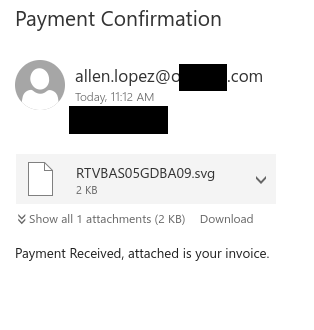
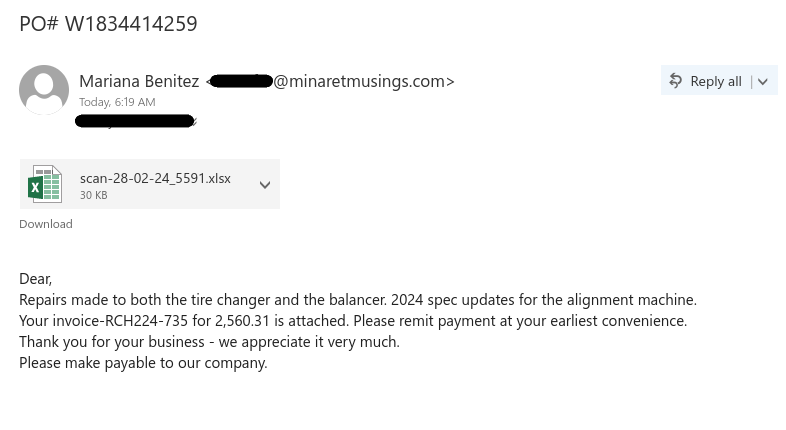
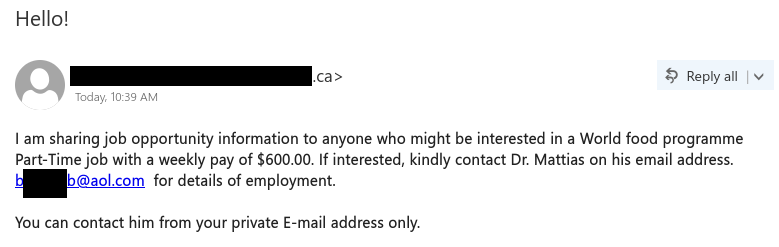
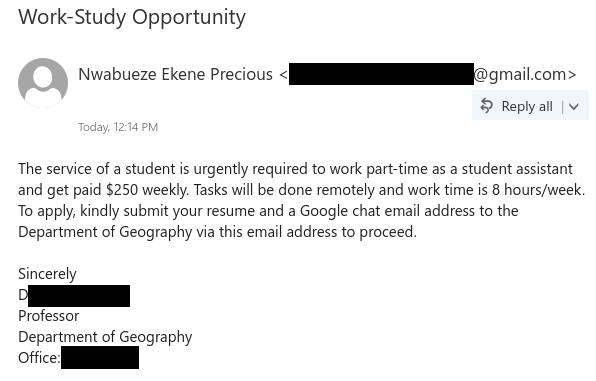
Scammers routinely attempt to target students with job scams, taking advantage of those trying to make ends meet or pay tuition and rent with a seemingly-attractive job offer. In reality, the victim is asked to deposit a fake cheque and immediately send an e-transfer from their personal banking account. Given the cheque is fake, the victim will see the deposit cancelled/reversed by the bank, and they will have lost their own personal funds.
Recently I had the opportunity to play the role of the victim using a persona configured for this purpose. The following are some screenshots of SMS messages and emails that give insight into how the attacker works and how a victim might be fooled into giving up their hard-earned personal funds.
Note that some details have been redacted. Also, do NOT try this yourself. This is posted for educational purposes only.
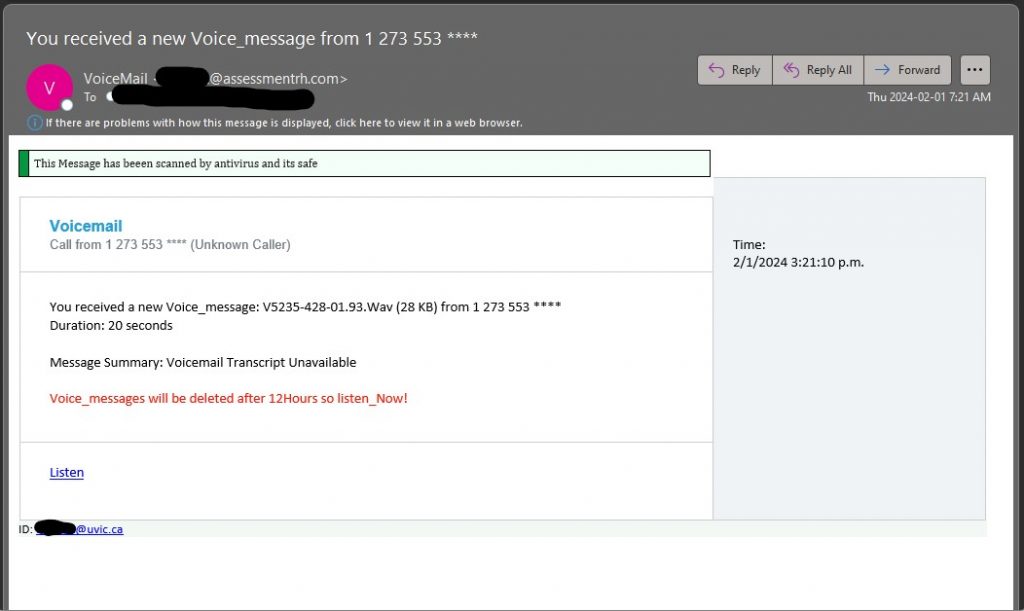
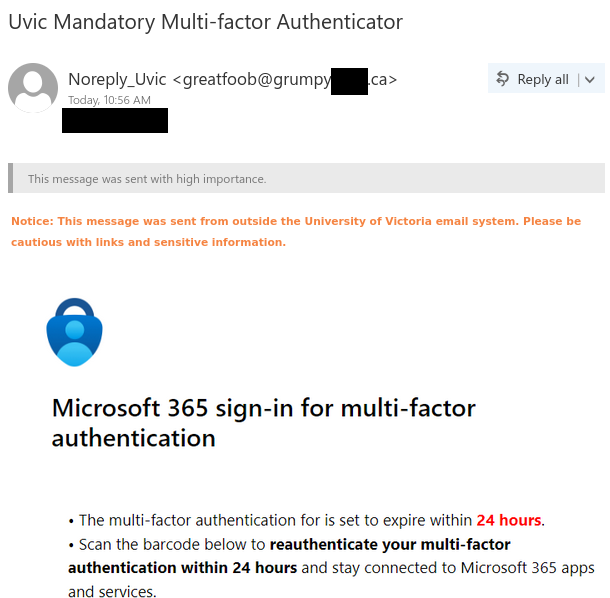
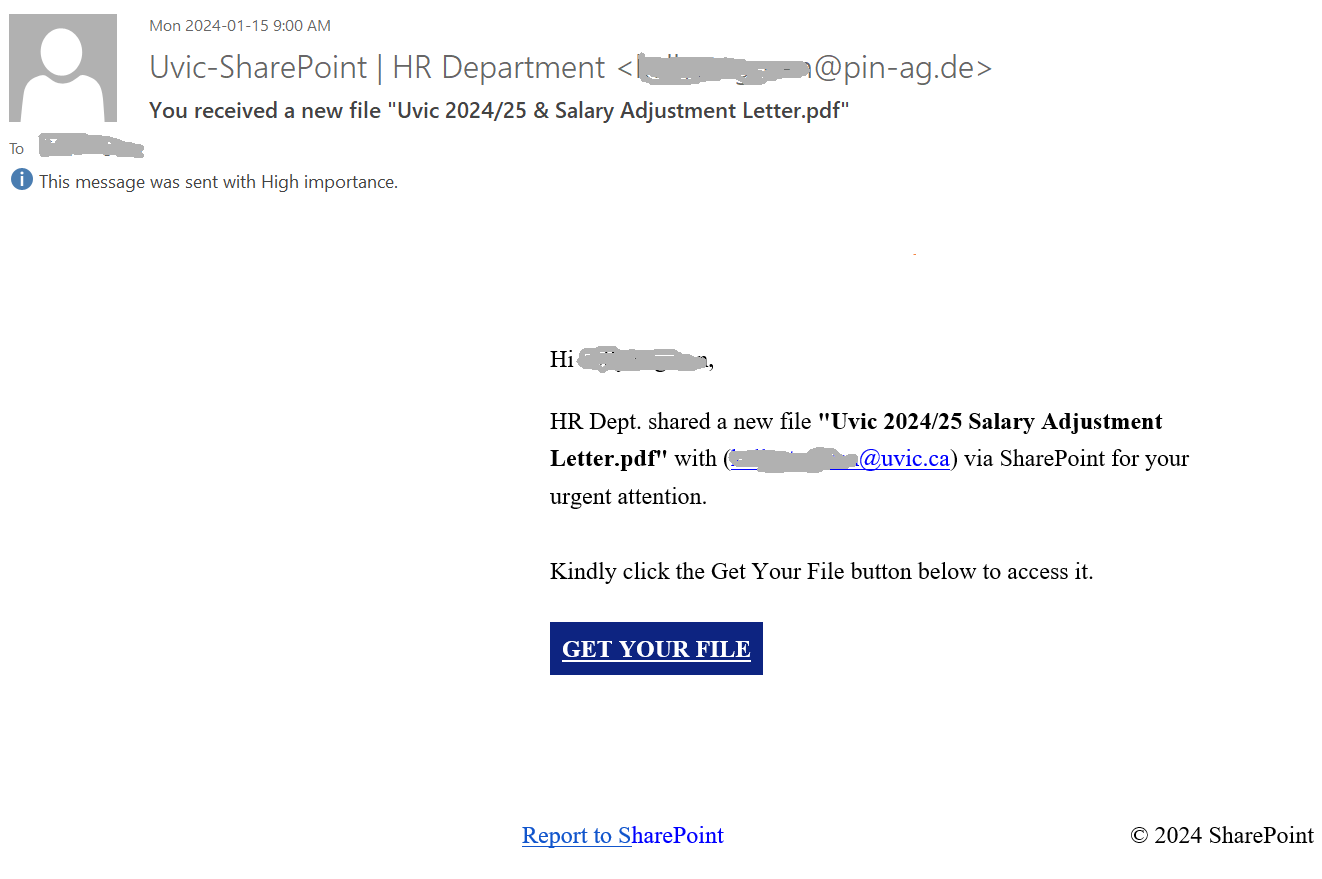
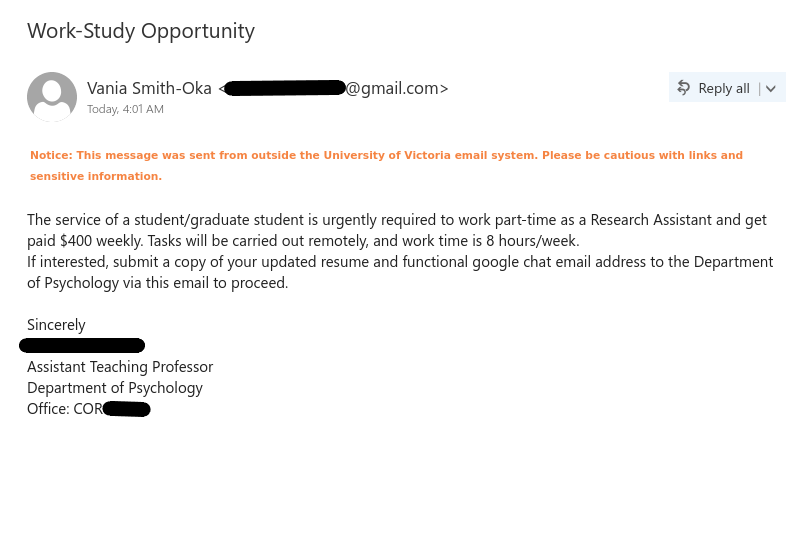
A recent phishing attack included form fields for username, password, and cell phone number. For this attack, a fake username and password were entered, as well as a temporary phone number from a SMS app. A couple weeks after the data was entered into the form, I received a text at that temporary number.
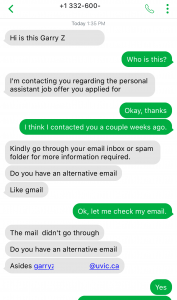
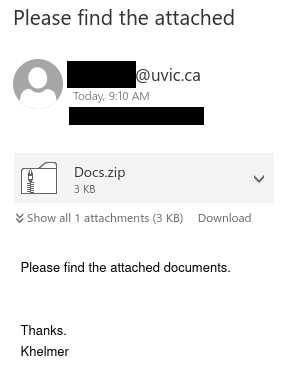
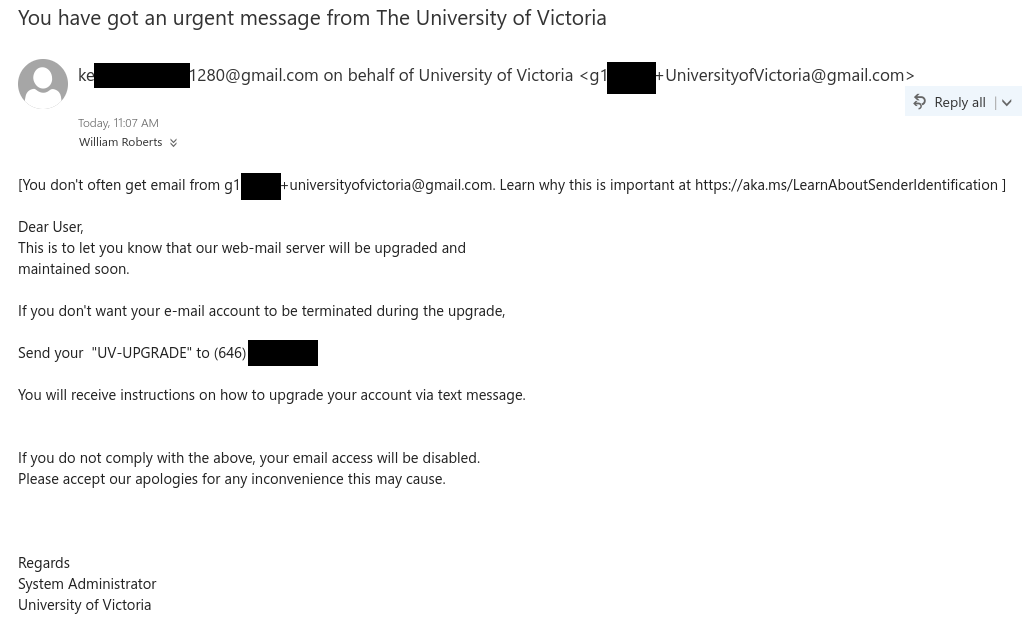
The attacker tries to pivot off of @uvic.ca email so that the information security team can’t discover or block the fraudulent activity. The use of SMS is also a common tactic for scammers to move the conversation off university infrastructure. I had to quickly create a new Gmail address to engage with the scammer.
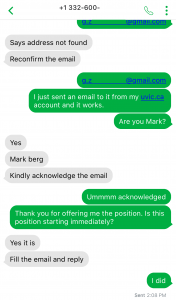
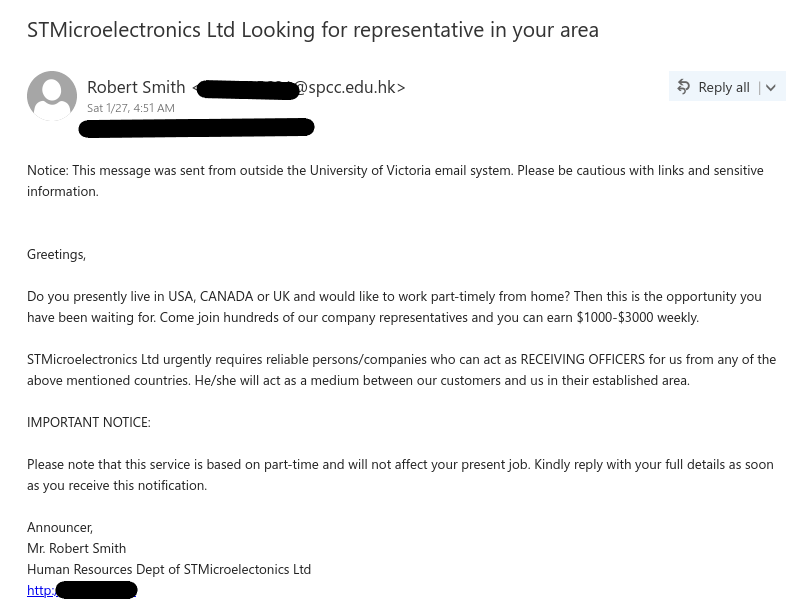
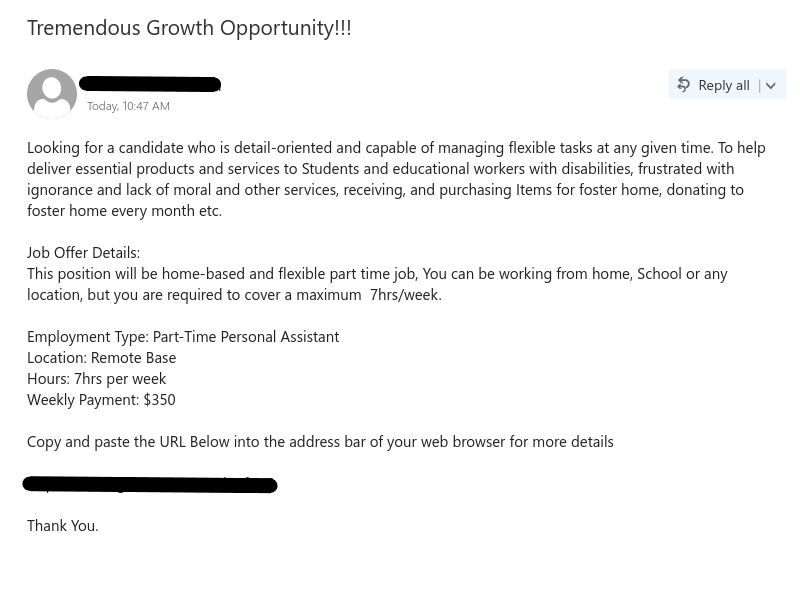
In my brand new Gmail account, I receive an email about the job offer. “Mark” is careful to make sure I know why I won’t be interviewing in person (or by Zoom) just to make sure I won’t ask questions. I carefully read the email, and then I respond with the requested information (plausible, but fake answers, knowing that Mark wouldn’t actually read them or care about them).

And there it is! I’ve gone through the very difficult interview process and have now become Mark’s employee. And I’m really looking forward to my 401k (a US financial instrument, even though I’m Canadian), multiple employment benefits, and a sign-on bonus! All for $450 per week. Time to quit my CISO job for the lucrative opportunity….

Of course, I have to be polite and let Mark know how excited I am. I wonder if he knows how “schmincere” I really am.
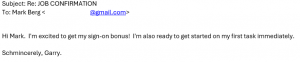
I am soooooo ready for the first task as my boss’s new personal assistant.
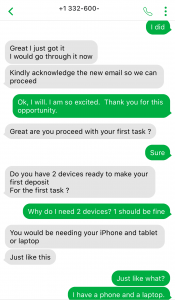
Amazingly, Mark emails me instructions on how to do a mobile deposit for the fake cheque using two devices. The support and instruction is superb for a new employee.
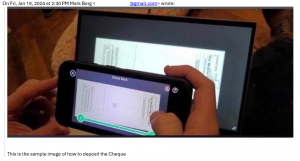
While I review the instructions, Mark pretends to have the bank endorse the cheque, so that I will be more comfortable doing the mobile deposit. Knowing the bank has blessed it makes me feel so much better. And of course, he gives me some great instructions on how to deposit, just so I get it right. Maybe Mark has worked at a help desk before.
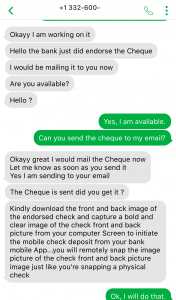
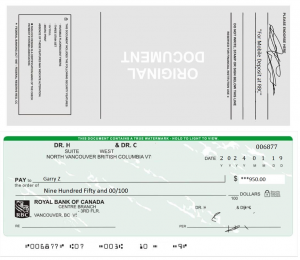
Here is where it get’s even more interesting. Mark emails me an image of a cheque from Royal Bank (I had indicated in my job application that I banked at Royal Bank).
The cheque appears to be plausible, if not legitimate. The transit numbers were validated using an online bank routing database, and matched the branch address information on the cheque. The names and address of the people on the cheque seem to be real, or at least based on a real person, from what I could tell from a searches of Google and Google Maps.
For most people, this look like a legitimate cheque… except that it’s a picture of a cheque, not a paper one. (Note that I’ve reported this to Royal Bank.)
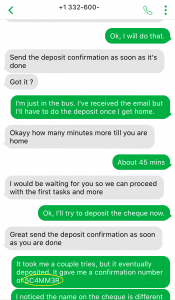
Now that I have some interesting information from Mark, I wanted to play a little and see if he noticed I was on to the scam. I don’t think he picked up on the confirmation number I received when I “deposited” the cheque.
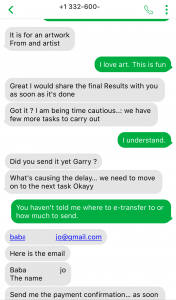
Mark’s name shockingly didn’t match the names on the cheque, so of course I had to see what reason he would give for that…

Mark still hasn’t told me what kind of business he is in, so I ask him, and of course it doesn’t even match the kind of business mentioned on the fake cheque. Clearly he doesn’t want to share lots of detail, and he has an urgent job to do. He provides me the name and email address to which I need to send an e-transfer. (I’ve reported this to Interac support for their awareness and action.)
We suspect this threat actor is possibly of Nigerian origin, based on some past activity. I decided to see if Mark would get another hint that I knew it was a scam, by mentioning Black Axe, which is a notorious Nigerian crime organization.
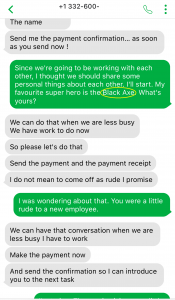
Mark is too busy for small talk and personal chatter. I dropped another hint for him. Air Lords are another known Nigerian criminal organization. Perhaps Mark isn’t familiar with them, or maybe he’s not really reading what I’m saying.
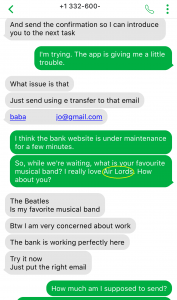
Earlier Mark had sent me the name and email address of the person to whom I was supposed to send the e-transfer. I looked up the person’s name on social media, and came back with several results, with multiple profiles indicating they lived in a particular town in Nigeria (surprise!). So, I used that town name as a confirmation code. I wonder if Mark started to suspect something…
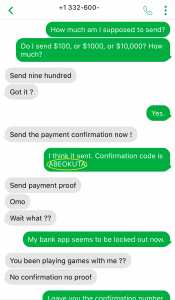
I think he’s on to me….
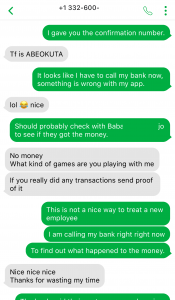
Mark and I eventually got tired of each other, and the conversation ended up dwindling after nearly 24 hours.
Hopefully this gives some insight into how someone could become a victim of such a scam and how the scammer tries to extract money from victims.