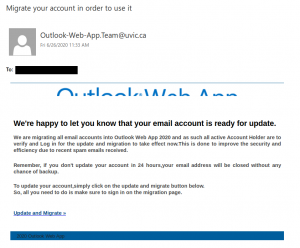
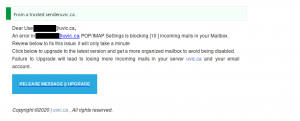
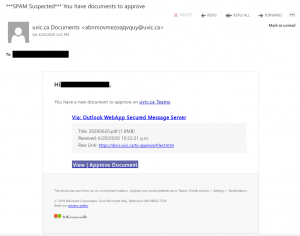
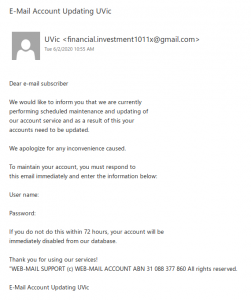
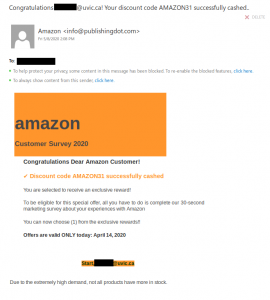
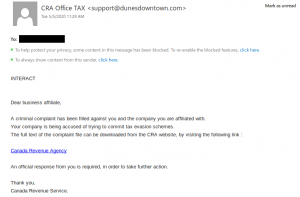
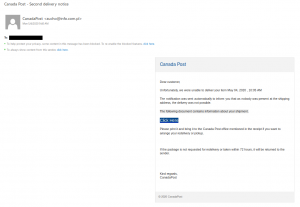
No doubt you’ve all seen a classic advance fee scam. A stranger emails you asking for assistance in transferring a large amount of wealth that they say they own but can’t access, offering you a cut of it in return. Most of the time, these scams are sent en masse and not targeted to the recipient.
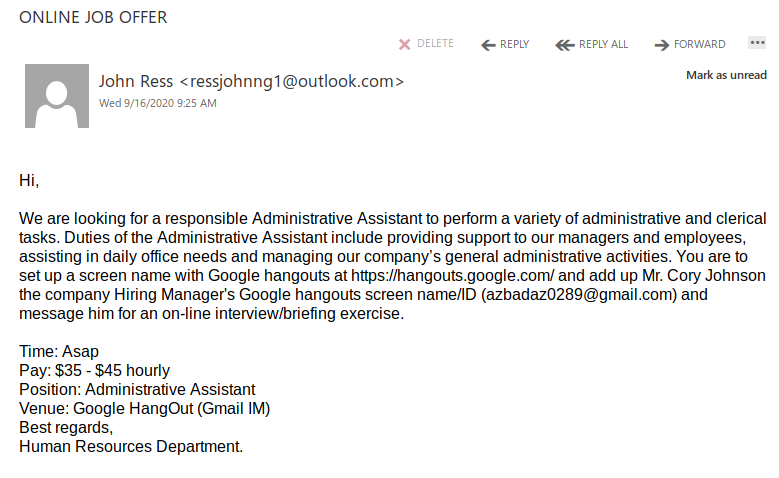
However, a bunch of UVic employees recently received a more targeted variant of this scam where the writer poses as someone wanting to come to UVic:
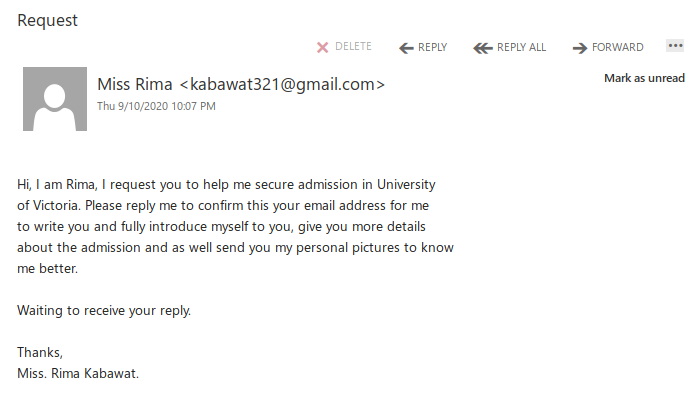
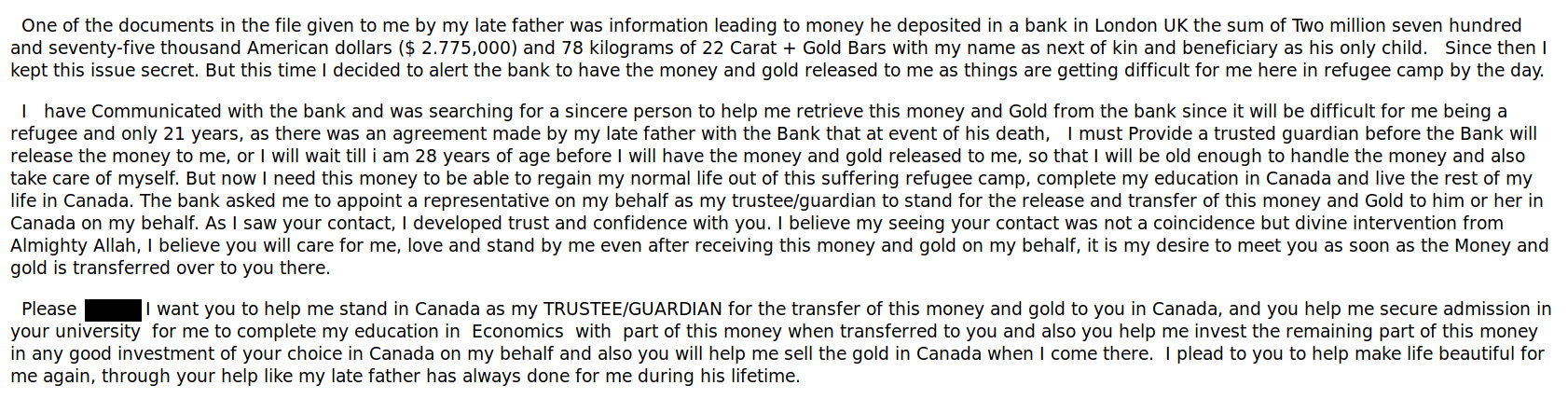
Those who reply will receive a lengthy letter back. For brevity’s sake I won’t post the whole thing, but here’s the part that makes it clear that this is just another advance fee scam. Note: you can right-click on the image and choose to open it in a new tab or window to view it at full size if the font is too small for your liking.