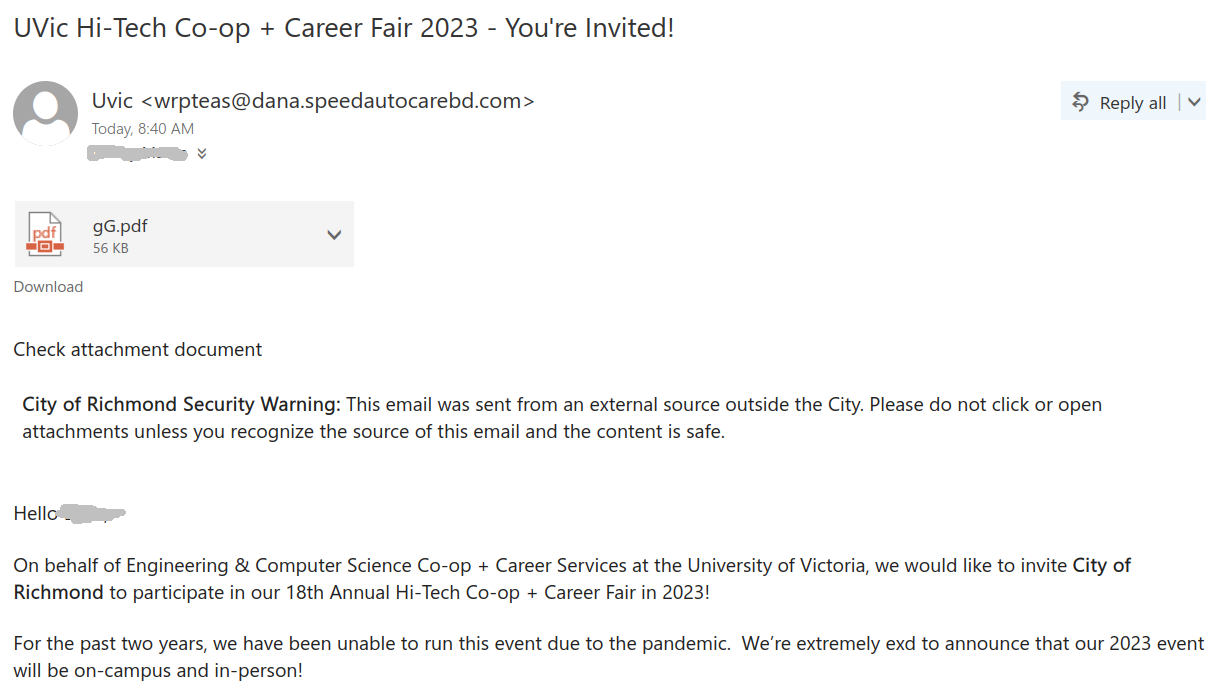
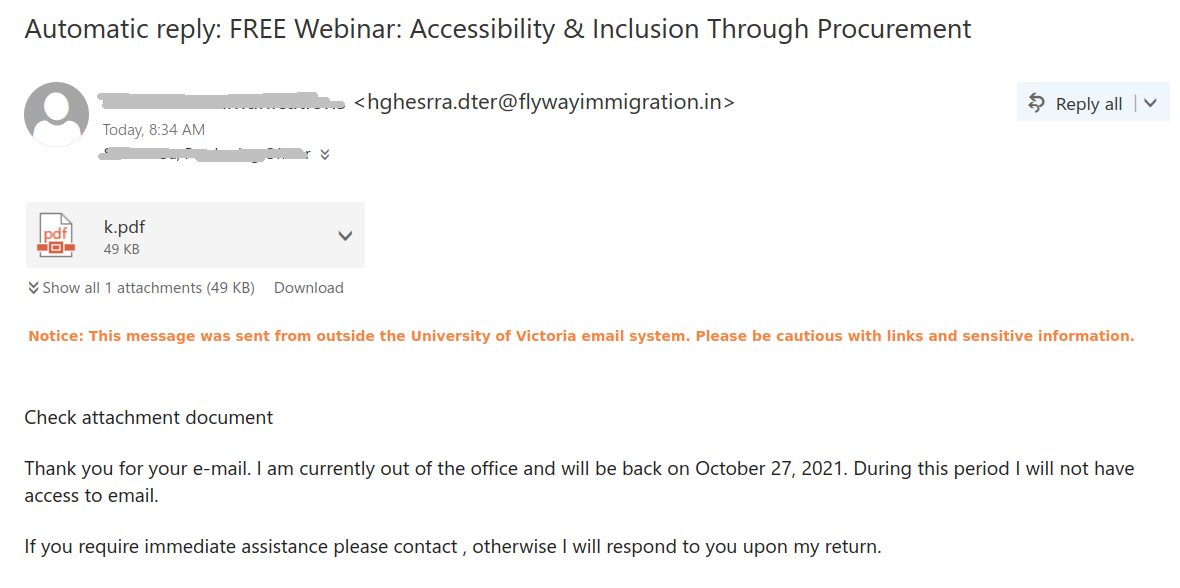
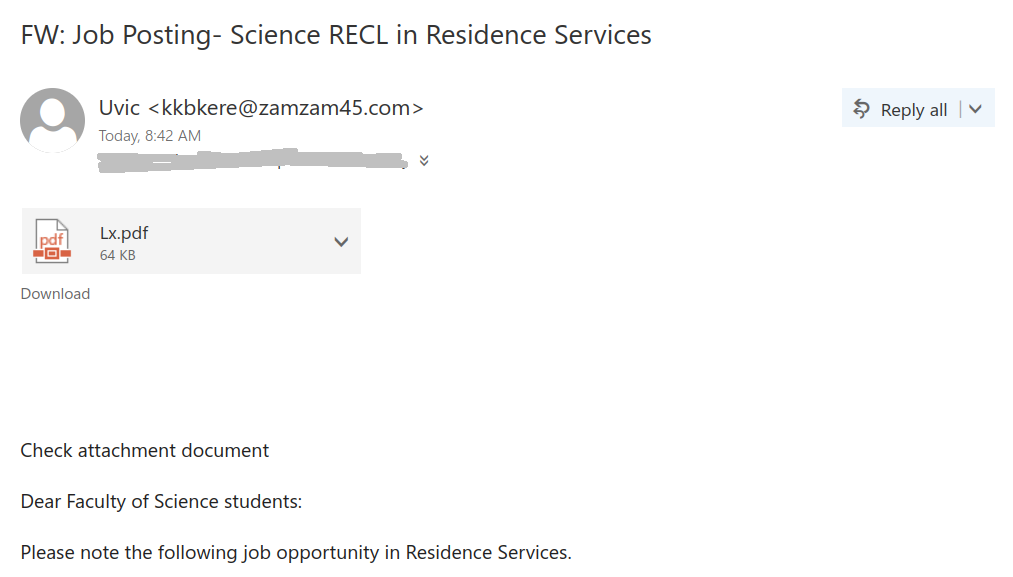
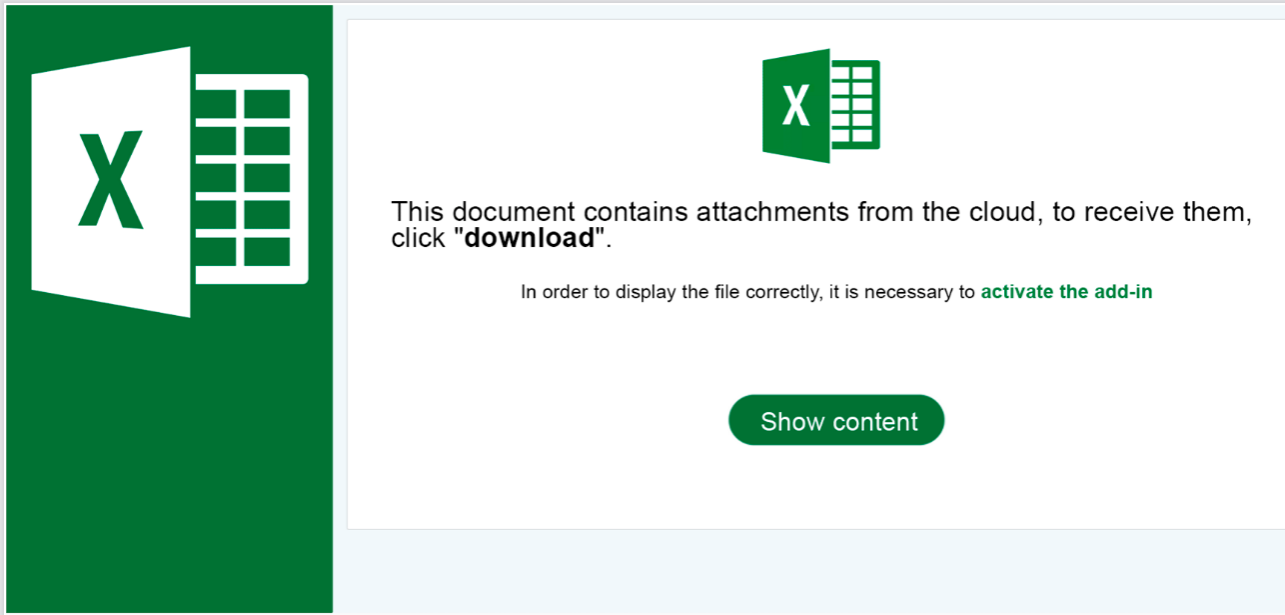
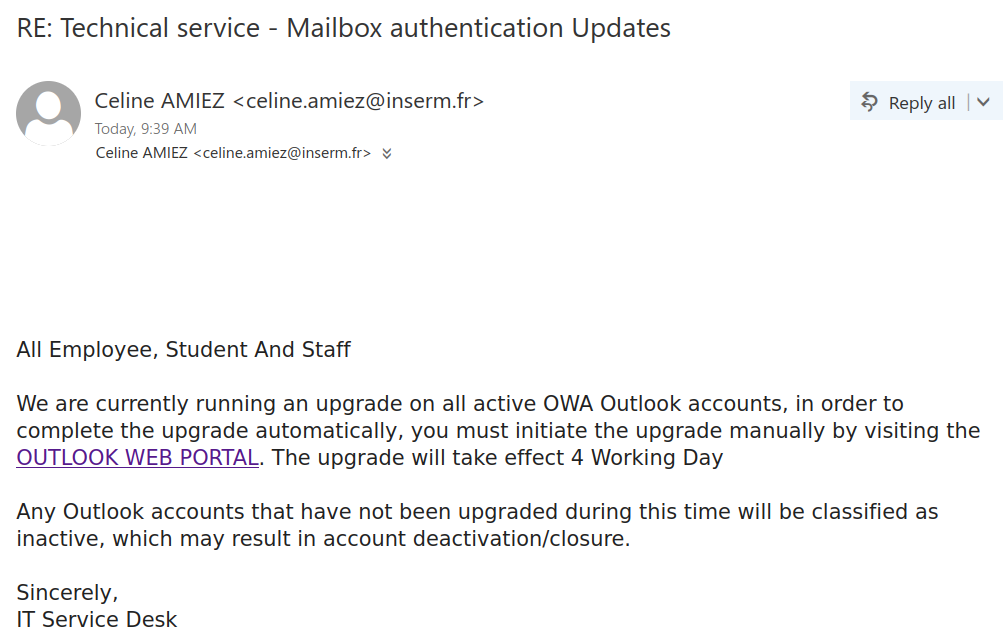
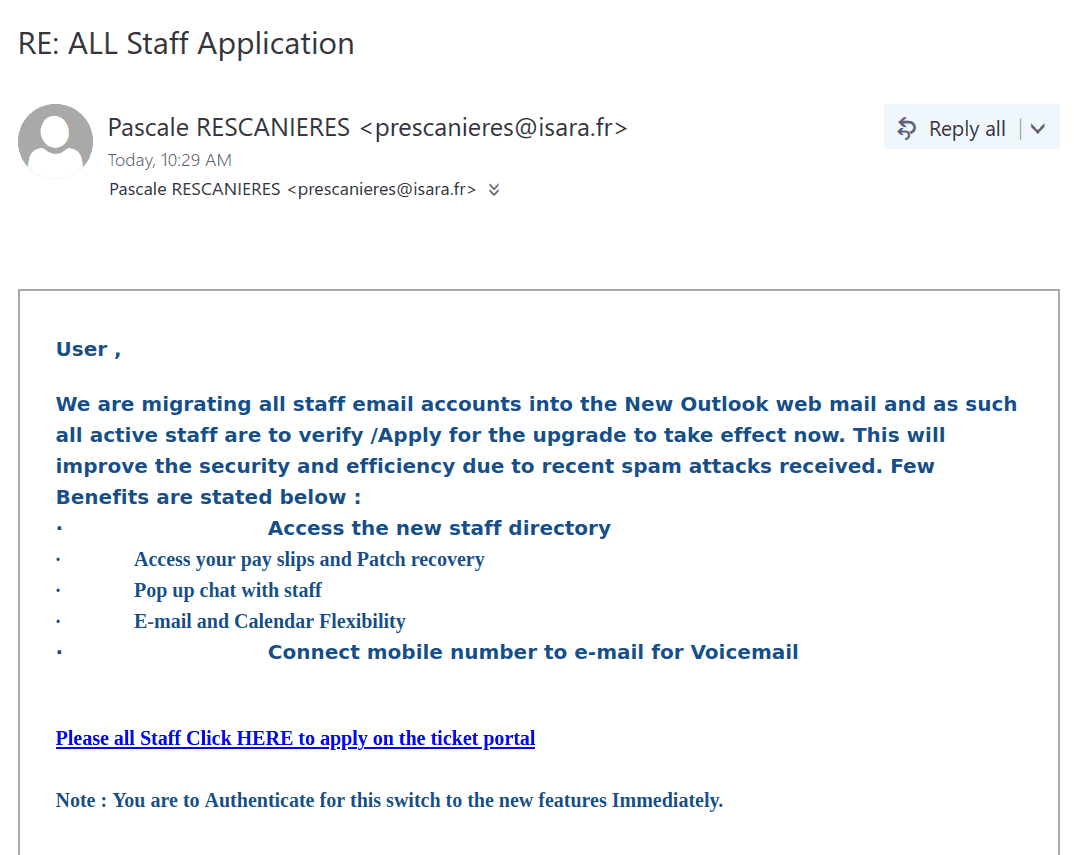
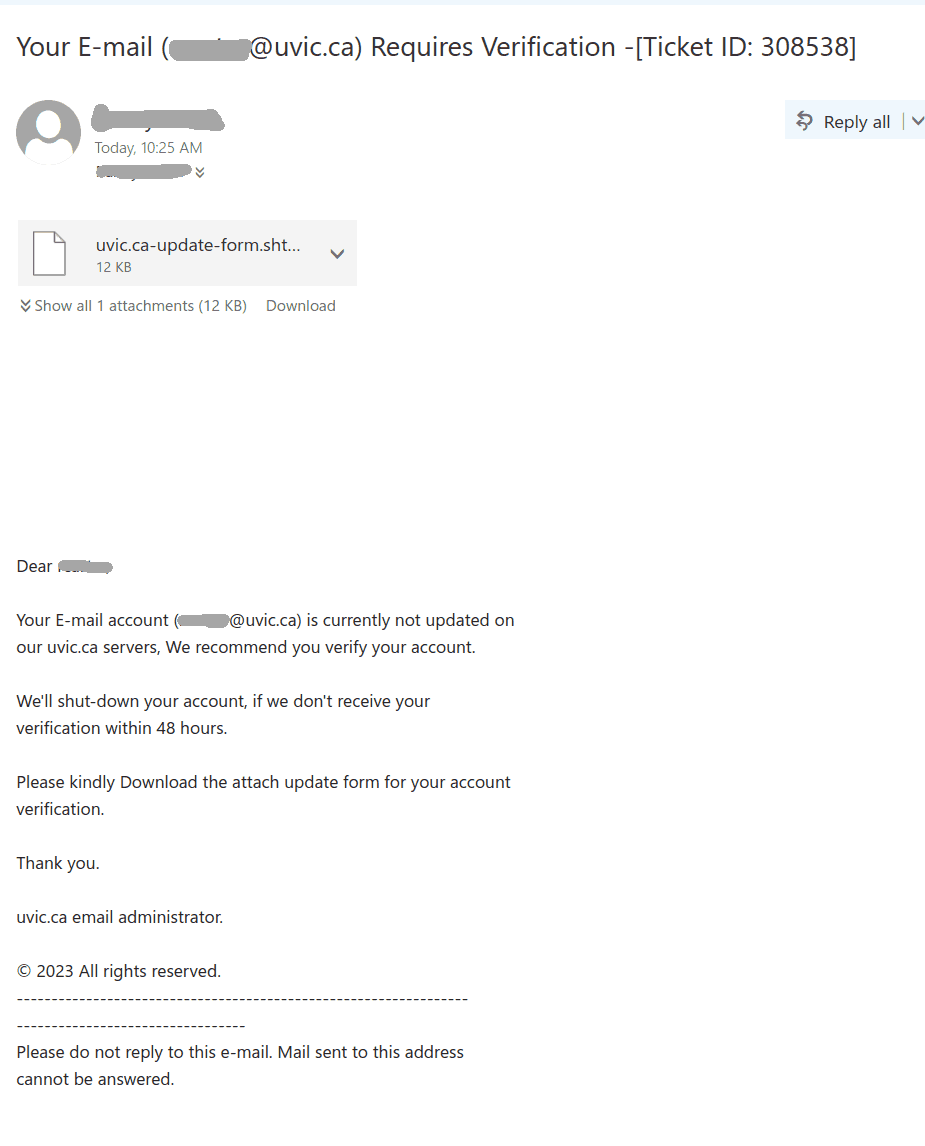
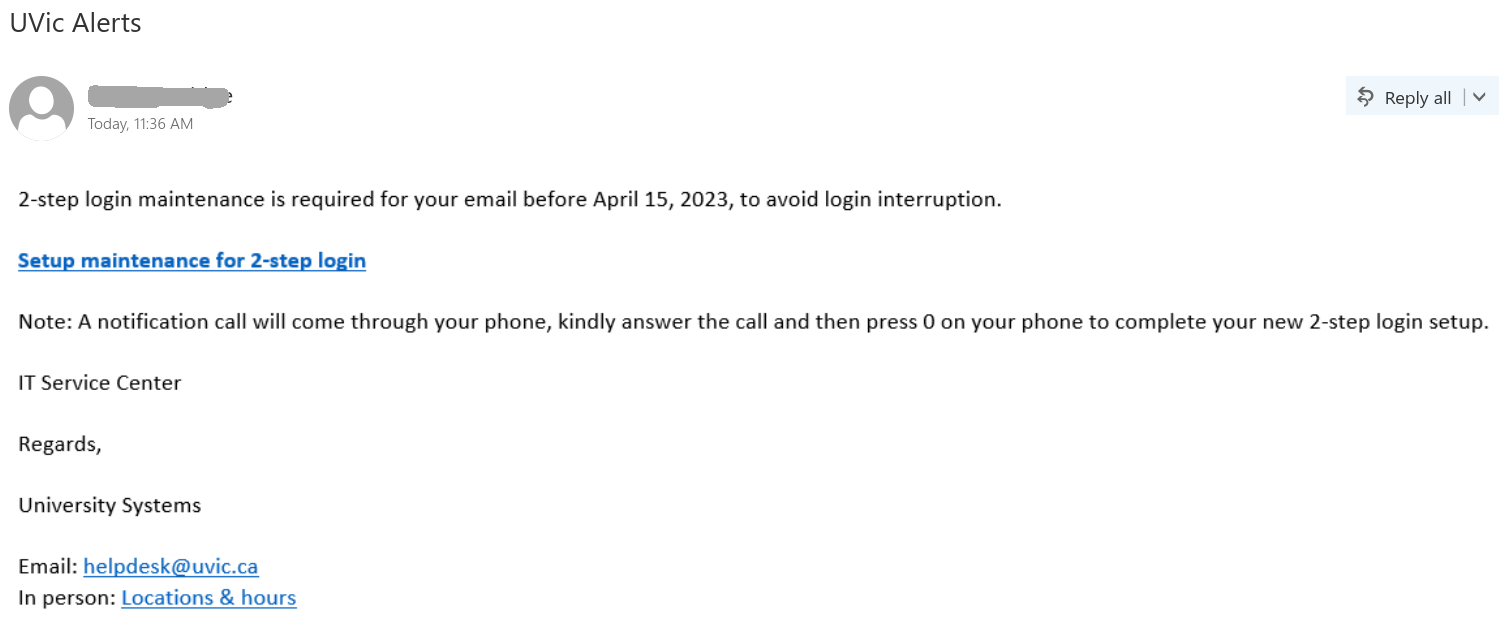
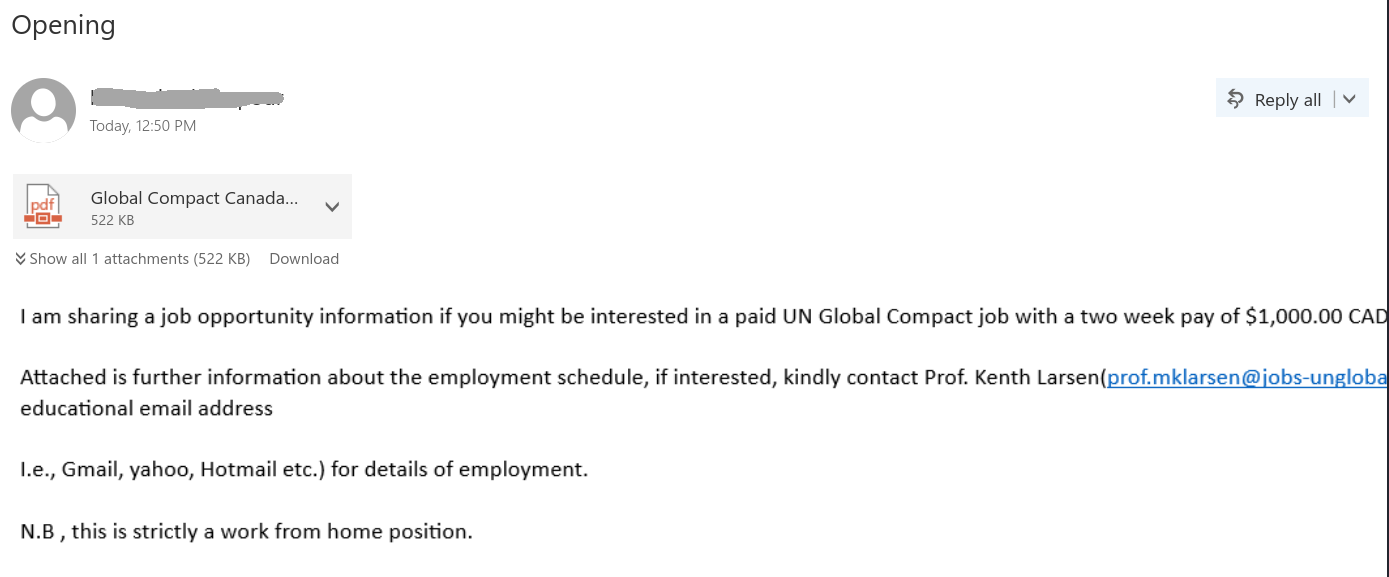
We received a report of an interaction with a scammer from an employee who was aware of the scam from the outset. We strongly advise against engaging with scammers, even ‘for fun’. Such interactions can inadvertently reveal valuable information, such as the active status of your email account, your work schedule, and more. We’ve redacted the name used by the scammer in this instance, as they were impersonating a real university professor.
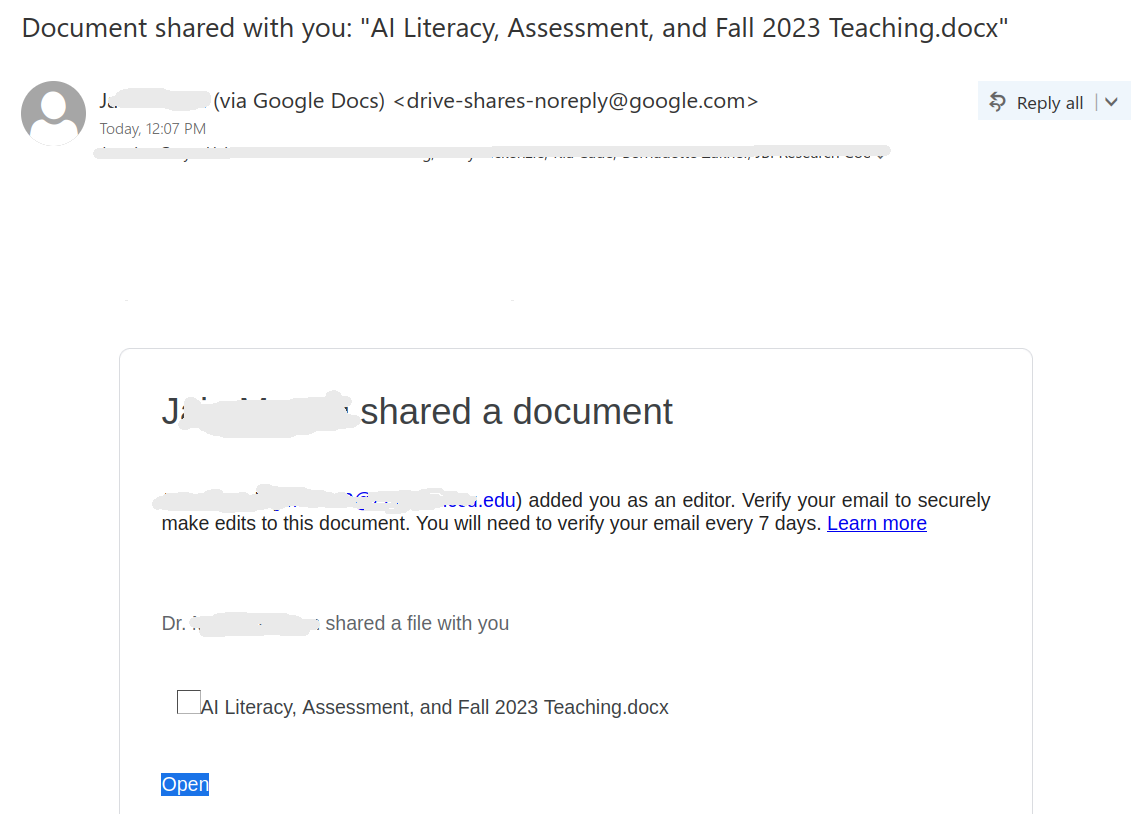
The thread begins with a succinct email body, the subject line merely containing the name of the impersonated professor, typically someone in an executive position such as a department chair, dean, or director.
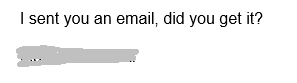
The employee responded as follows:
 At this juncture, many individuals might feel a twinge of guilt for overlooking the initial email. This is precisely the reaction the scammer is banking on, despite the fact that there was no previous email. The scammer swiftly replied, revealing their true intent:
At this juncture, many individuals might feel a twinge of guilt for overlooking the initial email. This is precisely the reaction the scammer is banking on, despite the fact that there was no previous email. The scammer swiftly replied, revealing their true intent:
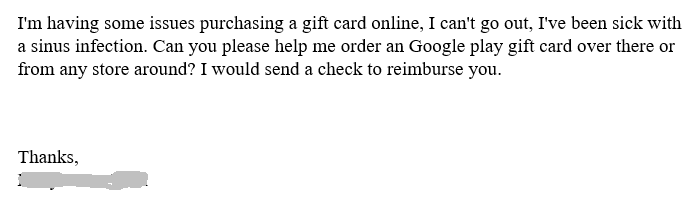 There’s always a reason why they can’t purchase the cards themselves. It could be a technical issue, illness, an ongoing meeting, or any number of pretexts.
There’s always a reason why they can’t purchase the cards themselves. It could be a technical issue, illness, an ongoing meeting, or any number of pretexts.
The employee responded:
 A scammer, realizing their ruse has been seen through, might typically abandon their efforts at this point. However, this scammer persisted, sticking to their script as shown below:
A scammer, realizing their ruse has been seen through, might typically abandon their efforts at this point. However, this scammer persisted, sticking to their script as shown below:
 Perhaps they believe persistence pays off statistically? That they might eventually convince a potential victim? Unfortunately, we do occasionally encounter victims who purchase gift cards and send photos of the scratched-off numbers to the scammer. This is another telltale sign. Since the scammer can’t physically collect the cards, they request photos of the ID numbers. It’s a good idea to discuss this scenario with your supervisor and confirm that they would never ask you to purchase gift cards.
Perhaps they believe persistence pays off statistically? That they might eventually convince a potential victim? Unfortunately, we do occasionally encounter victims who purchase gift cards and send photos of the scratched-off numbers to the scammer. This is another telltale sign. Since the scammer can’t physically collect the cards, they request photos of the ID numbers. It’s a good idea to discuss this scenario with your supervisor and confirm that they would never ask you to purchase gift cards.
Remember: It’s always best to avoid giving scammers any information, no matter how insignificant it may seem.