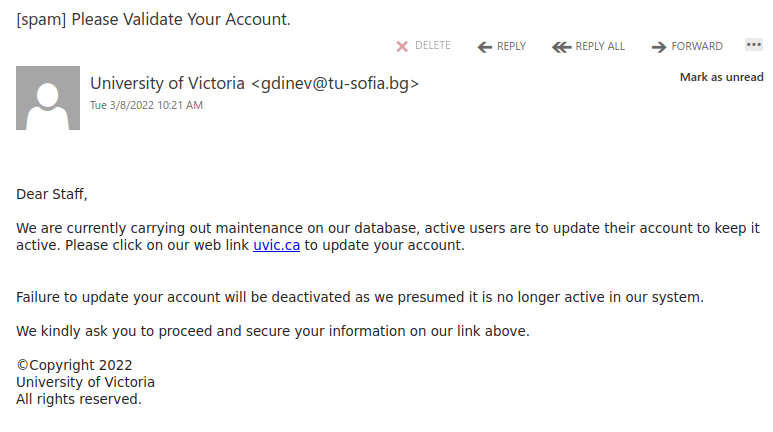
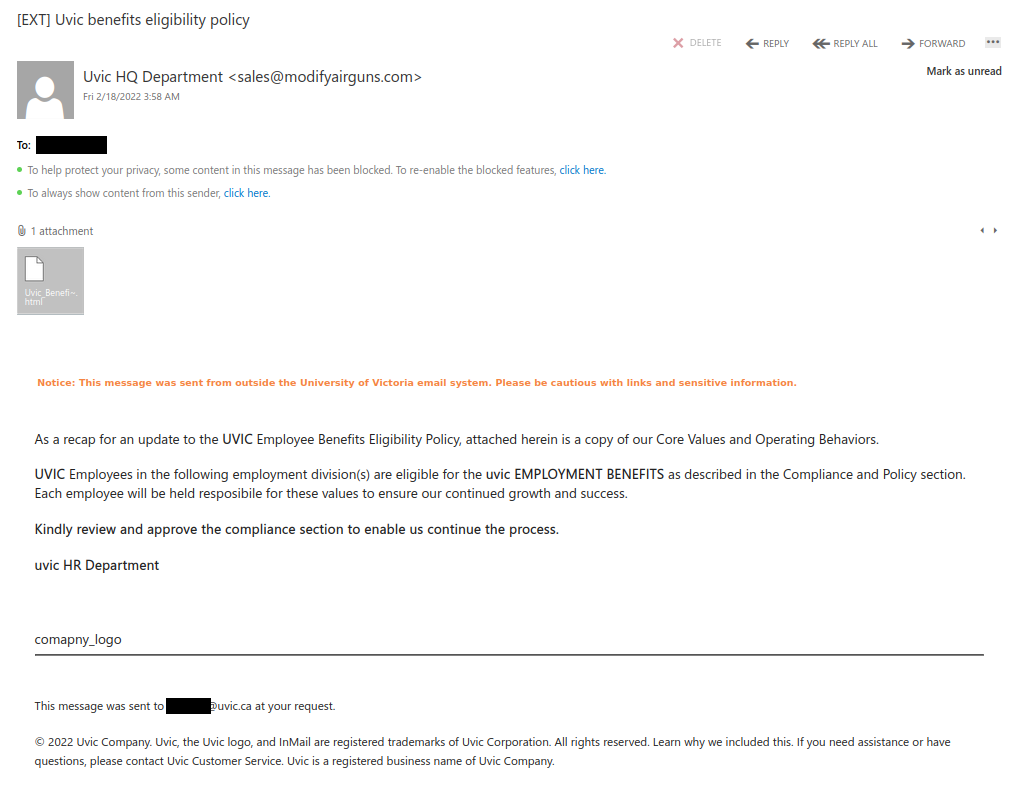
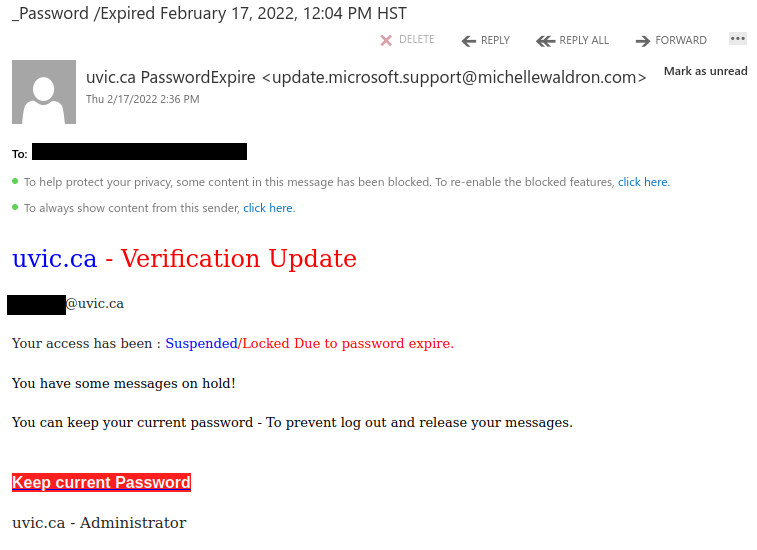
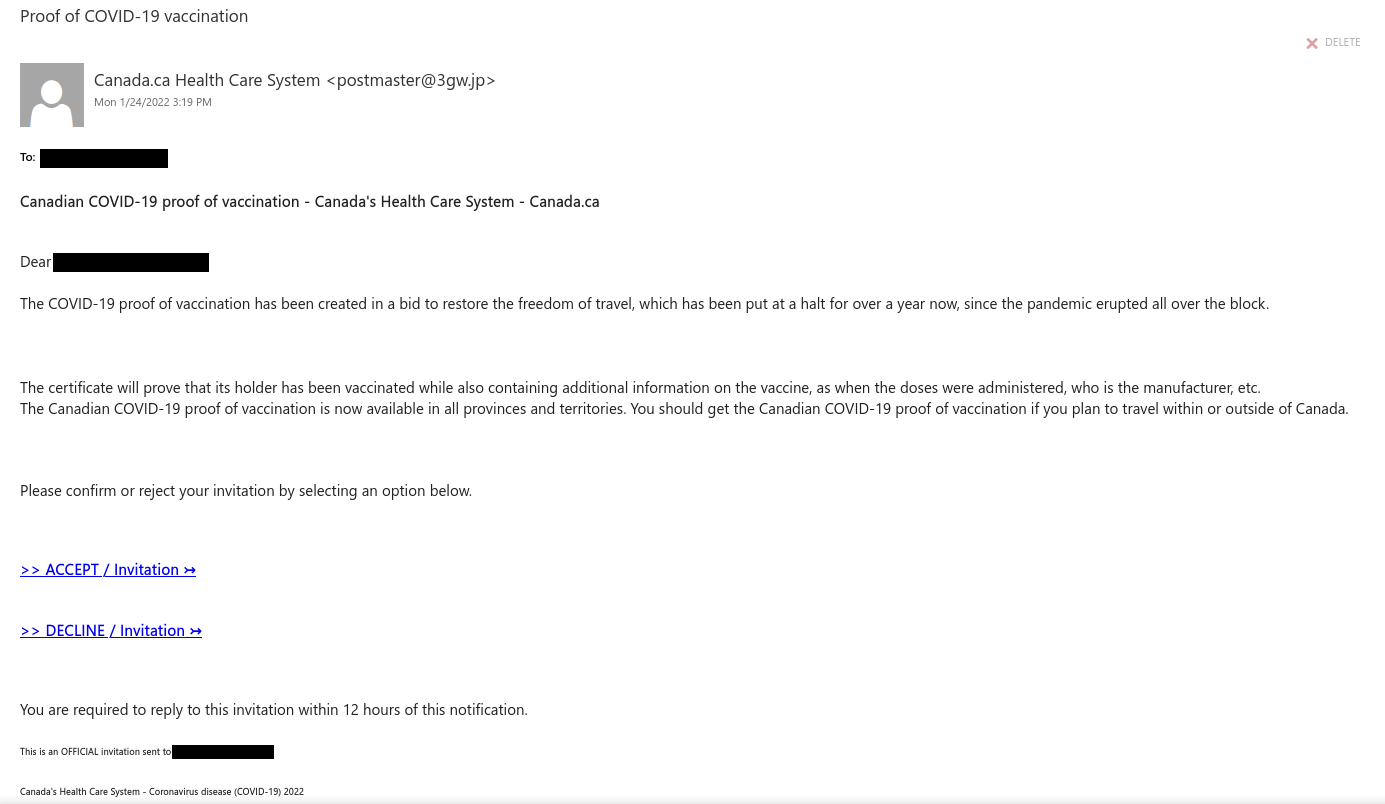
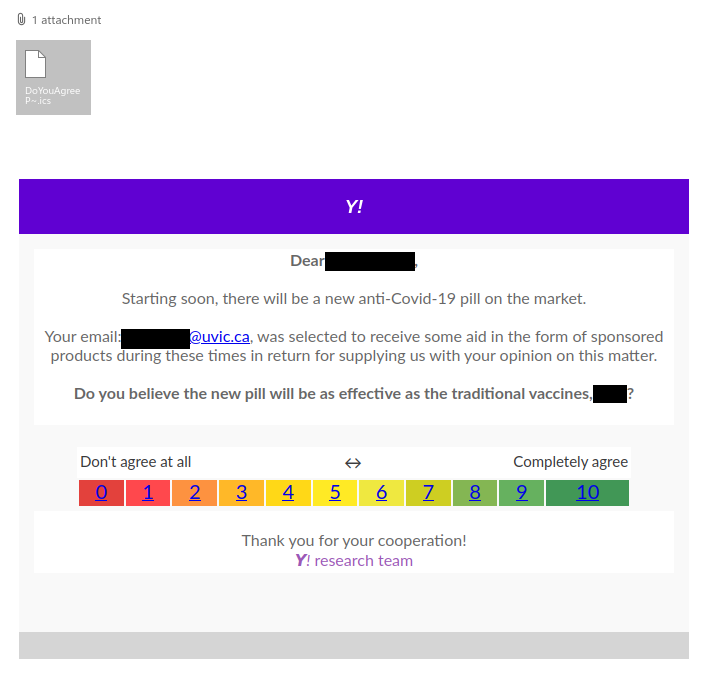
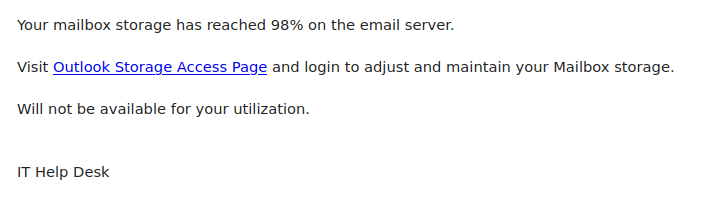
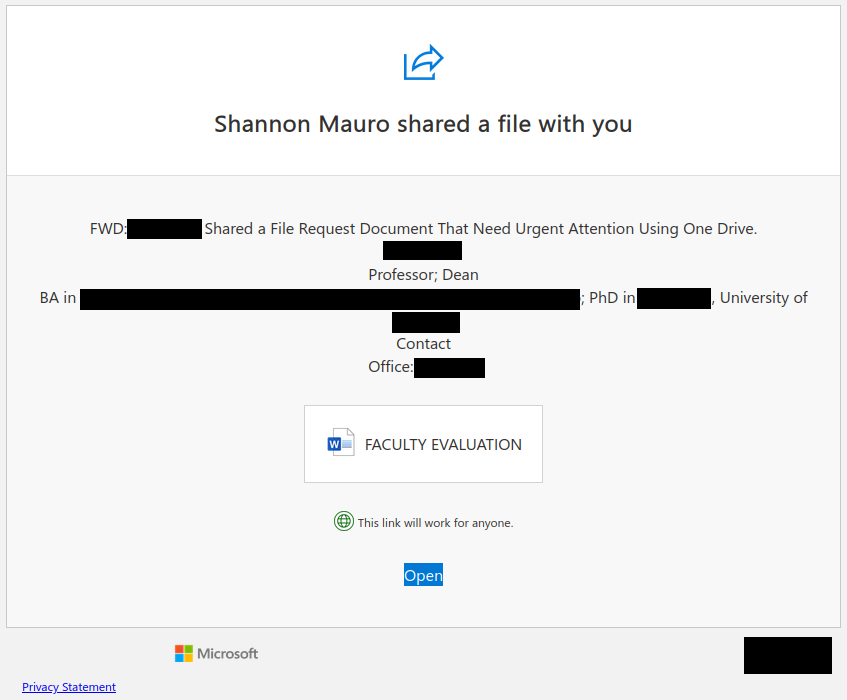
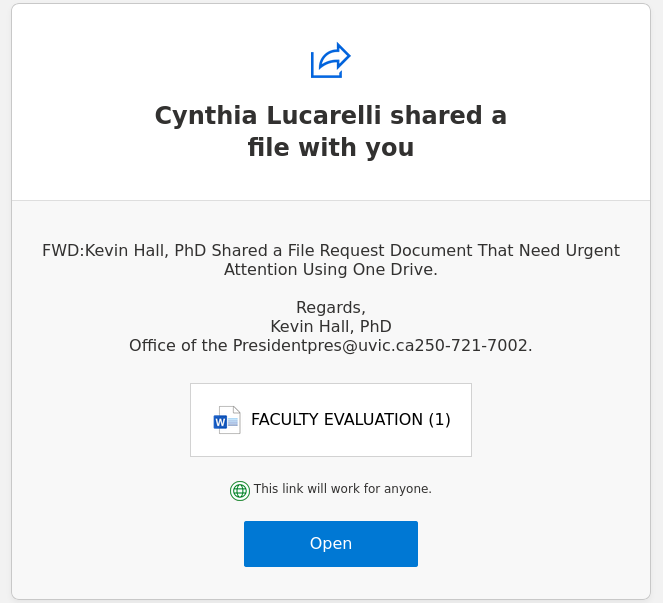
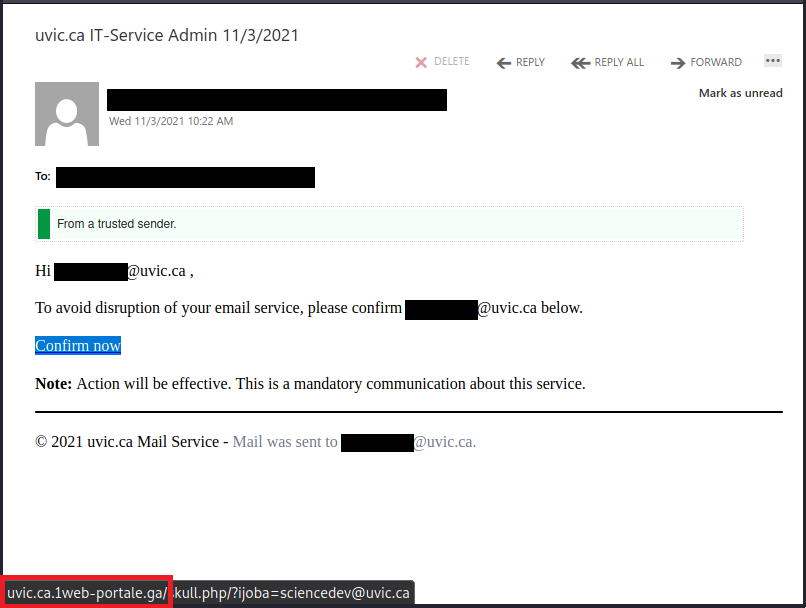
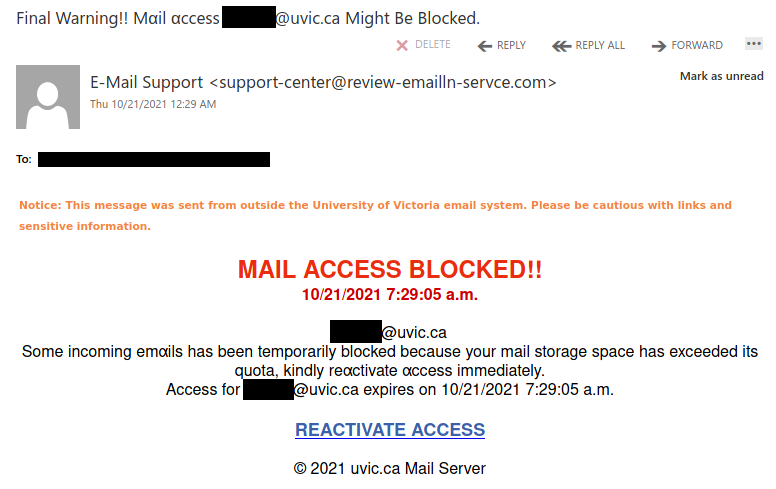
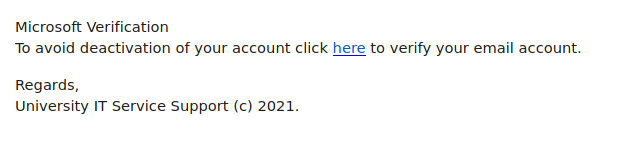
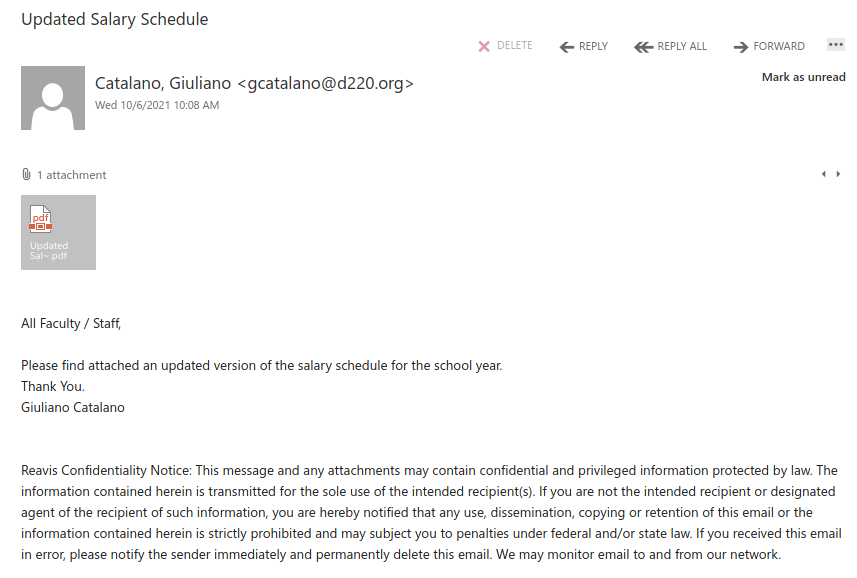
This is an example of a spear phishing email–it is designed to target the UVic community specifically. Notice how the actual sender address is not a UVic email address, even though the email claims to be from UVic (you may need to open/expand detailed sender information to see this if you are using a mobile app for email).
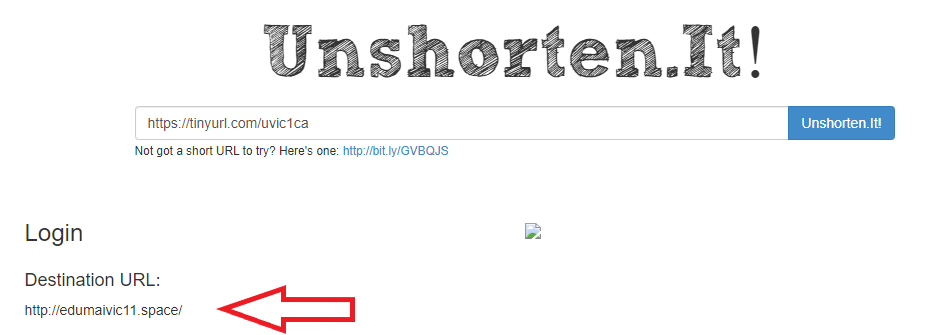
As always, hover over the link before you click. That link that says “uvic.ca” actually goes to a site that contains UVic in its name but actually ends in weebly.com. Weebly is a free website builder; phishers love to abuse such services to create phishing sites. No real UVic login page would ever be hosted on Weebly or any other free website or form builder.
If you clicked on this link, contact your department’s IT support staff or the Computer Help Desk immediately.