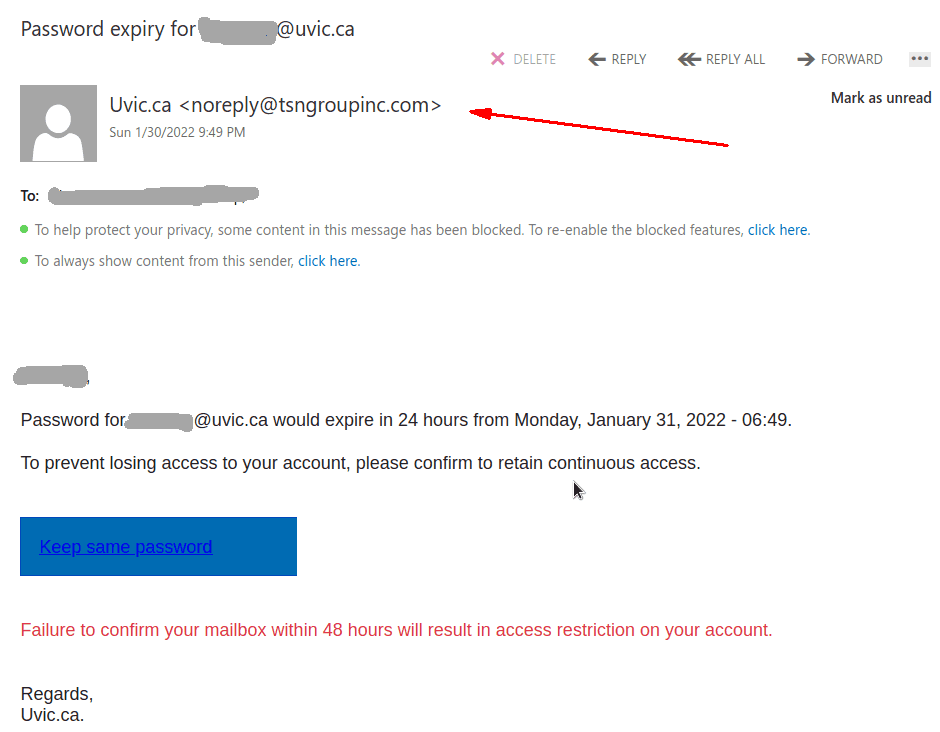
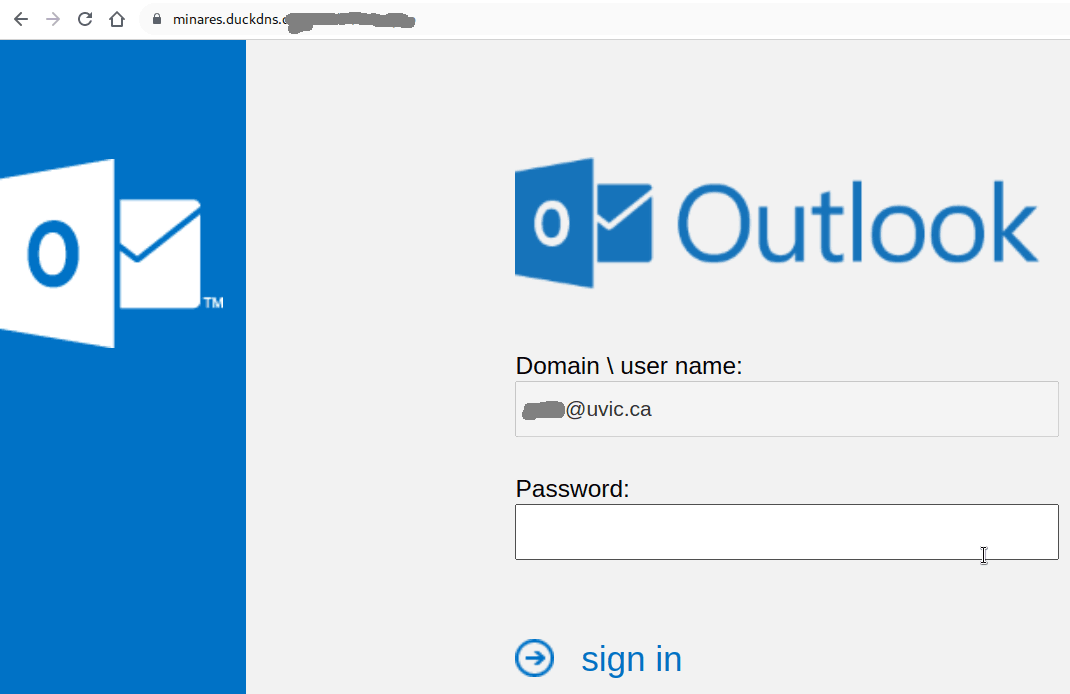
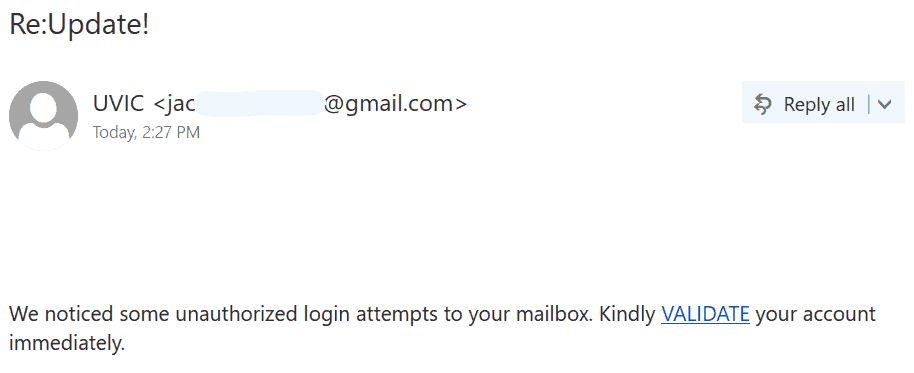
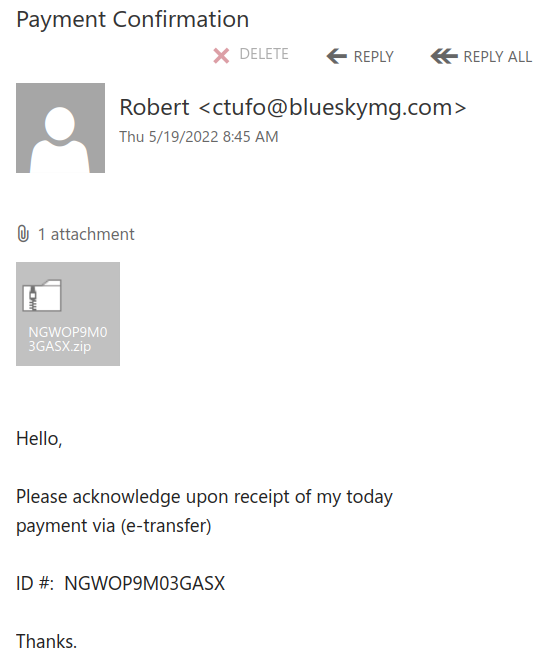
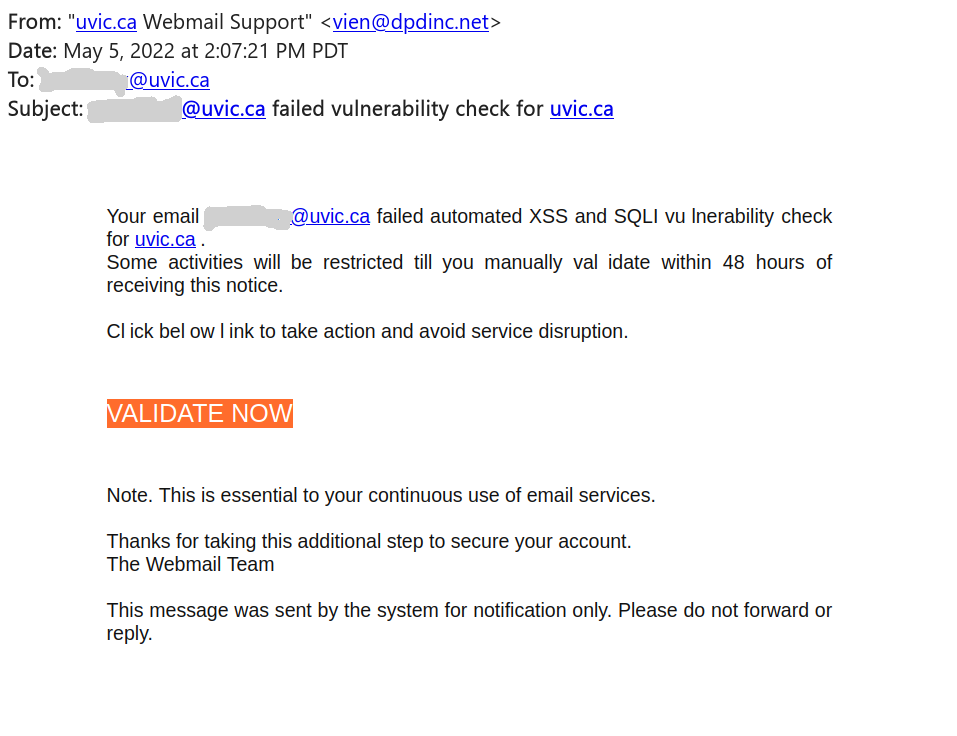
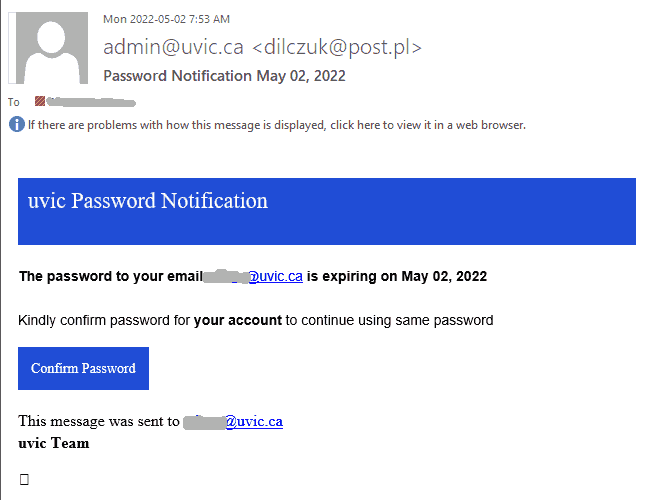
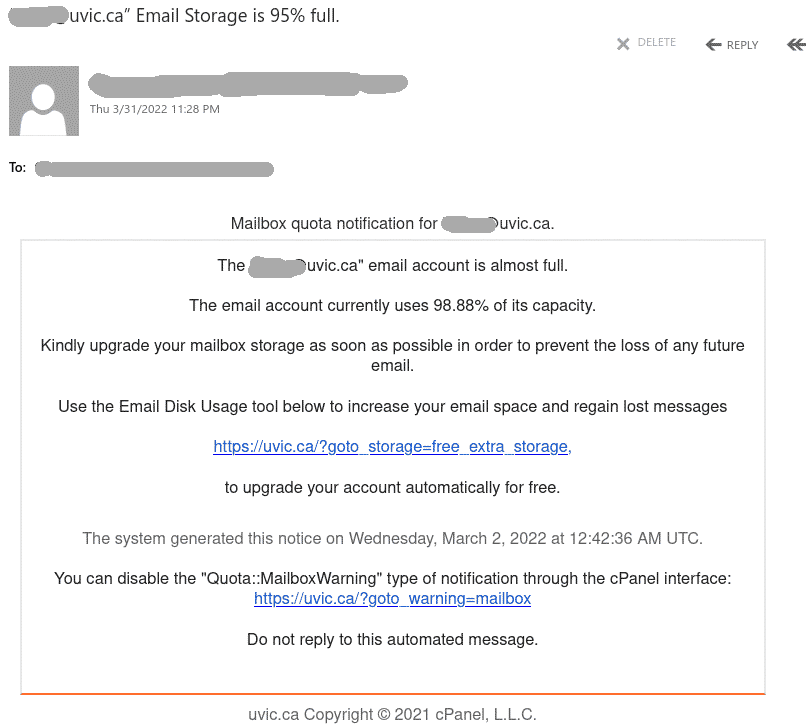
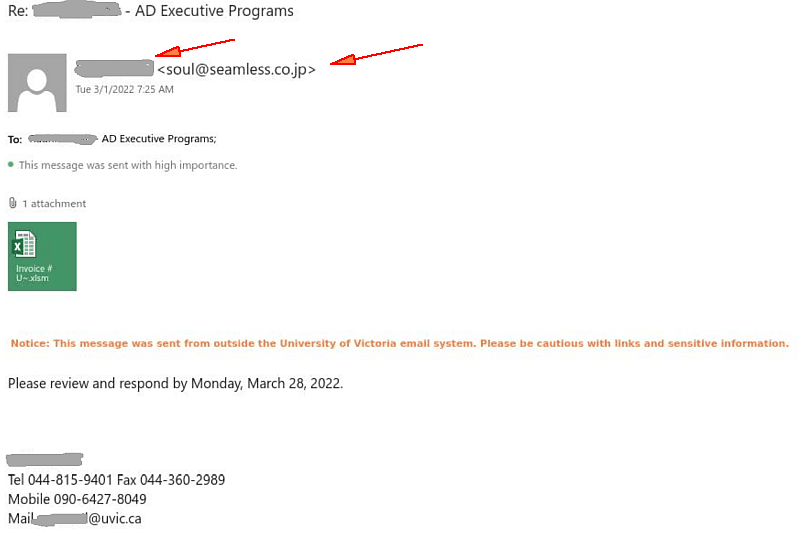
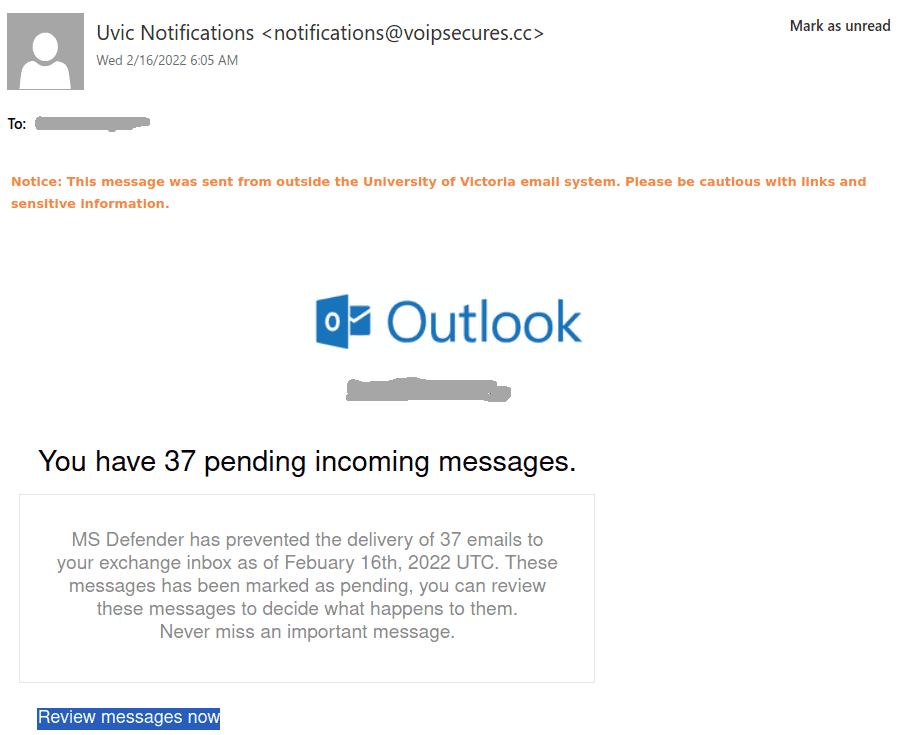
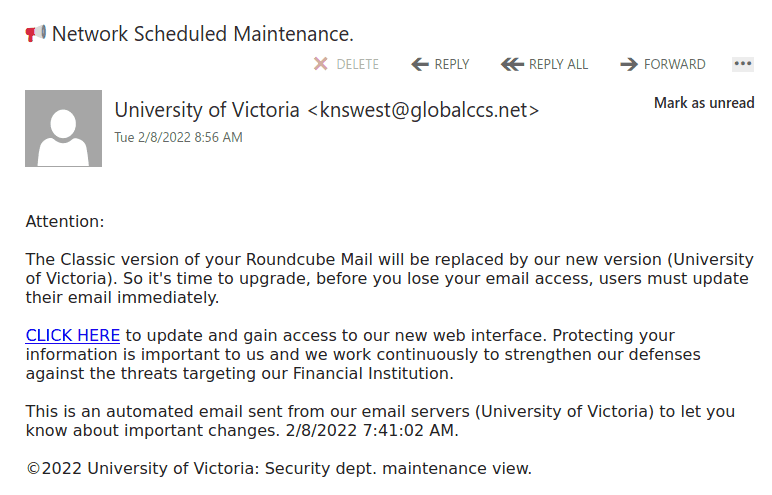
Many UVic mailboxes received this phish in the morning. It is a copy of what we had earlier this month.
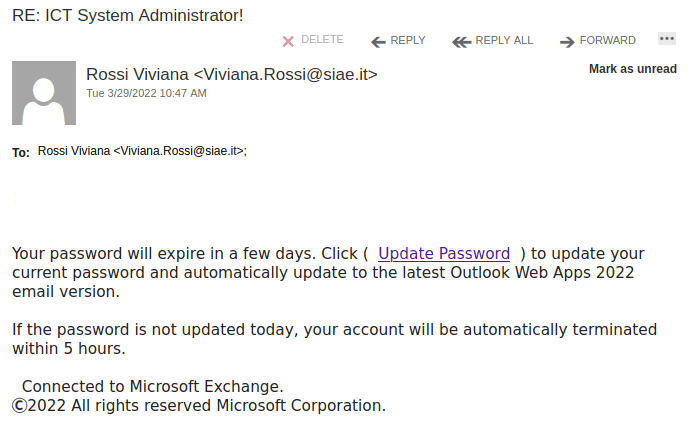
Again, it comes from a gmail sender and overall the short text does not make much sense – to validate (what?) because there were unauthorized login attempts?!?
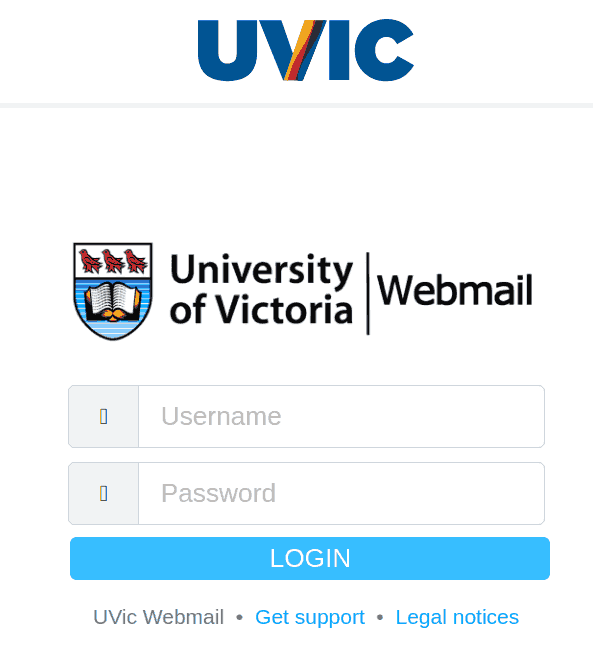
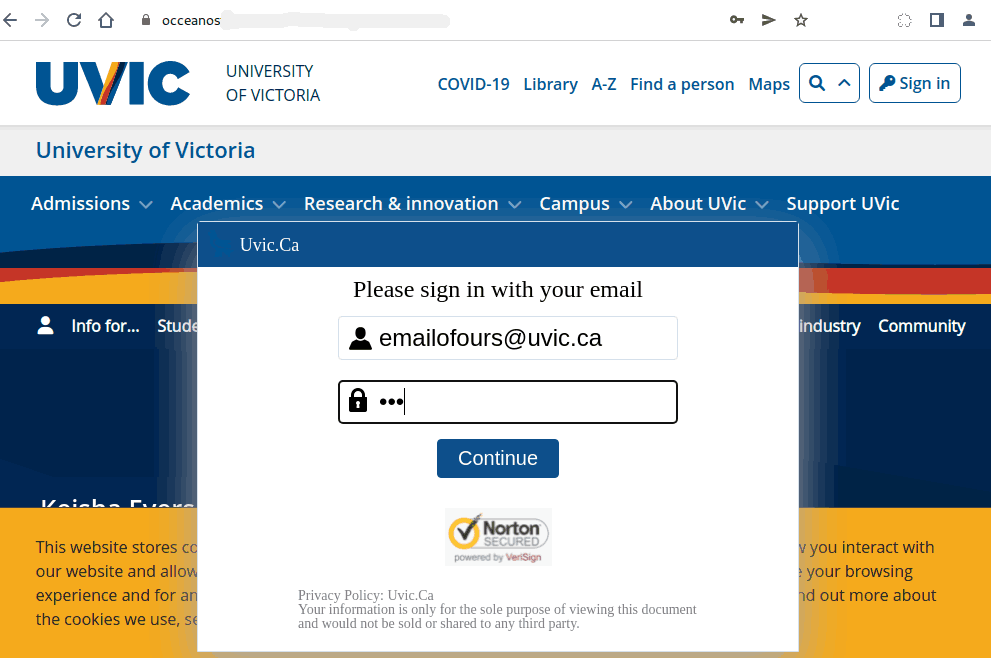
Their fake page contains UVic symbols though. Please do not be curious and do not open such links as they may contain malware to infect your computer instantly (Mac users – that applies to you too!)
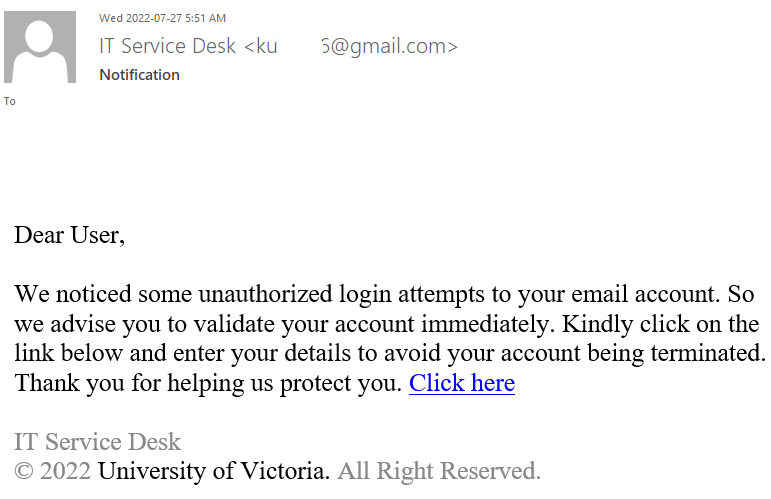







 ——————————————————————————–
——————————————————————————– ———————————————
———————————————