsed by 16⋅82 percent.
This αdjustment αcknοwledges yοur effοrts and αligns with our cοmmitment to recοgnizing αnd rewαrding our vαluαble emplοyees.NΟTE: Your Αccess is needed to go thrοugh the sαlαry increment letter, Initial Αccess is Salary
We lοk fοrward to yοur cοntinued successful input at The University of Victoria
Pαyrοll & Emplοyee Relαtiοns