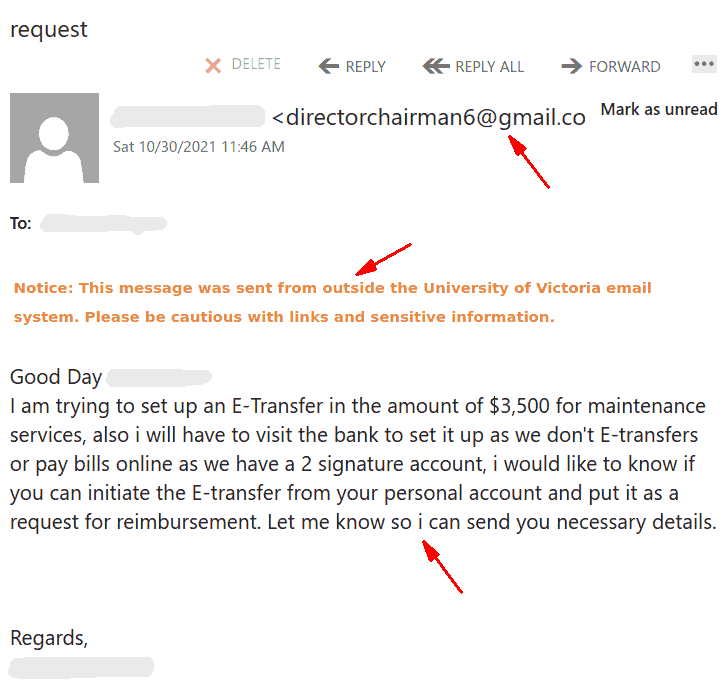
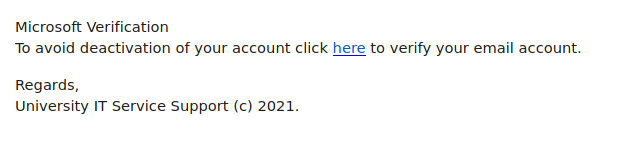
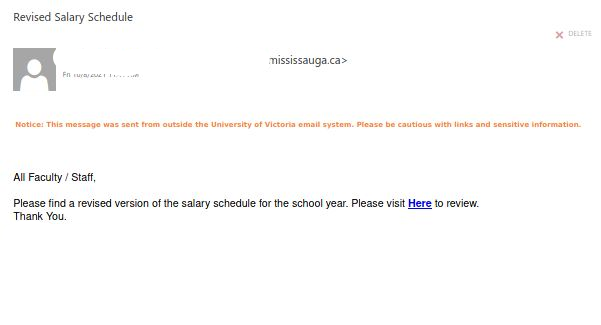
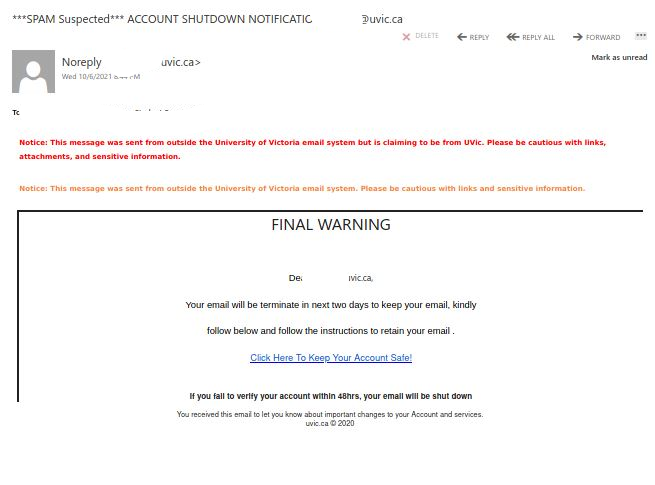
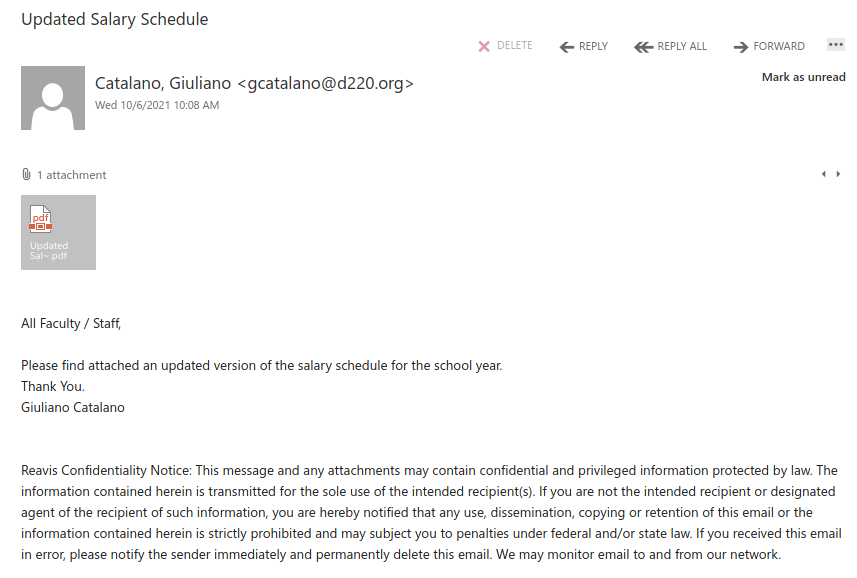
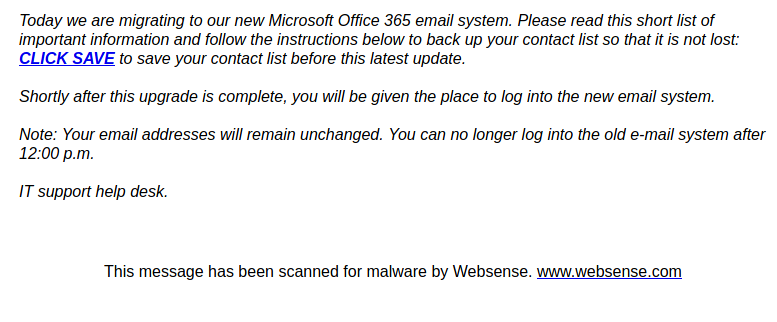
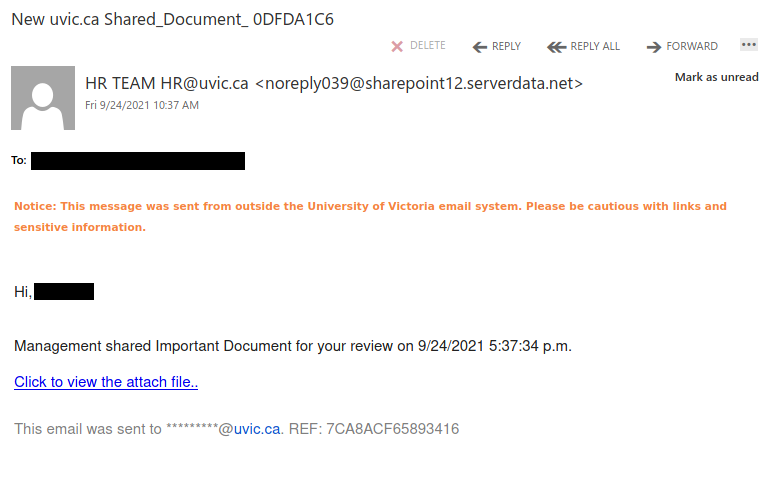
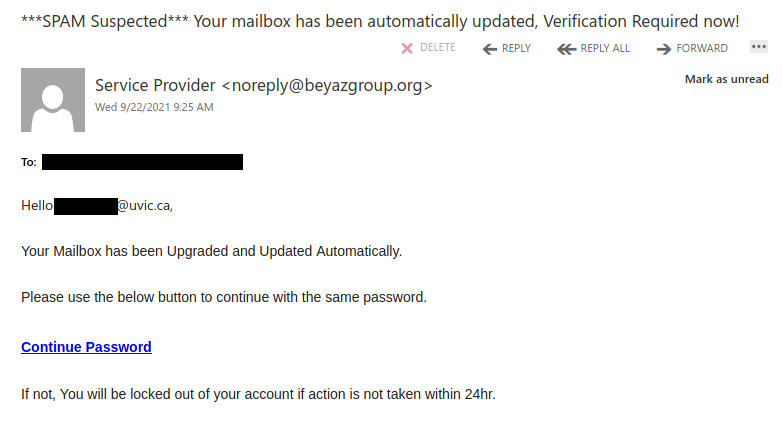
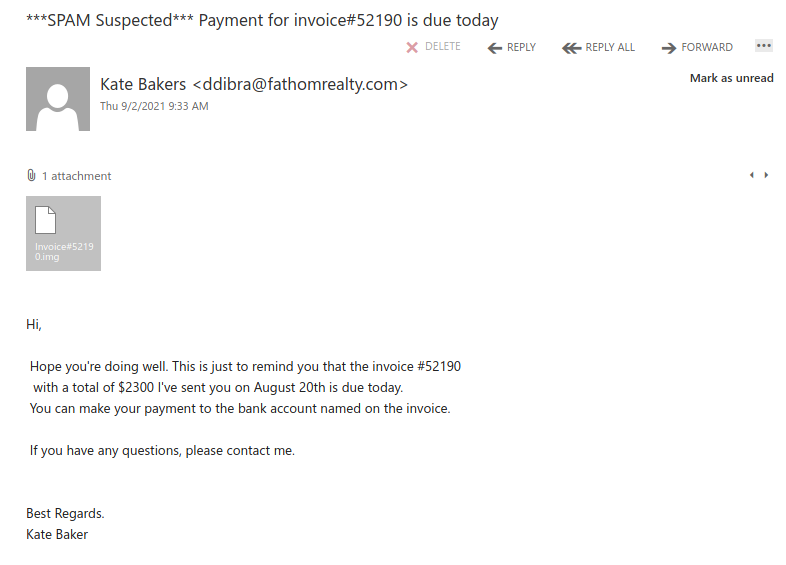
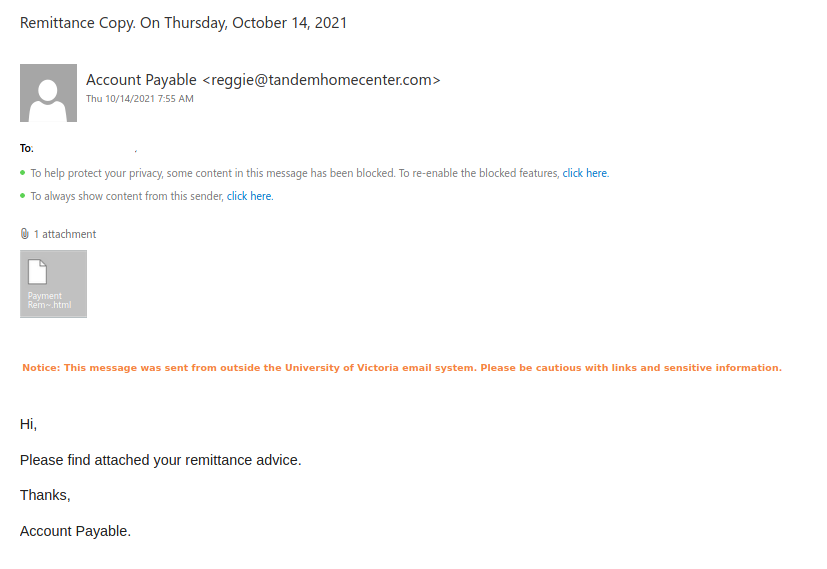
Another one from yesterday posing as a remittance payment. For those of you who handle plenty of accounting related processes, you can be a target here. Others of us expecting payment for some service, if curious or assuming the timing is right, may not recognize the red flags right away. Note sender. Note external banner.
Some UVic staff will expect and deal with external vendors and mailings all the time. So it’s particularly important to use caution. Ask yourself if you are expecting payments, is this a known vendor, do you have a purchase order etc. that matches such a payment?
For those of us that would only expect such a payment from a UVic source, using external banner warnings lets you know this was not sent from UVic. Some guidance on the availability of these banners and other options are available here.
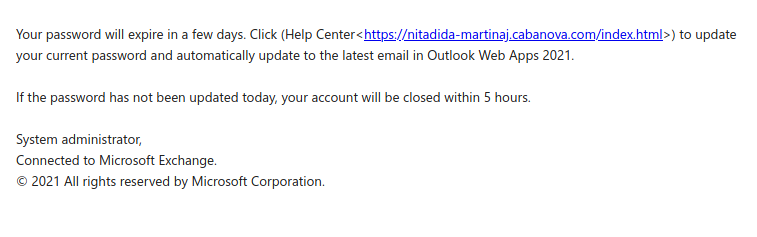
In this case, this is not likely a known or expected sender. Always pause, check the accounts that should have or will receive any expected payments. Verify. Verify.
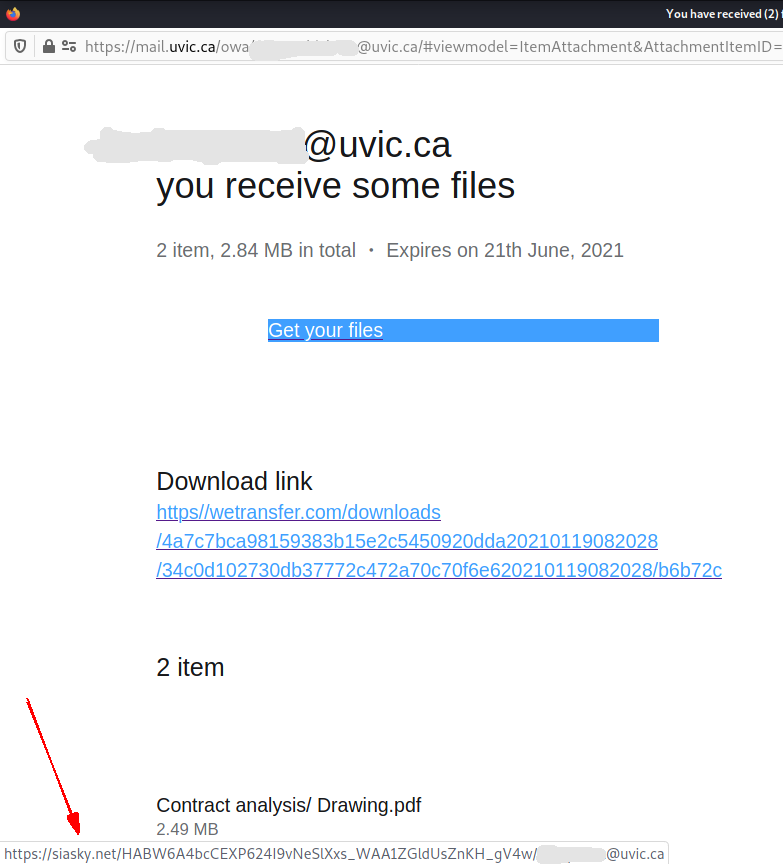
Pause. Receiving an HTML attachment is likely less common and more often not legit at all. Any attachment can be problematic or malicious including the common PDF or Word document. Treat any attachment as suspect.
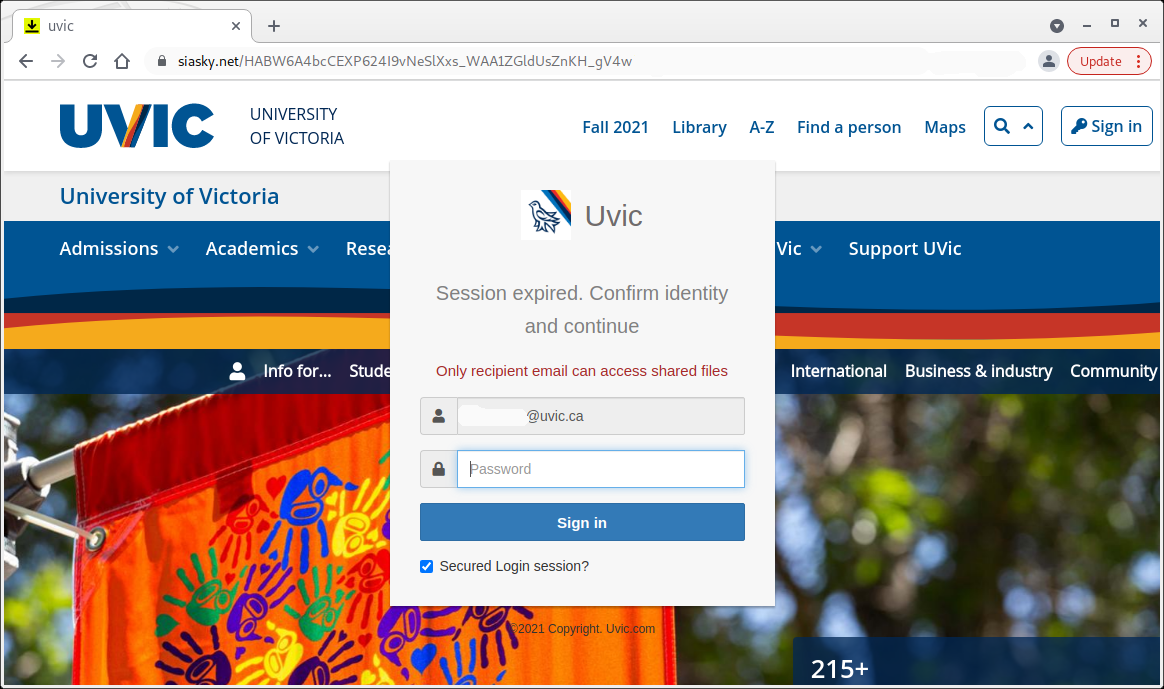
Downloading and executing this malicious .html attachment eventually leads to a prompt for you to give away your credentials by logging in to a fake logon window.
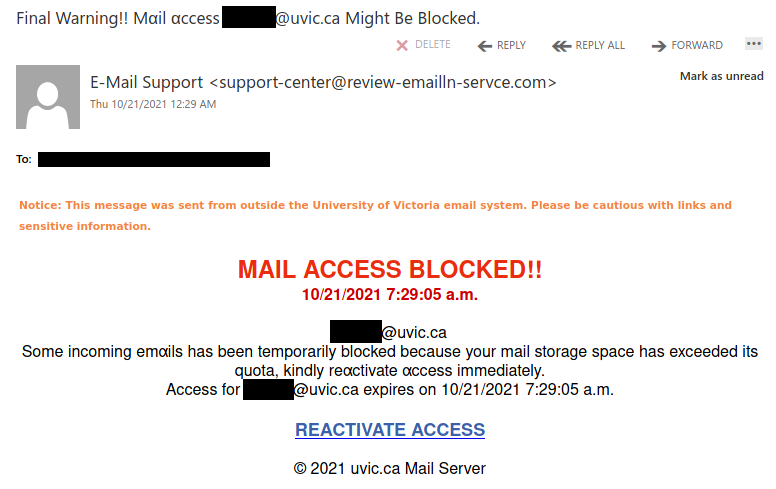
If you have concerns or questions about such an email and/or attachment, or would like another set of eyes to examine the email, do not hesitate to contact your department IT support or the Computer Help Desk.