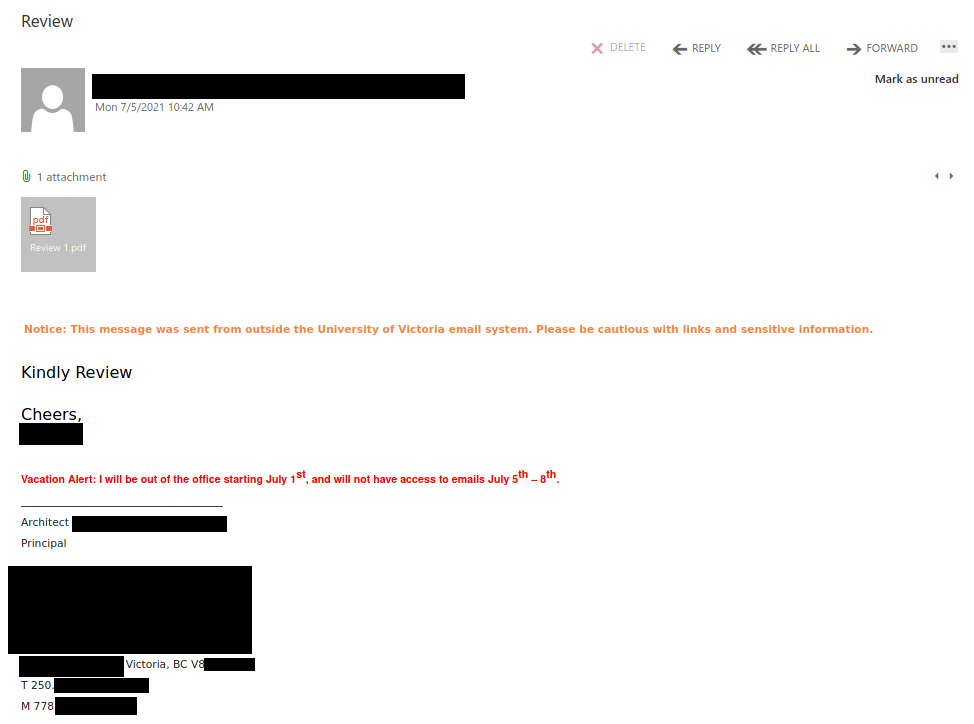
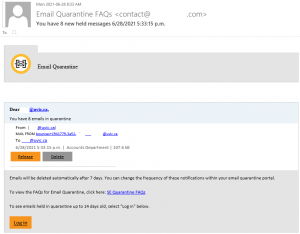
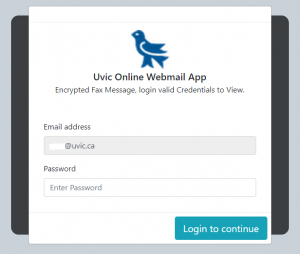
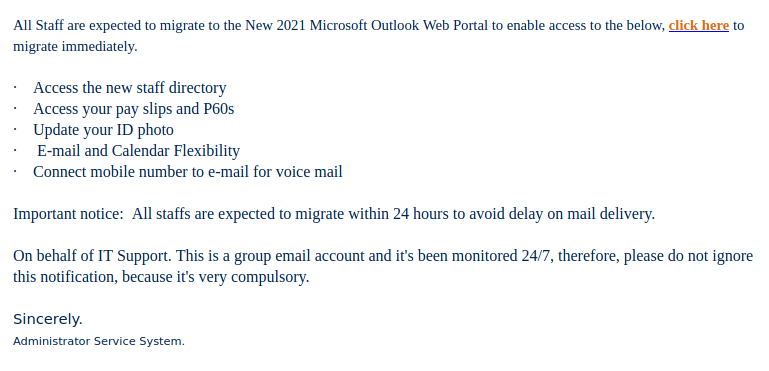
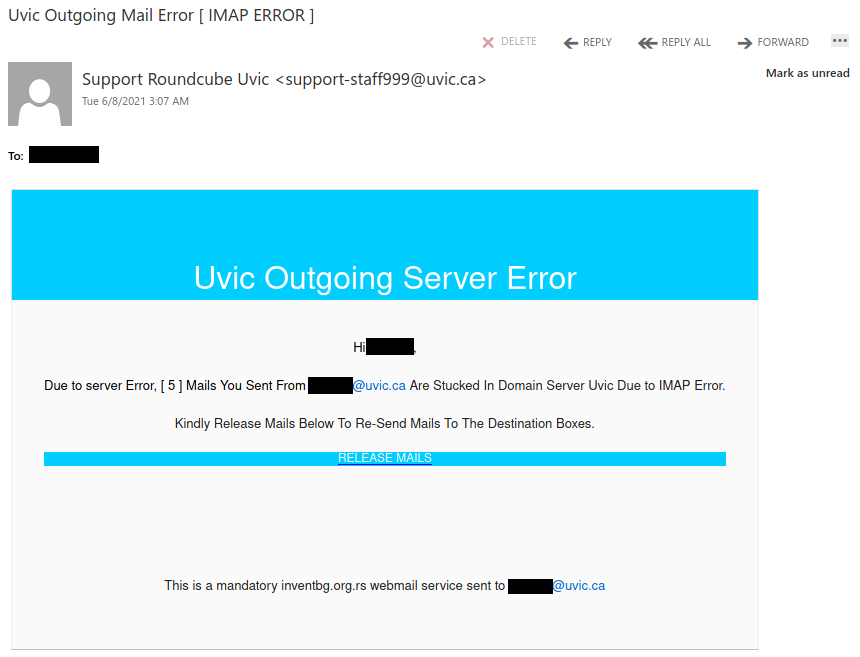
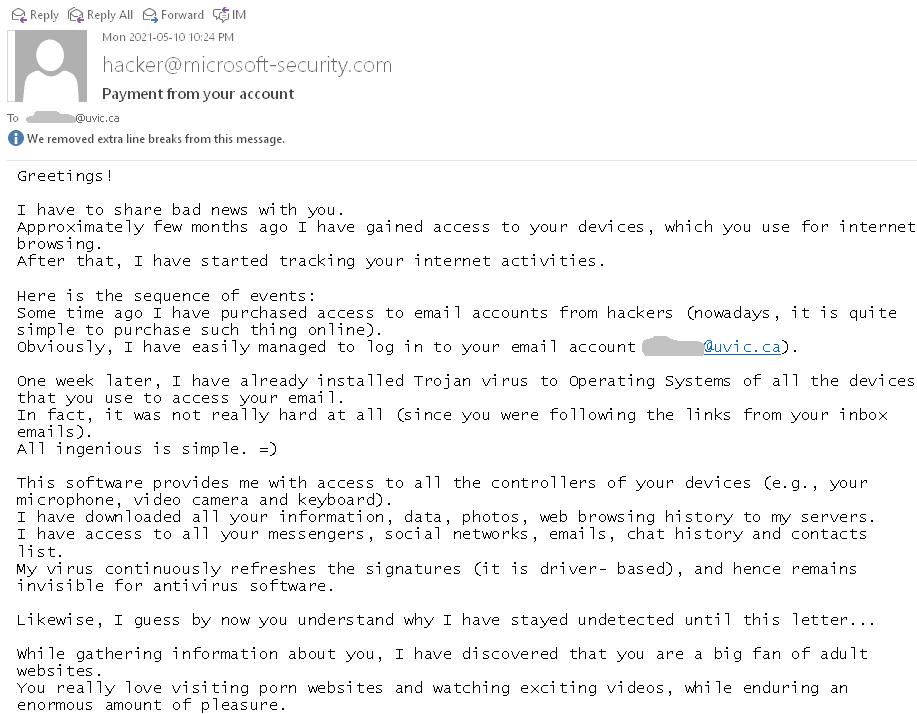
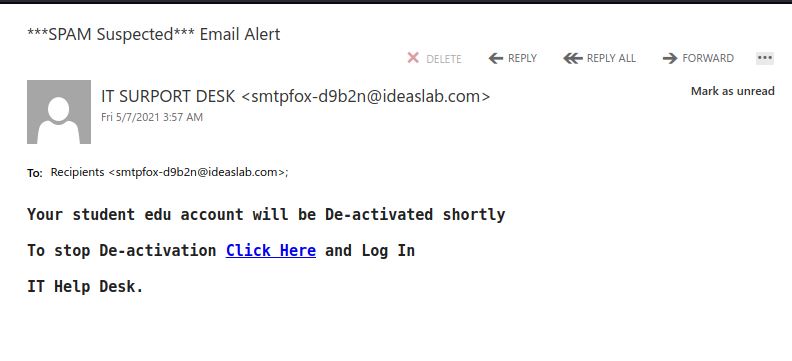
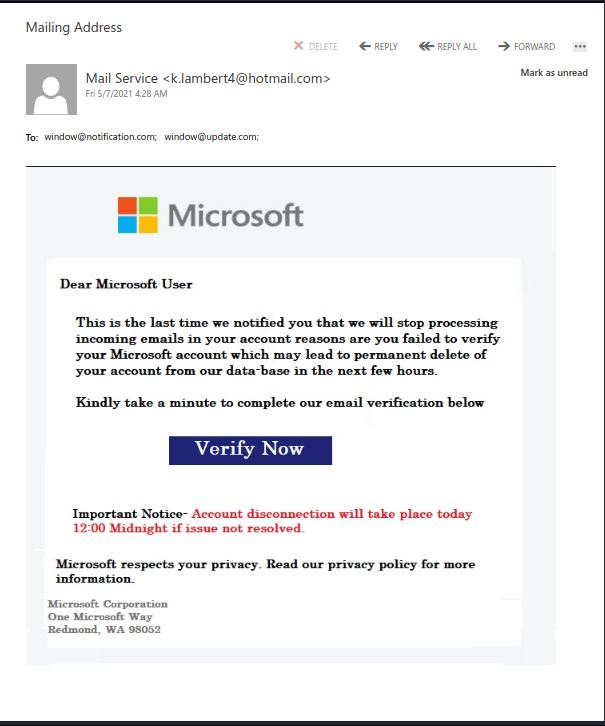
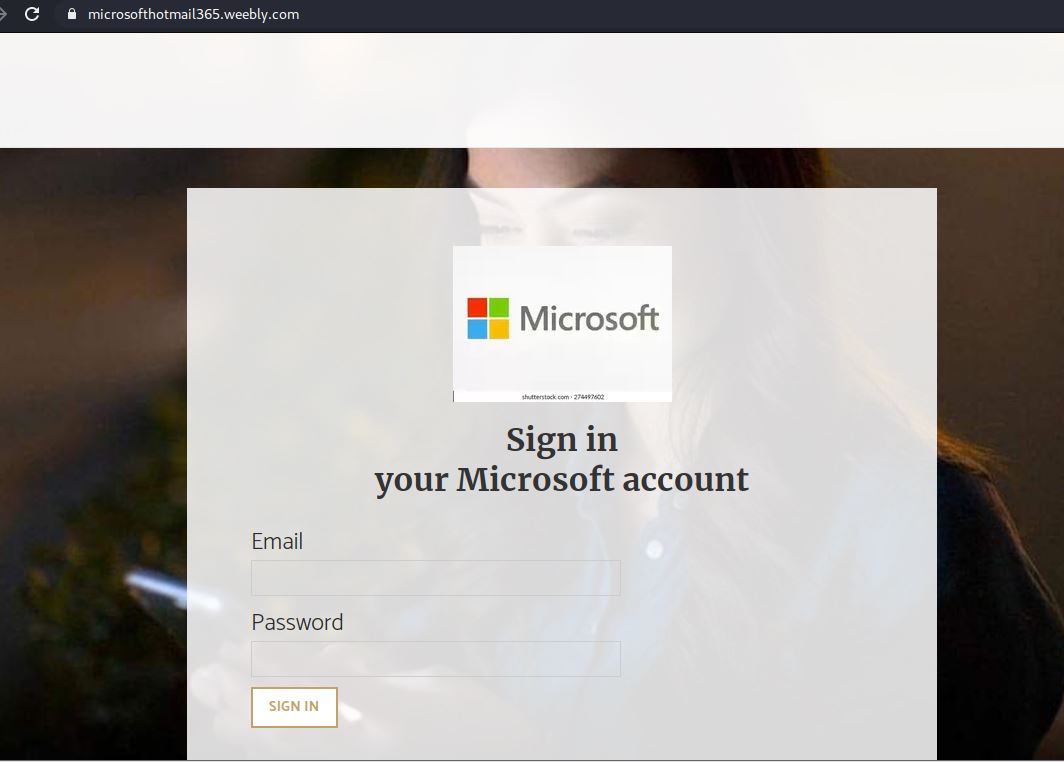
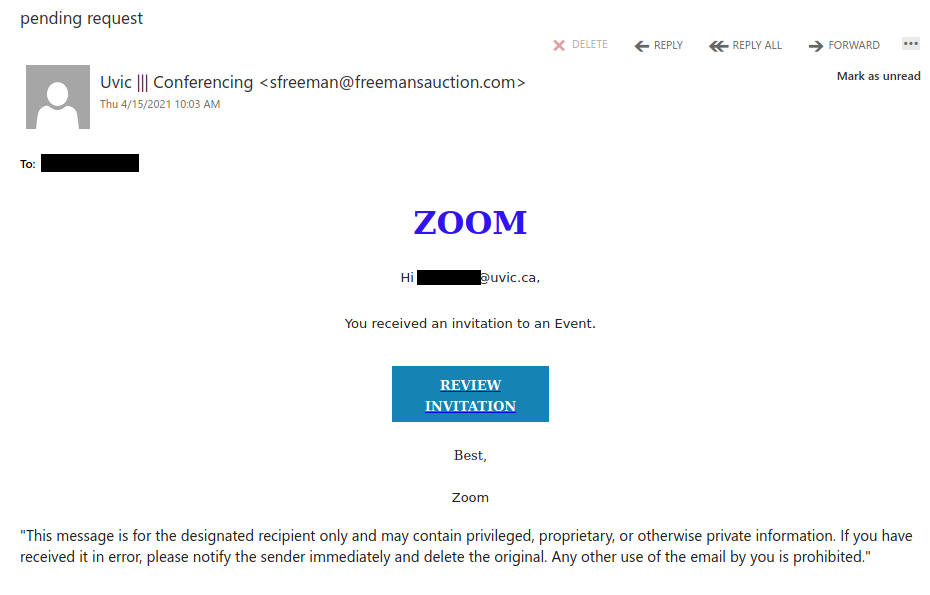
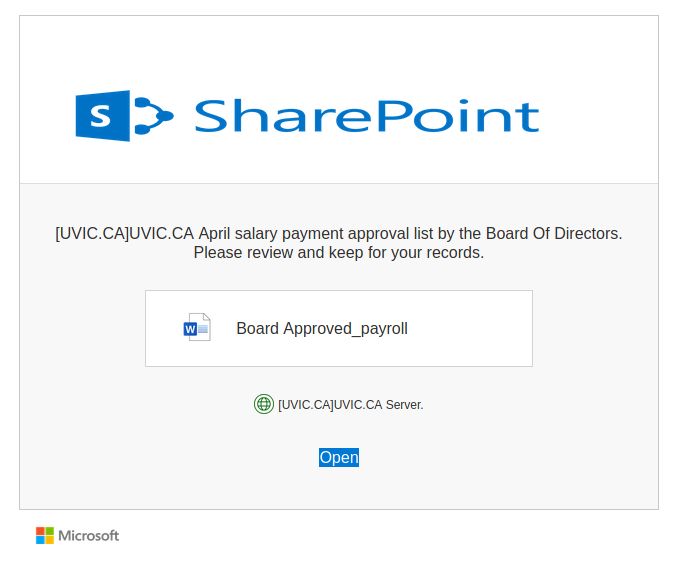
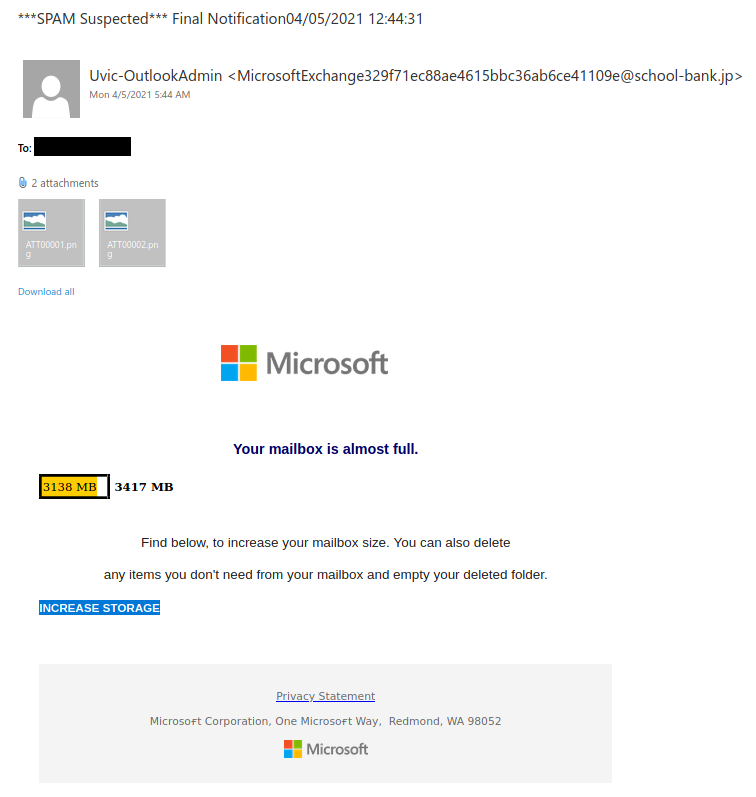
Recently there have been cases where a user at some other Victoria-area organization had their account compromised and used to send phishing emails. These emails come with a PDF attachment that poses as a M365 SharePoint file sharing notification and directs you to click on a link to login and view the shared file. That link takes you to a fake M365 login page to try and trick you into providing your username and password. If you opened this PDF, please reach out to your department’s IT support staff or the Computer Help Desk immediately.
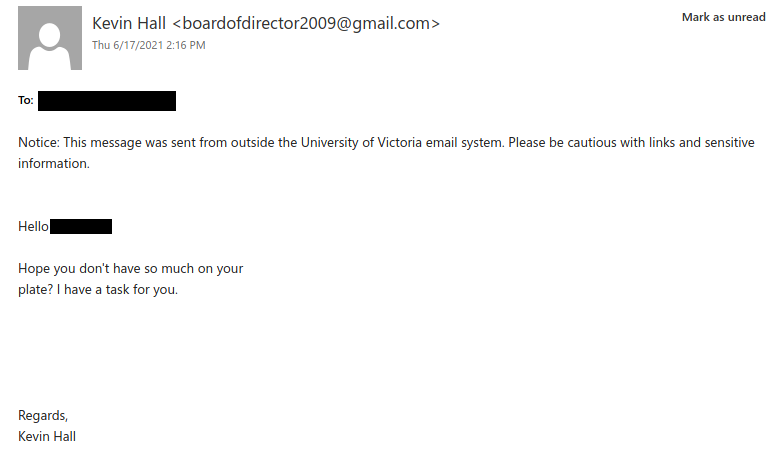
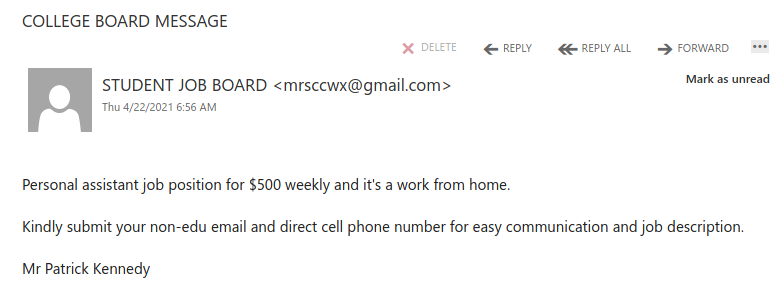
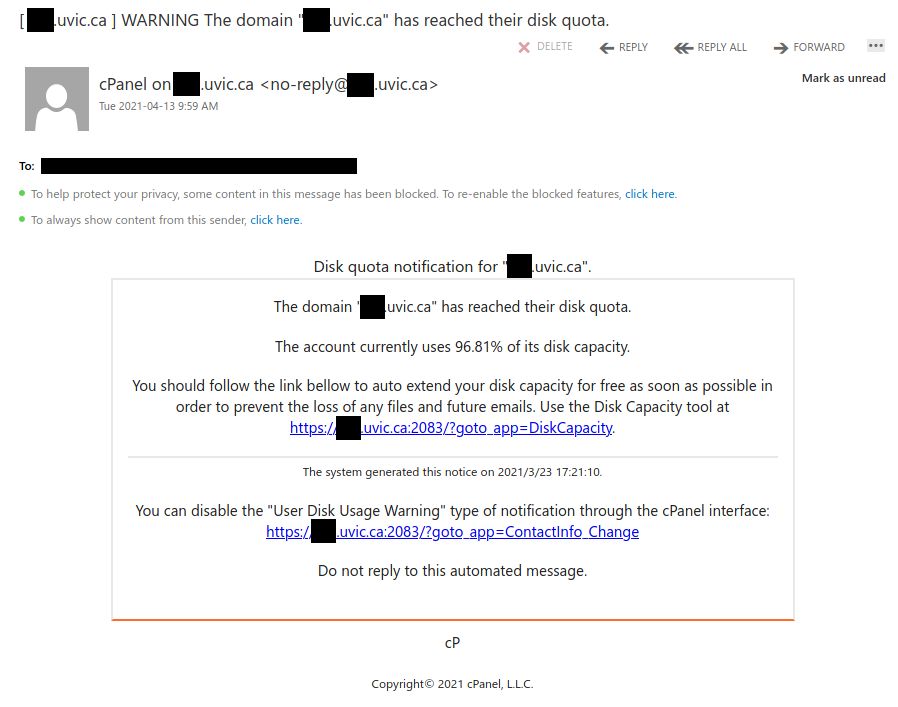
If a phisher manages to compromise an account belonging to someone you know or have prior dealings with, they may try to take advantage of that existing relationship in their phishing attempt, hoping that you’ll think the message is safe and click on links or attachments. When in doubt, contact the sender via another communication channel that you know is trustworthy (e.g.: a known good phone number) to verify that the email is legitimate.
See also: CISO Blog post – How can I tell it’s really you?