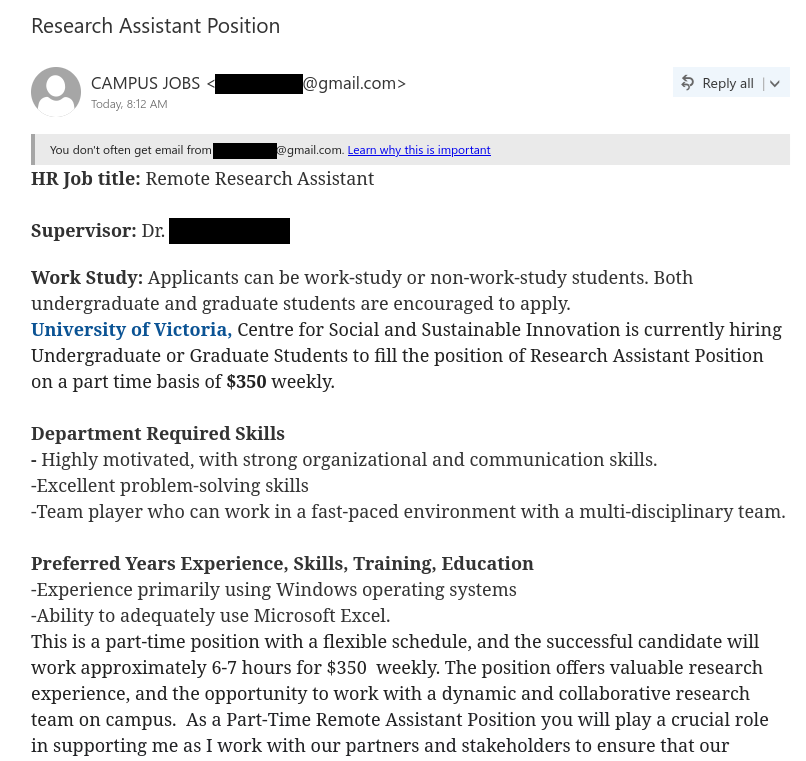
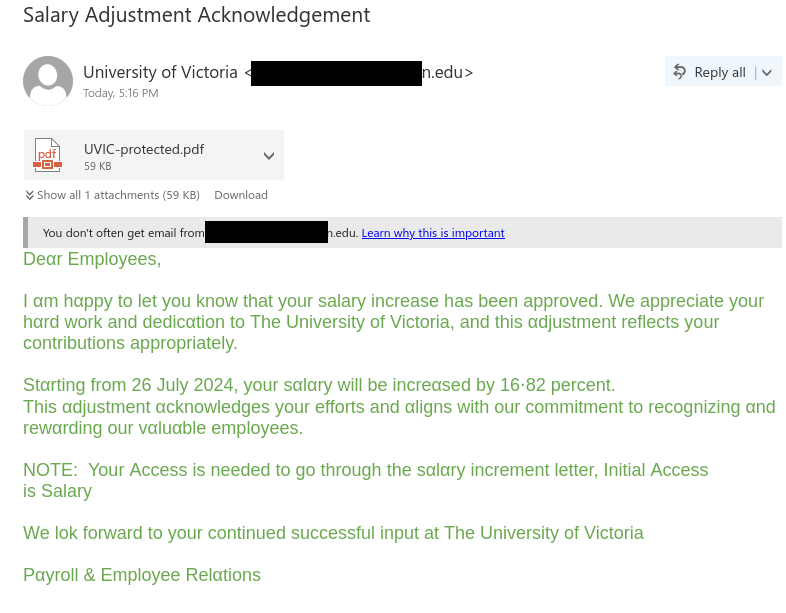
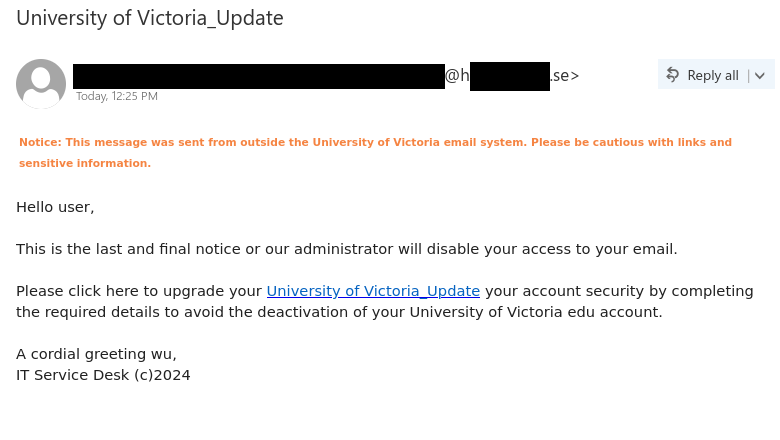
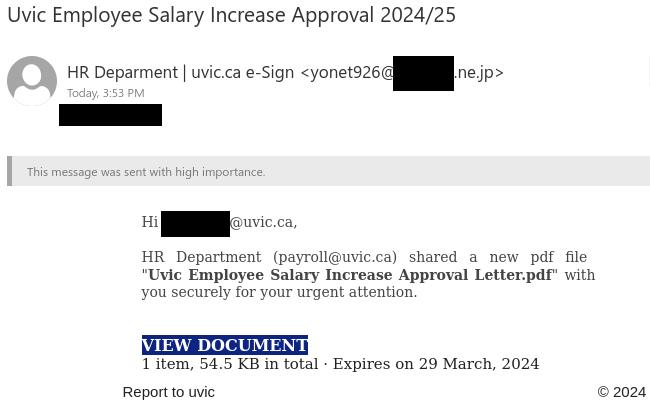
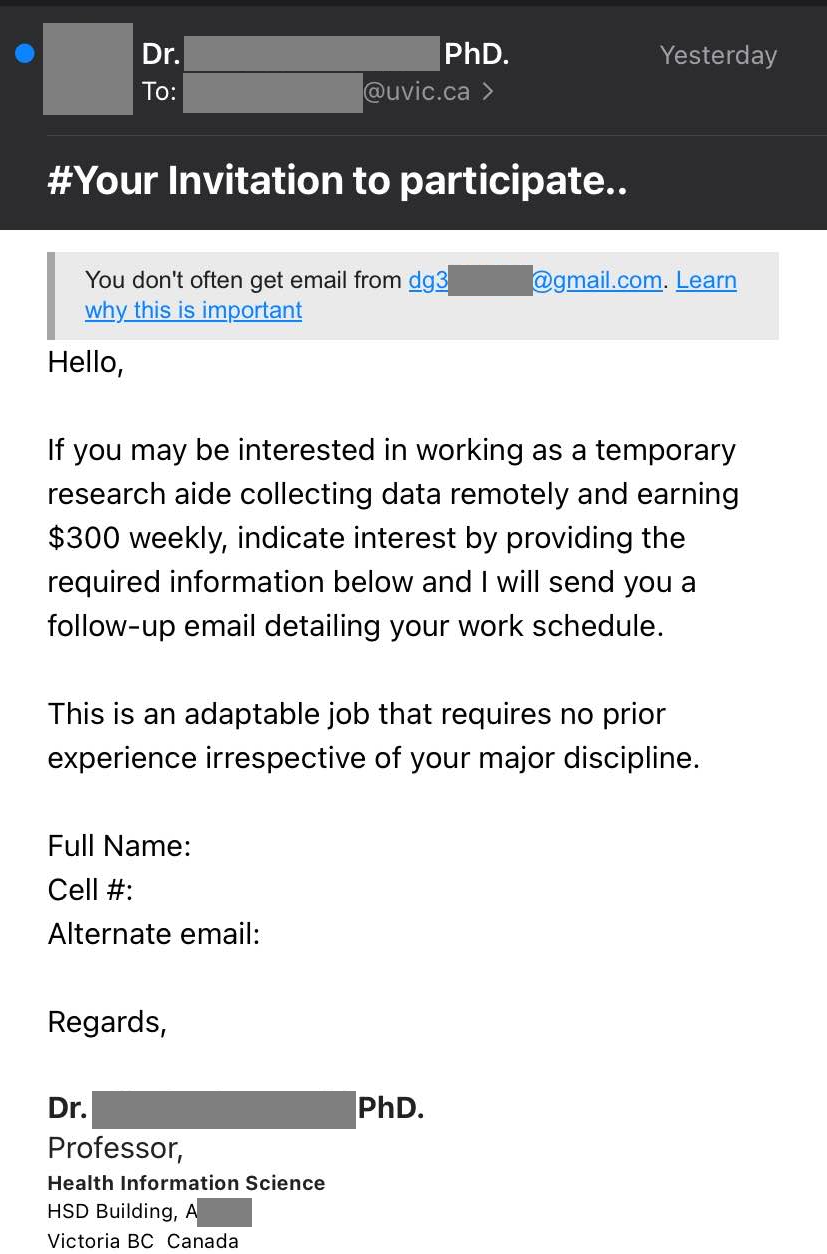
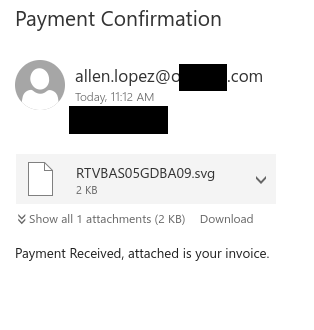
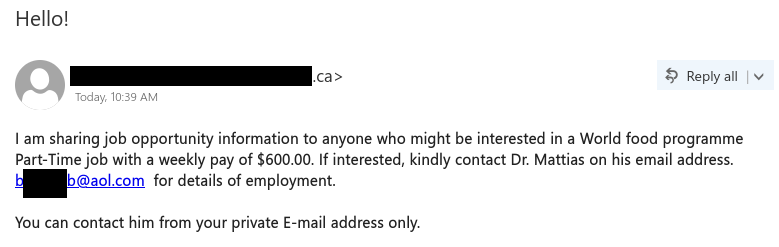
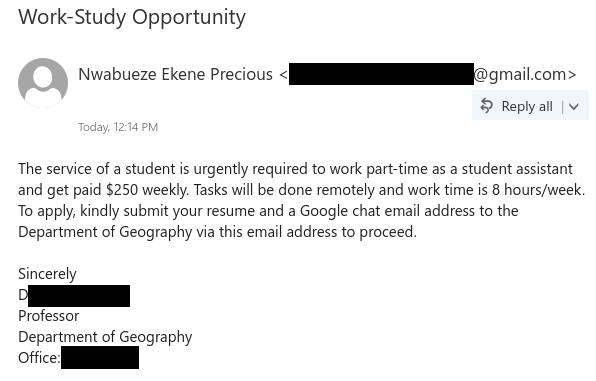
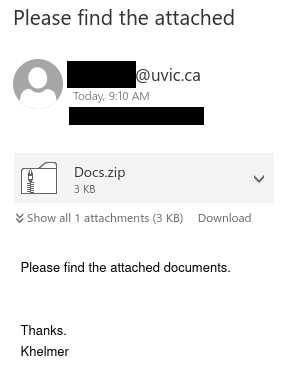
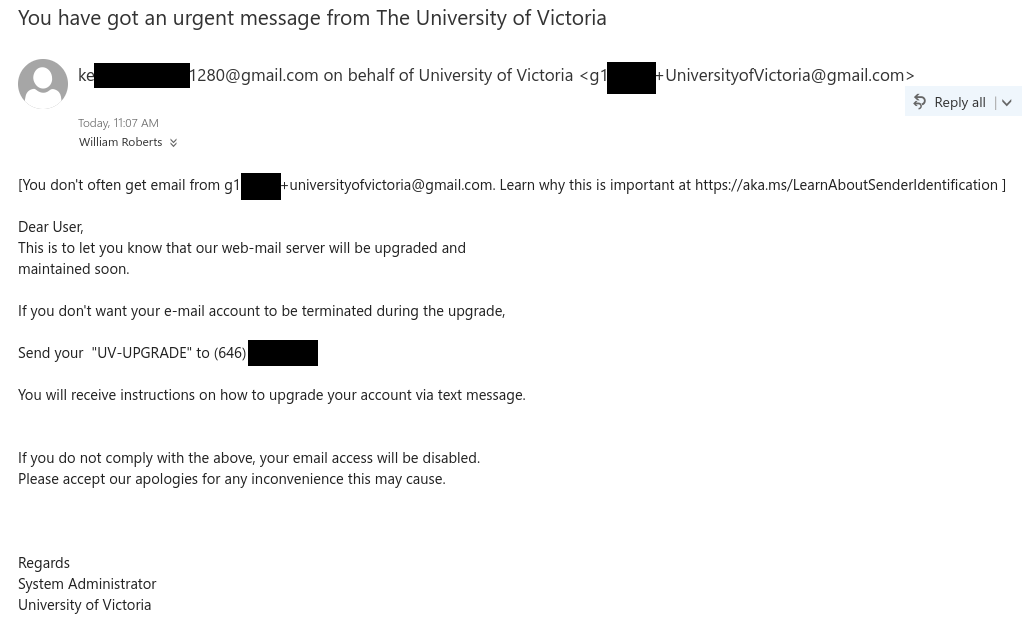
Job scams aren’t the only way that scammers try to take advantage of students in financial need–they are also sending out scam emails claiming to offer grant money. In this case, the tantalizing offer of a few thousand dollars that don’t need to be paid back is very likely to be a pretext for a cheque overpayment scam.
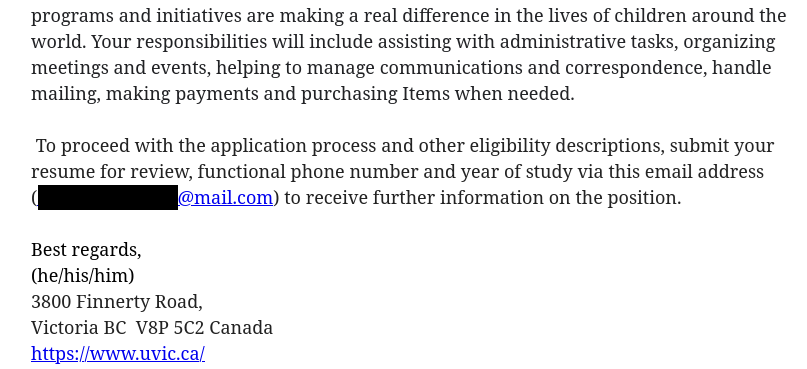
Notice how the email says you are supposed to use almost half of the funds for “humanitarian service for a disabled student”. In all likelihood, that means that the scammer will tell you to cash the cheque and then send some of the money to another person or bank account specified by the scammer. A few days after you do that, the cheque will bounce and the money you transferred will effectively come out of your own funds, meaning you’ll have lost a non-trivial amount of money. (Also, the scammer’s math doesn’t add up; $2700 + $2200 = $4900 and that’s more than the amount on the cheque!)
In addition to the above, there are many other red flags:
- The email was not sent from UVic, a provincial government (such as gov.bc.ca), or the federal government (canada.ca or something ending in gc.ca).
- You are told to apply by emailing an Outlook.com email address. If you are told to contact an address from a free email provider, the grant is very likely to be a scam.
- The scammer wants you to reply from your personal email and provide your mobile phone number. Scammers use this tactic to move the conversation away from UVic’s monitoring and security controls.
- The scammer also asks you to email other personal information like your address and where you bank.
- The greeting is impersonal.
- The email contains awkward wording and grammatical errors.
- The signature of “Canada Student Grant” is vague/generic and does not mention UVic or a specific government department.
- While the message looks like normal text, the whole thing is actually an image–that’s a strong sign that the message is not legitimate and the scammer has done that to evade spam filters.
If you replied to this email, cease contact with the scammer and reach out to the Computer Help Desk immediately for assistance.
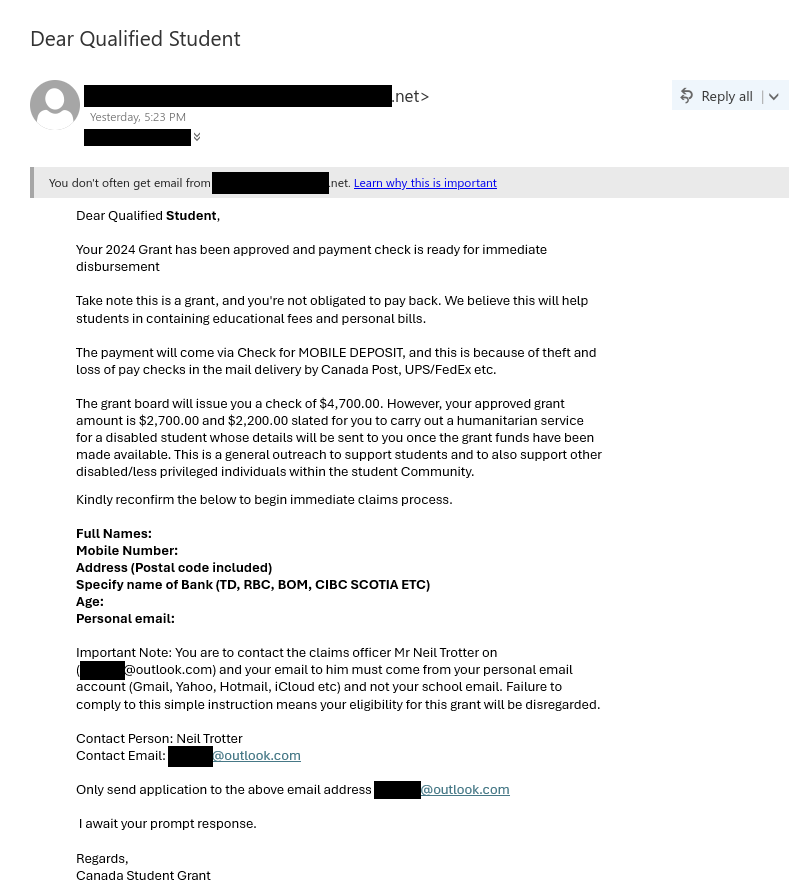
From: [redacted]@[redacted].net
Subject: Dear Qualified StudentYou don’t often get email from [redacted]@[redacted].net. Learn why this is important.
Dear Qualified Student,
Your 2024 Grant has been approved and payment check is ready for immediate disbursement
Take note this is a grant, and you’re not obligated to pay back. We believe this will help students in containing educational fees and personal bills.
The payment will come via Check for MOBILE DEPOSIT, and this is because of theft and loss of pay checks in the mail delivery by Canada Post, UPS/FedEx etc.
The grant board will issue you a check of $4,700.00. However, your approved grant amount is $2,700.00 and $2,200.00 slated for you to carry out a humanitarian service for a disabled student whose details will be sent to you once the grant funds have been made available. This is a general outreach to support students and to also support other disabled/less privileged individuals within the student Community.
Kindly reconfirm the below to begin the immediate claims process.
Full Names:
Mobile Number:
Address (Postal code included)
Specify name of Bank (TD, RBC, BOM, CIBC SCOTIA ETC)
Age:
Personal email:Important Note: you are to contact the claims officer Mr Neil Trotter on ([redacted]@outlook.com) and your email to him must come from your personal email account (Gmail, Yahoo, Hotmail, iCloud etc) and not your school email. Failure to comply to this simple instruction means your eligibility for this grant will be disregarded.
Contact Person: Neil Trotter
Contact Email: [redacted]@outlook.comOnly send application to the above email address [redacted]@outlook.com
I await your prompt response.
Regards,
Canada Student Grant