In this case, the phisher used admin@uvic.ca as the display name to make this message look legitimate. However, the sender address clearly shows that the message did not actually come from UVic.
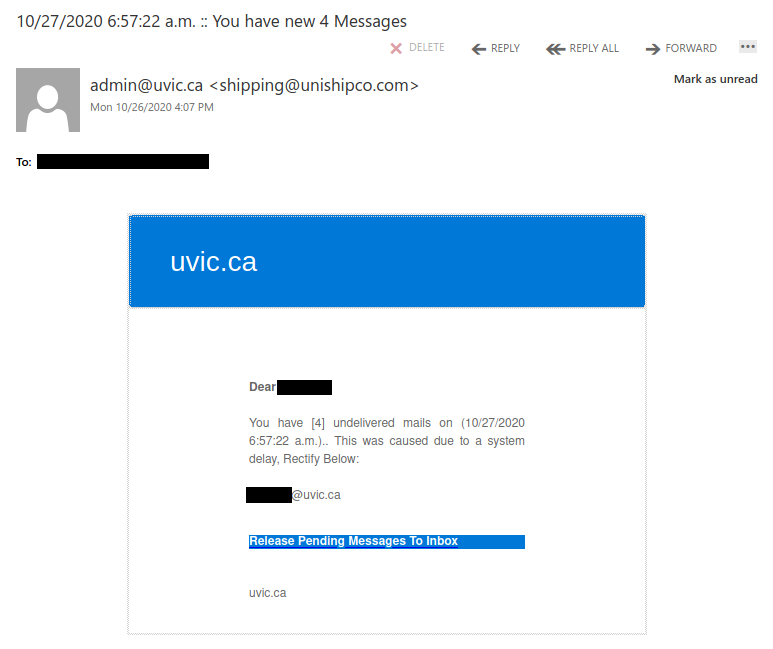
In this case, the phisher used admin@uvic.ca as the display name to make this message look legitimate. However, the sender address clearly shows that the message did not actually come from UVic.

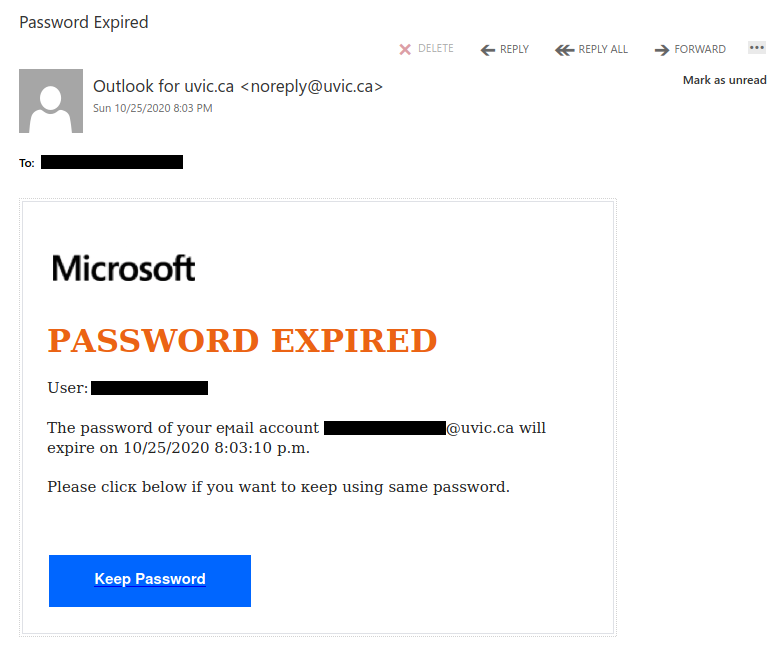
This email claims to come from the UVic no reply address but that has been spoofed. The password expiry notification is fake and did not originate from either Microsoft or UVic. Do not click on that link–if you did, please contact your department’s IT support staff or the Computer Help Desk immediately.
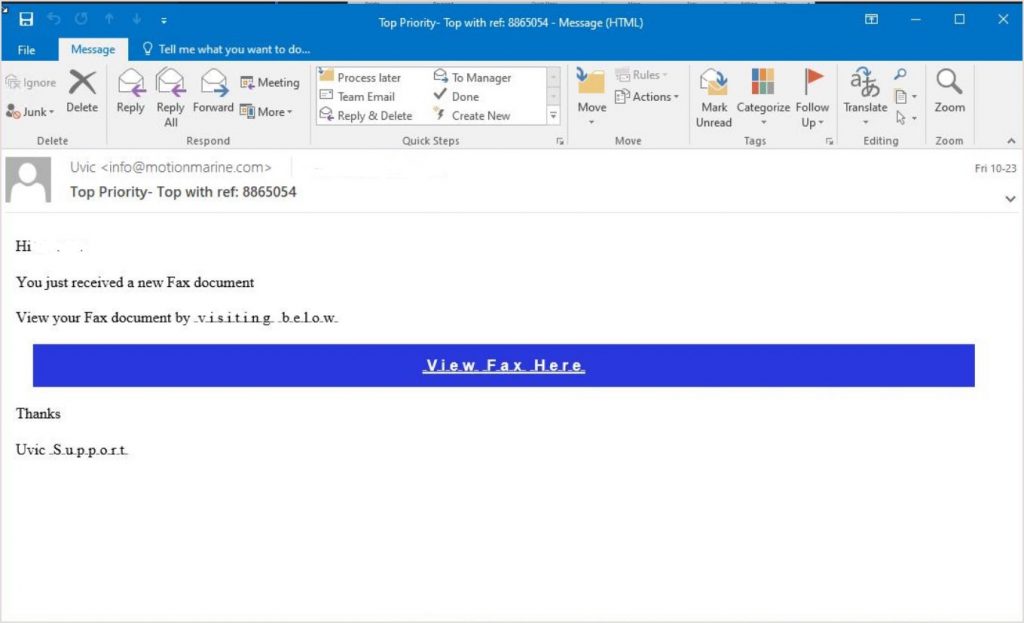
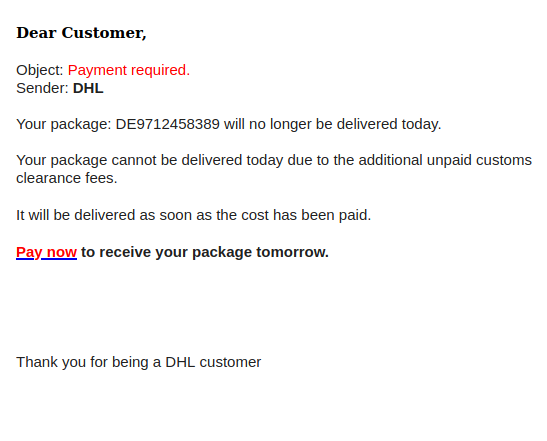
Digital faxes have replaced most old school fax machines, and we do see fake emails trying to trick users into clicking a link to a fax. If you’re not expecting one, it is suspicious. If it appears to be from a vendor you know, considering calling them to confirm before opening.
This phishing email also used some odd website encoding for some of the text (e.g. ‘visiting below’) that only displays correctly in certain email software, such as Outlook.
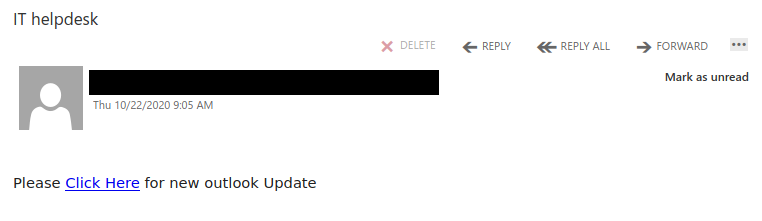
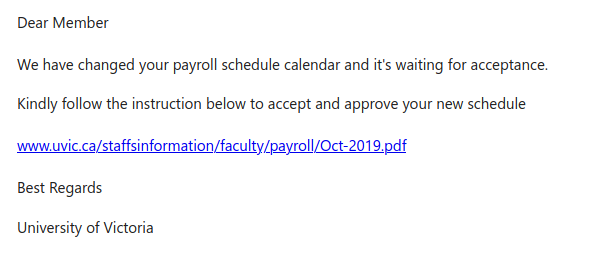
This message has a sender address of noreply@uvic.ca but that was spoofed; this message definitely did not come from UVic and the links all go to a phishing page.

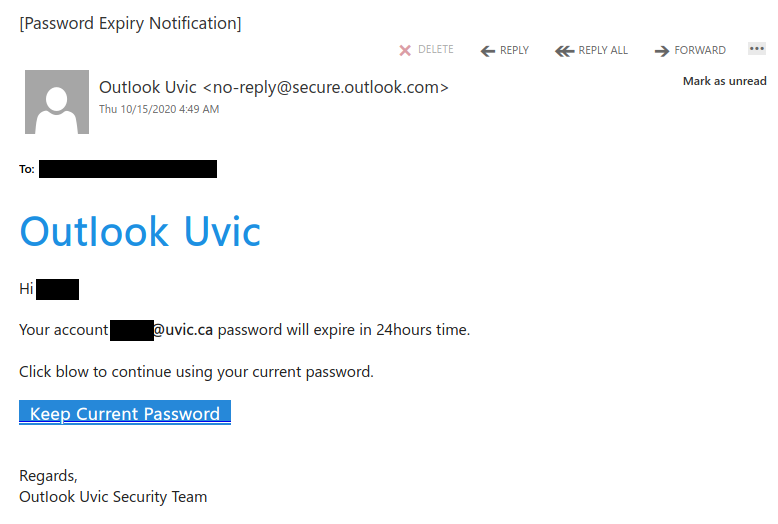
This phish has a spoofed sender of no-reply@secure.outlook.com, but in reality it did not come from Outlook.com. The link goes to a fake OWA login page on a site that is not affiliated with either Microsoft or UVic. Do not click on that link–if you did, contact your department’s IT support staff or the Computer Help Desk immediately.
The link in this spear phish may look like a UVic site, but if you hover over it you will discover that it actually goes to some other site that isn’t affiliated with UVic. Do not click on that link–if you did, please contact your department’s IT support staff or the Computer Help Desk immediately.
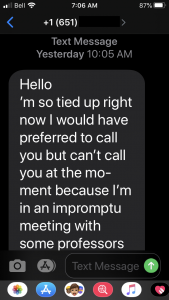
Scammers use multiple tactics to avoid detection. In this example, a likely gift card scam attempted to pivot to using SMS (text messaging) by asking for a staff member’s personal cell phone number. If successful, it would move the conversation with the scammer away from email systems to avoid detection of the conversation, and may have resulted in disclosing of a personal phone number to a scammer.

Signs this might be a scammer include a fake external email address, the urgency of the subject line, and the request for a personal number. The email warning banner at the top also indicates it didn’t originate from a UVic email address.
Someone who sent their cell phone number might have received a text message conversation starting out like this:
To see what a typical gift card scam email conversation might look like, check out a recent CISO Blog story detailing an interaction with a President Jamie Cassels impersonator.
The phishing link in this message goes to a fake OWA page that is actually a Weebly site. If you clicked on this link, please contact your department’s IT support staff or the Computer Help Desk immediately.
The message in French at the end basically says the message was automatically scanned by an email virus scanner. This was probably added by the phisher in an attempt to make the email look safe. For this reason, notes about antivirus scanning at the end of an email should not interpreted as a sign that the email is actually legitimate or trustworthy.
