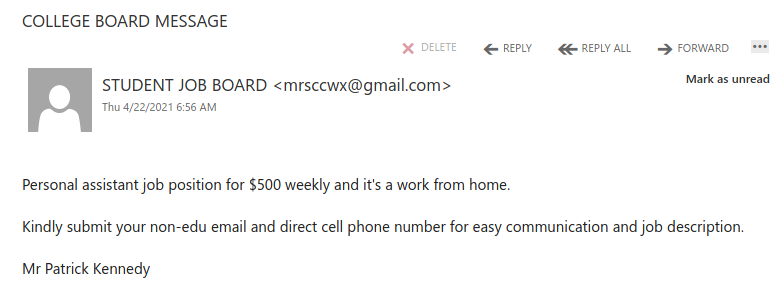
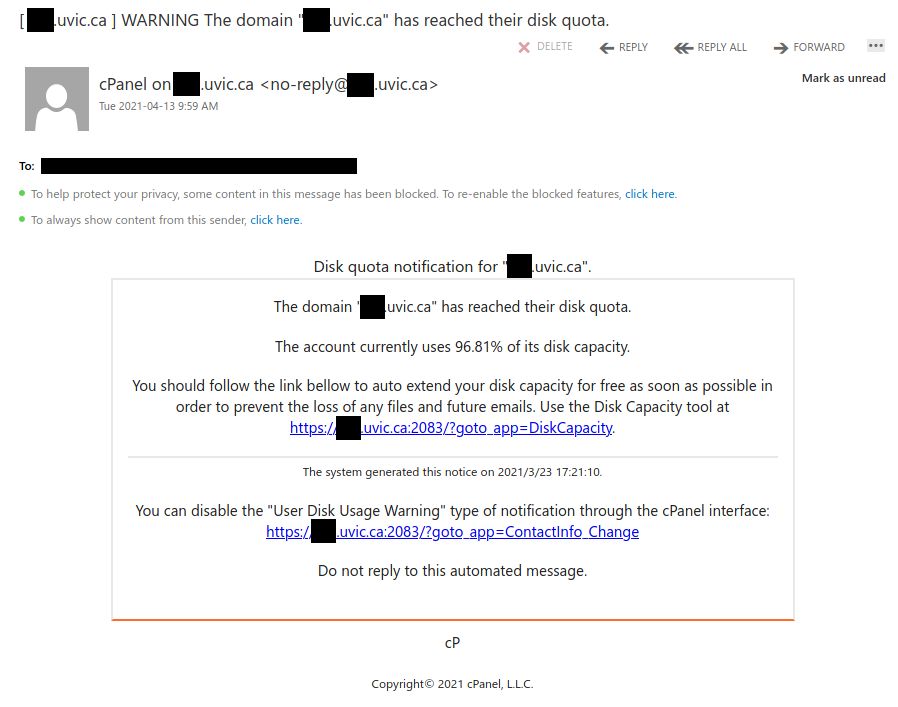
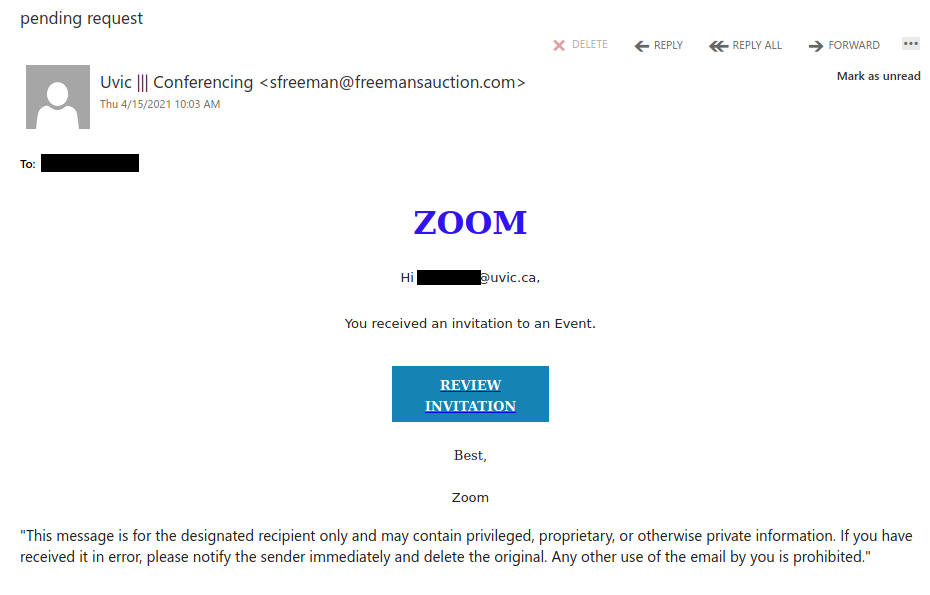
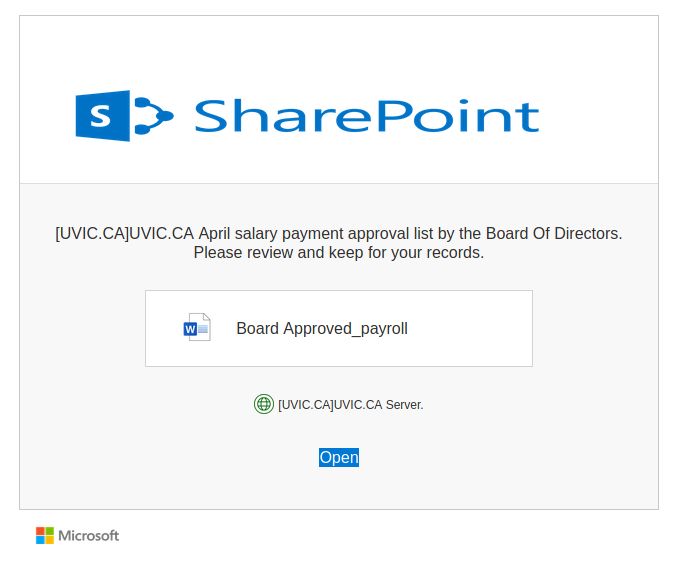
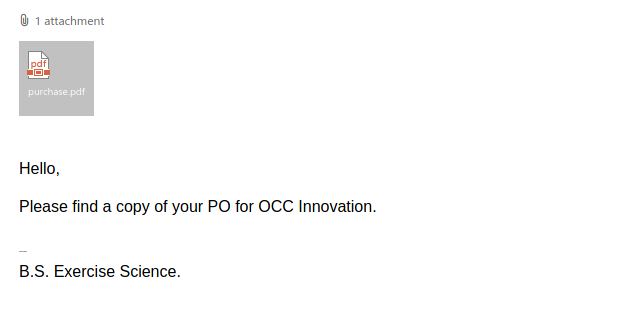
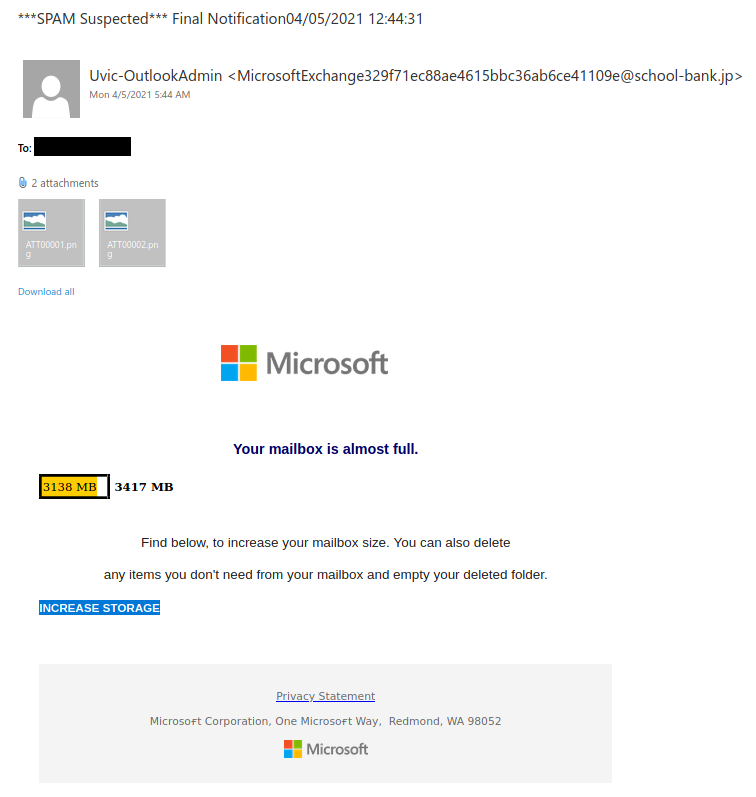
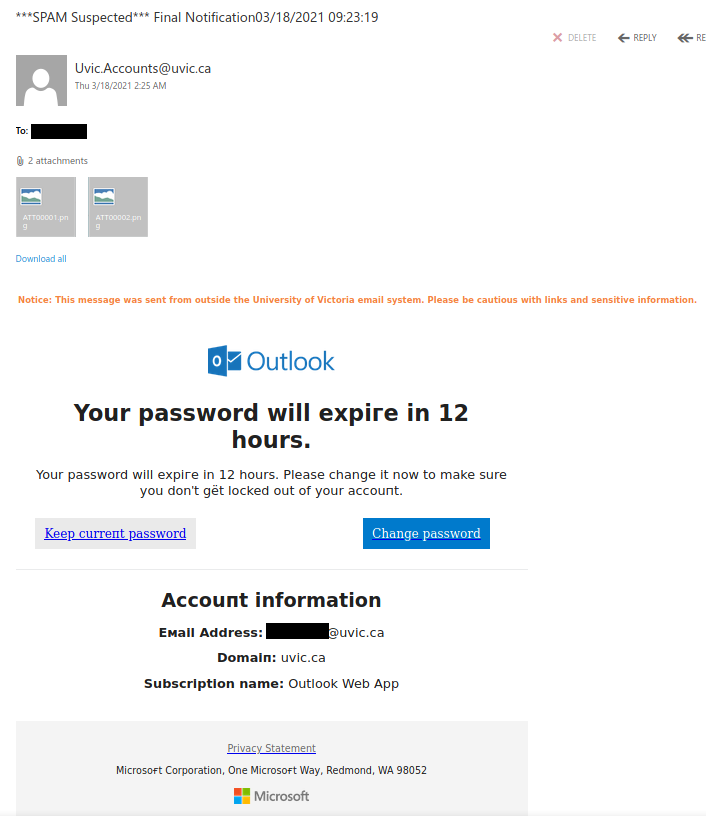
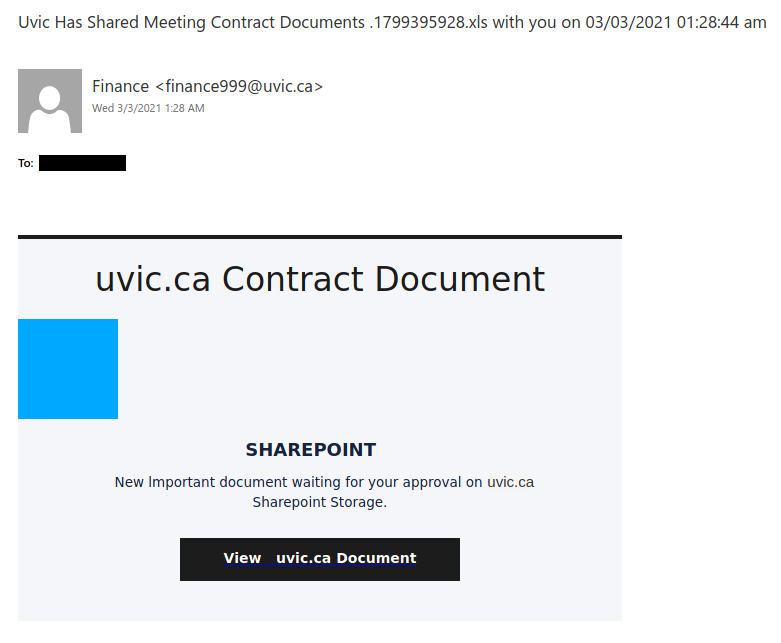
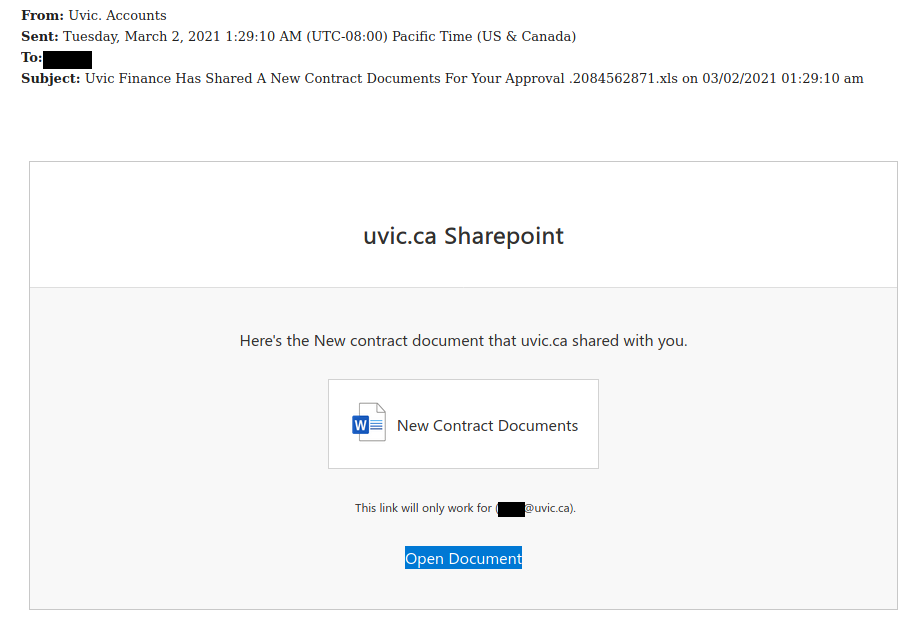
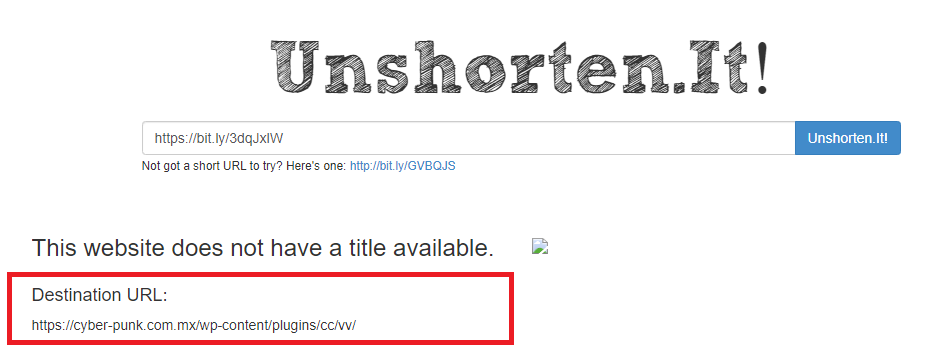
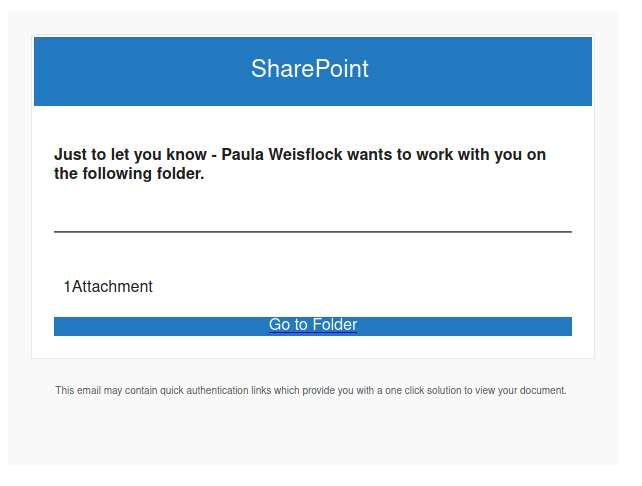
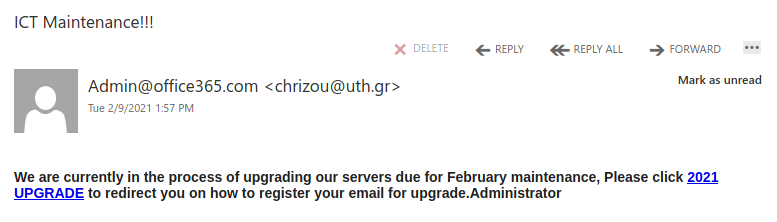
Work from home job scams are unfortunately very common right now with scammers trying to take advantage of people having financial difficulties due to the pandemic. If you receive an unsolicited email like this, do not reply with your email address, phone number or any other personal information. If you did, be extra vigilant about scams, phishing, smishing (SMS phishing) and vishing (voice phishing) since the scammers may view you as a promising target.
More on work from home job scams:
CBC News – Online job scams on the rise during pandemic year, fraud prevention expert says
CTV News – Better Business Bureau warning about these work-at-home scams