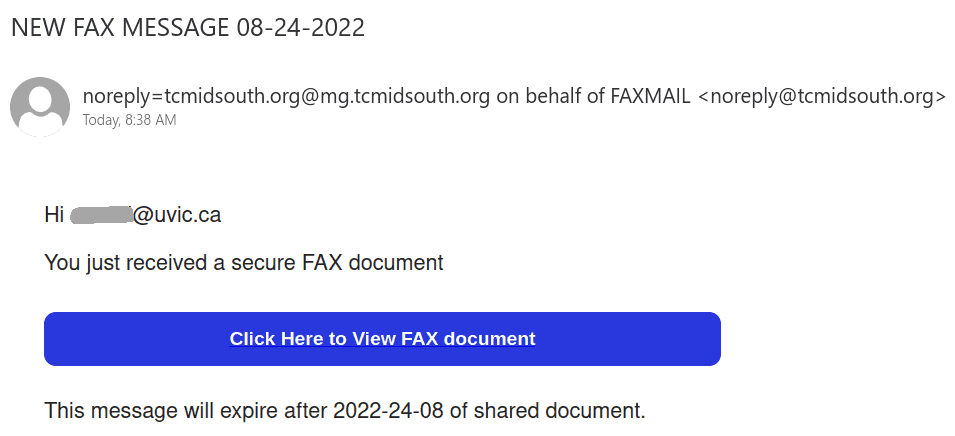
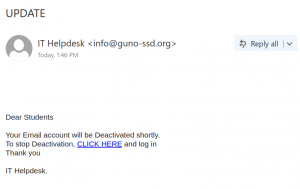
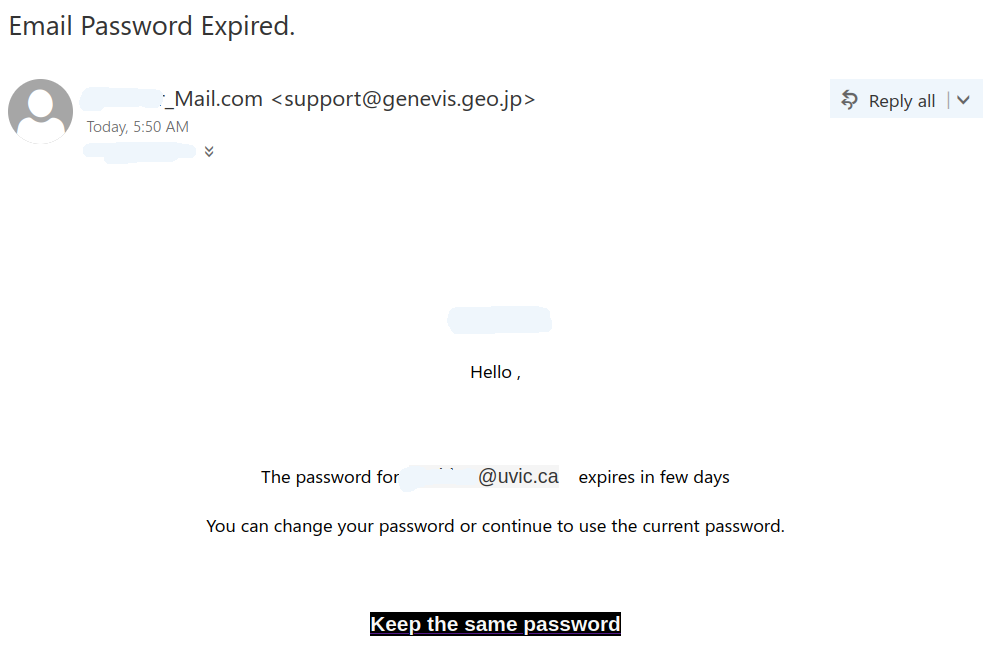
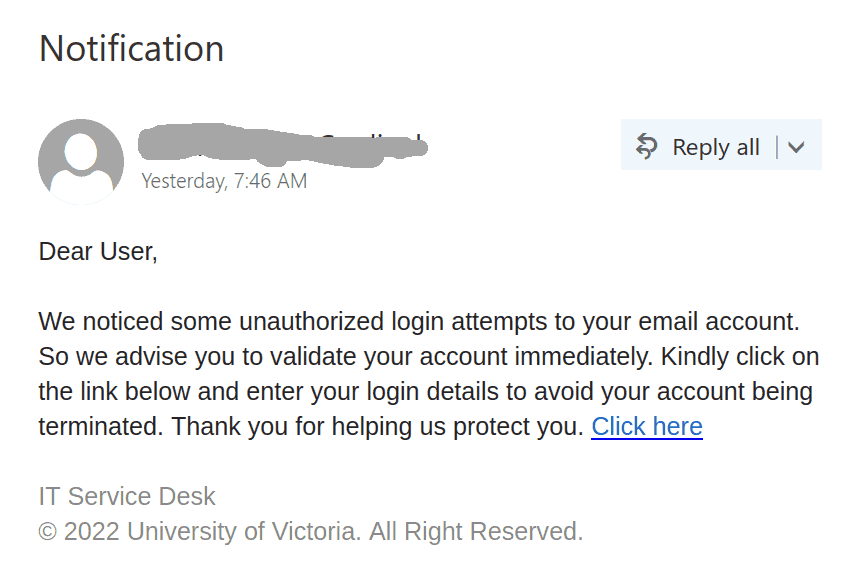
This phish is circulating today. It is virtually the same as our previous posting just a different sender. The sender is clearly external. The idea of keeping the same password doesn’t make sense. It is always better to change your password periodically with some new long phrase that you never used before. Our tips to choose a new password are published here:
https://www.uvic.ca/systems/support/loginspasswords/password/passwordtips.php
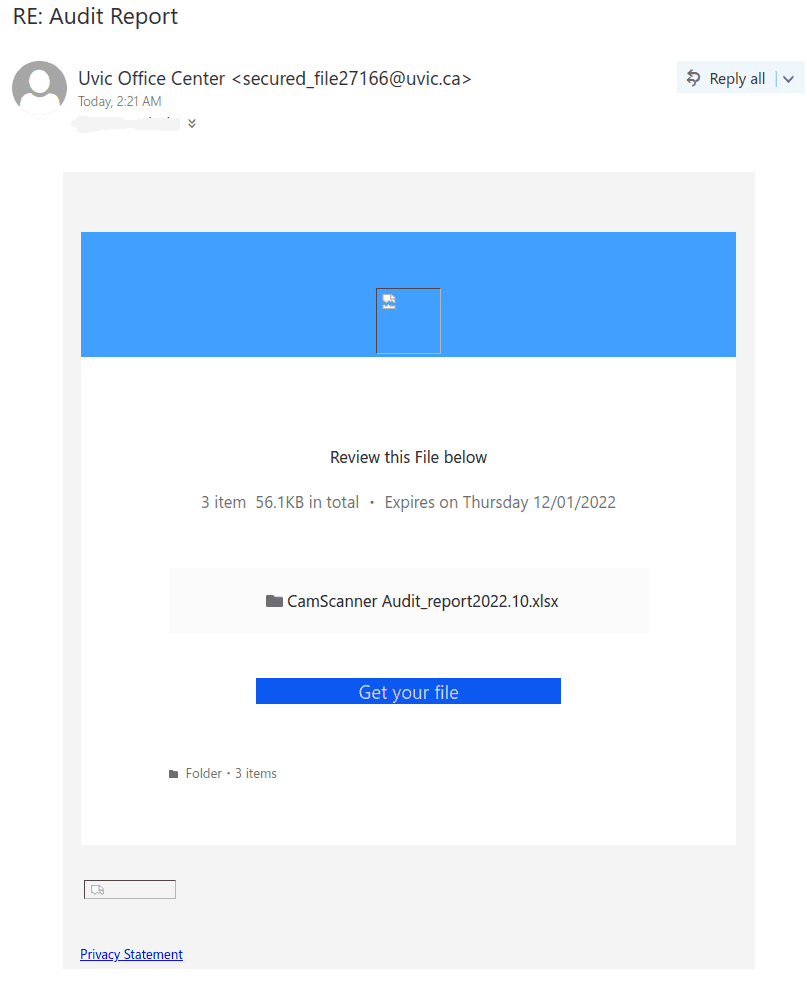
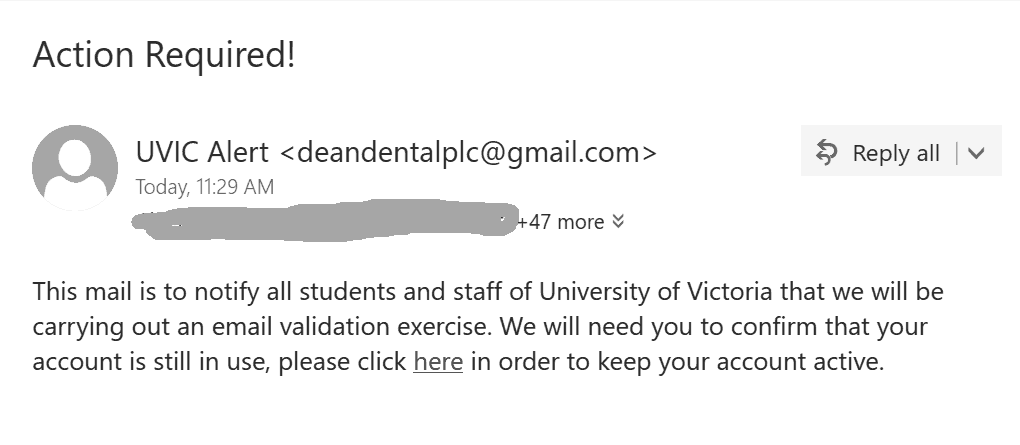
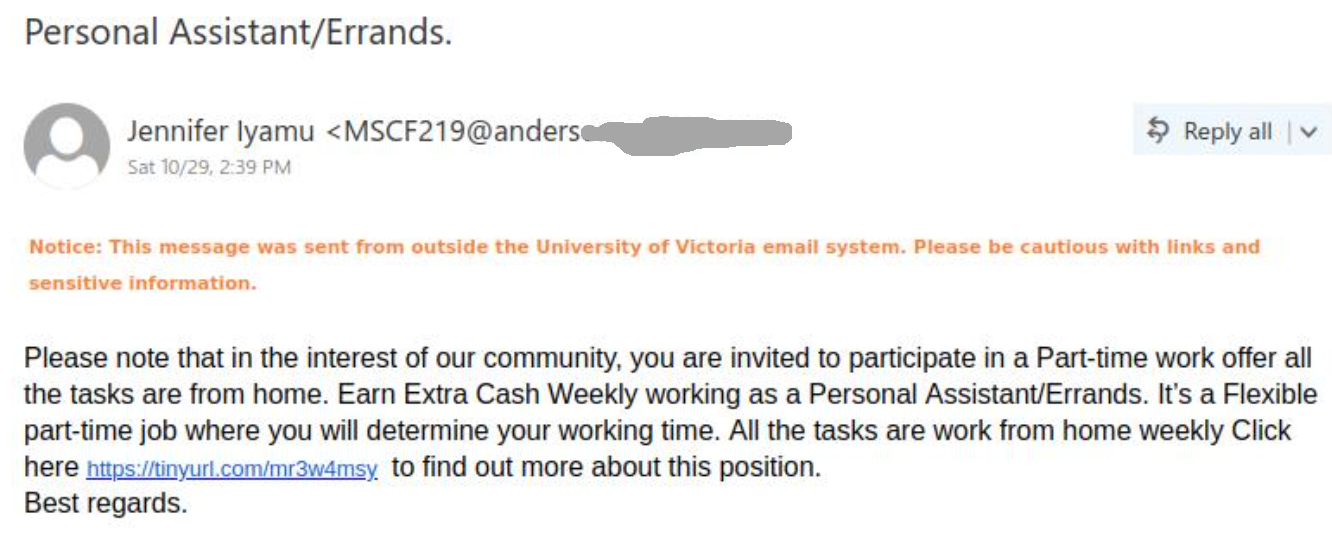
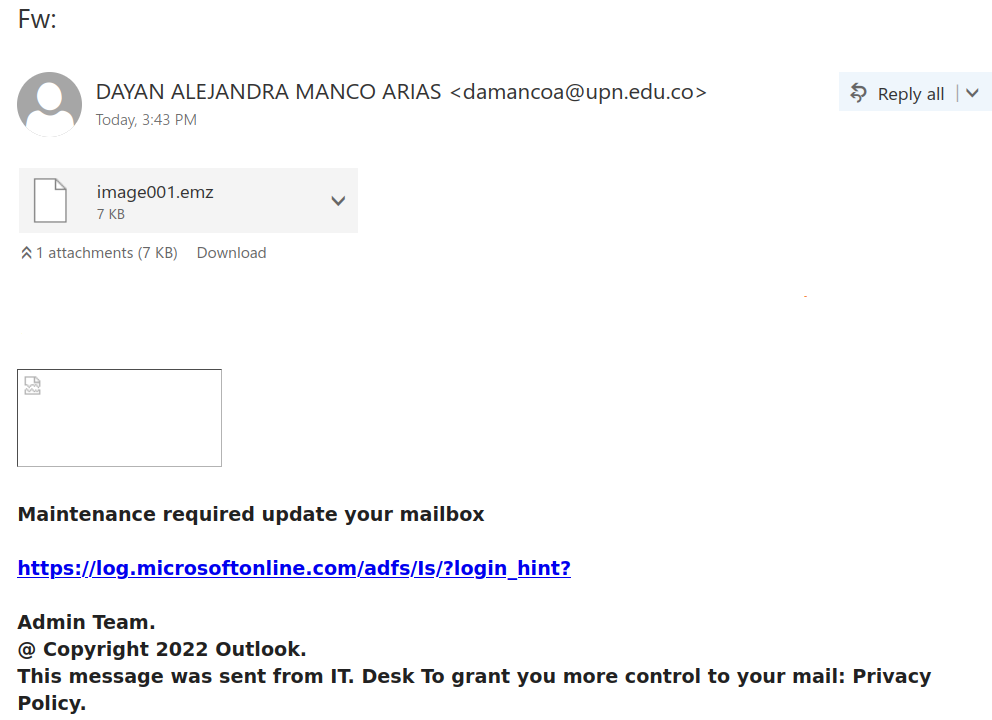
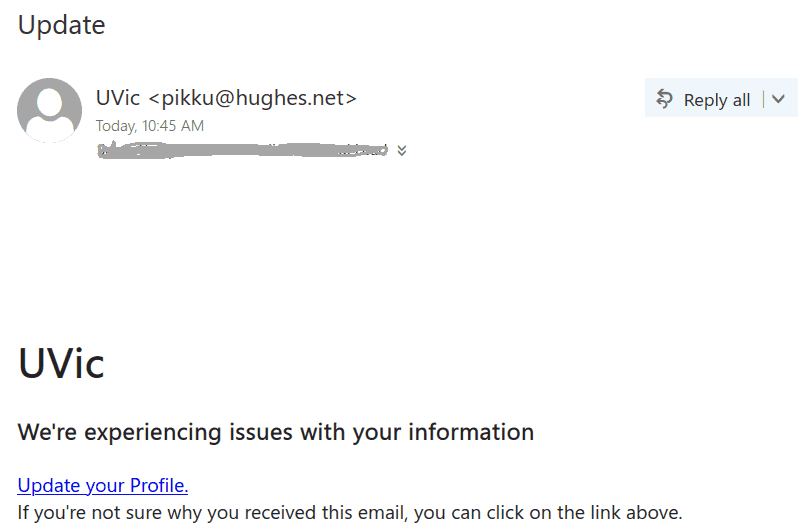
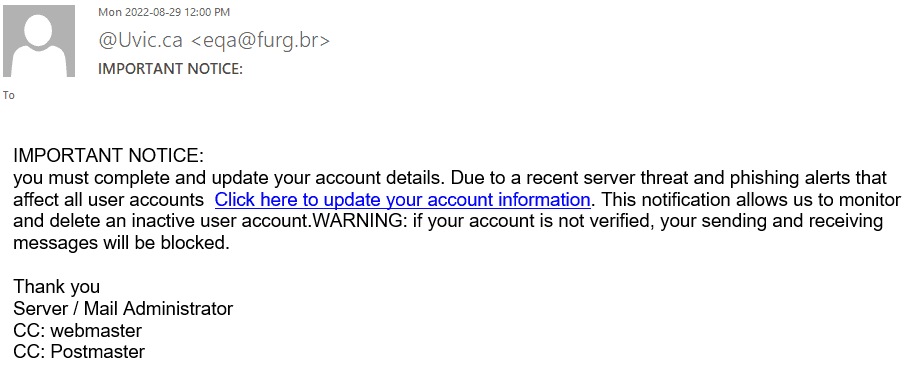
Here is a screenshot of the phish:
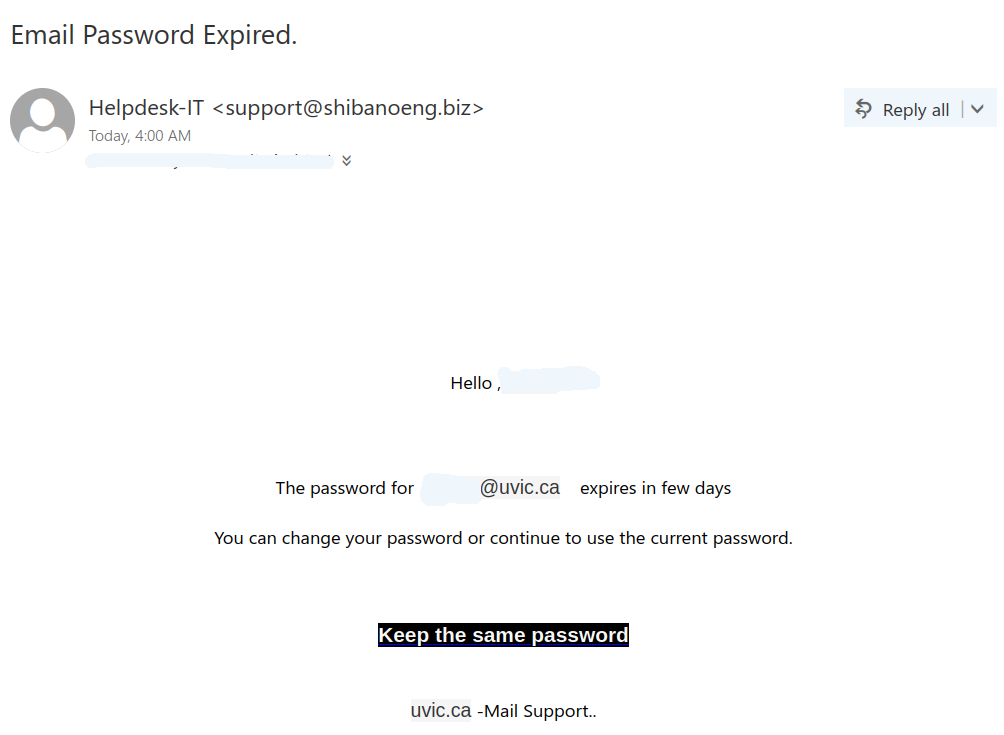
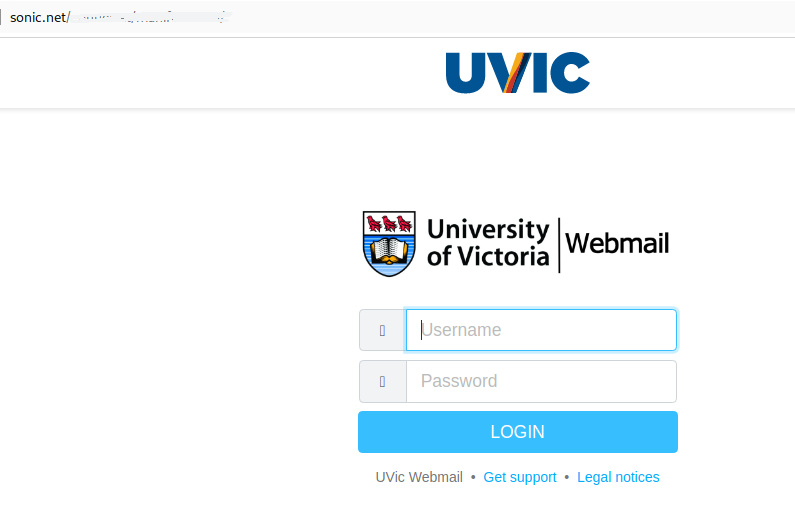
The goal is the same as usual – to steal your UVic credentials. For this purpose they created a fake UVic page – an exact copy of the real one. Please do not be curious and do not click these links, as sometimes they may contain malware to infect your computer instantly. Our experts open those in dedicated isolated environment.
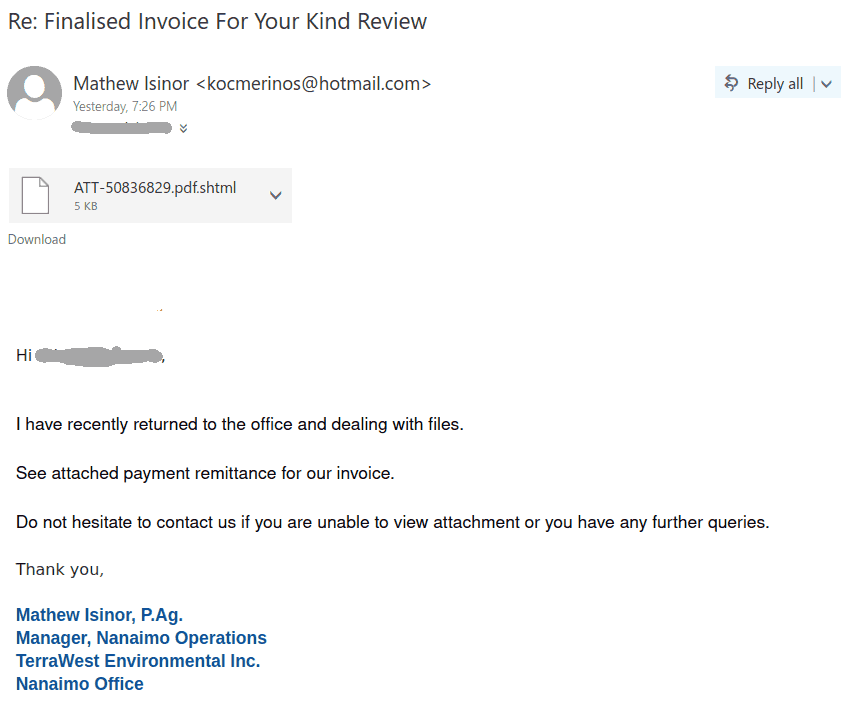

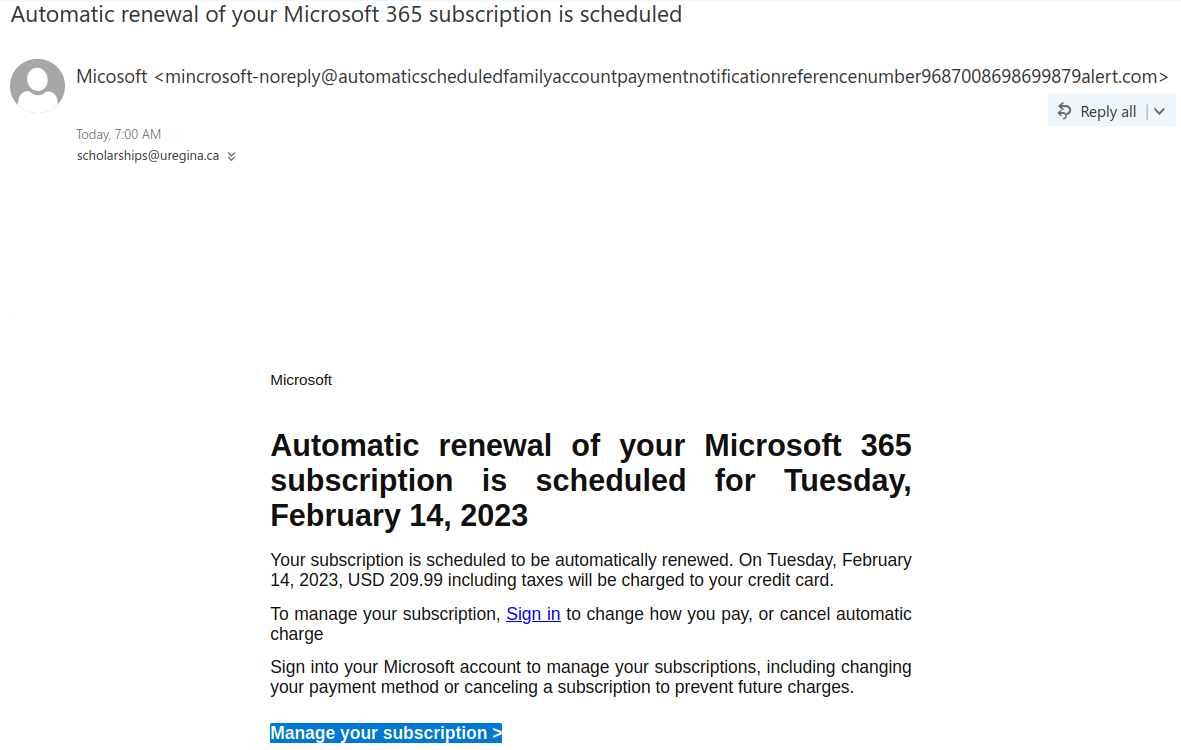



 ——————————————————————————
——————————————————————————