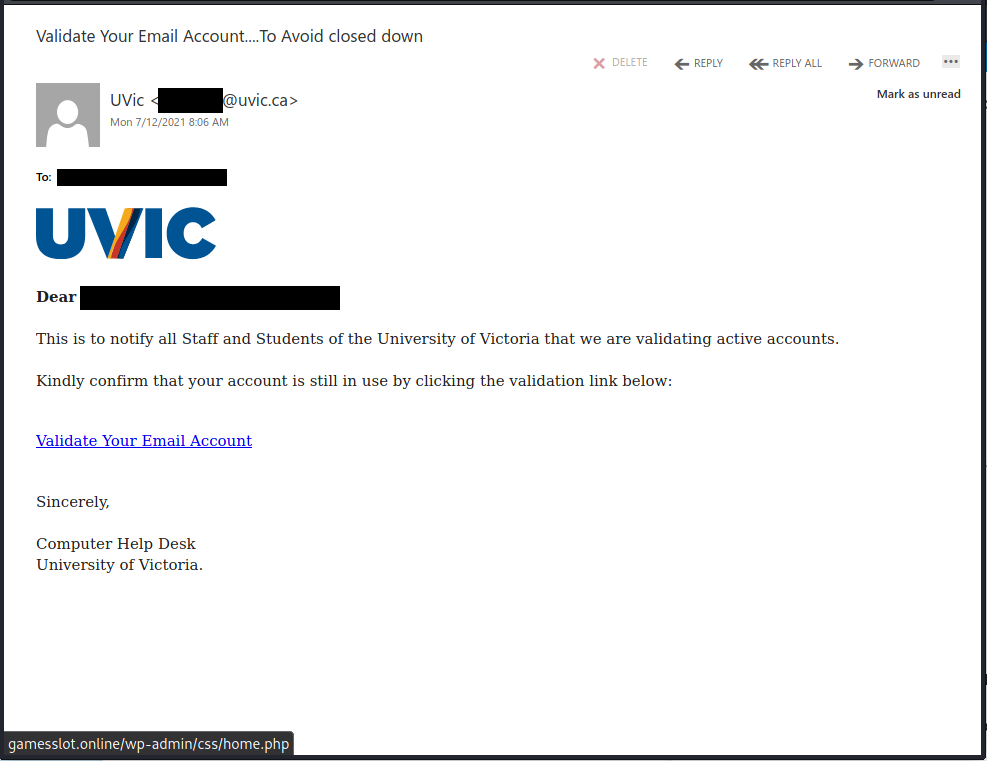
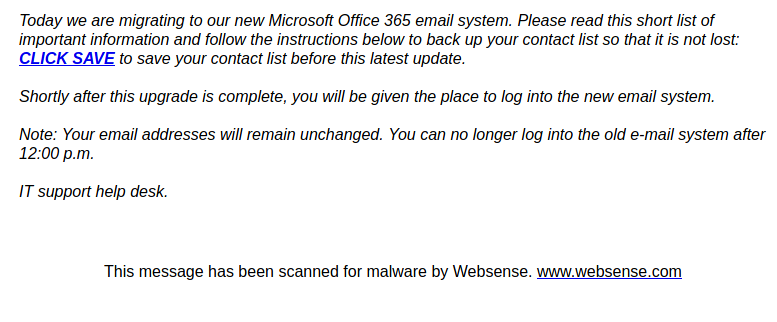
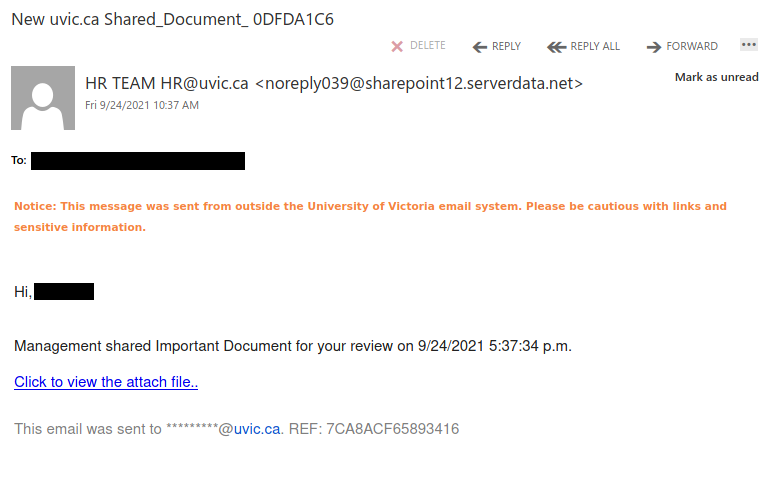
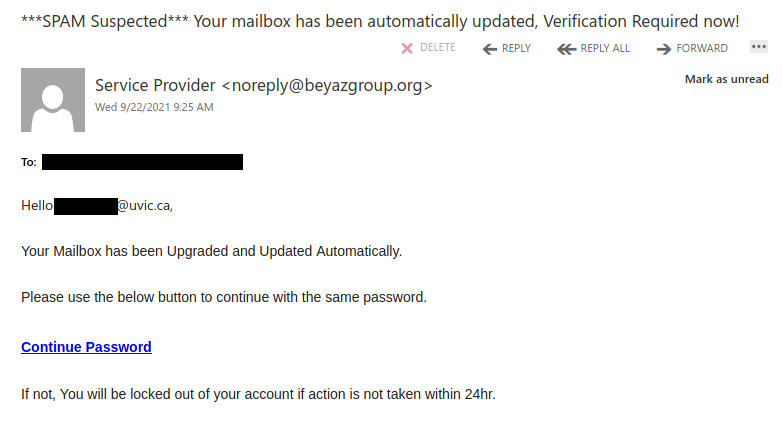
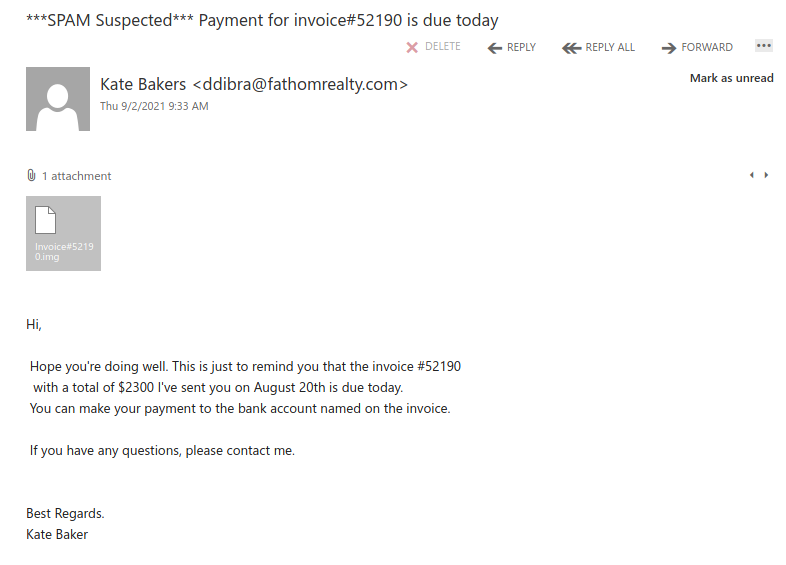
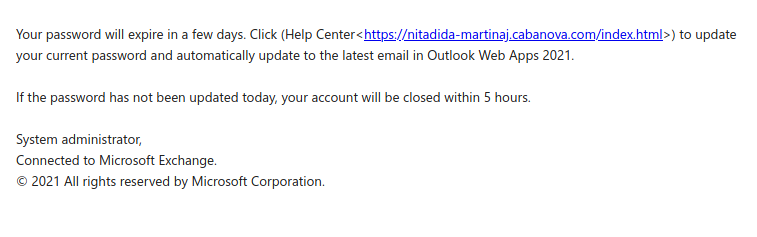
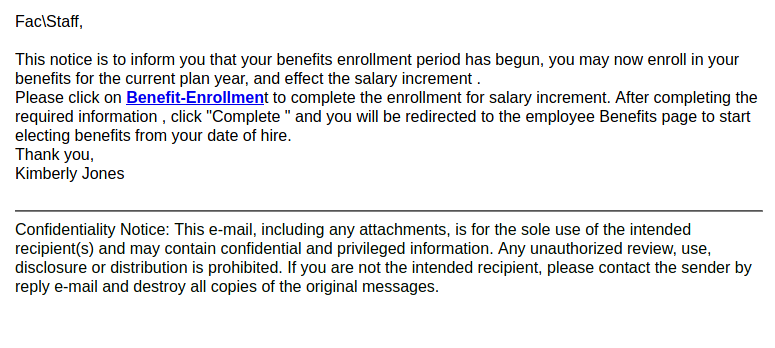
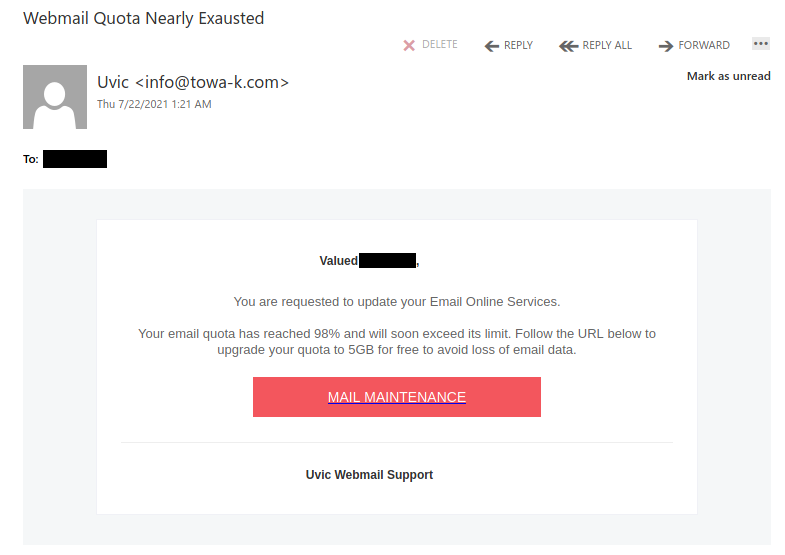
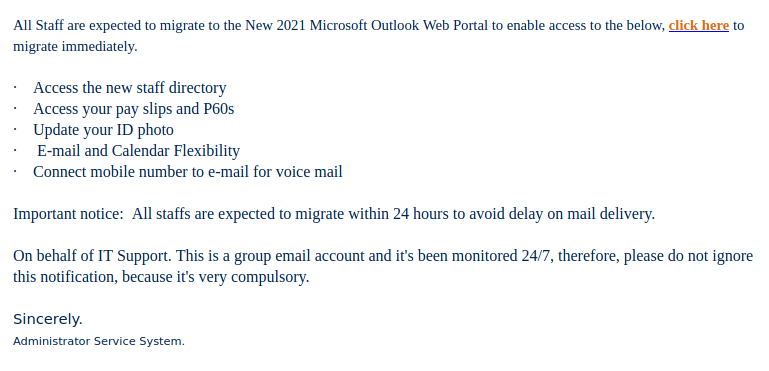
This spear-phishing email used a tailored sender display name, spoofed UVic email address and the UVic logo to make this spear phishing email look more legitimate. Unlike most other phishes, which tend to have a generic signature, the signature block here impersonates the UVic Computer Help Desk.
Though there are other red flags in the email’s contents, the smoking gun is the link–if you hover over it, you can clearly see that it goes to a suspicious non-UVic website (see the bottom of the screenshot). That website hosts a realistic copy of the UVic OWA login page, complete with the policy text. Don’t click on that link or enter your credentials on that page!
If you clicked on the link, contact your department’s IT support staff or the Computer Help Desk immediately.