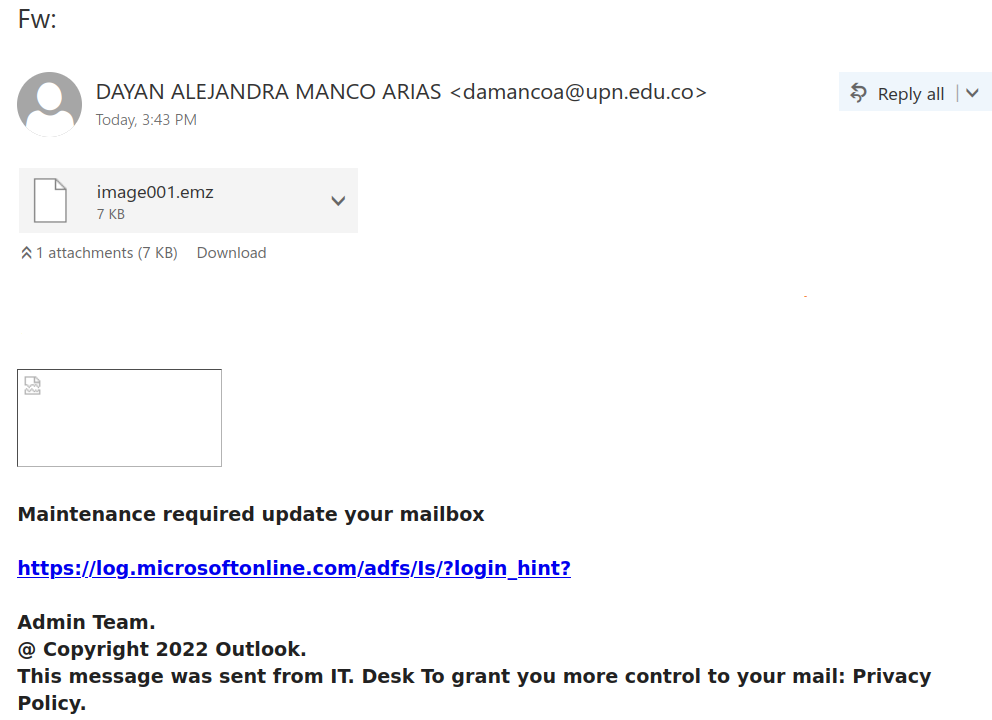
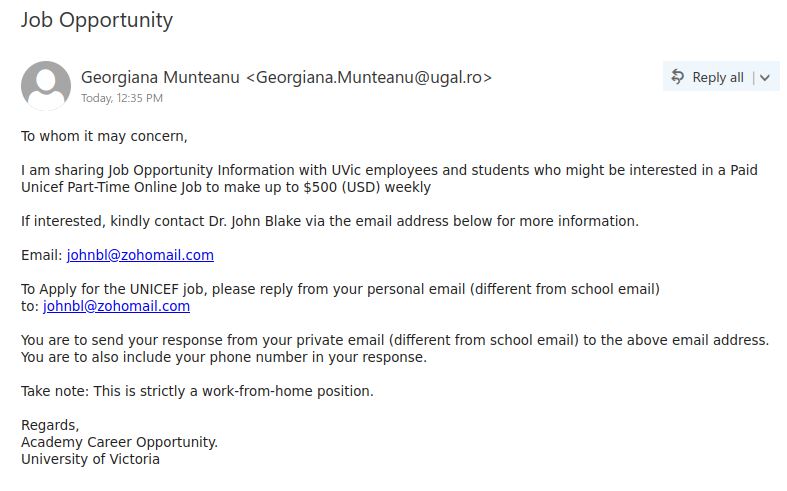
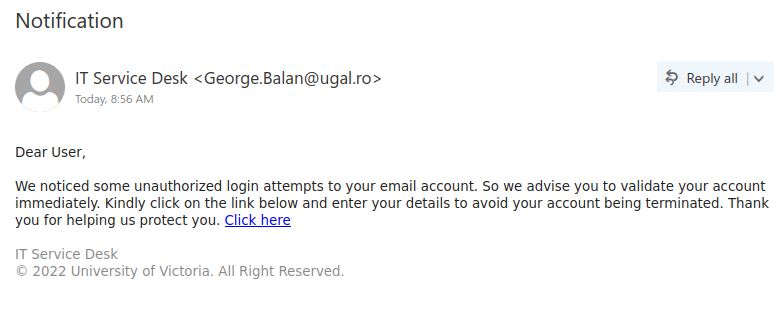
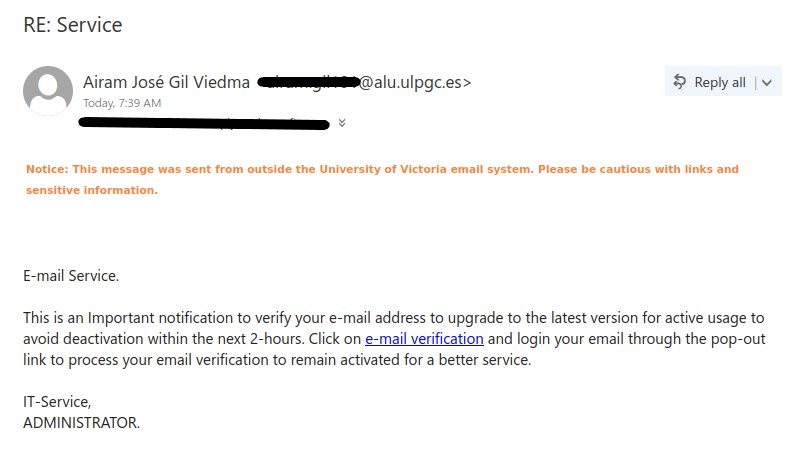
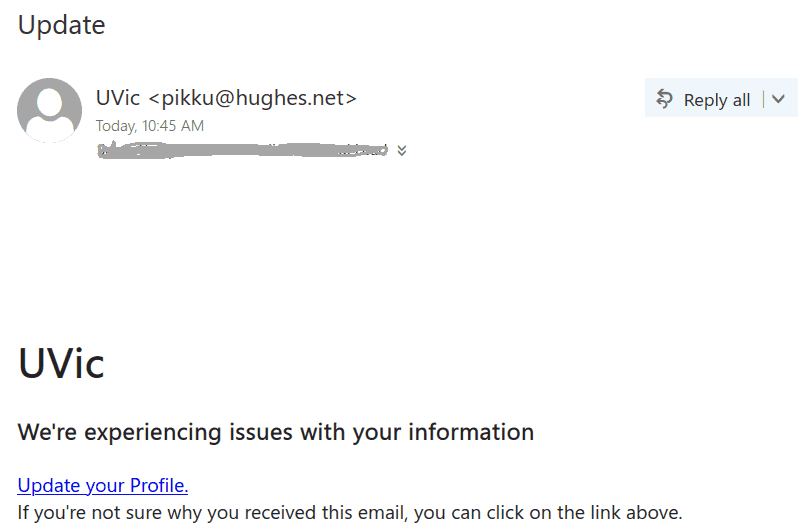
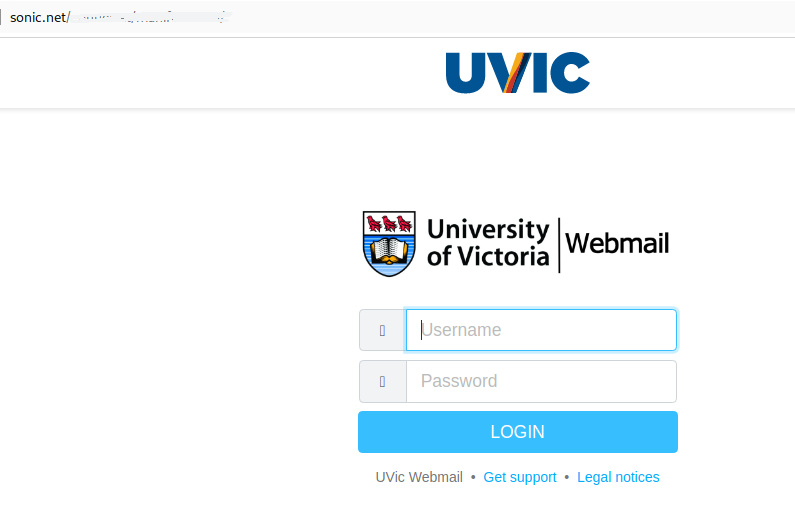
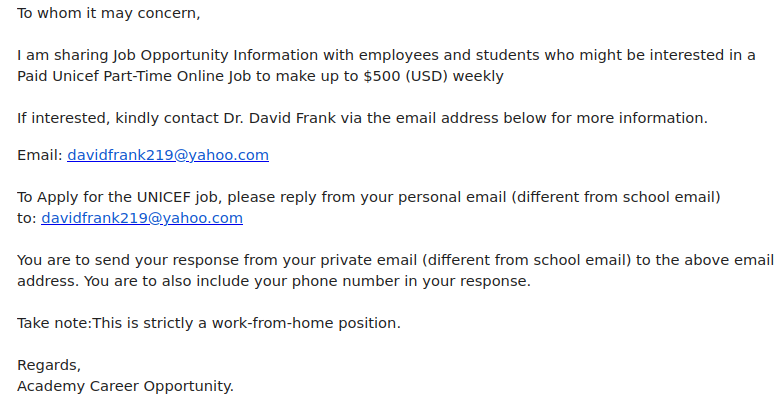
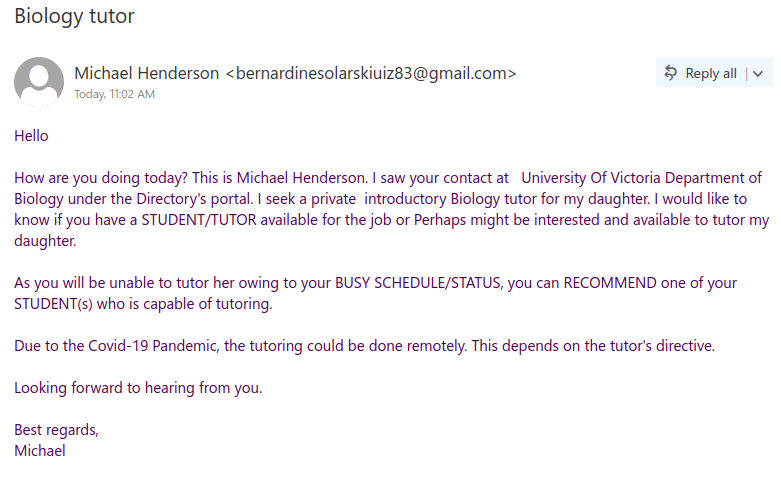
Staff from various departments were targeted with variations of this email, and the scammer seems to have made the effort to tailor the field of study to match the recipient’s department. This scam is likely to be a cheque overpayment scam or could be some other type of job scam. We have seen a previous case of a tutor scam in the past that turned out to be the former.
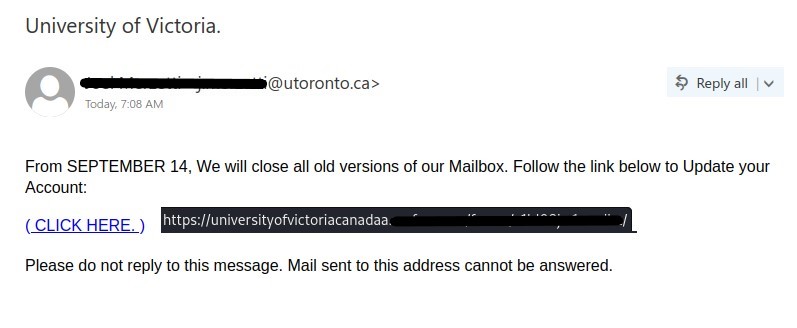
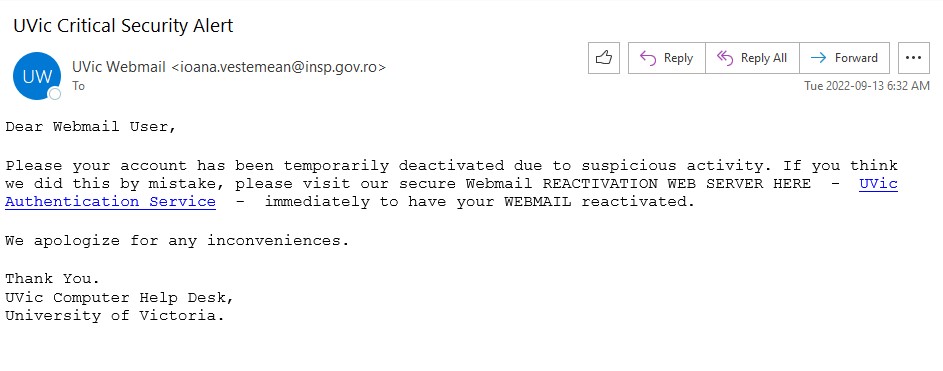
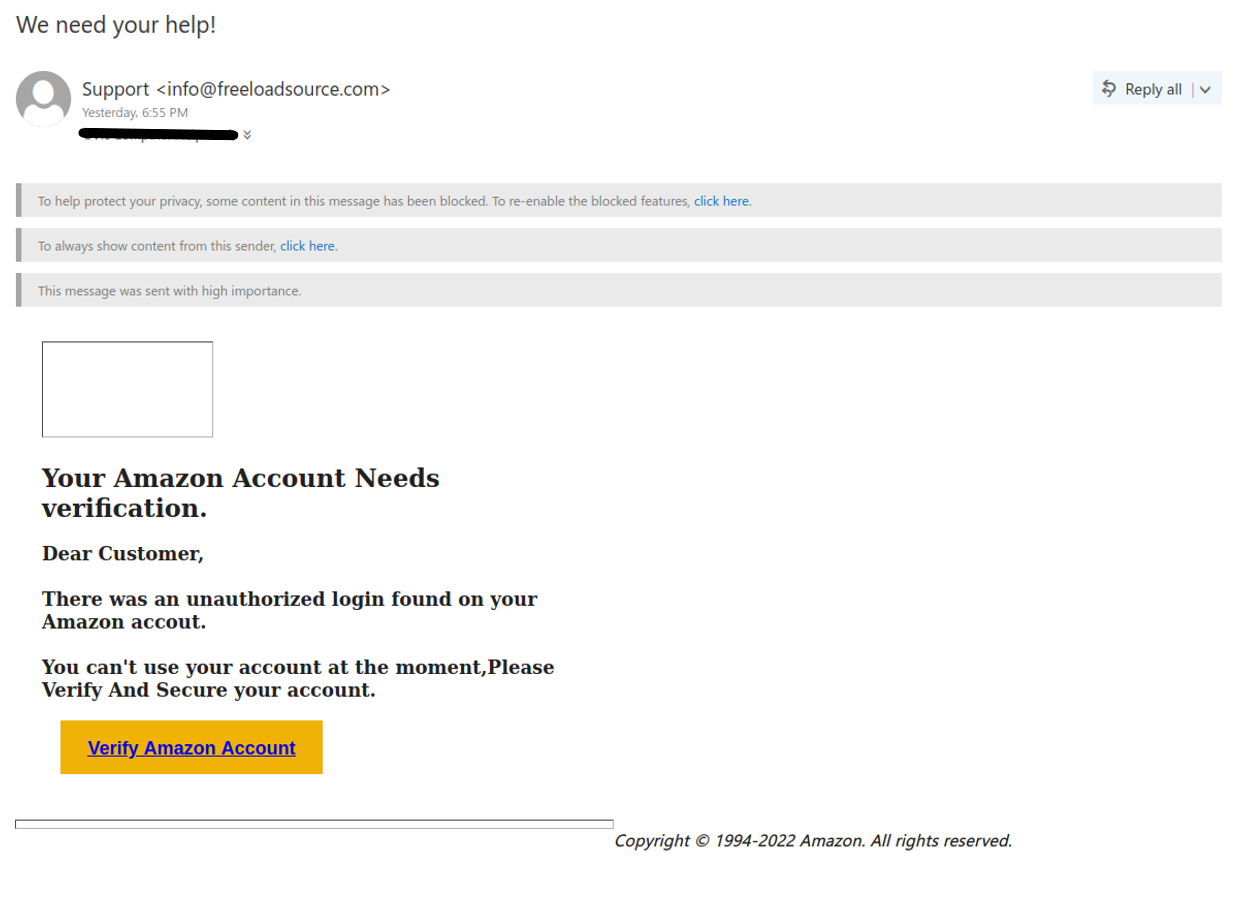
There are a few red flags in this email:
- There are errors in capitalization, punctuation and grammar
- The email was not addressed to a specific recipient (a sign that it was sent in bulk to many people) and the greeting is impersonal
If you received this scam, do not reply to the email and do not forward it to others (especially students). If you did either, reach out to your department’s IT support or the Computer Help Desk for assistance.
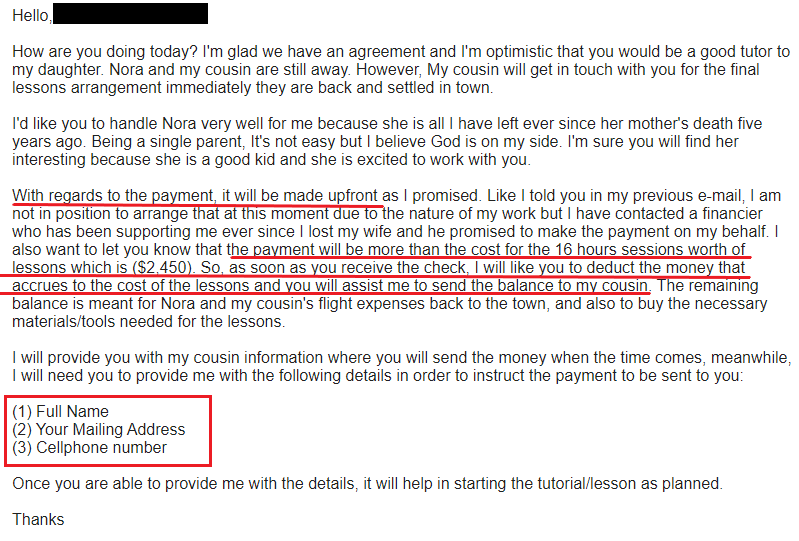
Update 2022-09-09: we can now confirm that this is a cheque overpayment scam. After some back and forth to build rapport, explain the (plausible but fictional) situation and discuss terms of employment, the scammer eventually will reach out with an email like this. The most significant red flags are underlined in the screenshot below:
- The payment will be in advance of the actual lessons
- The cheque will be for significantly more than the amount for the tutor’s actual wages, and the recipient is to transfer the remainder to someone else to cover for other expenses
- The scammer requests PII
According to this article, what eventually happens is that the cheque turns out to be fraudulent and bounces some time after the tutor sends away the surplus amount, leaving them out of pocket for a non-trivial sum of money.