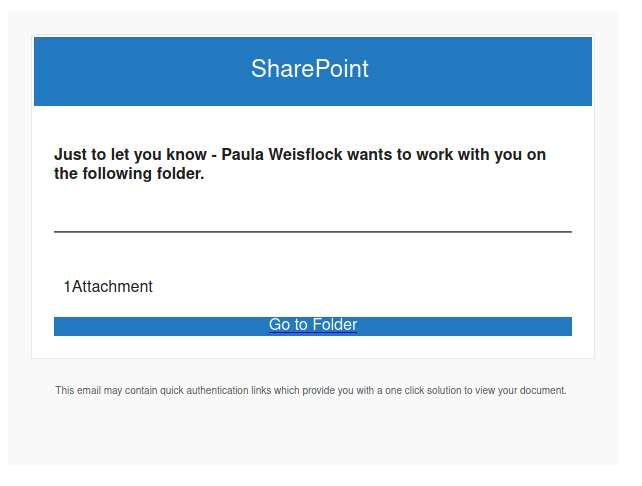
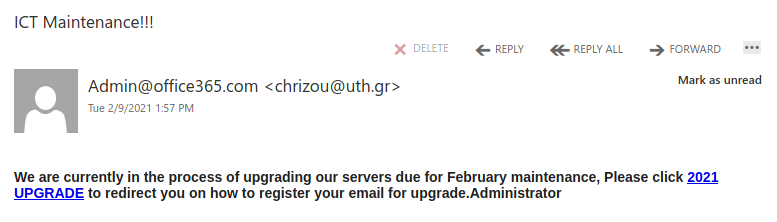
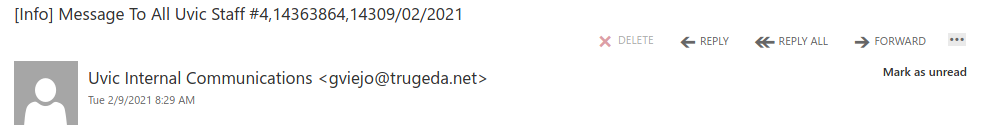
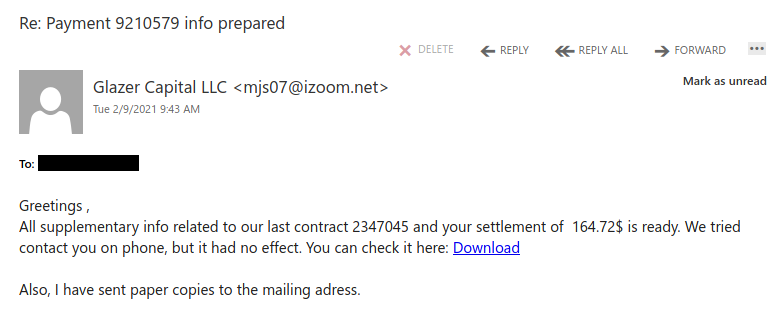
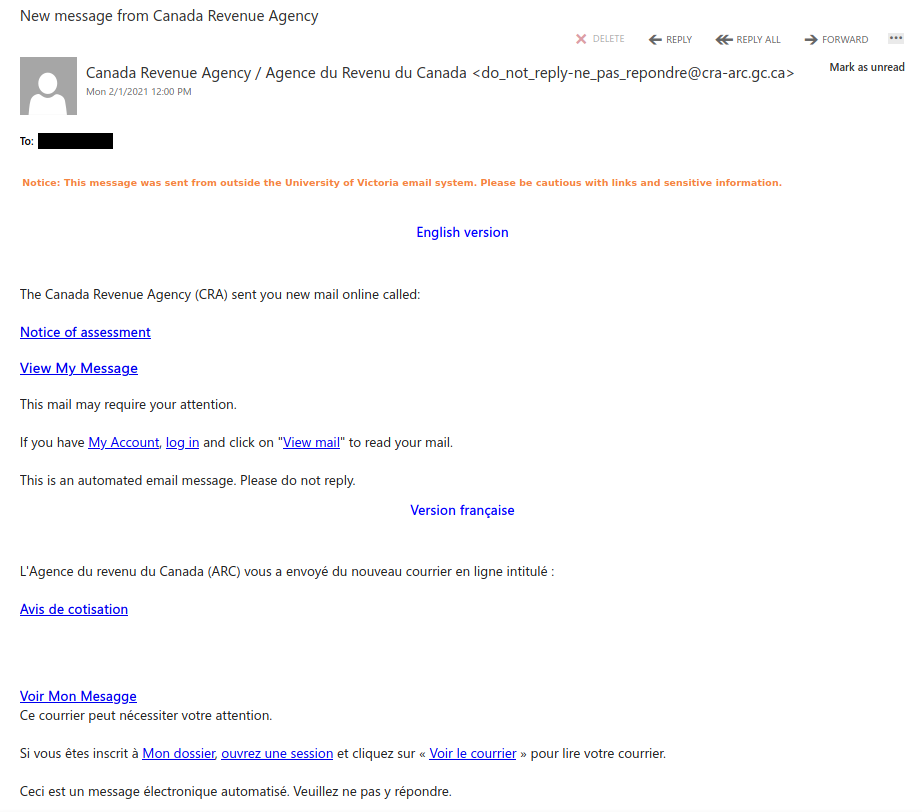
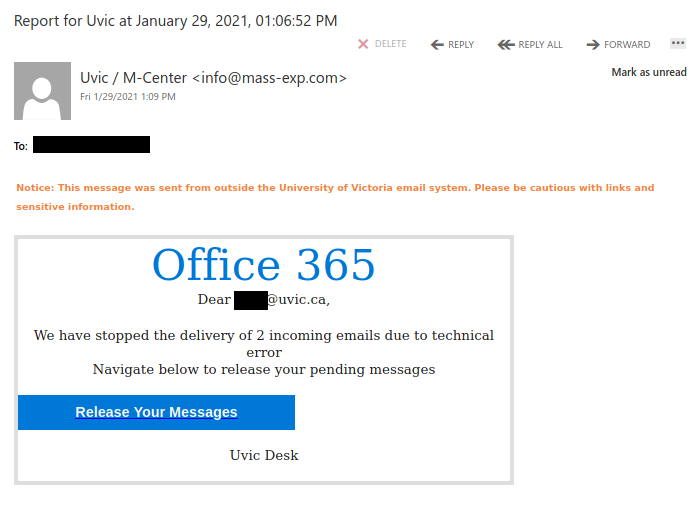
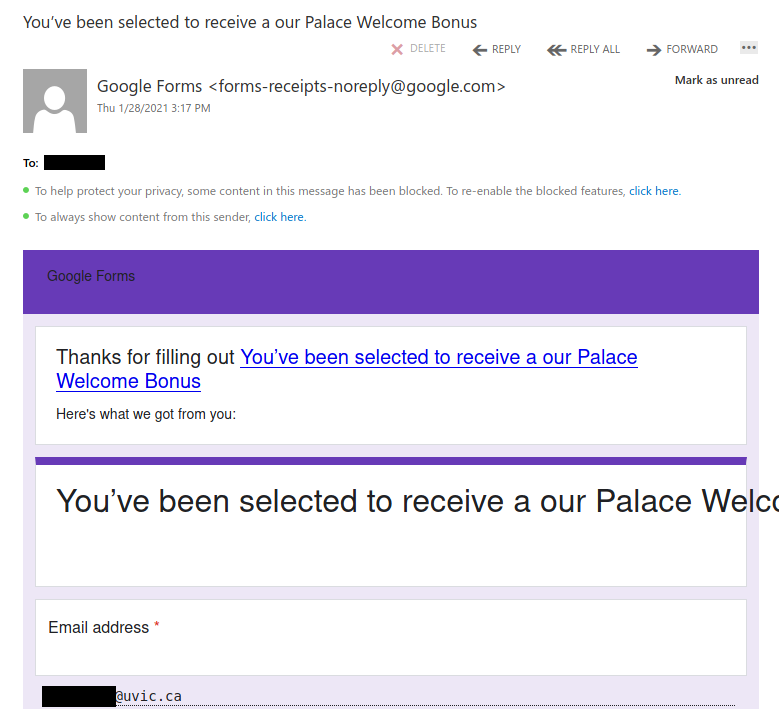
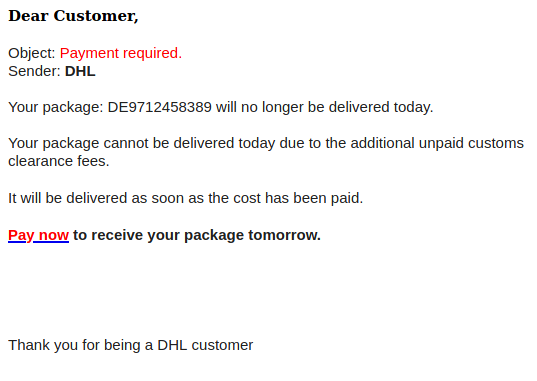
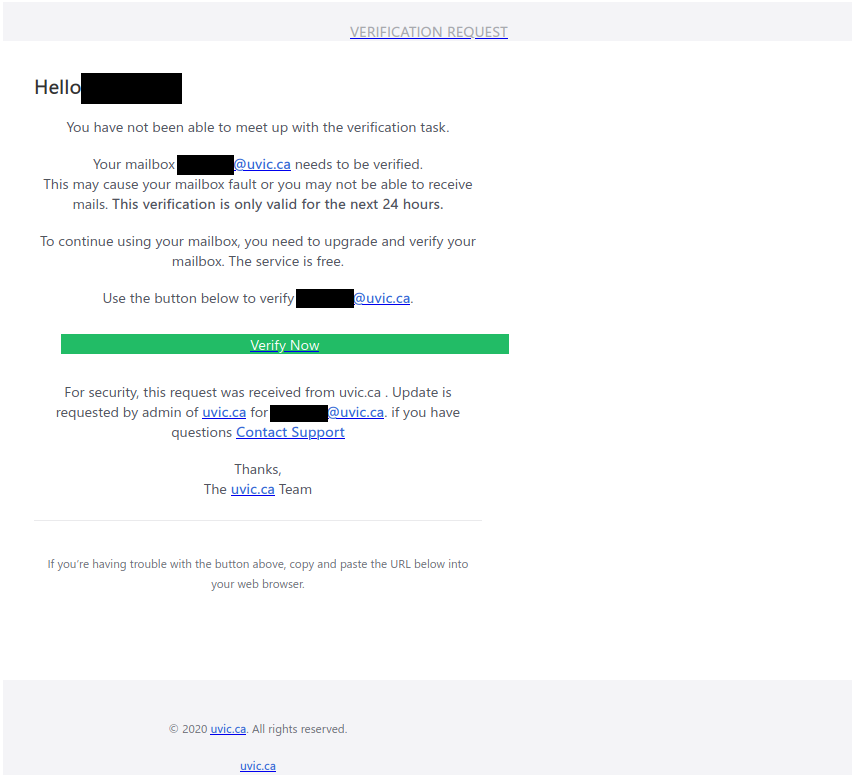
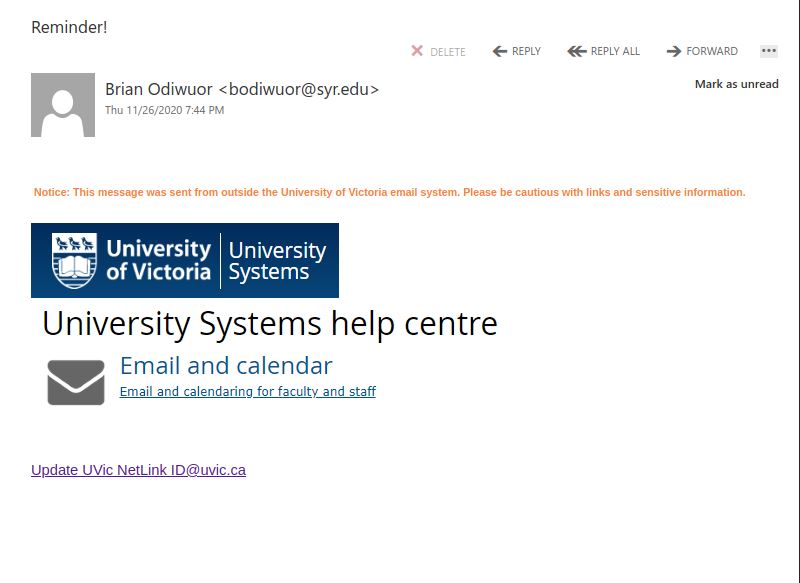
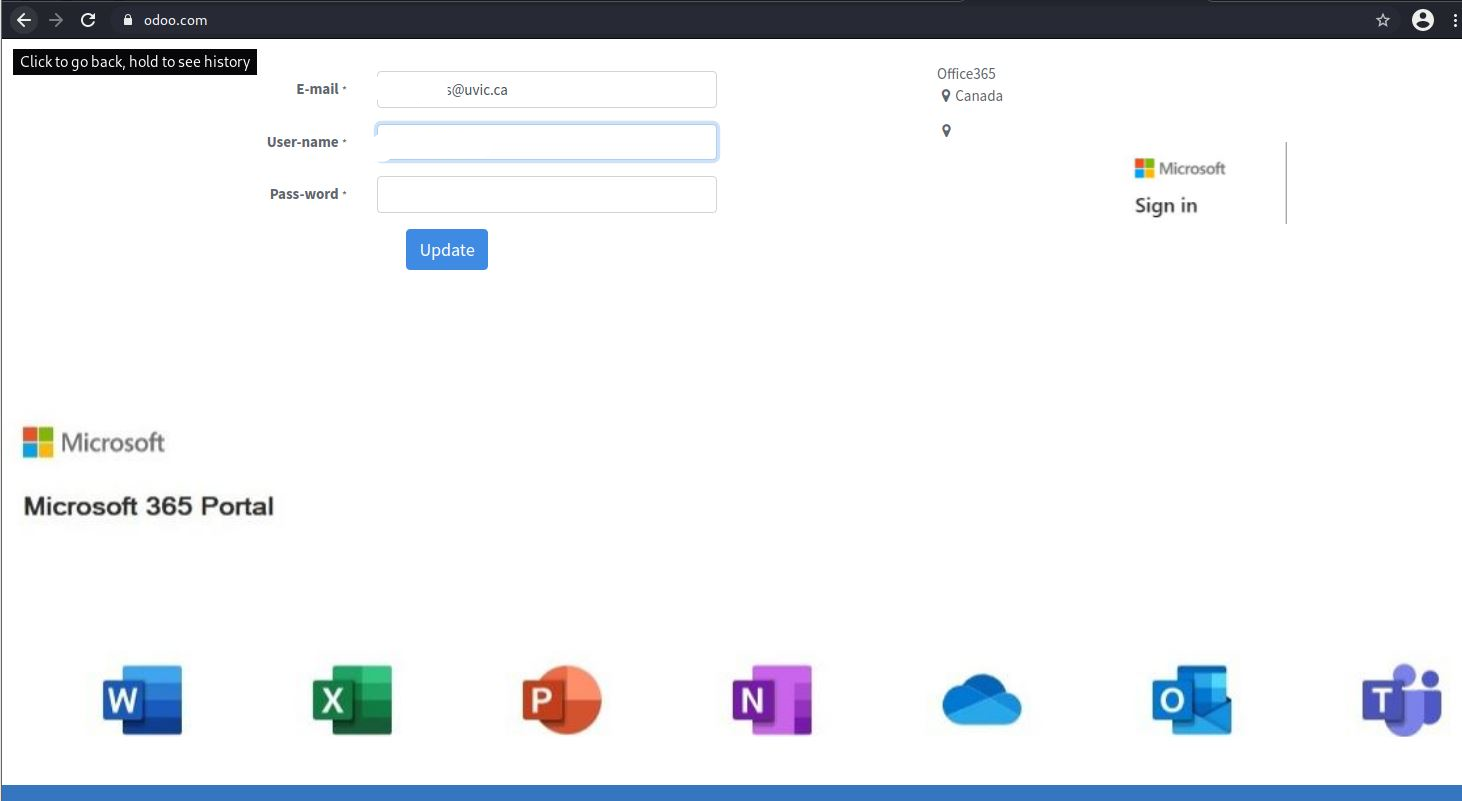
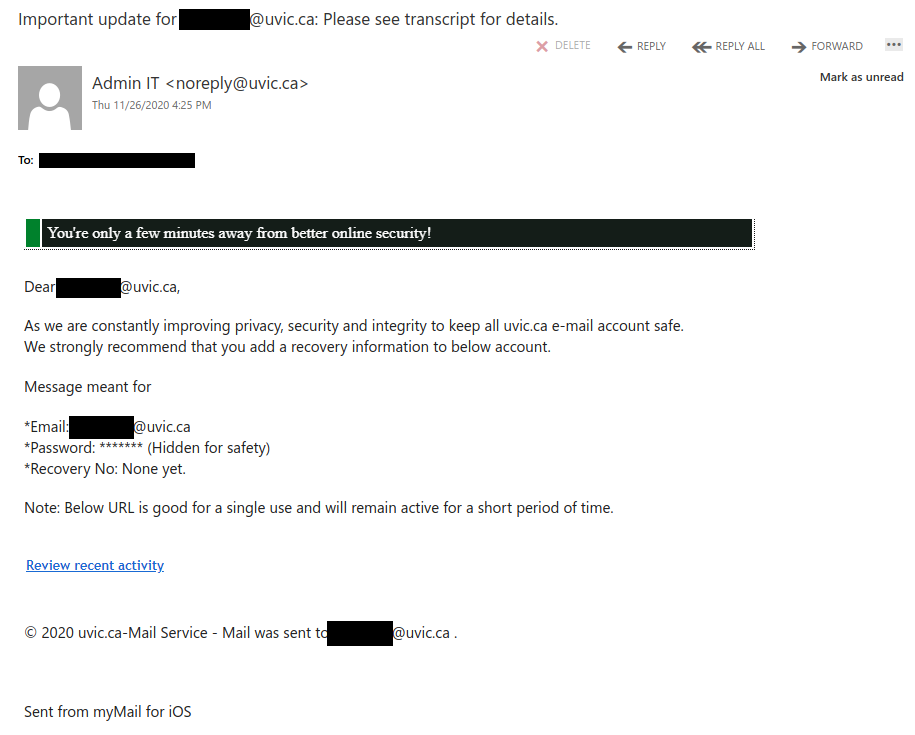
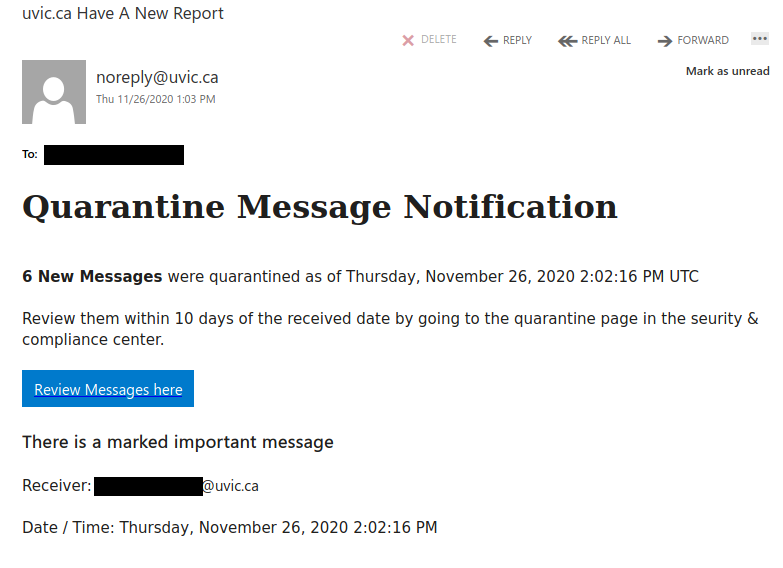
Don’t trust the link text that you see in an email. While that link claims to be from amazon.com, if you were to hover over it you’d find it’s actually a shortened URL from bit.ly. Be wary of shortened URL in emails; while the shortening service might be legitimate, phishers often use them to obscure the true destination of the link.

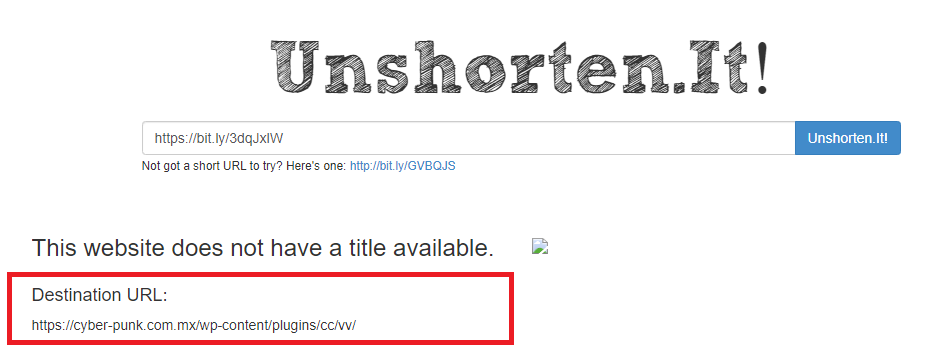
You can try using a URL unshortener like Unshorten.it to see if it can obtain the true destination. Here’s a screenshot of the results I got from running it on the URL from that phish–you can see that bit.ly link definitely doesn’t go to Amazon and shouldn’t be clicked!