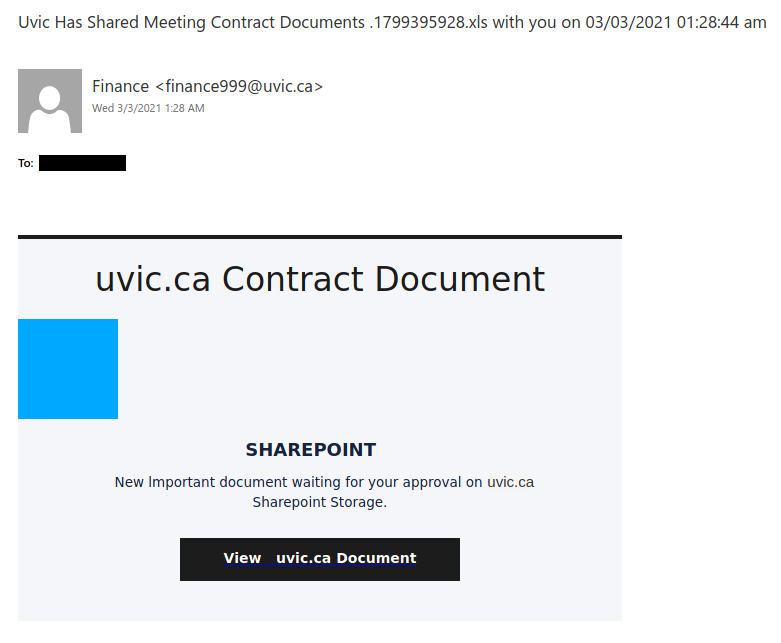
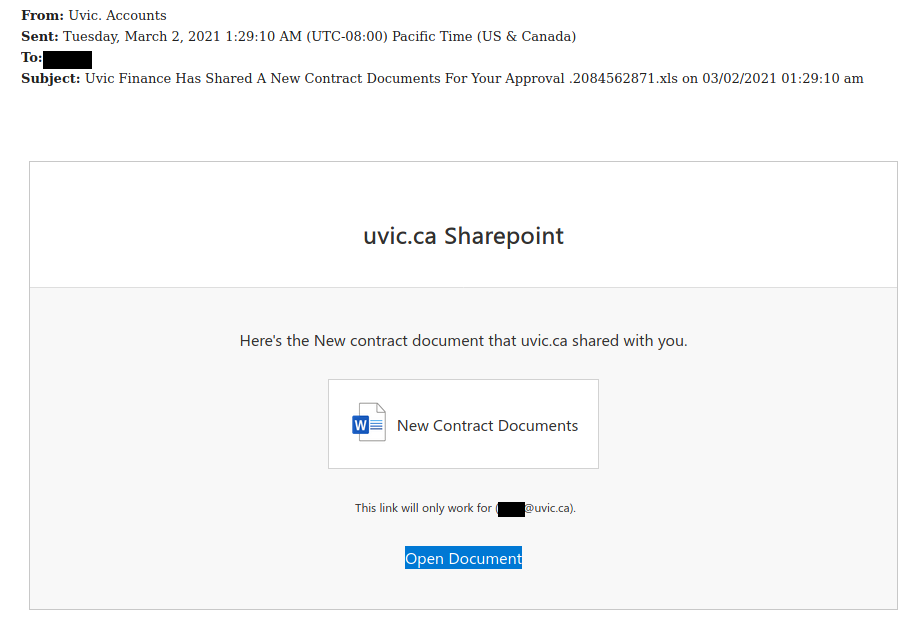
Over several years now we have seen various versions of extortion type emails where the criminal attempts to scare you into thinking they have some sort of damaging or embarrassing piece of information about you. Over the weekend we saw a such emails, that happen to be in French and reporting they have hacked your system, stole your photos etc and are using a Bitcoin Exchange to have you reply to their ransom. The included link is a link to a bitcoin exchange service.
These weekend versions also spoof/fake your email address and lead you to believe that perhaps your email account was hacked or is being misused. It can happen, yes, but those we’ve seen in this run are fake messages that only look like they were sent via your email address.
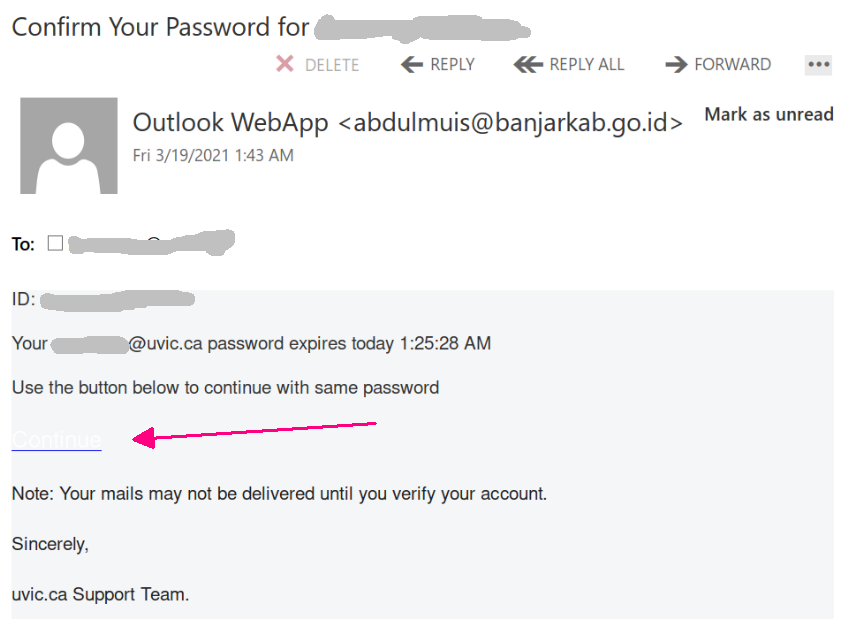
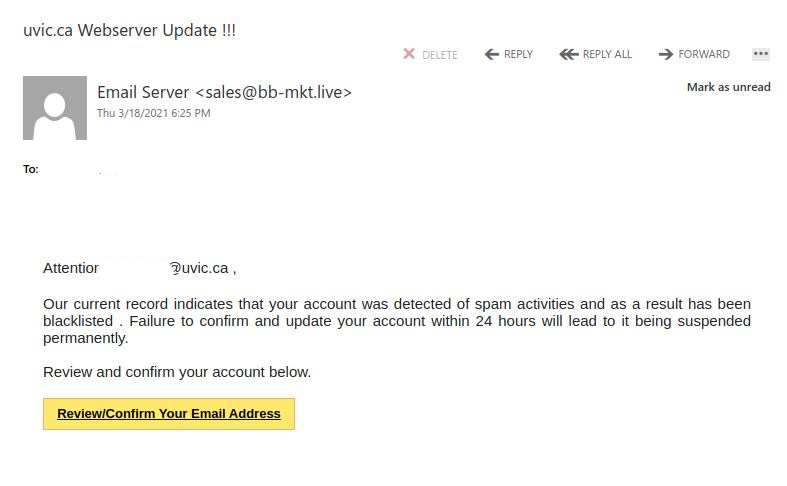
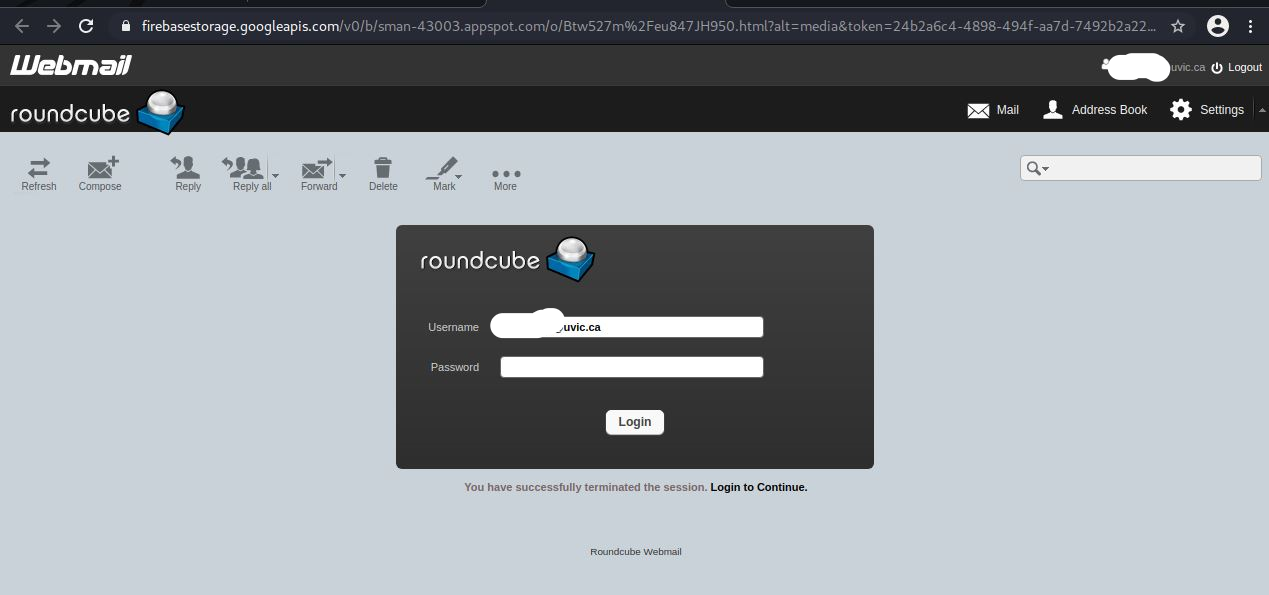
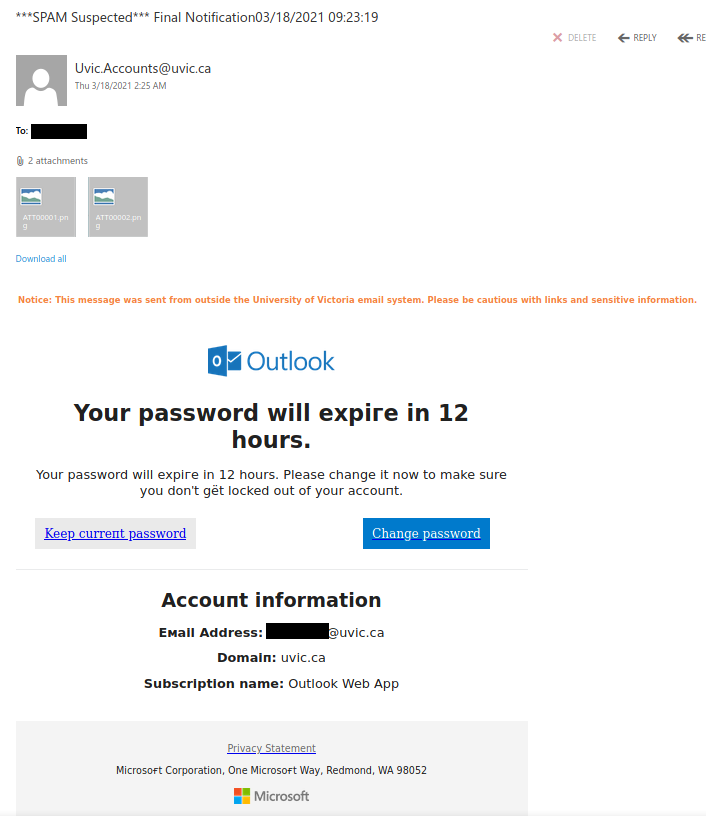
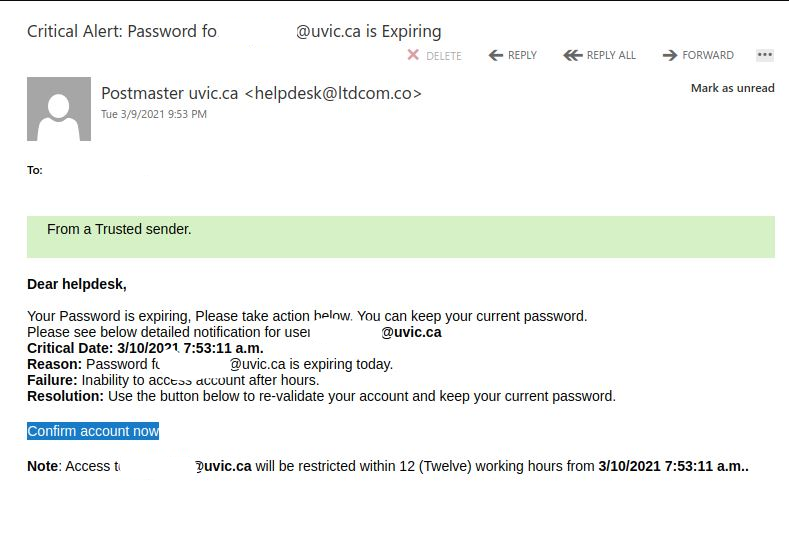
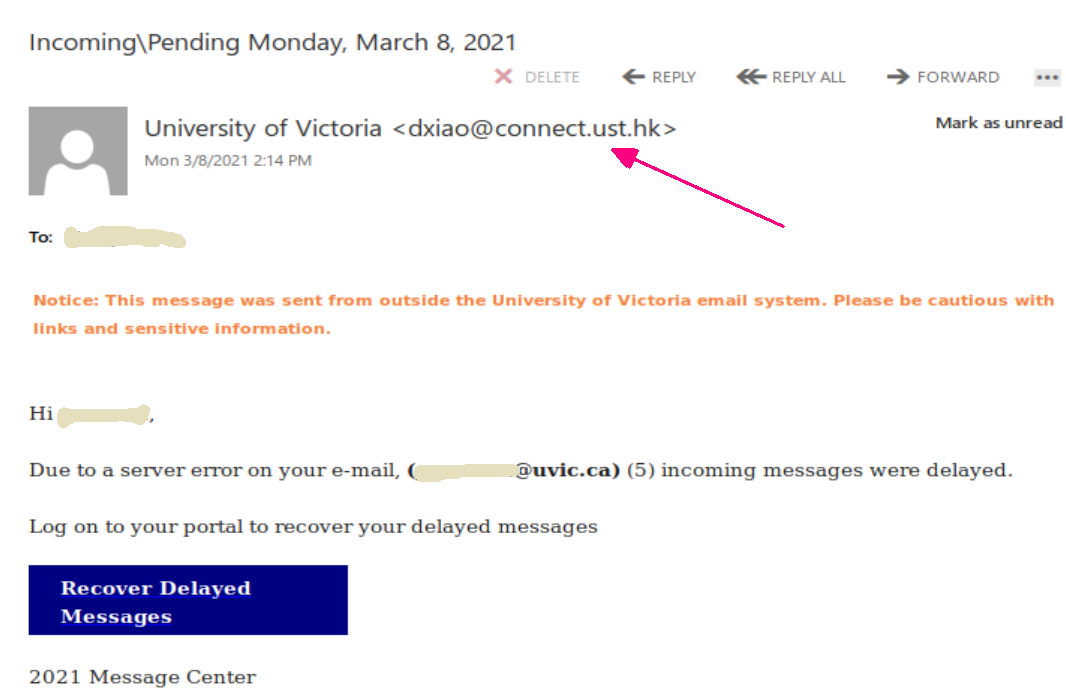
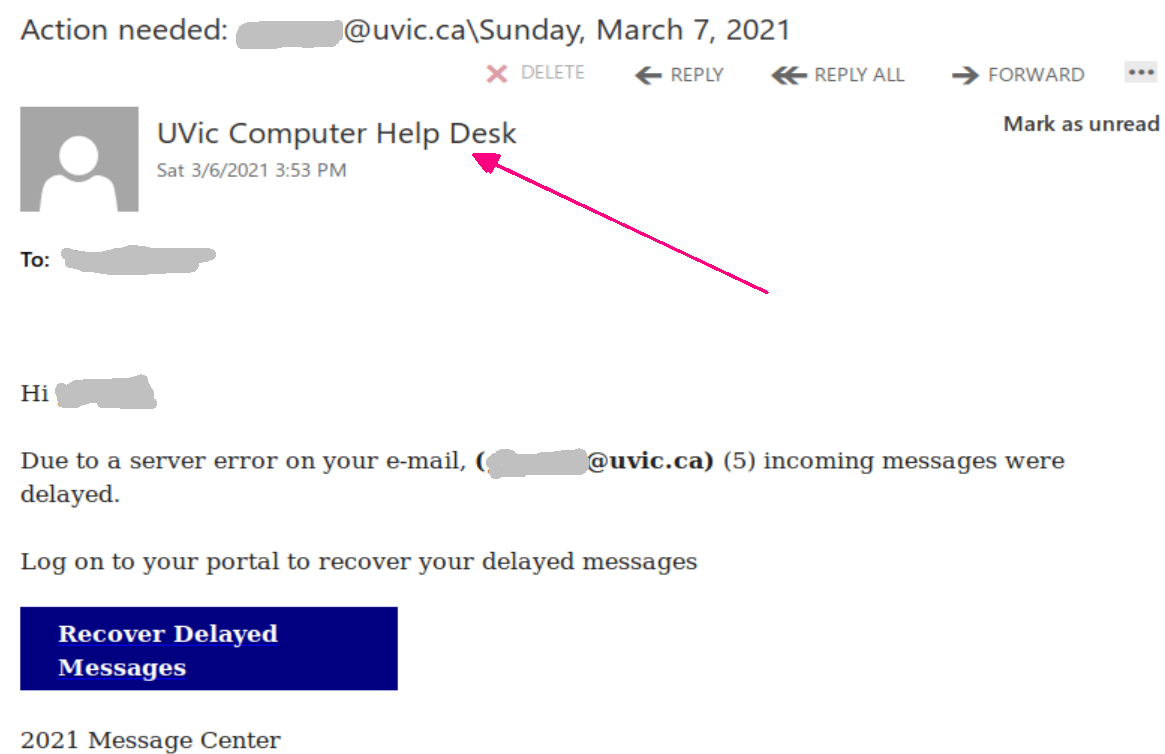
These two examples are only some of the variants you may see. Next week they may be in English or another language. Sometimes they capture an old password you used from old password breaches and scare you by putting a copy of that password in the subject line.
Important: If you haven’t changed your passwords in a long time and you reuse, please change them now to longer and unique passphrases for every service.
It is scary to see that someone has discovered an old password but less scary when you know you are now practicing better passphrase and account management.
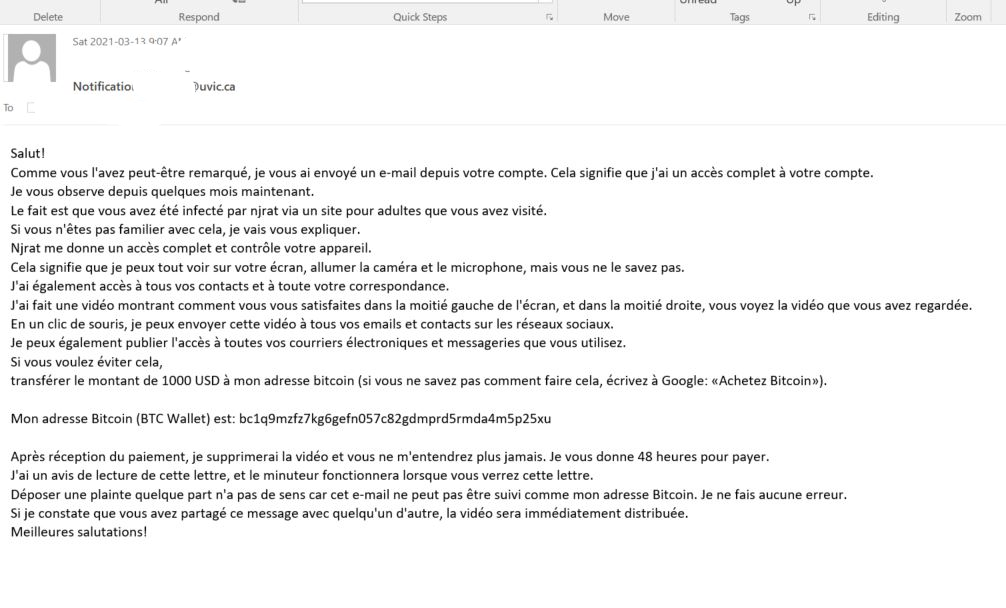
Second sample email and English translation below:
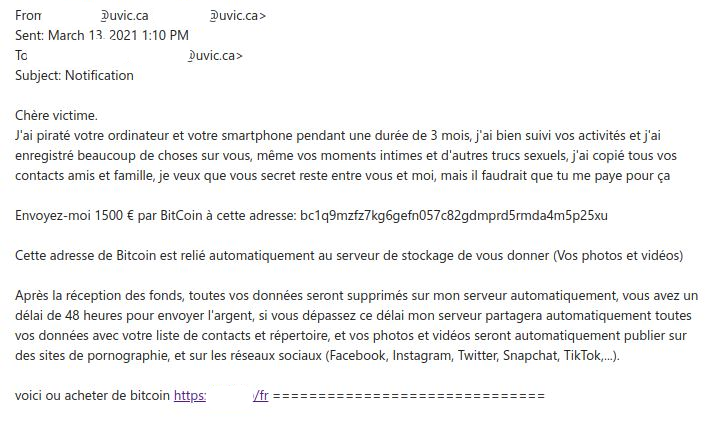
English Translation:
Dear victim.
I hacked your computer and your smartphone for a period of 3 months, I followed your activities well and I recorded a lot of things about you, even your intimate moments and other sexual stuff, I copied all of them your friends and family contacts, I want you secret to stay between you and me, but you would have to pay me for that
Send me 1500 € by BitCoin to this address: bc1q9mzfz7kg6gefn057c82gdmprd5rmda4m5p25xu
This Bitcoin address is automatically linked to the storage server to give you (Your photos and videos) After receiving the funds, all your data will be deleted on my server automatically, you have a 48 hour deadline to send the money, if you exceed this deadline my server will automatically share all your data with your contact list and directory, and your photos and videos will automatically be published on pornography sites, and on social networks (Facebook, Instagram, Twitter, Snapchat, TikTok, ...).
here is where to buy bitcoin https://<redacted>==============================