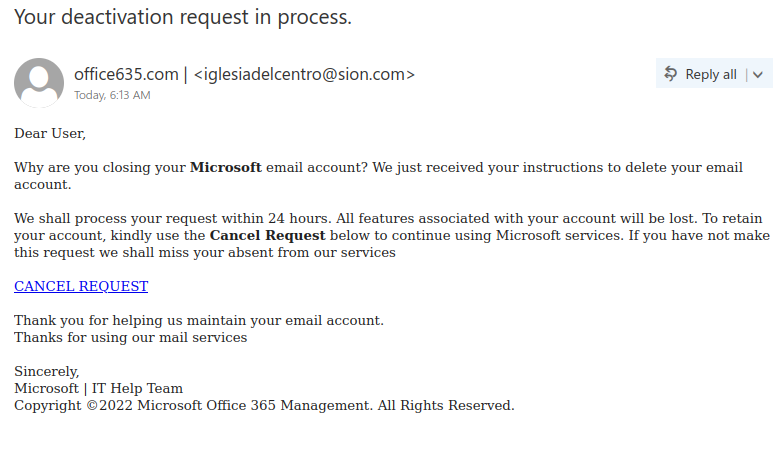
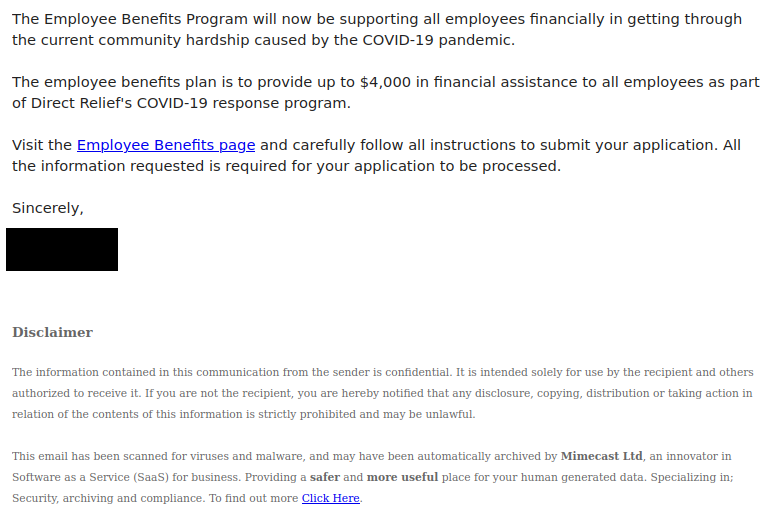
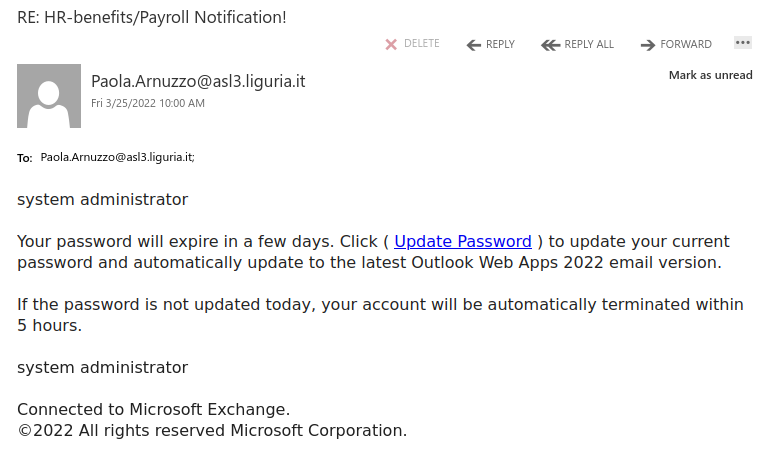
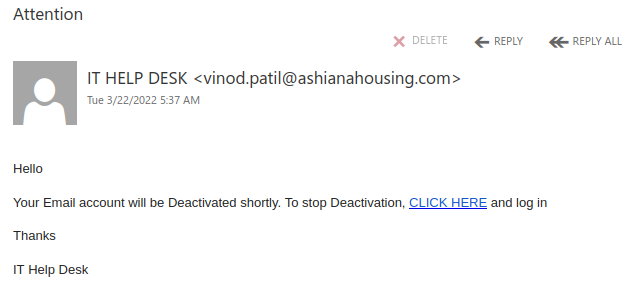
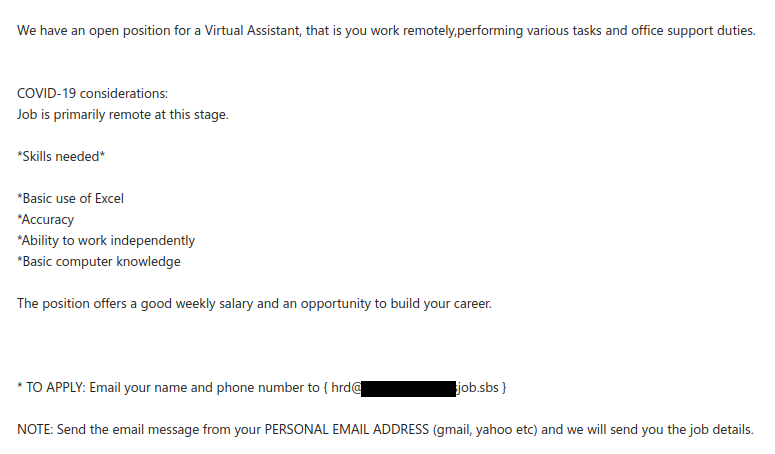
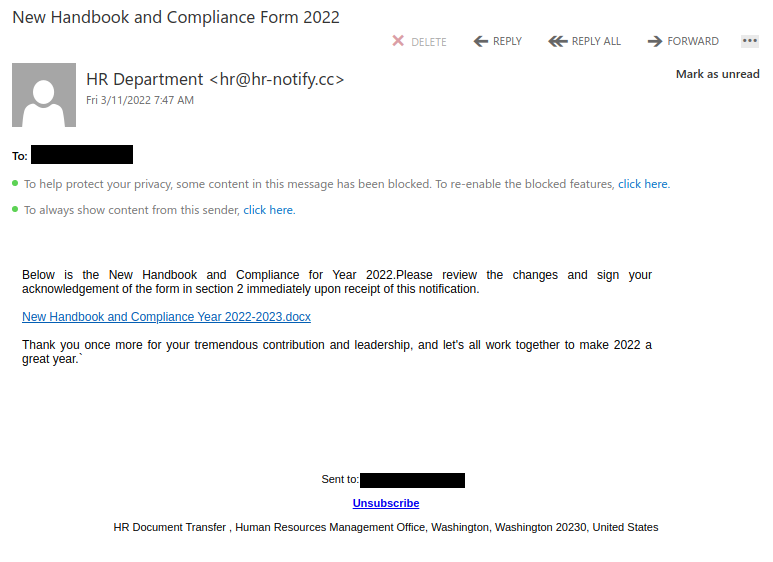
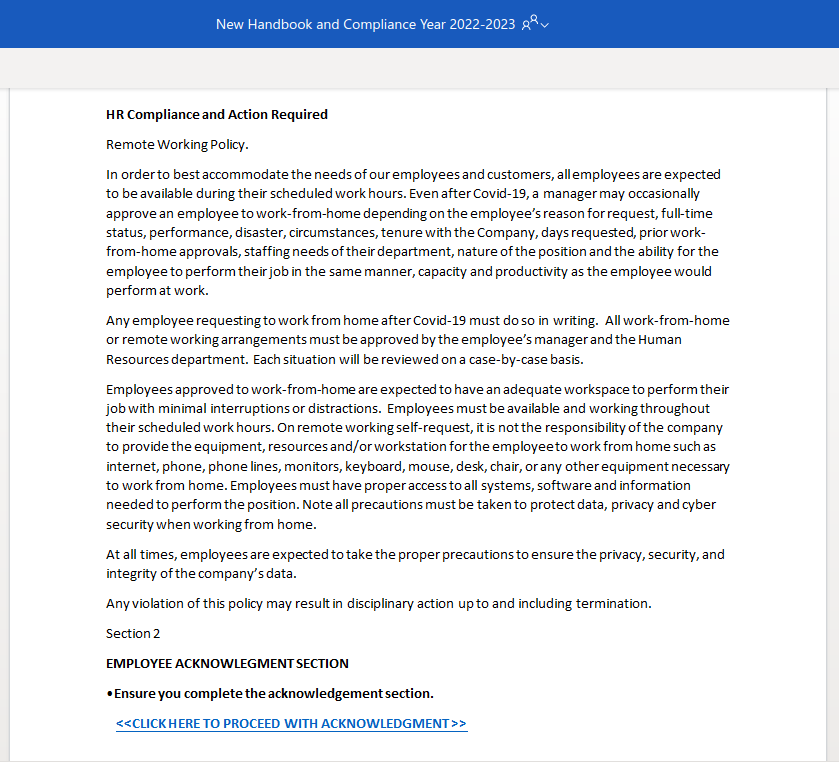
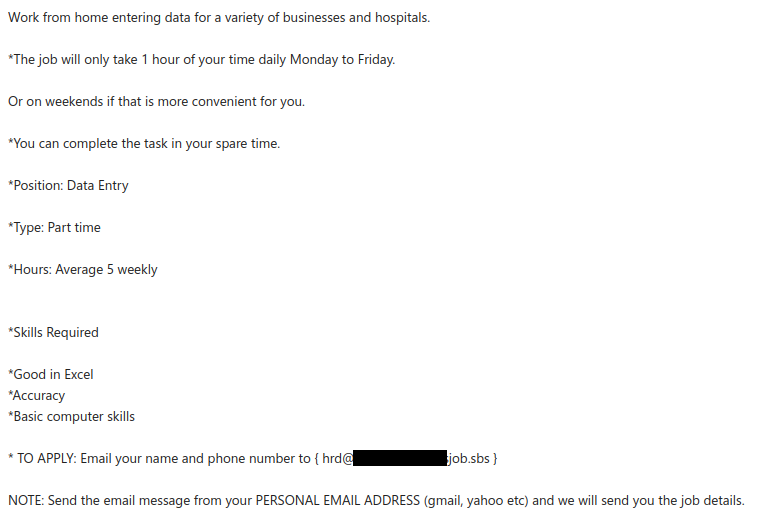
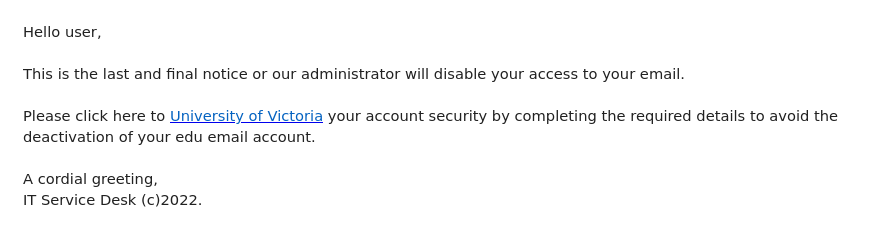
Like many other Microsoft-themed phishing messages, this one uses the threat of impending account deactivation to get you to hastily click on the link. But take a moment to look closely and you’ll spot a lot of red flags:
- The sender display name contains an error (office635)
- The sender email address is not from Microsoft (or UVic, for that matter)
- The greeting is impersonal
- The message contains a good deal of awkward wording and grammatical errors
Hovering over the link is also a good idea–that would show that it doesn’t go to a Microsoft website.