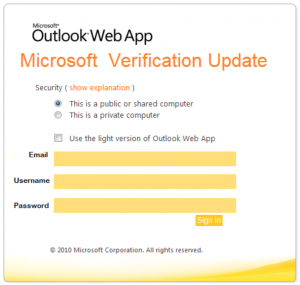
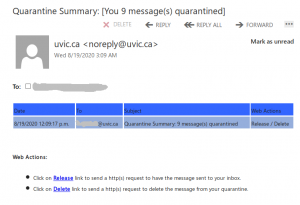
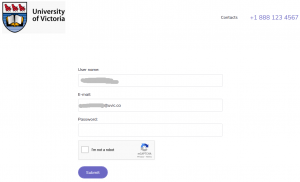
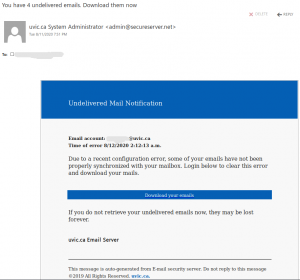
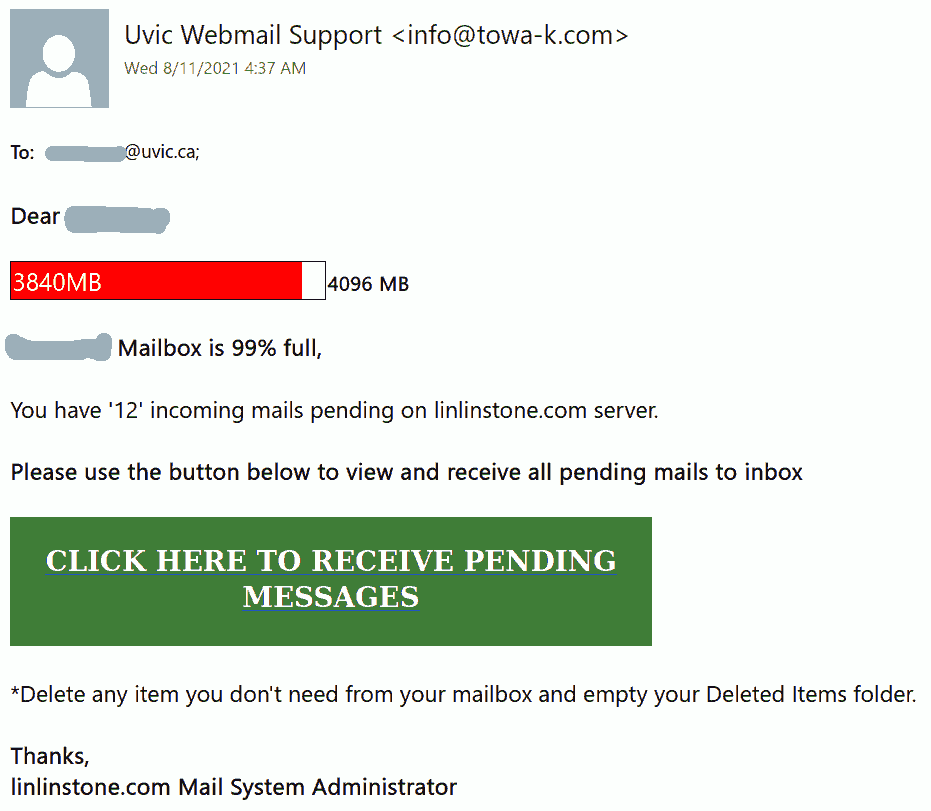
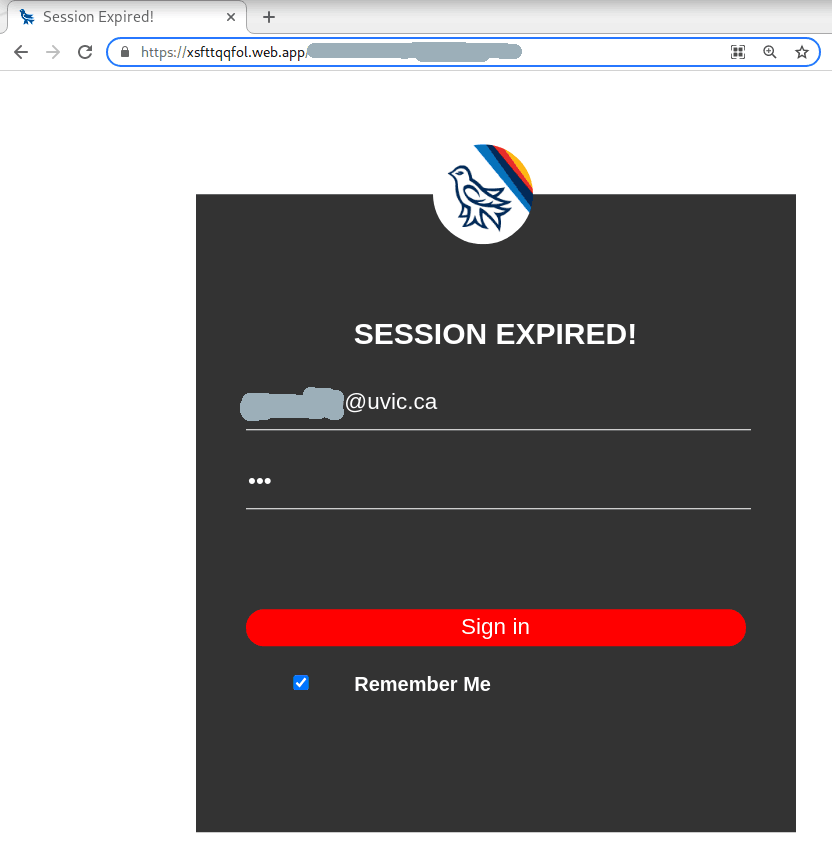
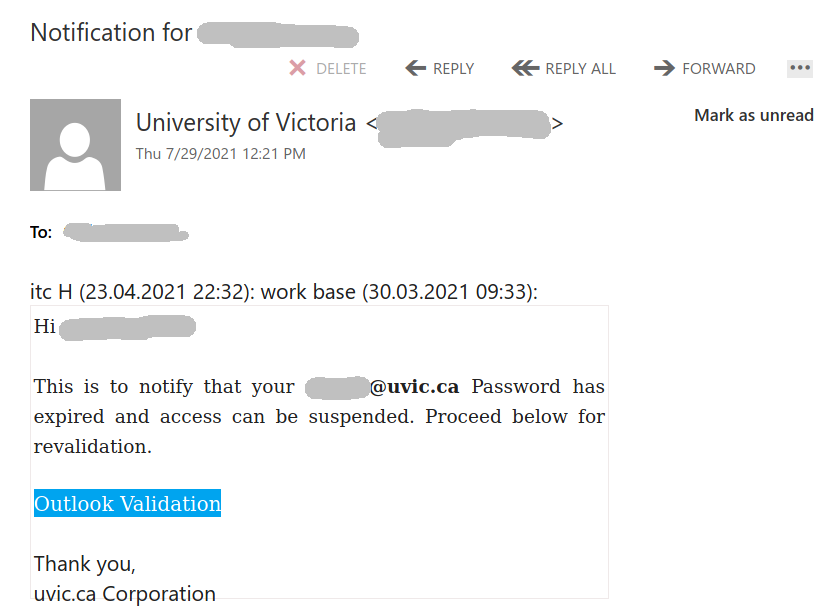
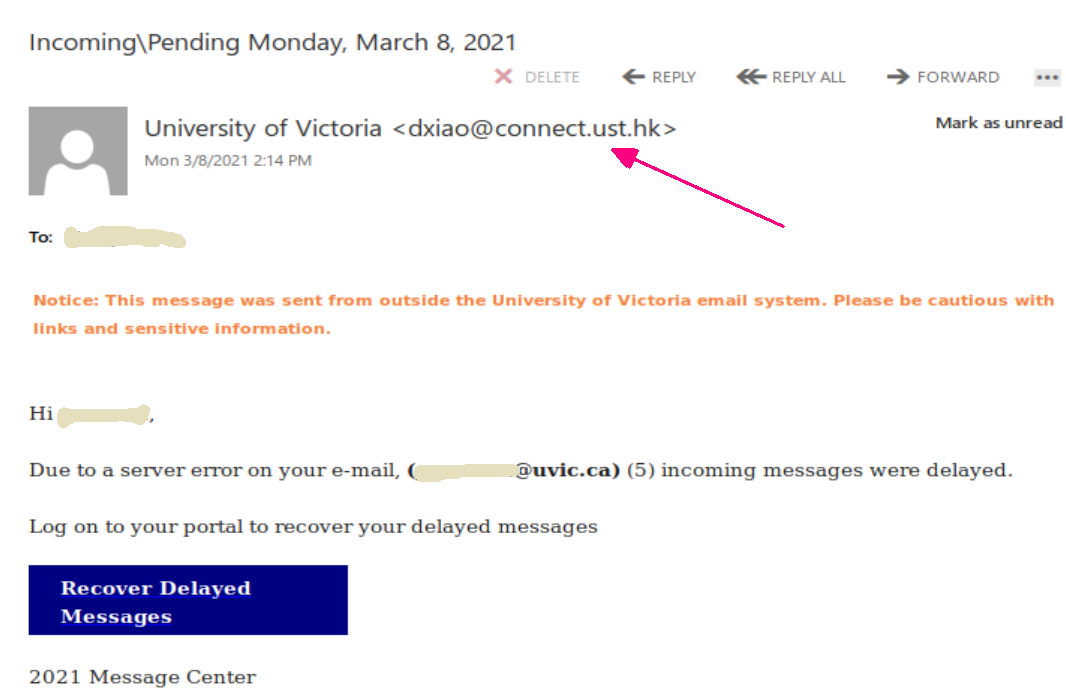
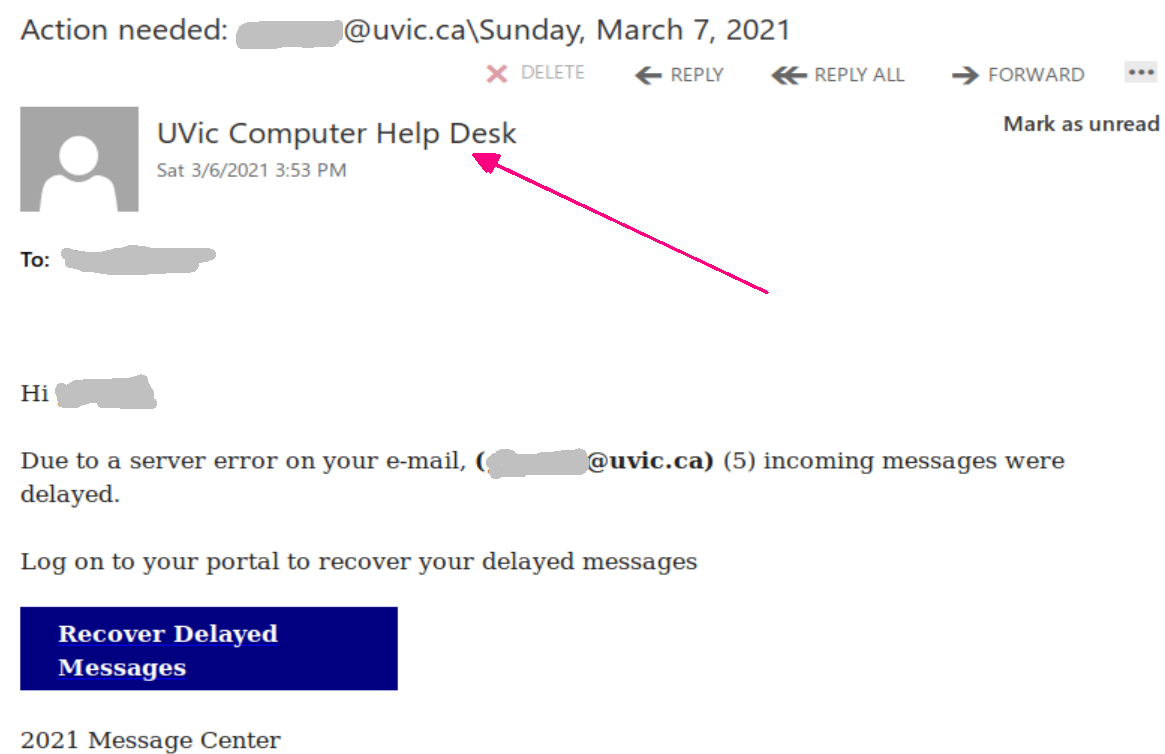
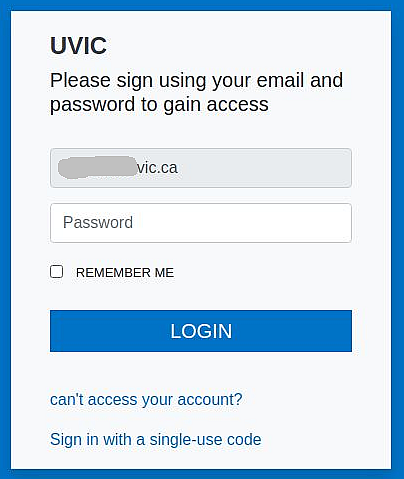
A colourful phish is circulating today. It has a flashy subject – [IMPORTANT] NOTICE and it tries to persuade you that you have to click the button in order to release a certain number of pending messages in your mailbox. The malicious actor named themselves “Uvic Webmail Support” but they did not bother to spoof the sender’s address. It is obviously not a UVic address. Also if you hover the mouse cursor over the link you will see it does not point to a UVic page. As we always repeat – Please do not be curious and do not click the link. Sometimes these pages may contain malware which gets installed in an instant. No matter you did not enter credentials, no matter you closed the bad page quickly. We investigate such pages in a special safe environment, the second screenshot shows how this fake Outlook Web Access page looks like. Apparently they targeted UVic specifically and used a UVic logo there.
 —————————————————————————————————–
—————————————————————————————————–





 =================================================================
=================================================================
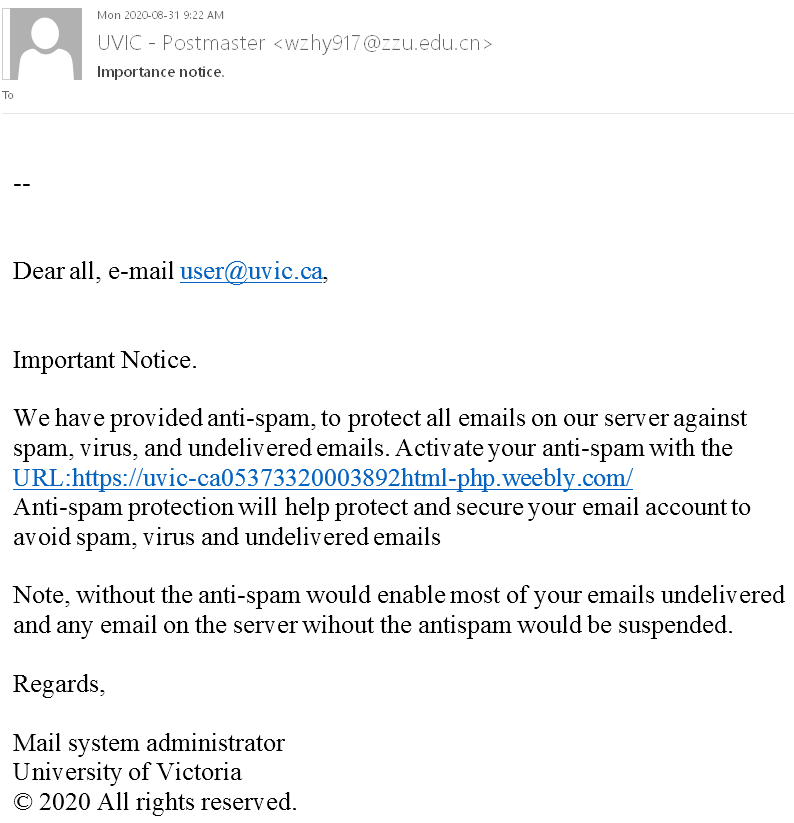
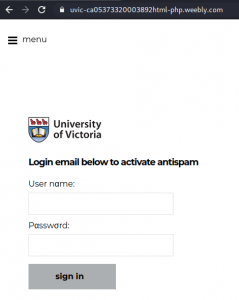
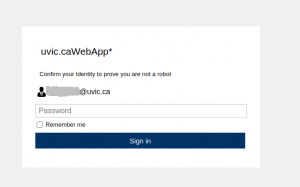
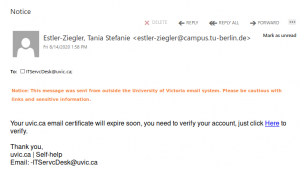
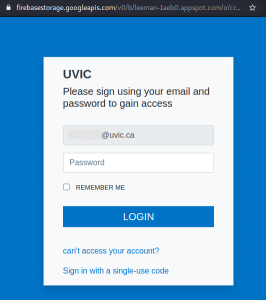
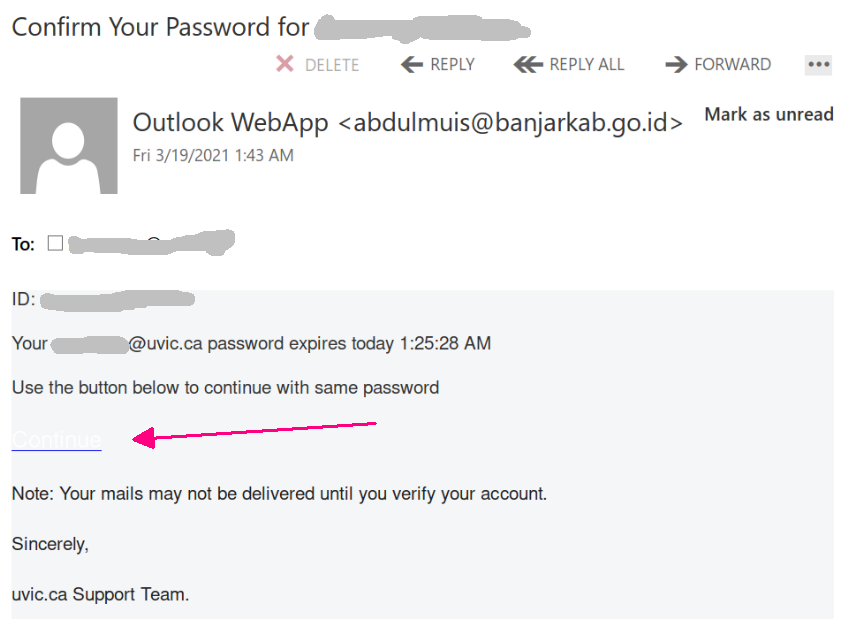
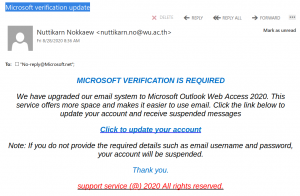 Please do not be curious and do not click on the link. The goal is to steal your UVic credentials (fake Outlook Web App page is shown below). Besides stealing credentials, these pages may contain malware which is why even opening the page is not a good idea.
Please do not be curious and do not click on the link. The goal is to steal your UVic credentials (fake Outlook Web App page is shown below). Besides stealing credentials, these pages may contain malware which is why even opening the page is not a good idea.