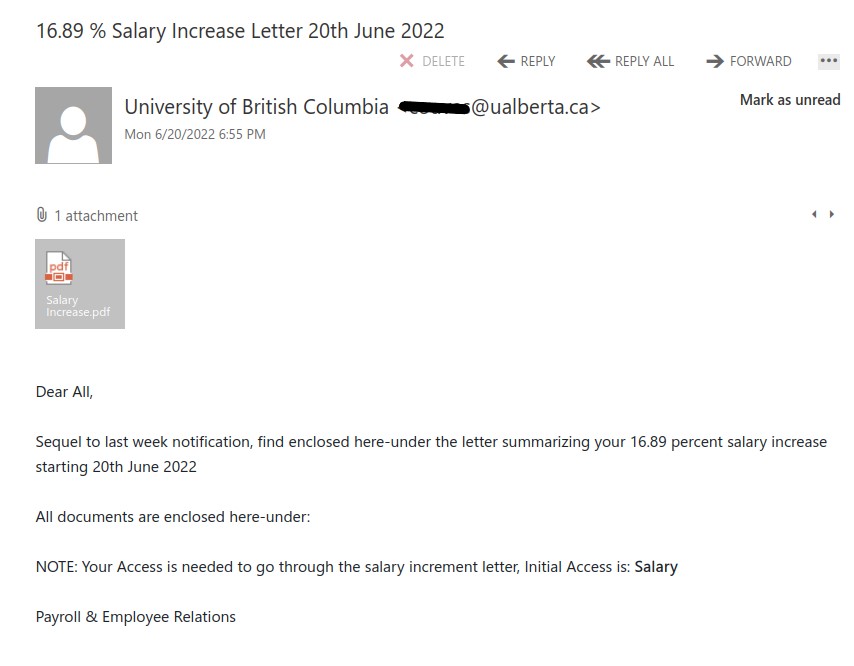
Yesterday evening we were hit with massive phish, around 11k recipients.
Telltale signs:
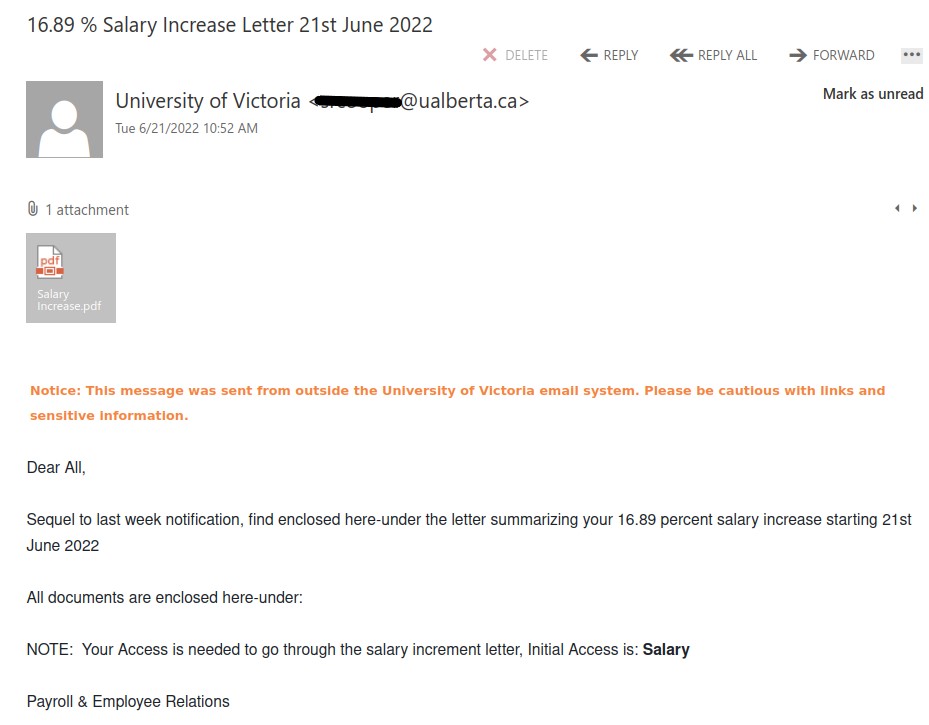
- Giving you the bait of 16.89% salary increase. Too good to be true!
- Why would your salary increase notice be coming from ‘University of British Columbia’?
- Although it says sender is ‘University of British Columbia’ but if you look at the email account, it indicates University of Alberta.
- General Salutation, ‘Dear All’.
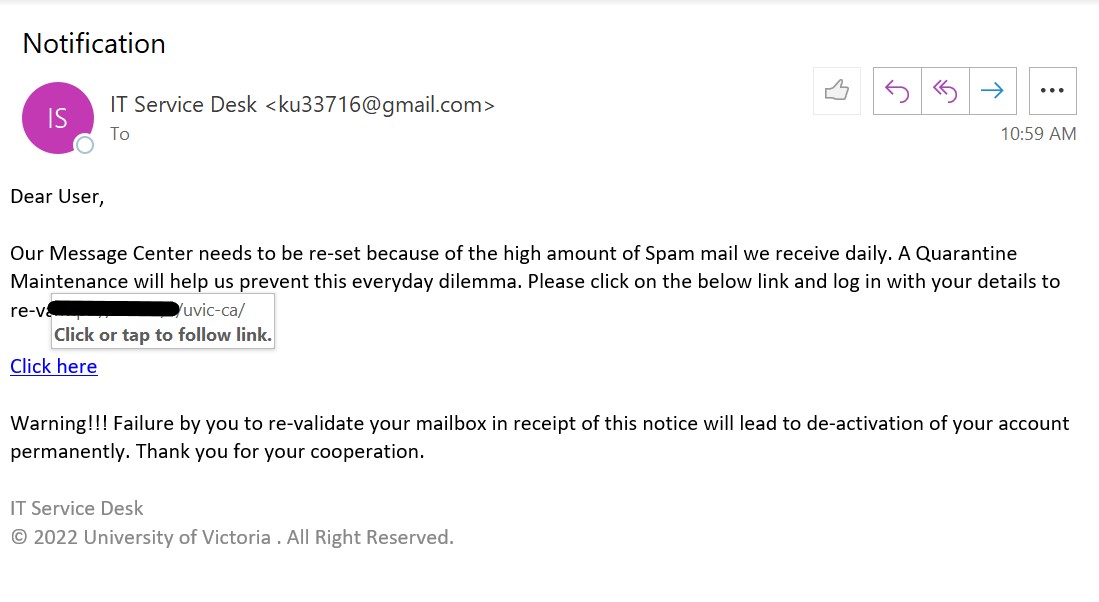
Whenever you get such phish emails, STOP before taking any action and THINK who would send you such an email if it were to be true. It would never be an external sender and would never have an attachment.
Never open any attachments unless you were expecting one.
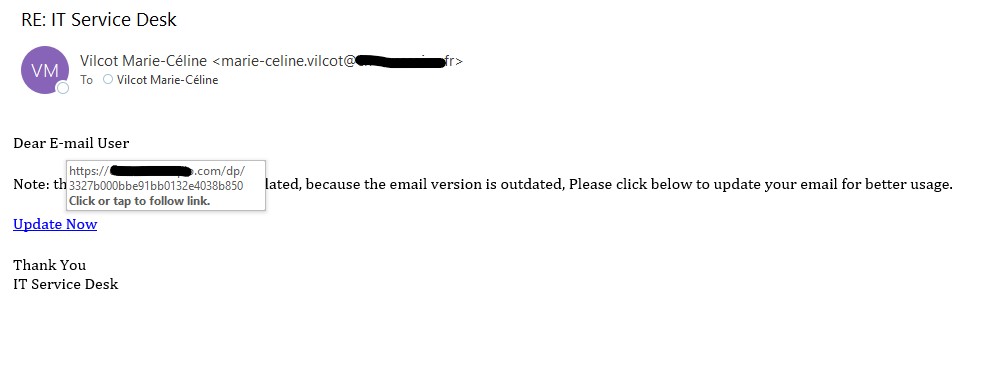
The attachment actually leads to the following sign in page. Hence, this phish is after your credentials.

The attachment was opened by InfoSec team in a safe and locked environment. Never be curious to do it yourself.
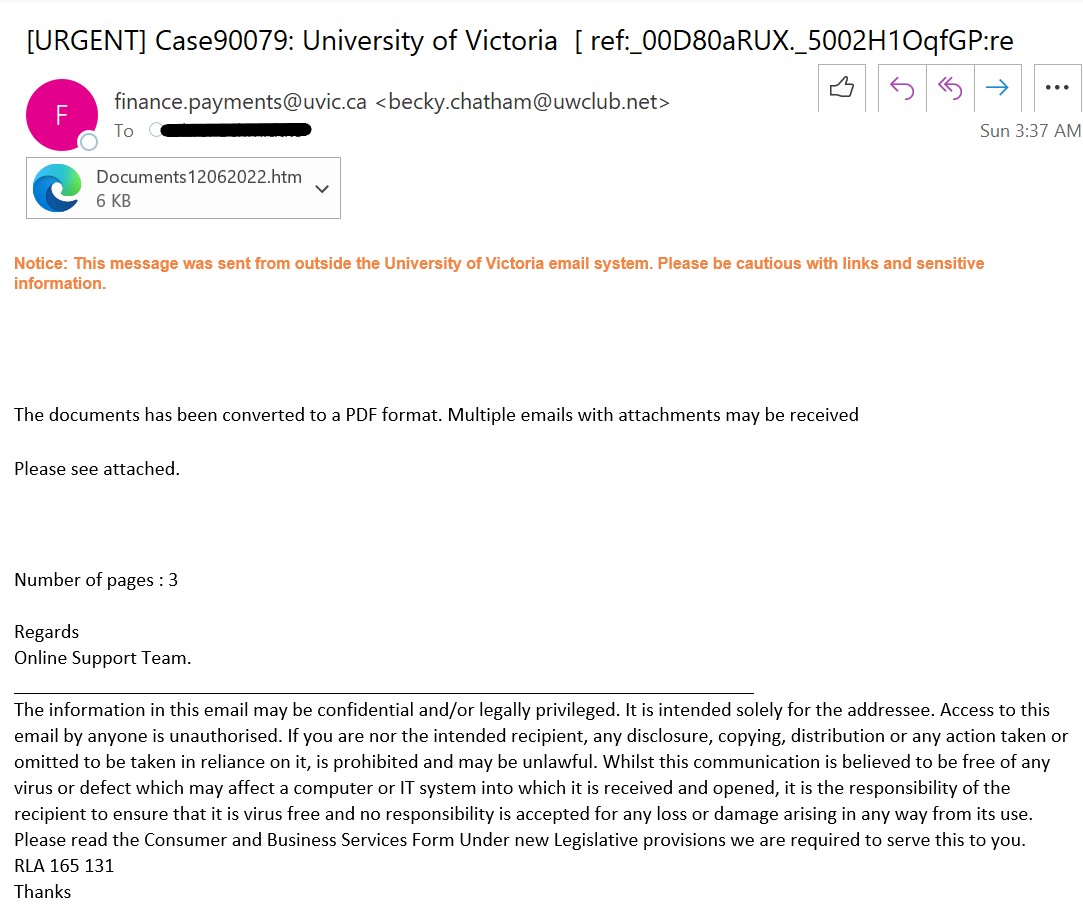
The new phish batch just arrived using a different ualberta account. Phishers corrected their mistake and changed the sender to ‘University of Victoria’, so as to appeal to our audience.