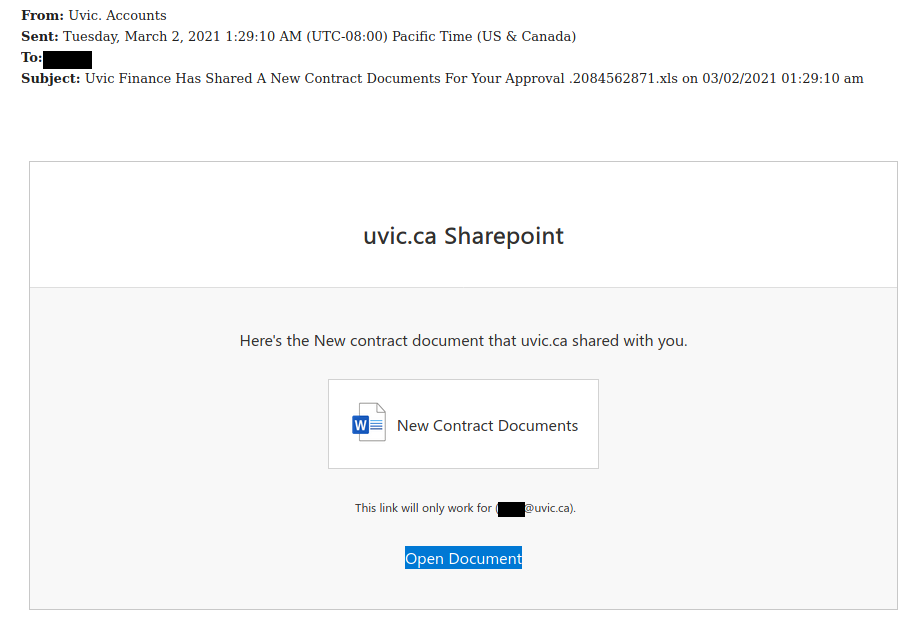
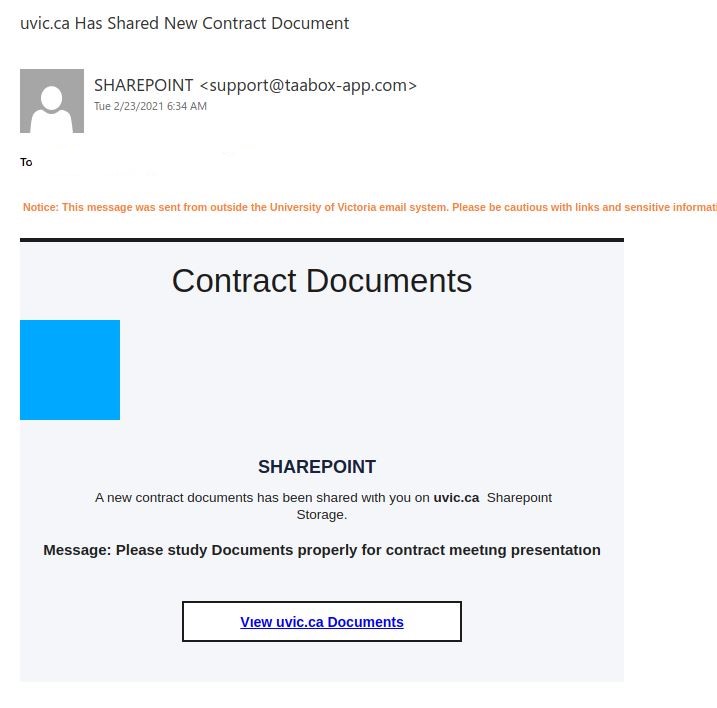
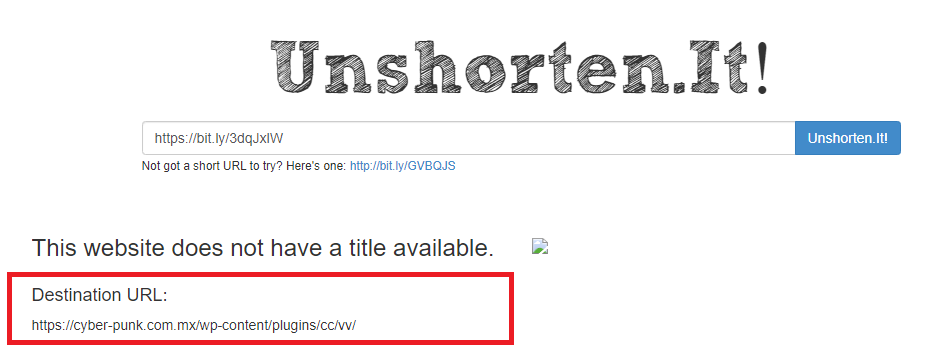
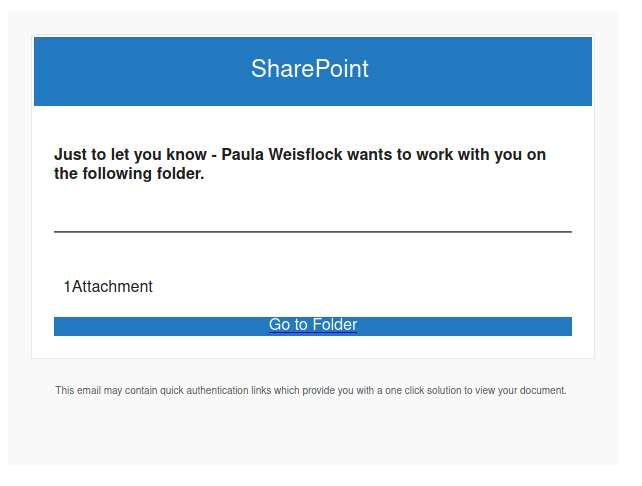
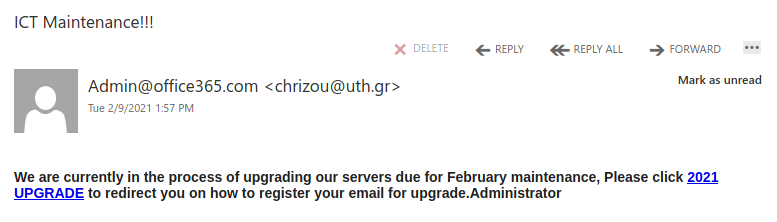
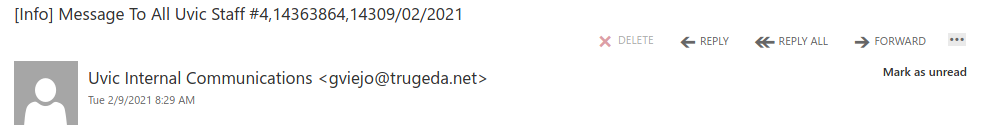
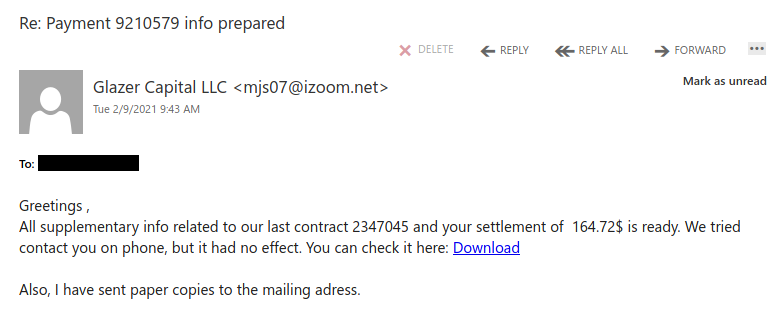
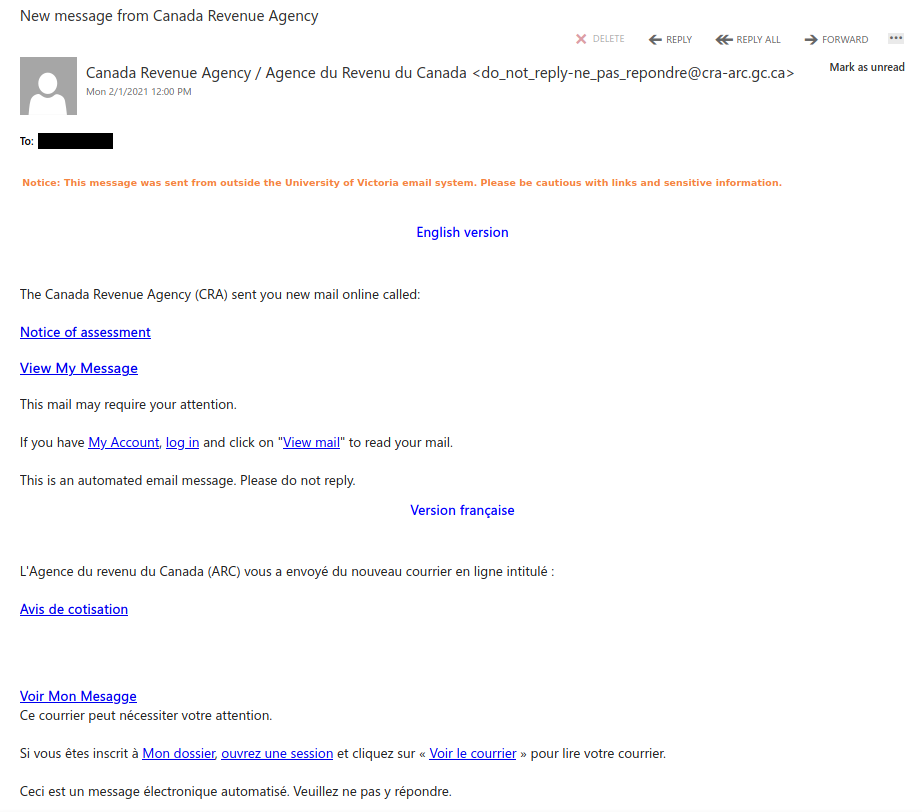
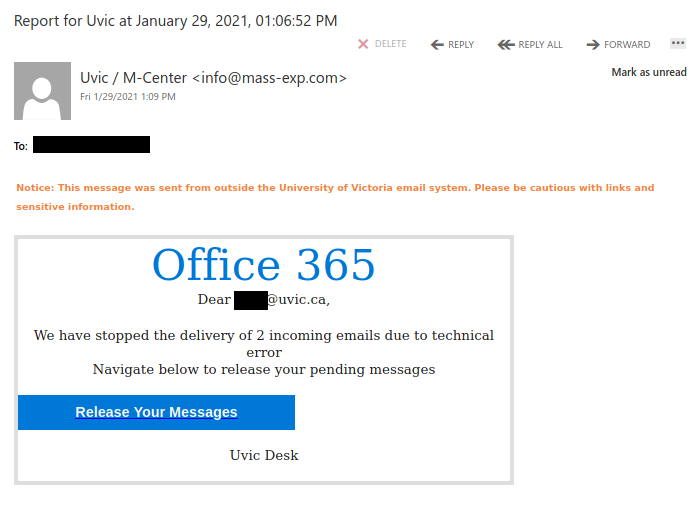
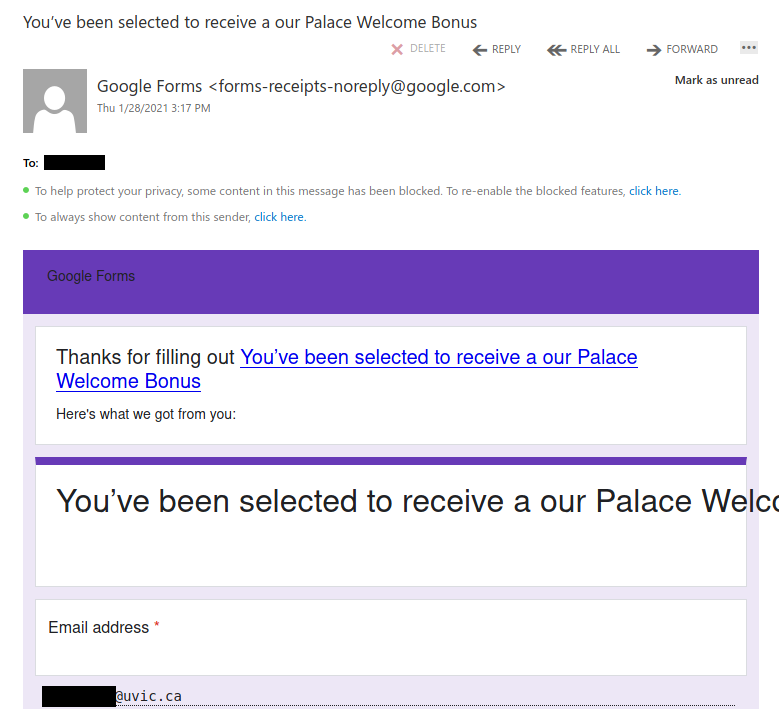
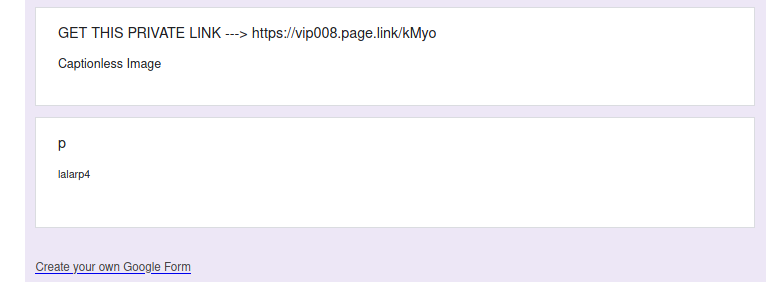
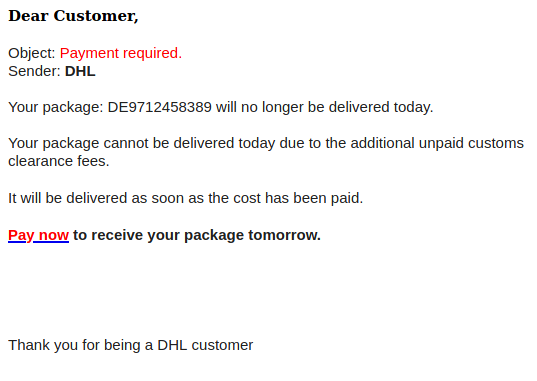
This is a spoof phish; the phisher tried to make this email look like it came from a UVic sender but it really came from an external source. The second half of the subject line varies between recipients but follows the same pattern. Hovering over the links would show that they do not go to UVic SharePoint and should not be clicked.
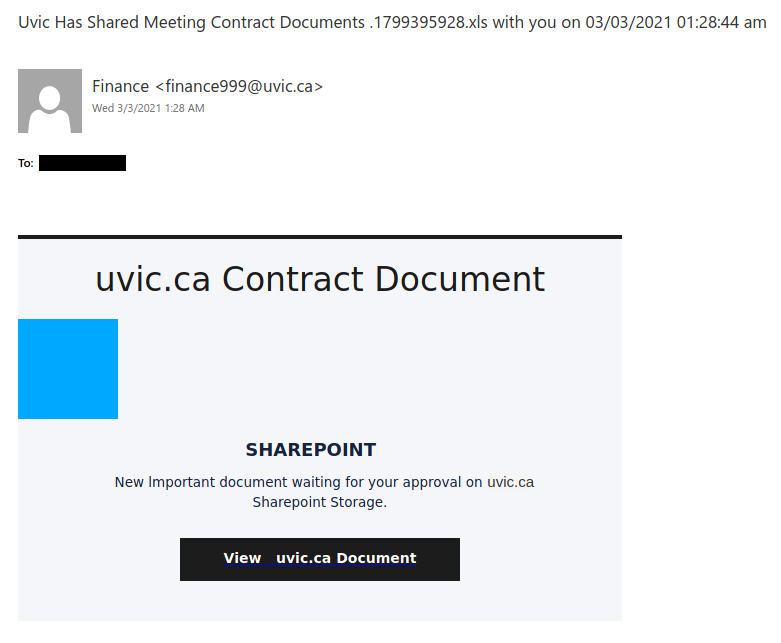
A few people received the variant below. This version had a spoofed sender of accounts@uvic.ca.