Scammers use multiple tactics to avoid detection. In this example, a likely gift card scam attempted to pivot to using SMS (text messaging) by asking for a staff member’s personal cell phone number. If successful, it would move the conversation with the scammer away from email systems to avoid detection of the conversation, and may have resulted in disclosing of a personal phone number to a scammer.

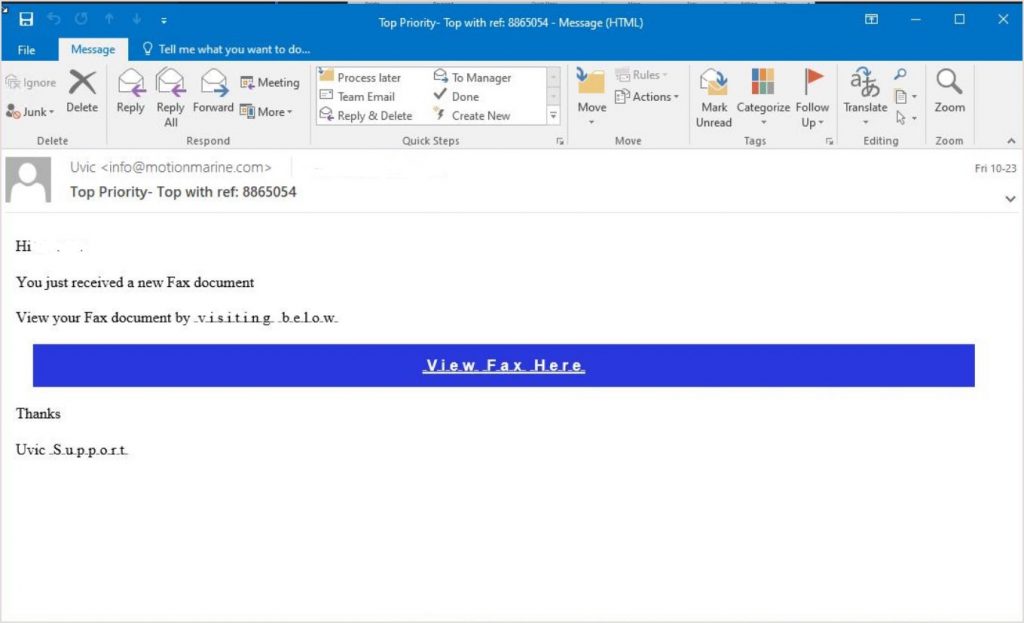
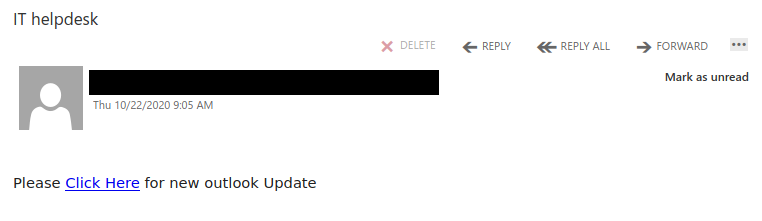
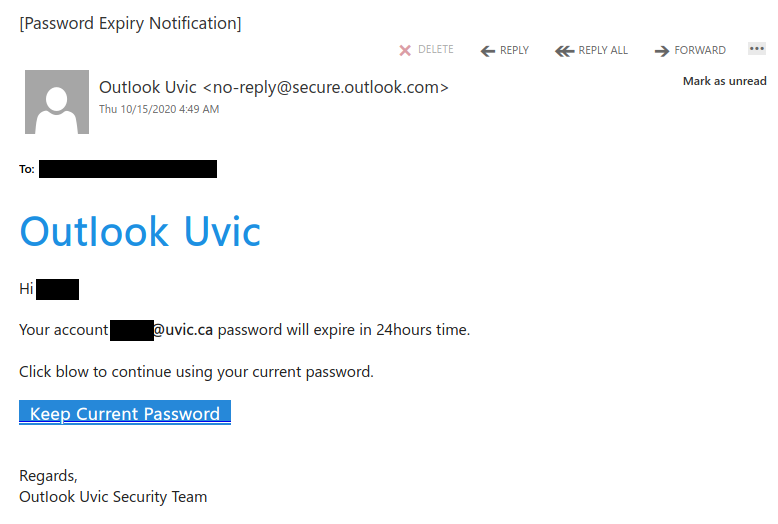
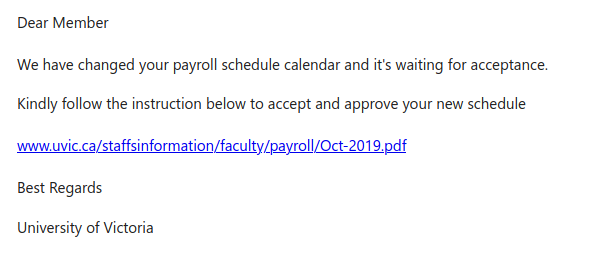
Signs this might be a scammer include a fake external email address, the urgency of the subject line, and the request for a personal number. The email warning banner at the top also indicates it didn’t originate from a UVic email address.
Someone who sent their cell phone number might have received a text message conversation starting out like this:
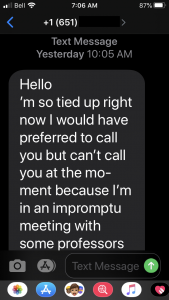
To see what a typical gift card scam email conversation might look like, check out a recent story detailing an interaction with a President Jamie Cassels impersonator.








 =================================================================
=================================================================