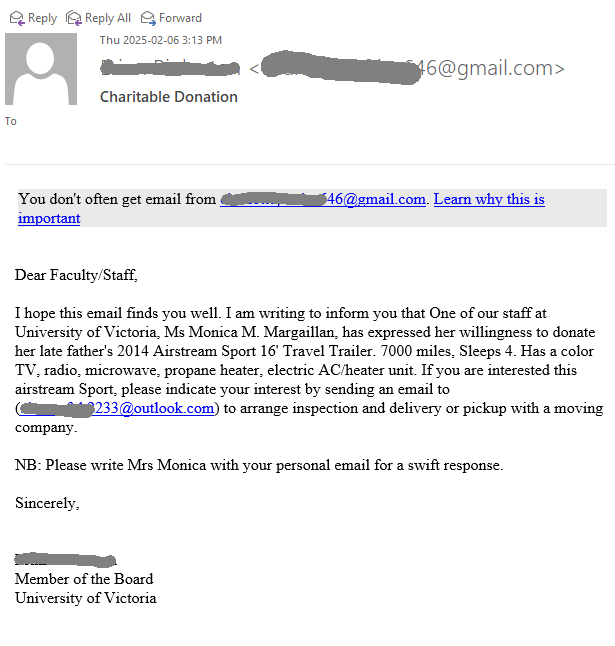
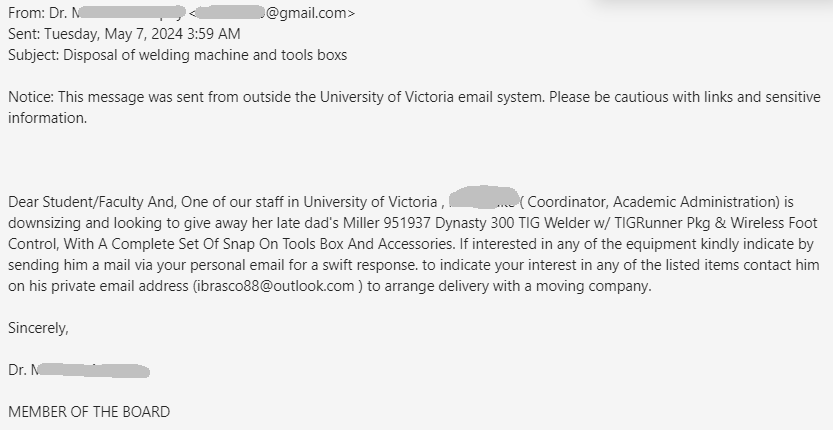
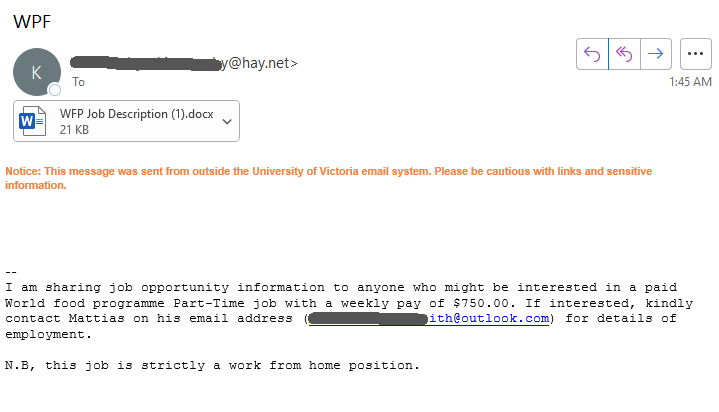
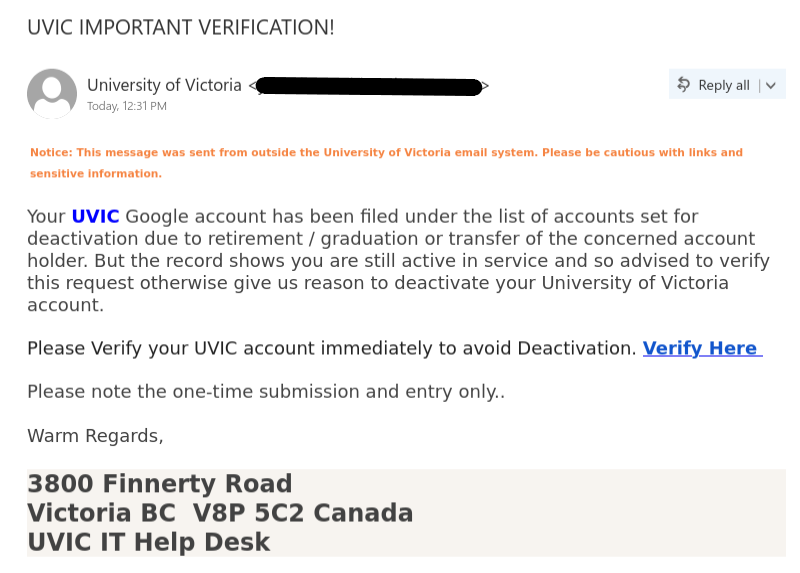
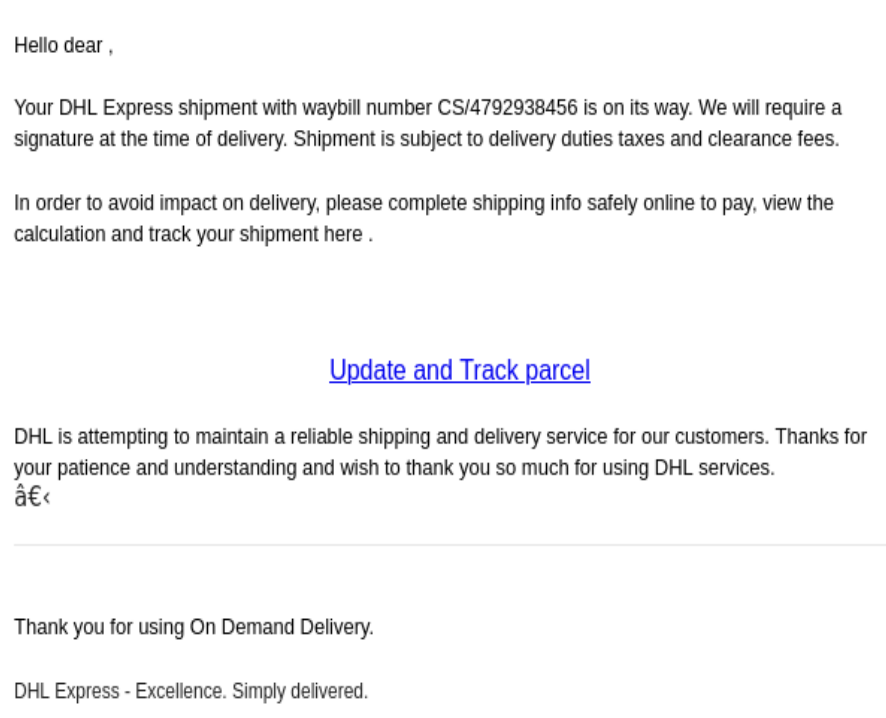
With students back on campus, these kinds of scams will continue to target them. Most of the emails with the subject “Students seeking Jobs should check below” were properly identified by the antispam filters and ended up in the junk folders of Exchange mailboxes.
These emails typically contain a short text in the body of the message, while the actual scam is in an attached text file. The body may look like this:

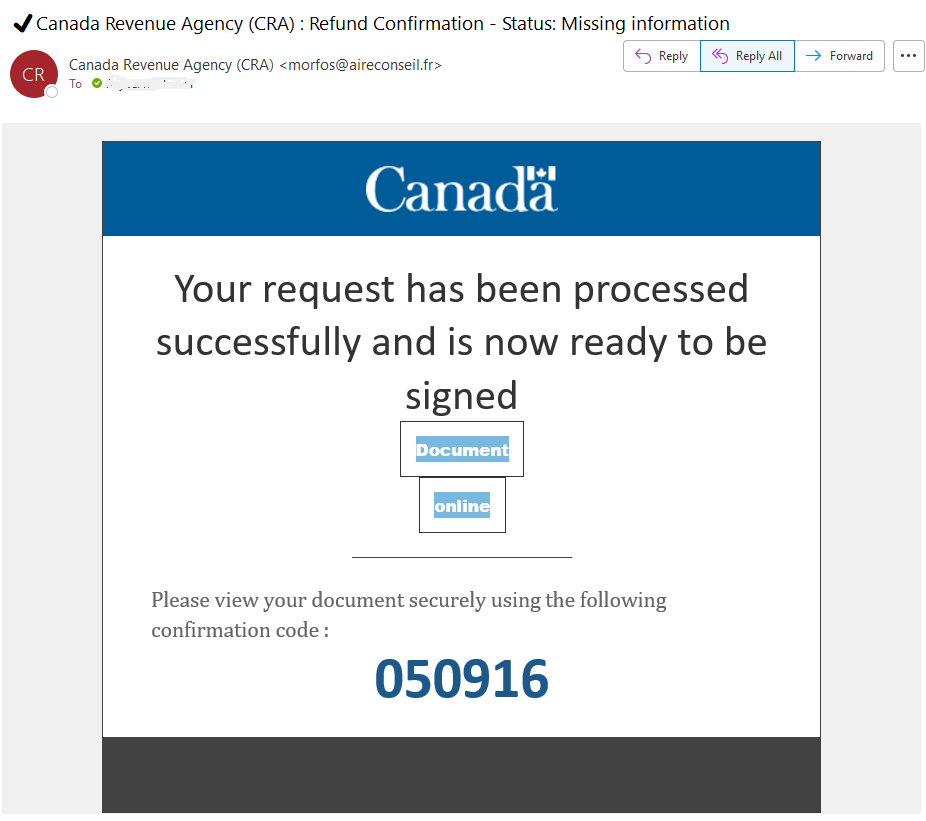
These emails may come from different sender addresses (typically Gmail).
The text file contains a rather long description of the “job and benefits,” which includes typing mistakes and, as usual, sounds too good to be true.
Please do not reply to such scammers (even for fun!). If in doubt, ask the helpdesk or your supervisor.
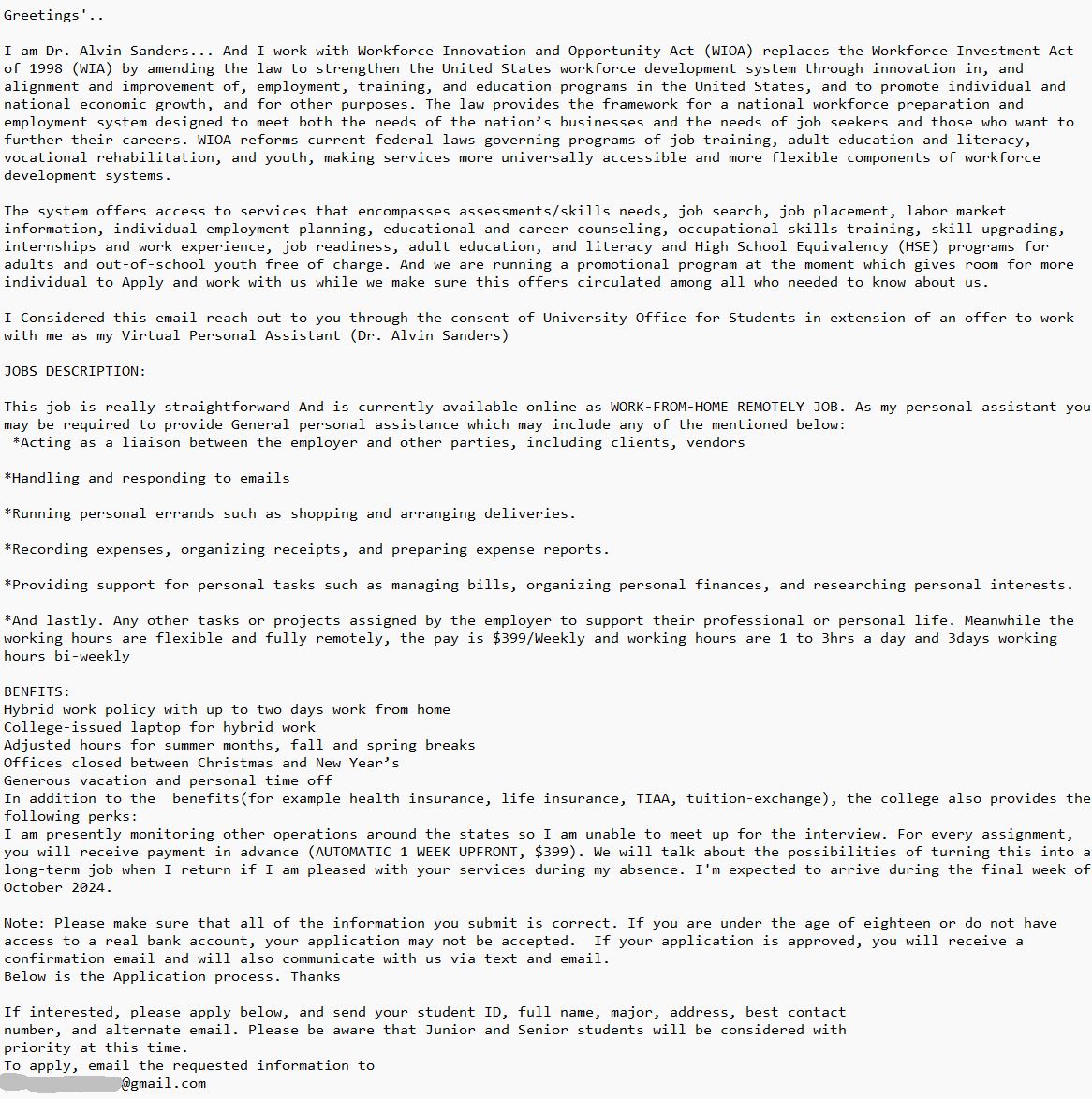
The transcripts of the body of the email and the attachment are listed below:
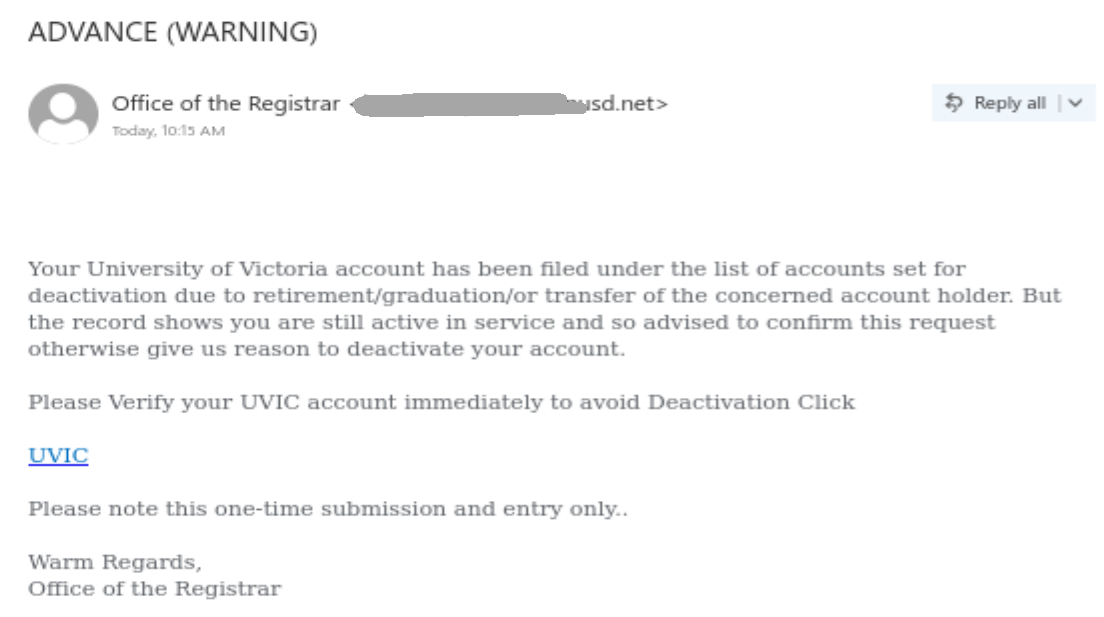
University Of Victoria has resources in place to help you succeed in your career and your relationships. work for $(four Hundred weekly and study. If interested, see attached
Regards.
the attachment:
Greetings’..
I am Dr. Alvin Sanders… And I work with Workforce Innovation and Opportunity Act (WIOA) replaces the Workforce Investment Act of 1998 (WIA) by amending the law to strengthen the United States workforce development system through innovation in, and alignment and improvement of, employment, training, and education programs in the United States, and to promote individual and national economic growth, and for other purposes. The law provides the framework for a national workforce preparation and employment system designed to meet both the needs of the nation’s businesses and the needs of job seekers and those who want to further their careers. WIOA reforms current federal laws governing programs of job training, adult education and literacy, vocational rehabilitation, and youth, making services more universally accessible and more flexible components of workforce development systems.
The system offers access to services that encompasses assessments/skills needs, job search, job placement, labor market information, individual employment planning, educational and career counseling, occupational skills training, skill upgrading, internships and work experience, job readiness, adult education, and literacy and High School Equivalency (HSE) programs for adults and out-of-school youth free of charge. And we are running a promotional program at the moment which gives room for more individual to Apply and work with us while we make sure this offers circulated among all who needed to know about us.
I Considered this email reach out to you through the consent of University Office for Students in extension of an offer to work with me as my Virtual Personal Assistant (Dr. Alvin Sanders)
JOBS DESCRIPTION:
This job is really straightforward And is currently available online as WORK-FROM-HOME REMOTELY JOB. As my personal assistant you may be required to provide General personal assistance which may include any of the mentioned below:
*Acting as a liaison between the employer and other parties, including clients, vendors
*Handling and responding to emails
*Running personal errands such as shopping and arranging deliveries.
*Recording expenses, organizing receipts, and preparing expense reports.
*Providing support for personal tasks such as managing bills, organizing personal finances, and researching personal interests.
*And lastly. Any other tasks or projects assigned by the employer to support their professional or personal life. Meanwhile the working hours are flexible and fully remotely, the pay is $399/Weekly and working hours are 1 to 3hrs a day and 3days working hours bi-weekly
BENFITS:
Hybrid work policy with up to two days work from home
College-issued laptop for hybrid work
Adjusted hours for summer months, fall and spring breaks
Offices closed between Christmas and New Year’s
Generous vacation and personal time off
In addition to the benefits(for example health insurance, life insurance, TIAA, tuition-exchange), the college also provides the following perks:
I am presently monitoring other operations around the states so I am unable to meet up for the interview. For every assignment, you will receive payment in advance (AUTOMATIC 1 WEEK UPFRONT, $399). We will talk about the possibilities of turning this into a long-term job when I return if I am pleased with your services during my absence. I’m expected to arrive during the final week of October 2024.
Note: Please make sure that all of the information you submit is correct. If you are under the age of eighteen or do not have access to a real bank account, your application may not be accepted. If your application is approved, you will receive a confirmation email and will also communicate with us via text and email.
Below is the Application process. Thanks
If interested, please apply below, and send your student ID, full name, major, address, best contact
number, and alternate email. Please be aware that Junior and Senior students will be considered with
priority at this time.
To apply, email the requested information to
<redacted>