Malicious actors are trying a new trick this week. And it is gaining momentum because of the neat tricks of obfuscation they apply so that our automatic mechanisms cannot sort out such emails and more precisely such attachments.
The email subjects can be of any kind, for example this pattern is quite popular:
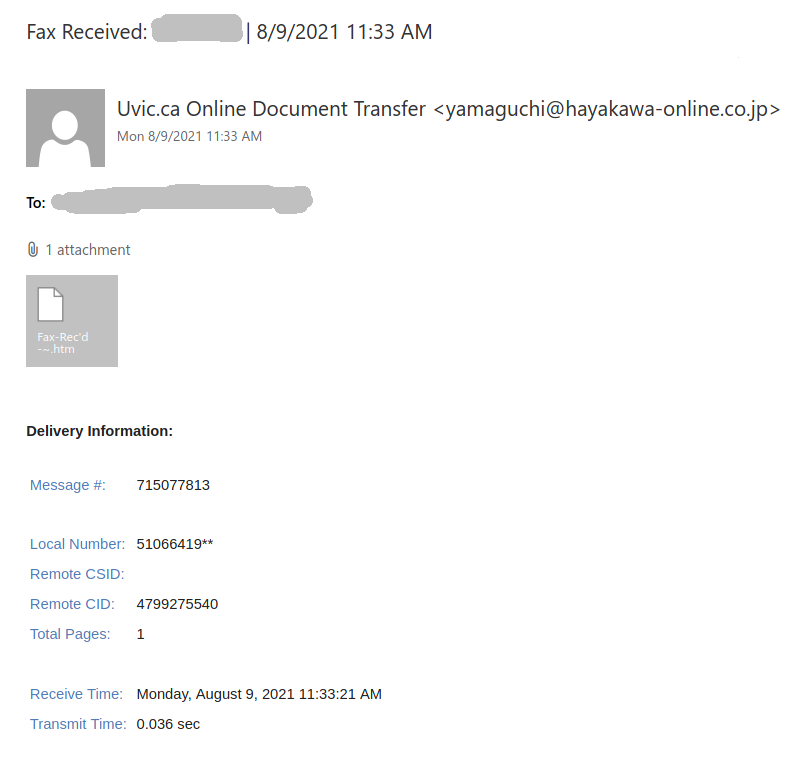
Fax Received: kakapena | 8/9/2021 5:44 AM
where the word after “Fax Received:” is the actual recipient’s name.
We’ve seen subjects without the recipient name like:
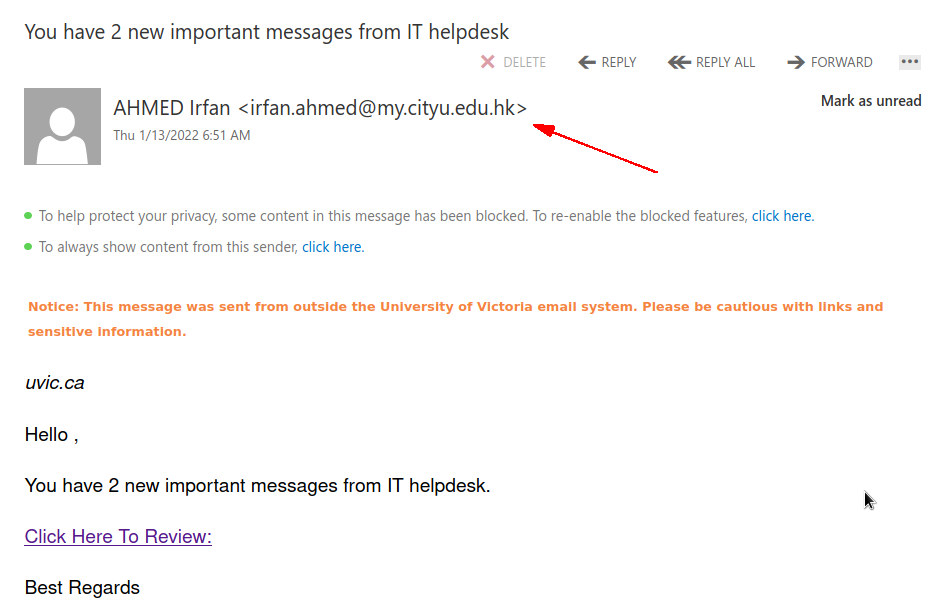
Incoming Fax notification 6:51:48 PM'
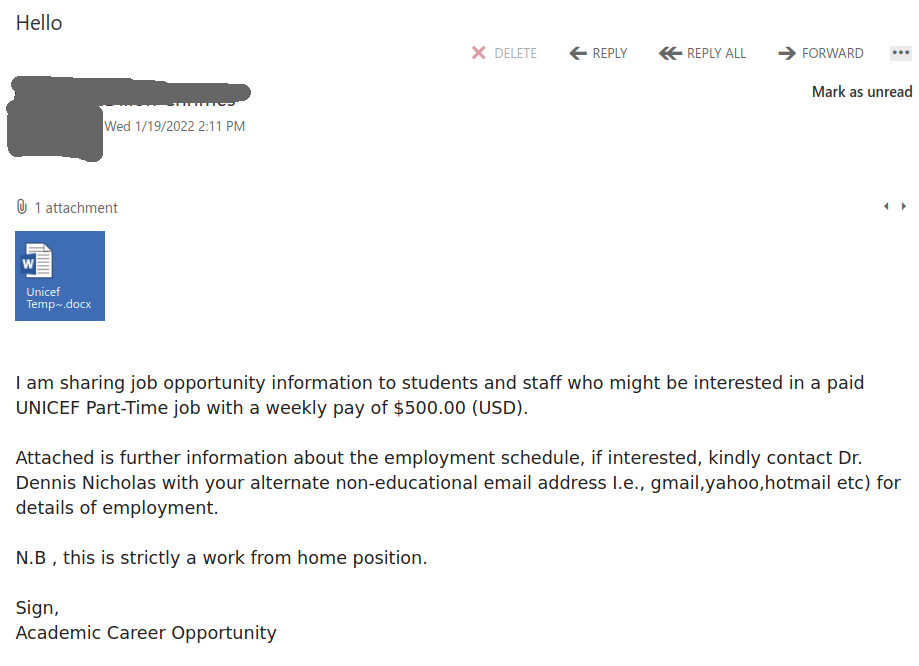
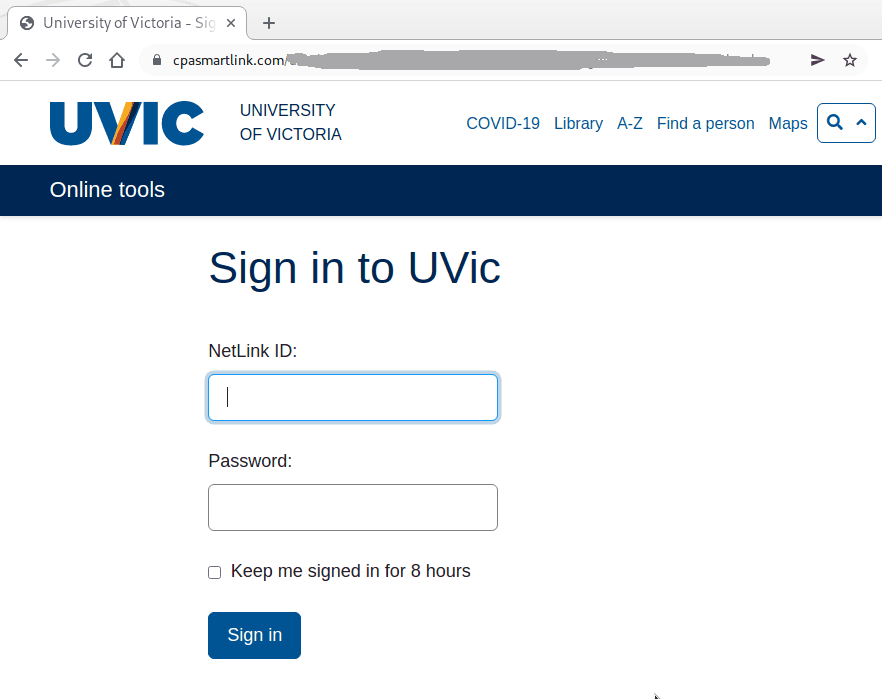
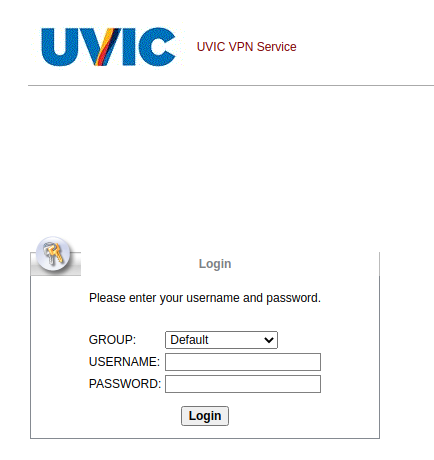
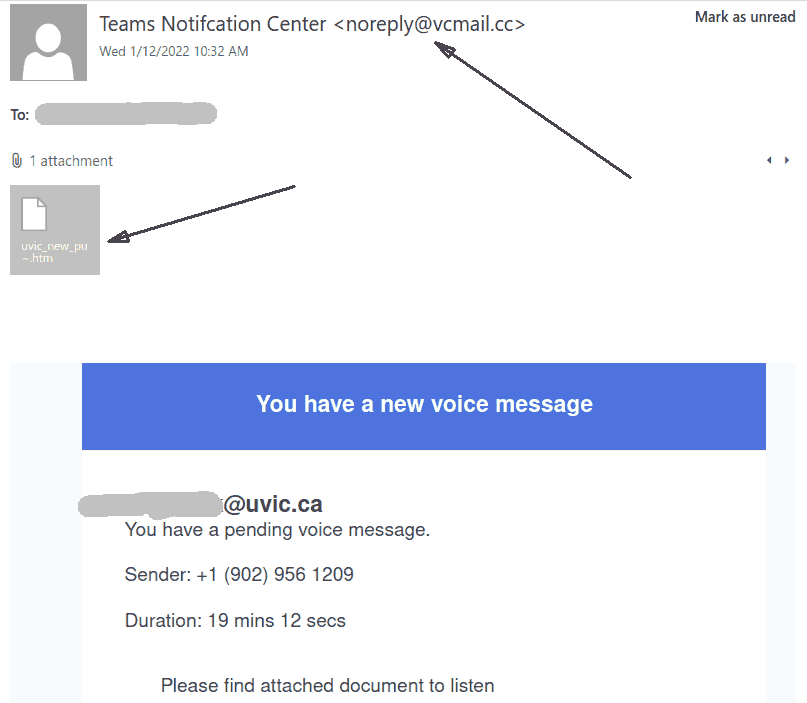
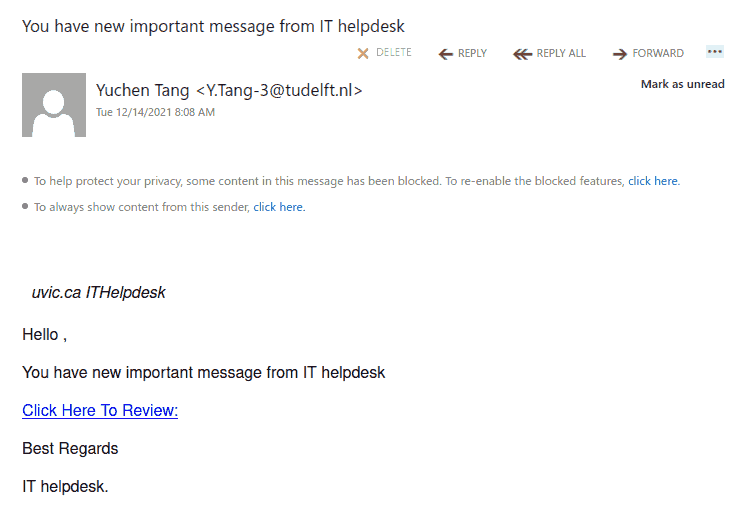
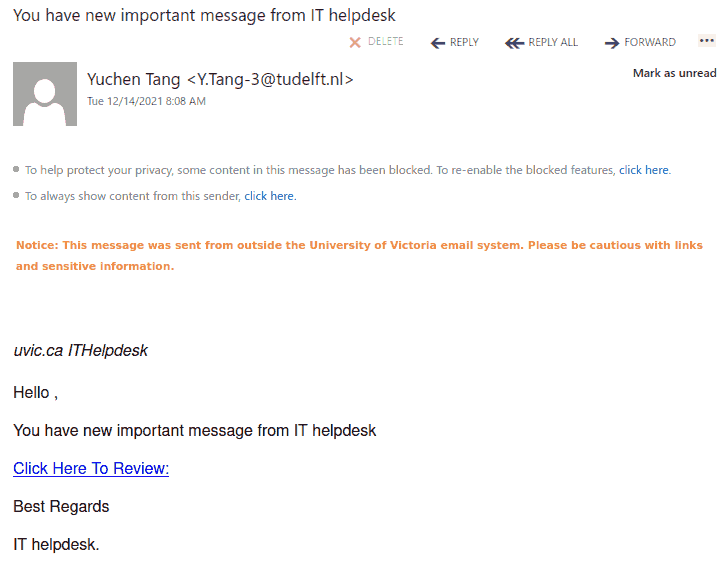
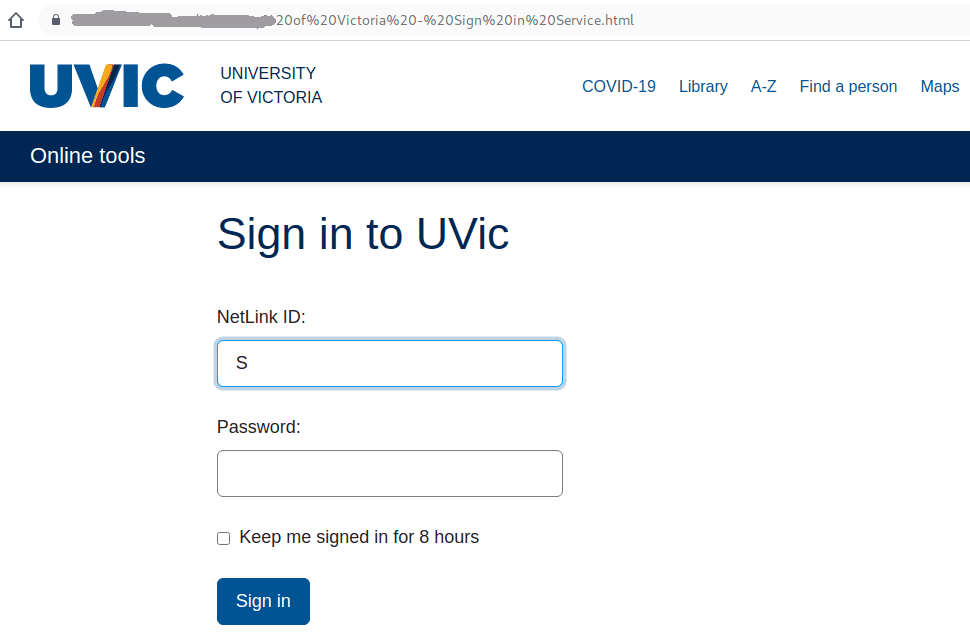
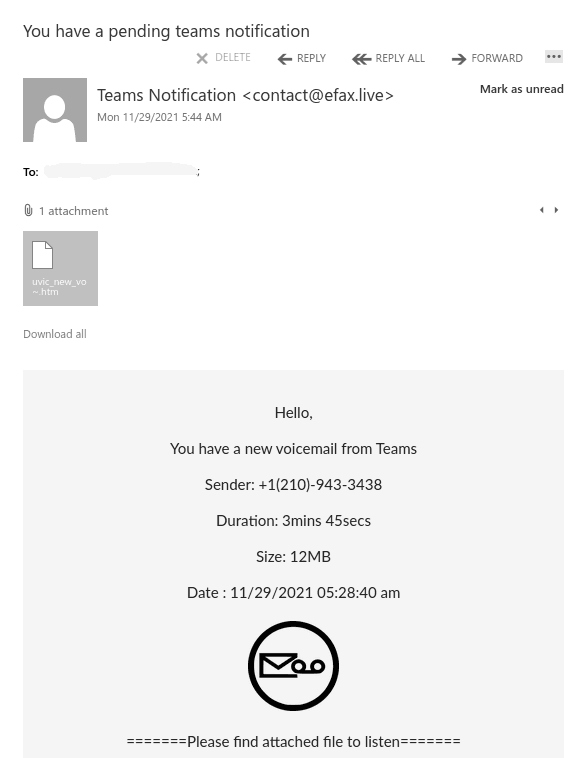
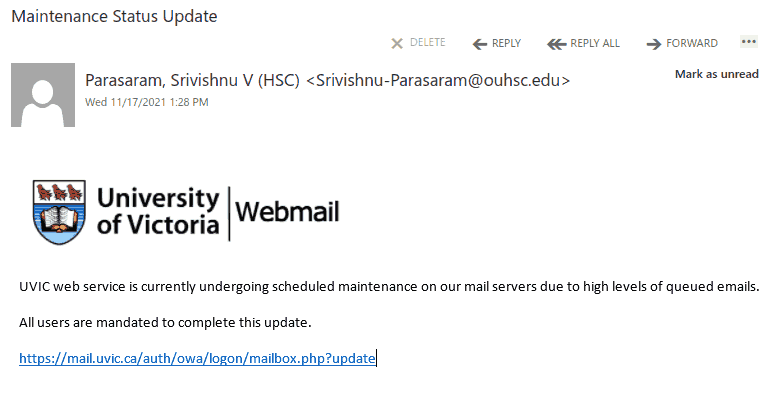
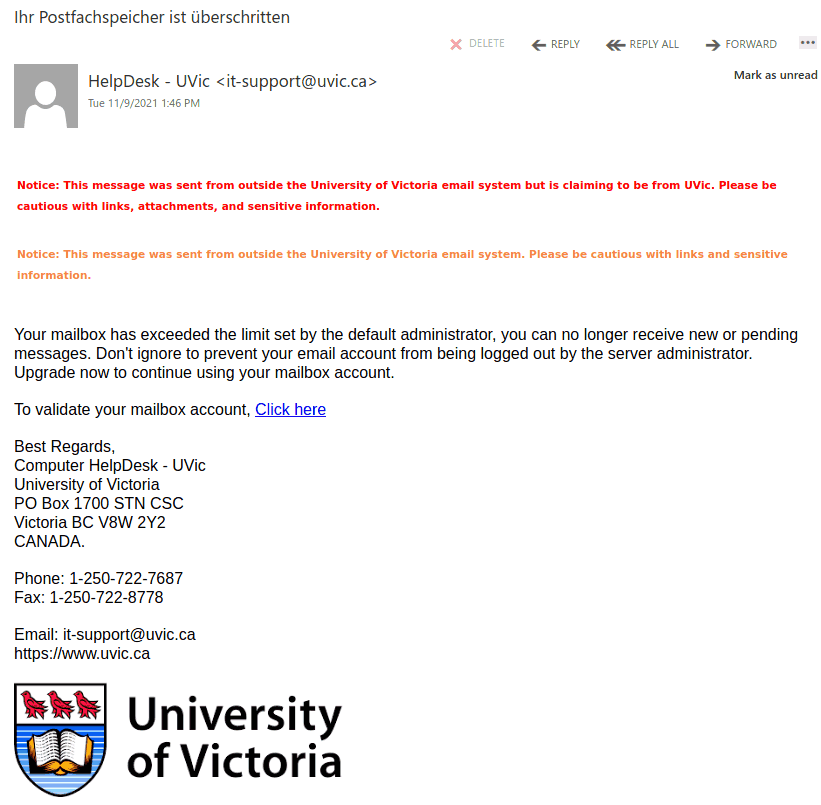
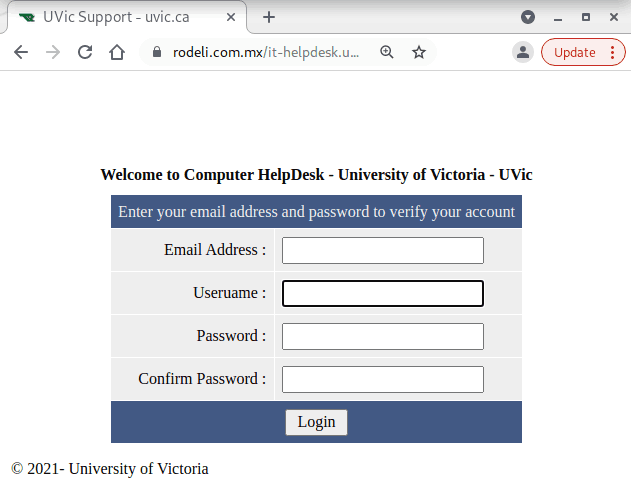
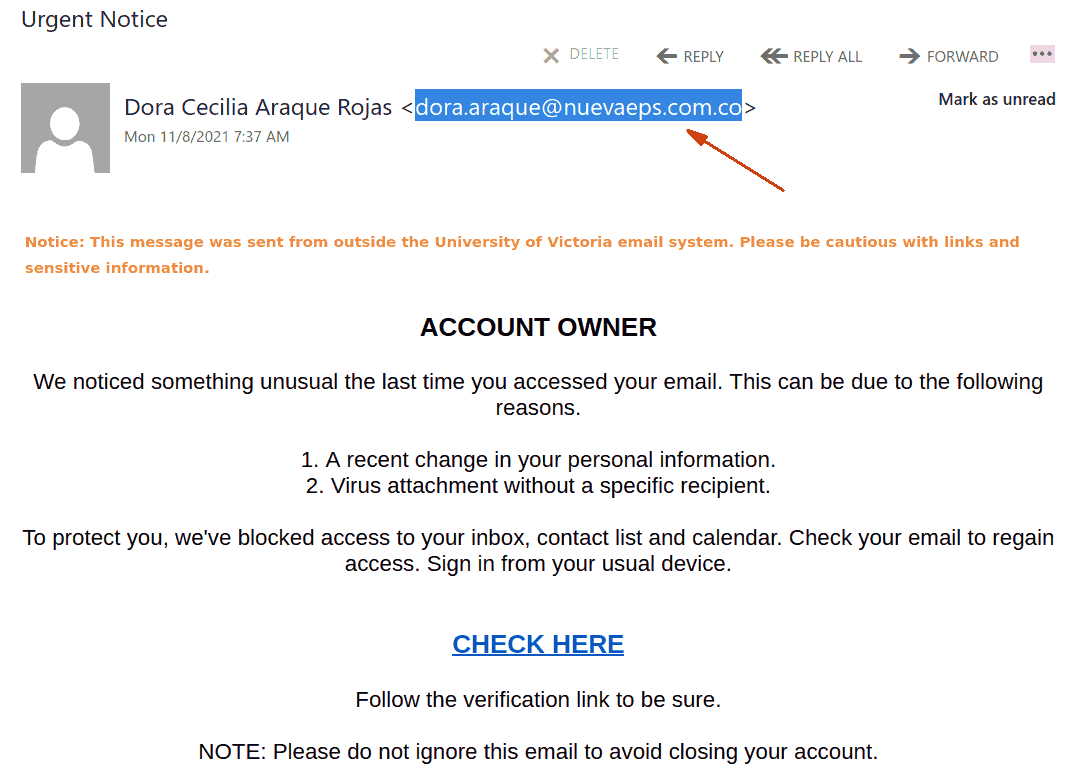
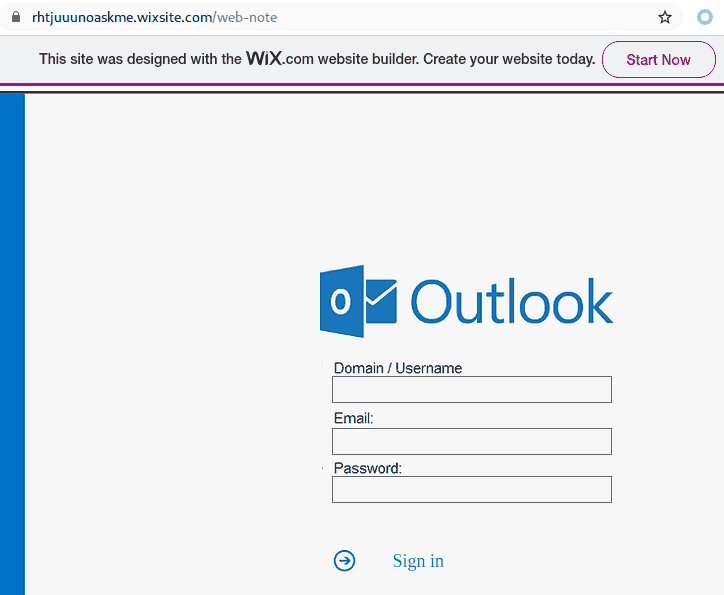
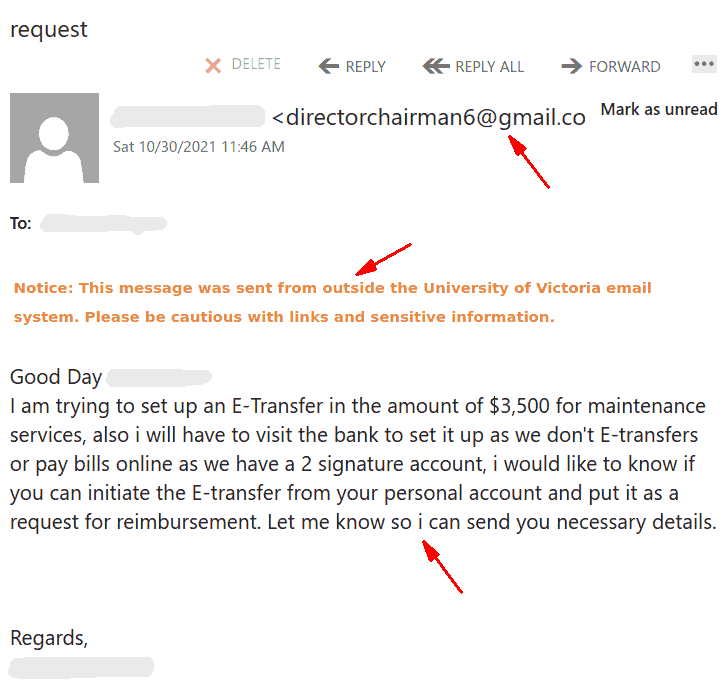
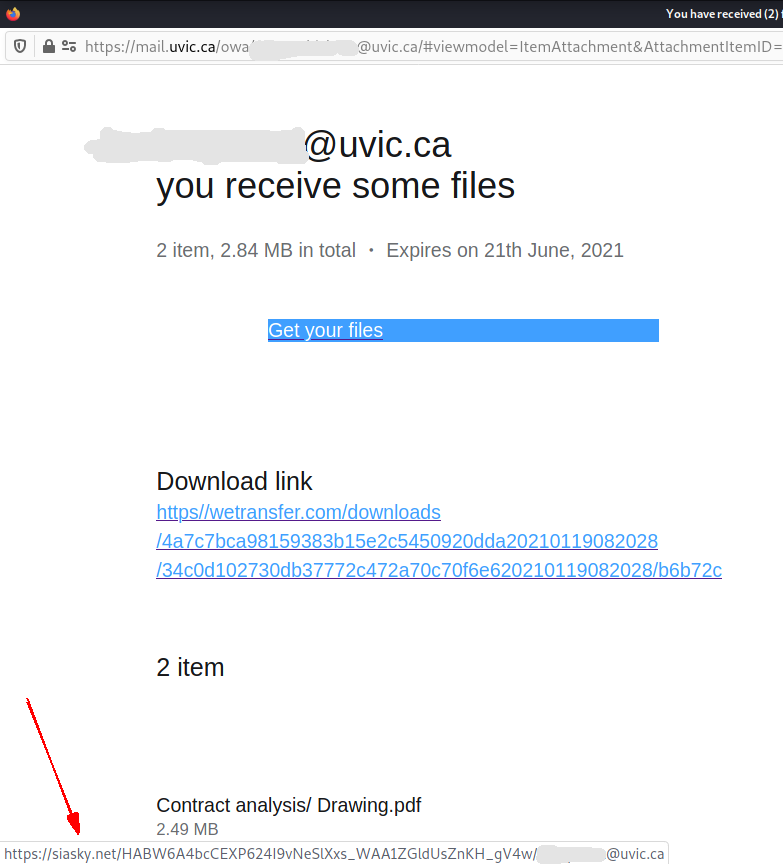
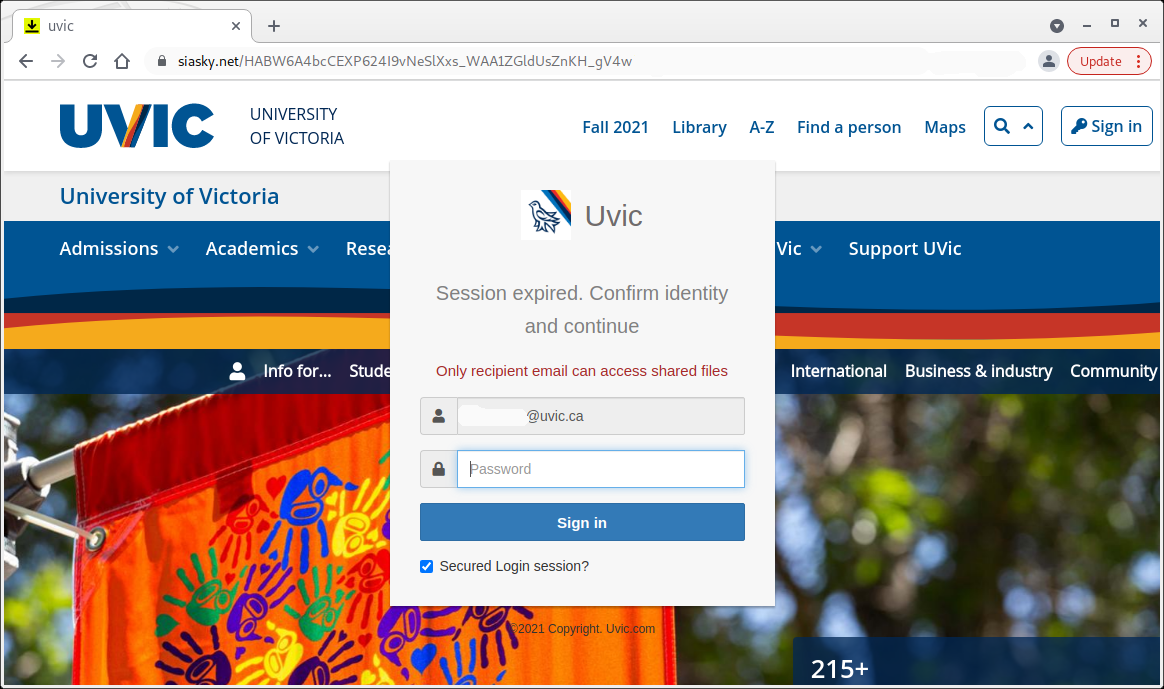
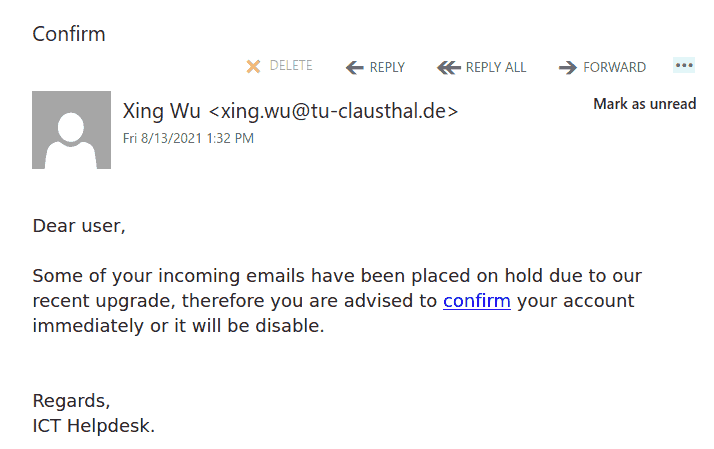
The subject is not important though. It could be any. The body of the email is also unimportant. See an example below. The common thing is the attachment which is a .htm or .html file. If you double-click that attachment it will open in the default application which is your default browser and present you with a web page designed to look like belonging to UVic with the sole purpose of stealing your UVic credentials. That’s the common type we are seeing recently.
Never click on those attachments!
They may utilize other tricks leading to downloading of malware and potential compromise of your computer.