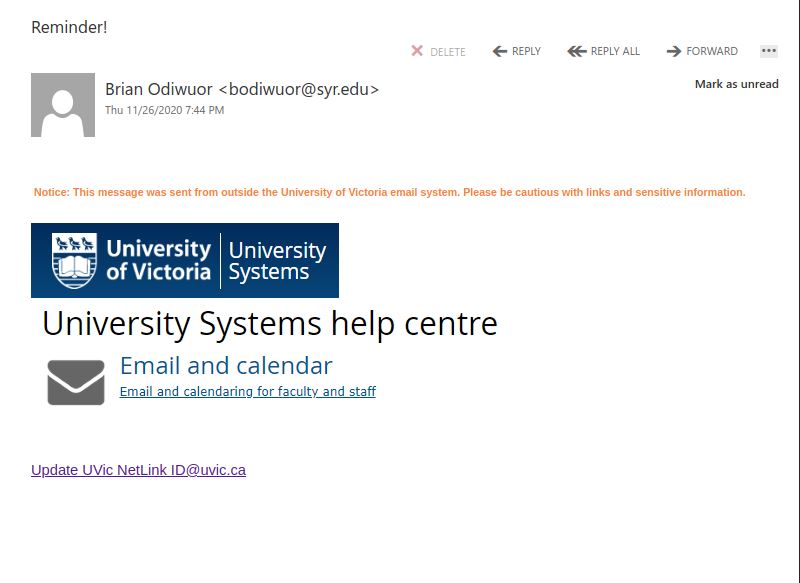
Subsequent to the Fake Microsoft logon this morning, urgent deactivation messages are suspect. We do not send out such messaging.
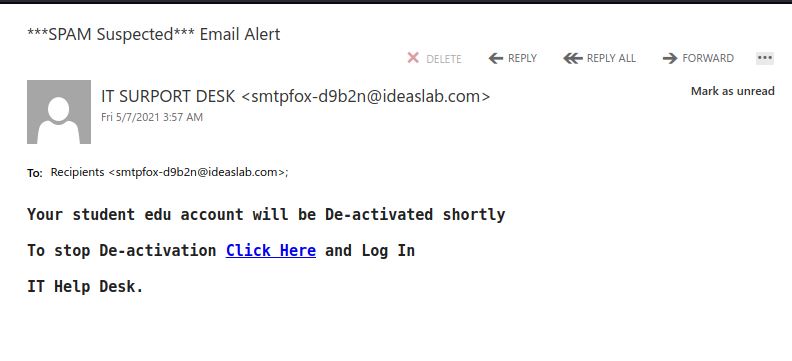
In this case the malicious or compromised Weebly site was already taken down.
Subsequent to the Fake Microsoft logon this morning, urgent deactivation messages are suspect. We do not send out such messaging.

In this case the malicious or compromised Weebly site was already taken down.
Pause when you feel sense of urgency and when it doubt, simply contact the Computer Help Desk. We /Microsoft do not have extreme/urgent account disconnection notices or implementations or deadlines.
NOTE: Microsoft does not host their services on WordPress or Weebly. These and other free web hosting services are commonly abused/compromised for such phishing campaigns.
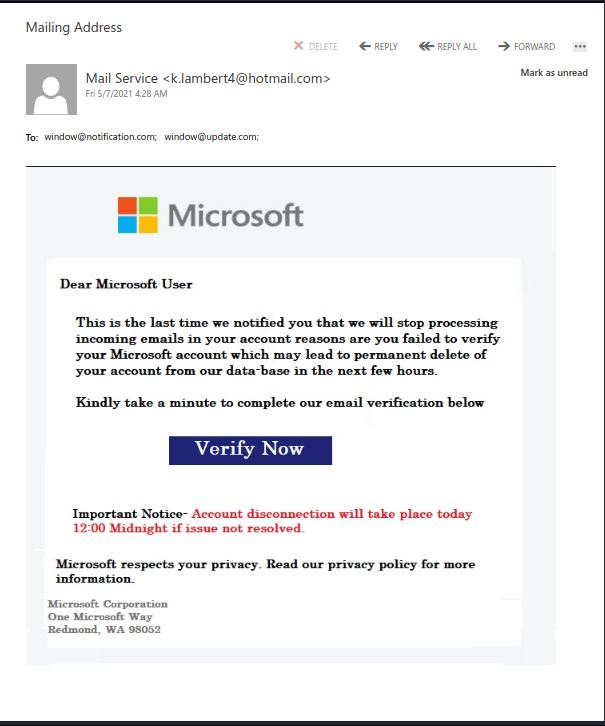
The Verify Now button will lead to a Fake Microsoft My Activation page hosted on a compromised WordPress site.

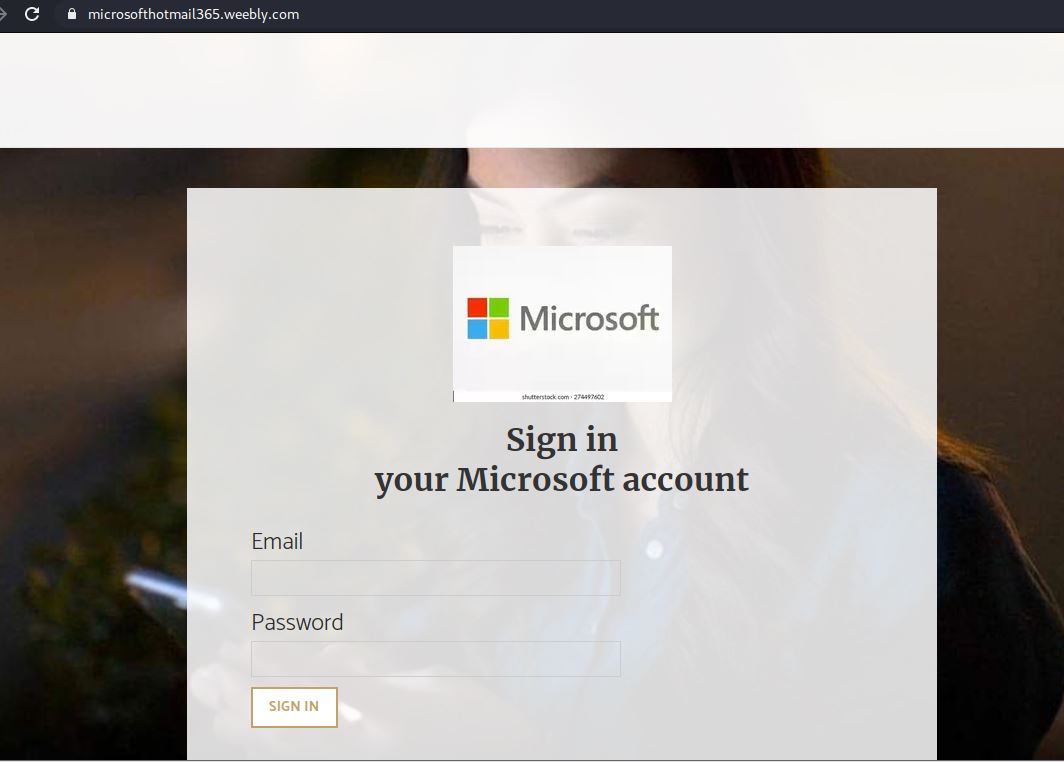
The Click Here button will land you on Fake Microsoft Logon page hosted on a compromised or malicious Weebly site.
Do not use buttons provided in a suspect page (eg. Close and accept button above). If you’d proceeded this far, simply close the whole browser instead and inform your IT Support contact.
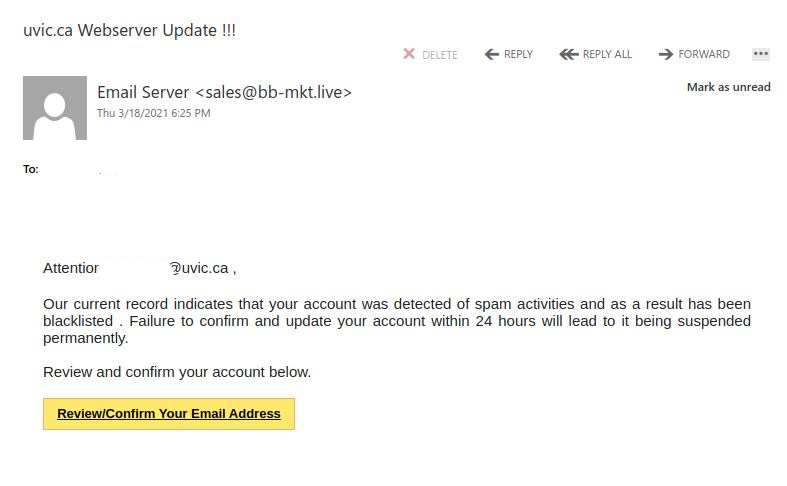
Another scare tactic suggesting your account has been blacklisted. On occasion you may have challenges with your account due to forgotten passwords, password changes or potential compromise from clicking on links in emails such as these but typically this can be rectified with a quick call to the Computer Help Desk.
Pay attention to your sender email as well.
If in any doubt whether there is a problem, instead of opening attachments or clicking links, check to see if you can use it as you normally would for UVic service access. You can always contact the Computer Help Desk to verify its authenticity as well.
Thank you for continuing to report these.
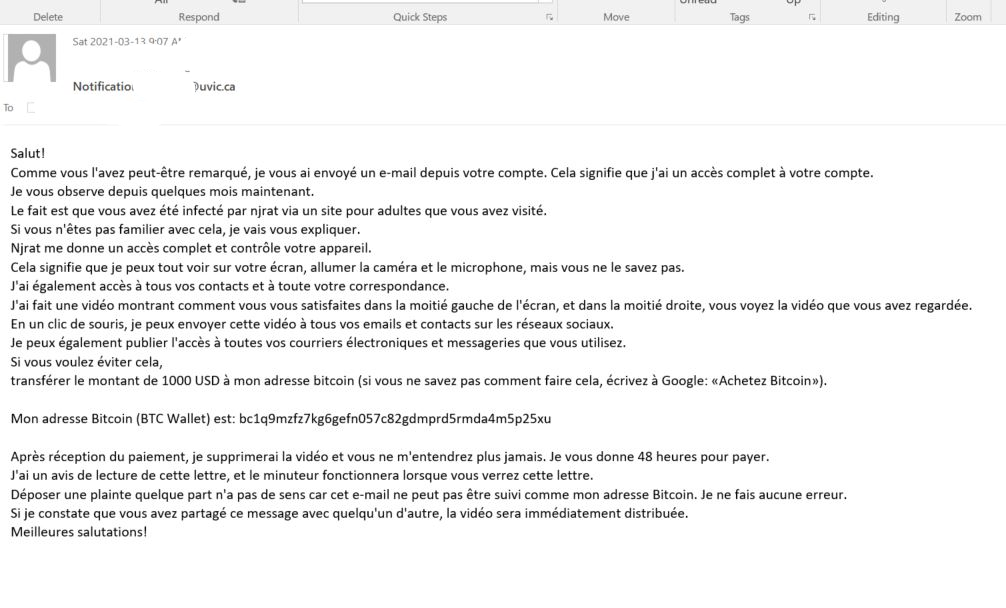
Over several years now we have seen various versions of extortion type emails where the criminal attempts to scare you into thinking they have some sort of damaging or embarrassing piece of information about you. Over the weekend we saw a such emails, that happen to be in French and reporting they have hacked your system, stole your photos etc and are using a Bitcoin Exchange to have you reply to their ransom. The included link is a link to a bitcoin exchange service.
These weekend versions also spoof/fake your email address and lead you to believe that perhaps your email account was hacked or is being misused. It can happen, yes, but those we’ve seen in this run are fake messages that only look like they were sent via your email address.
These two examples are only some of the variants you may see. Next week they may be in English or another language. Sometimes they capture an old password you used from old password breaches and scare you by putting a copy of that password in the subject line.
Important: If you haven’t changed your passwords in a long time and you reuse, please change them now to longer and unique passphrases for every service.
It is scary to see that someone has discovered an old password but less scary when you know you are now practicing better passphrase and account management.
Second sample email and English translation below:
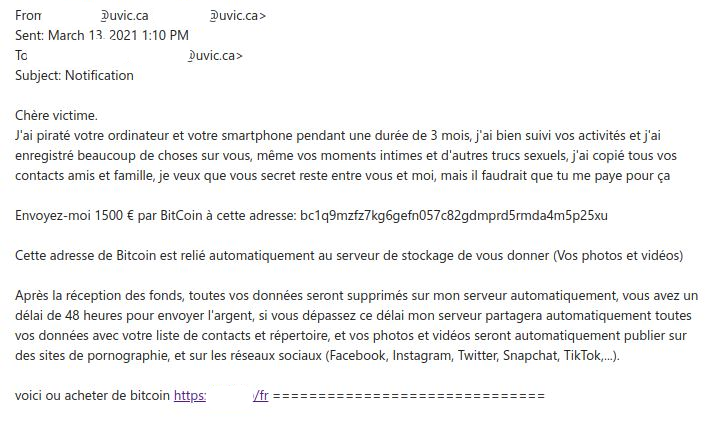
English Translation:
Dear victim. I hacked your computer and your smartphone for a period of 3 months, I followed your activities well and I recorded a lot of things about you, even your intimate moments and other sexual stuff, I copied all of them your friends and family contacts, I want you secret to stay between you and me, but you would have to pay me for that Send me 1500 € by BitCoin to this address: bc1q9mzfz7kg6gefn057c82gdmprd5rmda4m5p25xu This Bitcoin address is automatically linked to the storage server to give you (Your photos and videos) After receiving the funds, all your data will be deleted on my server automatically, you have a 48 hour deadline to send the money, if you exceed this deadline my server will automatically share all your data with your contact list and directory, and your photos and videos will automatically be published on pornography sites, and on social networks (Facebook, Instagram, Twitter, Snapchat, TikTok, ...). here is where to buy bitcoin https://<redacted>==============================
Fake password expiry notice encouraging a webmail logon.
Attempted to encourage you to click as soon as possible by giving you a deadline and scaring you into thinking you won’t be able to access your account.
Account and password management processes will always follow known UVic procedures and any hiccups with accounts can typically be alleviated relatively quickly by contacting the Help Desk at helpdesk@uvic.ca or calling them directly when you encounter a problem. We do not encourage or force changes via email or phone calls.
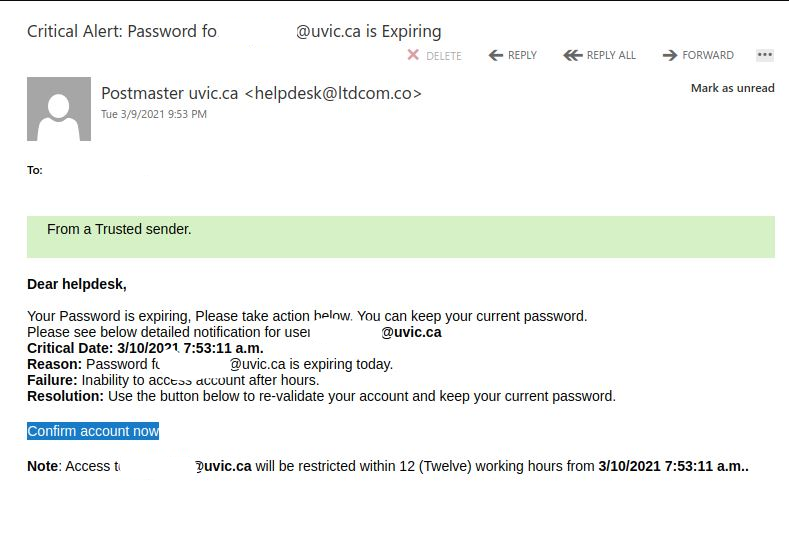
Another attempt to toy with your sense of urgency this morning.
We have normal processes through your regular logon and use of UVic Services for any required password changes, if there is ever need for them.
As a general rule, we really do not want you to “keep the same password” or reuse them. If you change your password because you think someone may have guessed it, its time to make it significantly different and more importantly, longer.

Today’s phish (multiple versions) did land on a fake version of our UVic logon page and some of them have already been taken down.
Sharing this version with email content for reference.
Although many phishing emails will look as if they are coming from a known contact or service, note the sender address here.
There is a link named with the uvic.ca name but if you hold your mouse over the link (without clicking) you will see that this is not a UVic service at all, never mind a UVic Sharepoint service.
NOTE: There have been varying versions of this one throughout the day with Shared Contracts, Memos etc.
Thank you for continuing to report these!
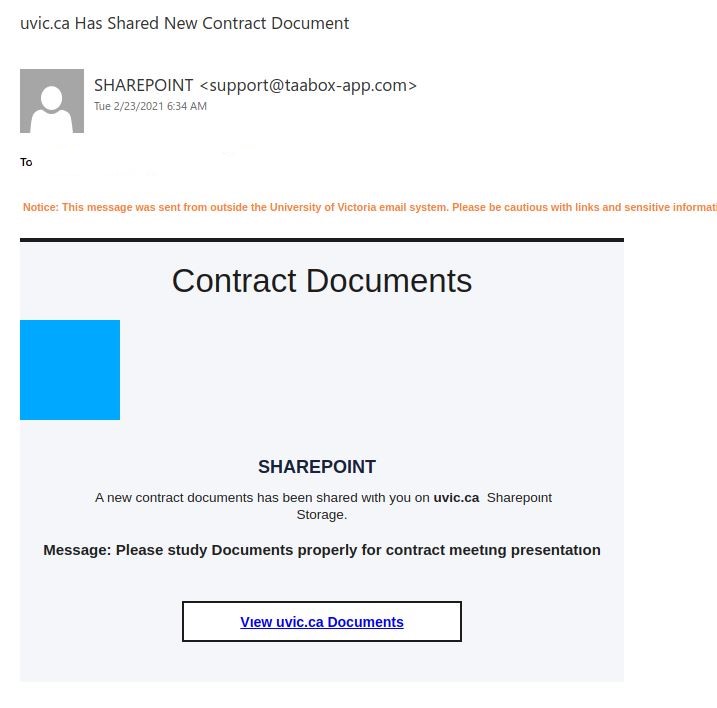
Phishing email using our University of Victoria Logo. Note the sender email and the external email banner.
Visiting link will bring you to Fake M365 logon page which has nothing to do with UVic:
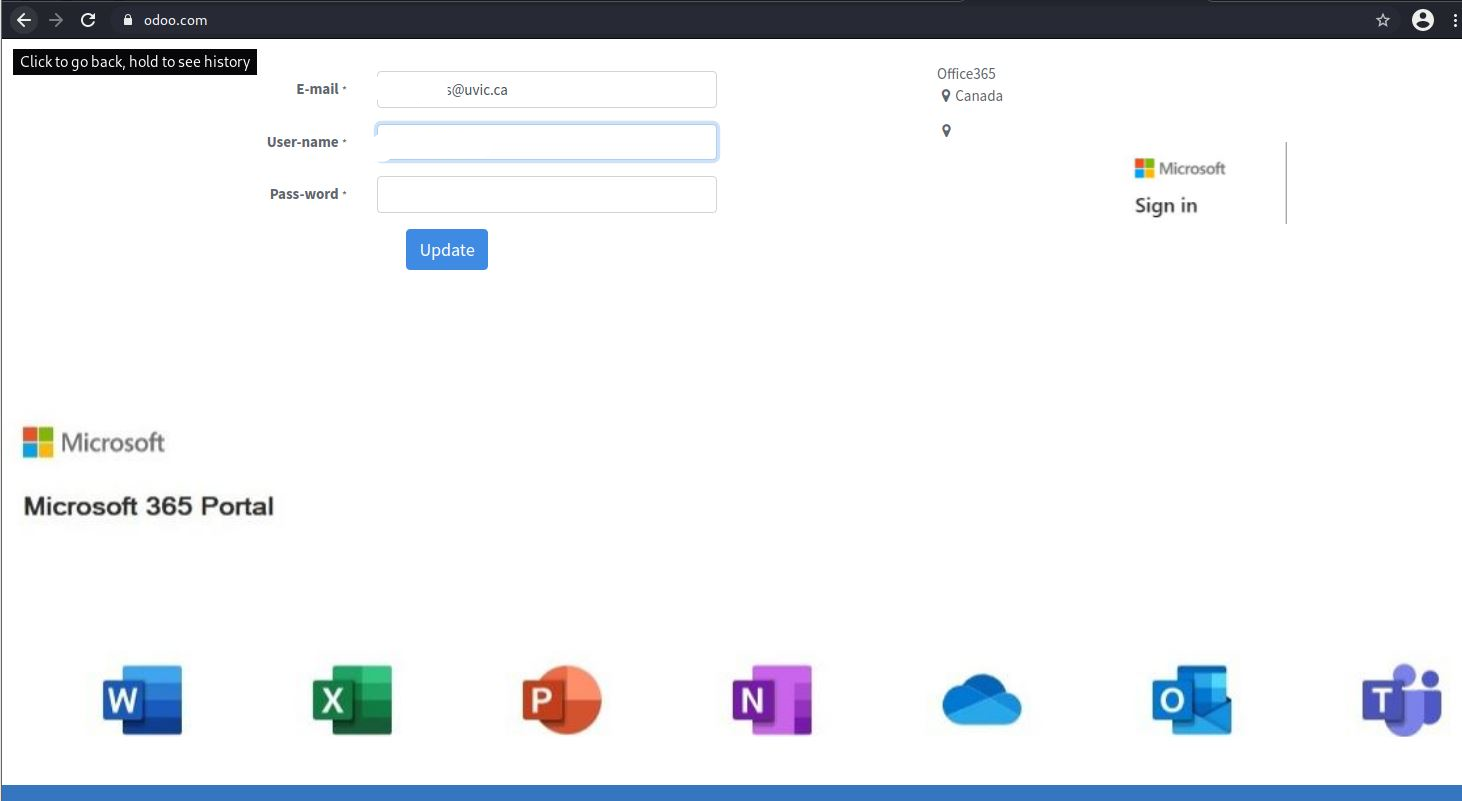
With the overall increased usage of M365 by many, it is important to be careful as criminals will attempt to deceive you with the “newness” of various products.
Check for valid senders and review the Internet Address/URL closely.
Whenever in doubt, go directly to known good logon windows and refrain from using links in email.
This one emphasizes the need to consider where you are accessing files from and how you expect them to be shared with you. UVic managed services are the only recommended way to share UVic work related documents.
This one is tricky. You cannot rely on the visible senders here so much and of course there is some comfort in seeing they are using your legitimate name and email address. The supposed download also has Uvic in the name. NOT LEGIT.
The caution here is, now that many of us are working from home and with the growth of cloud service use, specifically Microsoft and other big name products, we are becoming more comfortable with the idea that we may receive something legit from those sources. If you look at the body of this message, it does look phishy but it also looks as if it is coming from a known good Microsoft domain.
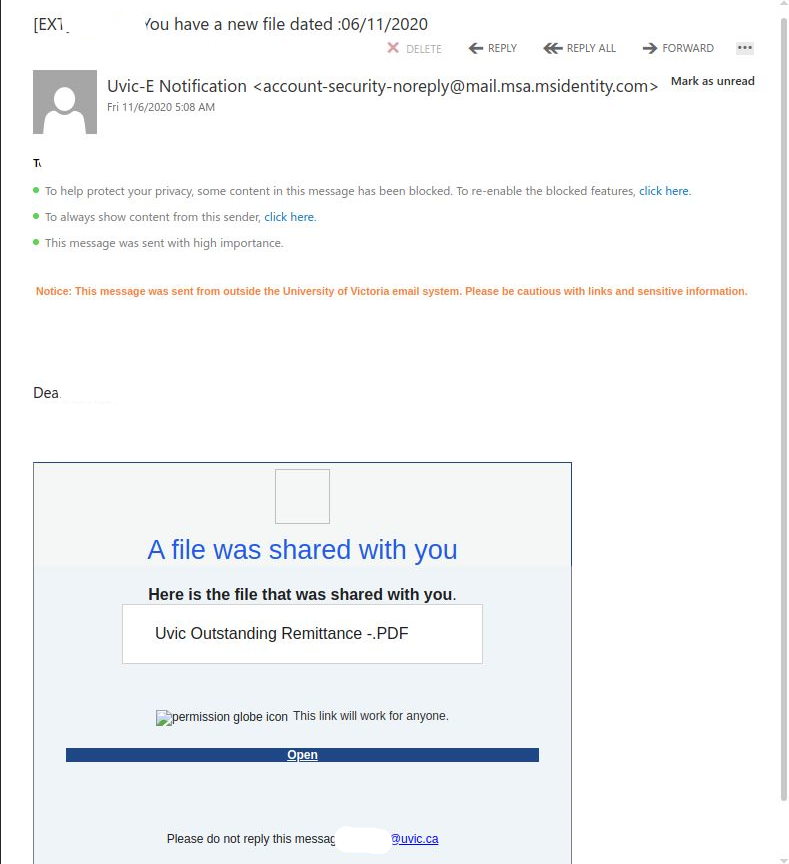
What you don’t see is a bad sender used/abused the Microsoft service to add a bit of authenticity to the message. This one was actually sent from a likely compromised .jp email address.
Question to ask yourself:
PAUSE.
Follow your gut.
There is no rush.
This one doesn’t include a known contact but oftentimes, you can call your colleague or contact them via a different known good method. eg. phone, and verify whether or not they have sent you something.
In addition to Microsoft service being abused here, if you hold your mouse over the PDF or the Open link, you’ll see they are also abusing a legit Google hosting service called firebase. The Firebaseapp is the legitimate Google service, the trailing link off the end goes to a website, that again, is NOT LEGIT.
If you proceed to view the PDF or click on the Open Link you will land on a fake Outlook Web App page that you are used to seeing. Yes, it does not have the UVic logo in this case, but we often see that level of duplication. The key in this case again is to look at the Internet Address.
In my sample, I am not revealing the email address but these are also customized with your personal work email in the URL and already populated in the User name text box. If you provide your legitimate password, they will capture it for later use and then conveniently, will just sent you back to the main UVic logon page.
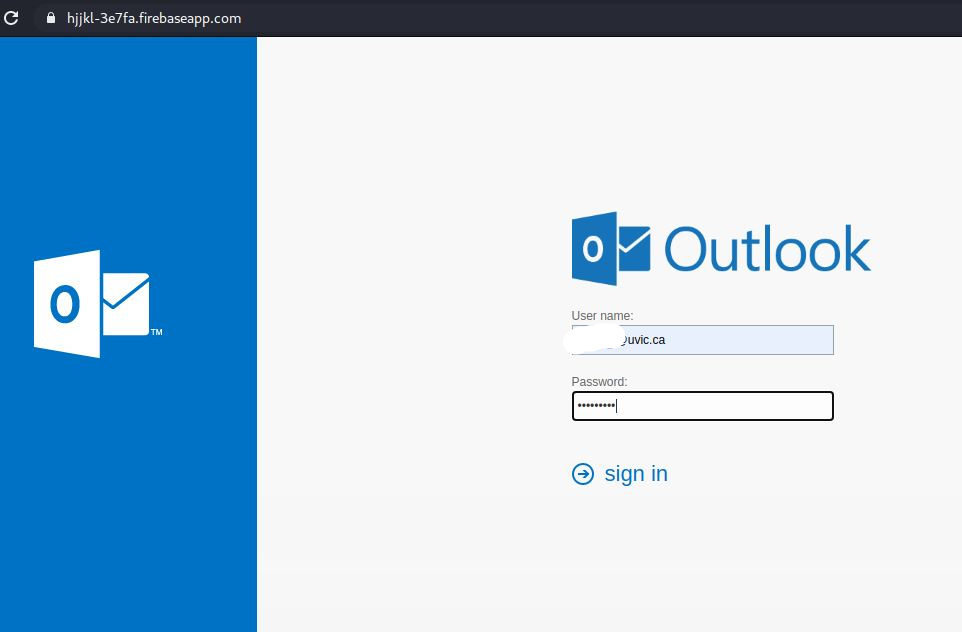
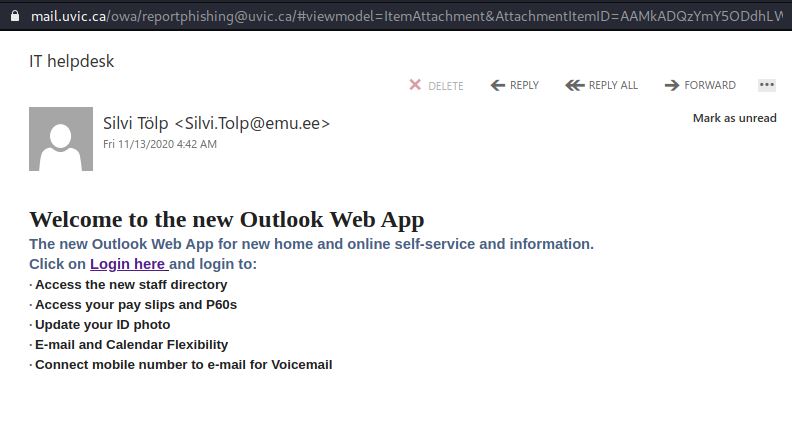
We are continuing to see abuse of the Weebly hosting service with varied “helpdesk” or “IT Support” like names and notifications.
If you make it this far, ALWAYS look at the Internet address. UVic is not hosting official UVic services on weebly.
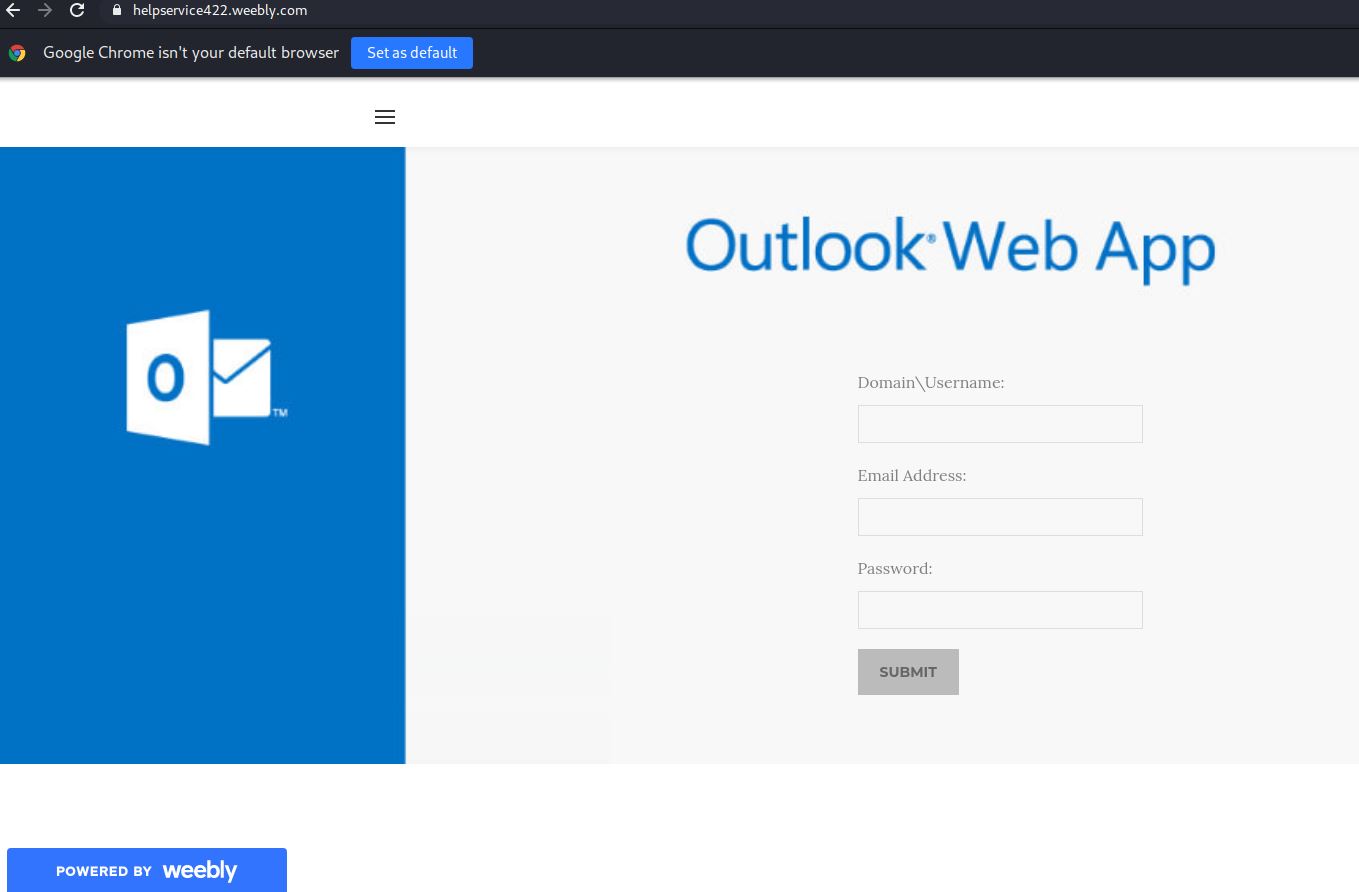
 Further deception here, they have also stolen the official Weebly 404 (page not found) page and are using it to make you think the page is down. They’ve simply assigned it to a new fake Internet Address. Check it out.
Further deception here, they have also stolen the official Weebly 404 (page not found) page and are using it to make you think the page is down. They’ve simply assigned it to a new fake Internet Address. Check it out.
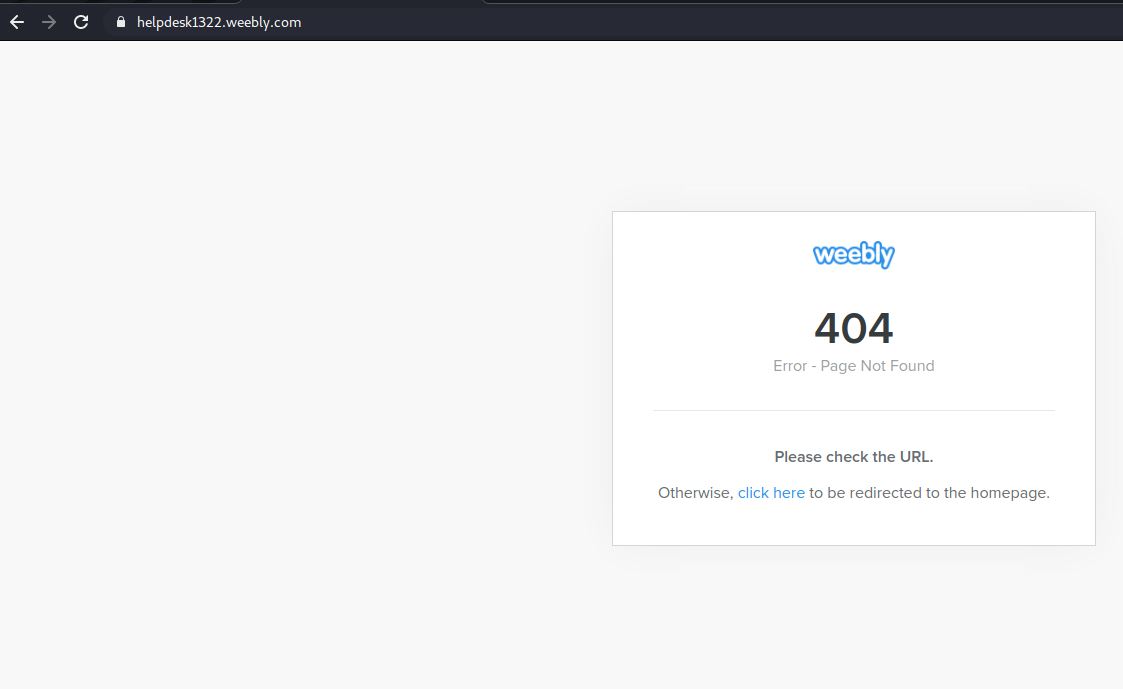
The click here link will send you back to the original fake url. An endless loop.
Over the last couple of days we are seeing fake Walmart Surveys linked to Black Friday campaigns. There are notable signs that this is not a legit mailing from the spelling of shopping to the gmail account linked to a Walmart username.
While this email is not well prepared, we provide this sample to remind you that large phishing campaigns typically pick up for such events like Black Friday and associated shopping sites leading up to the holiday season.
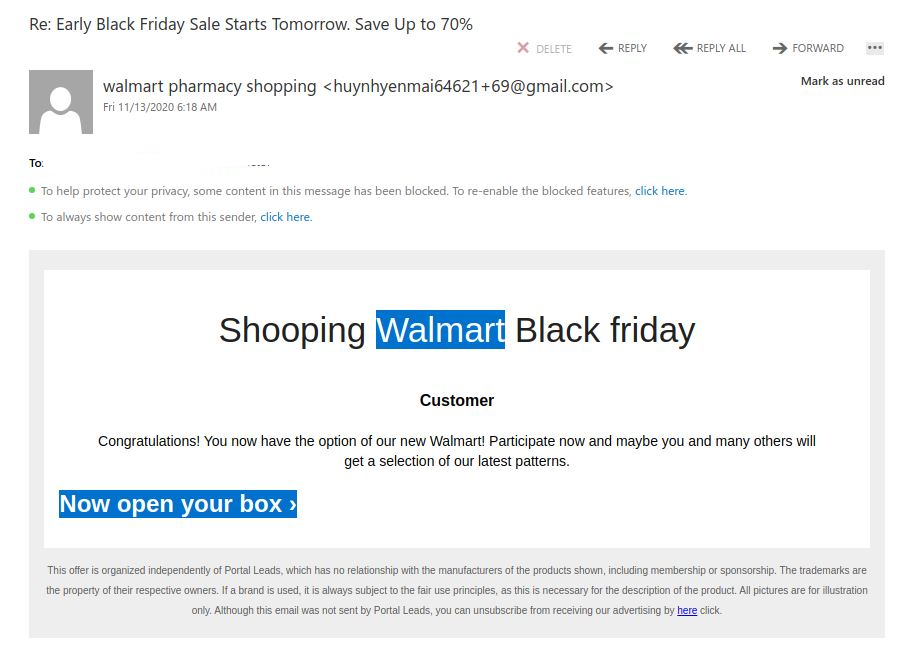
If you click the link you’ll land on this fake Walmart Survey page. Note the Internet address.
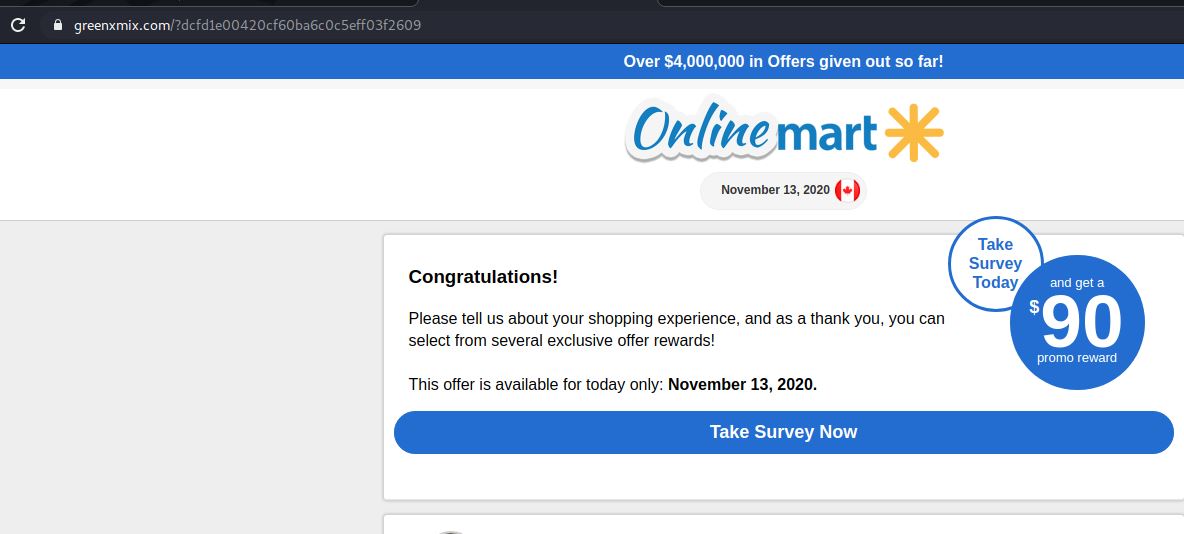
Instead of relying on marketing links and notifications, always best to login to your accounts directly by a known good Internet address to check for updates on any orders.
Another attempt to trick you into validating your credentials in order to perform a system update. It is customized to your specific accounts, leading to you to believe this must actually be intended for you.
It also leads you to believe that if you don’t action it, you may have delayed messages. They are attempting you to rush you into making a quick decision about proceeding.
Visual of the email: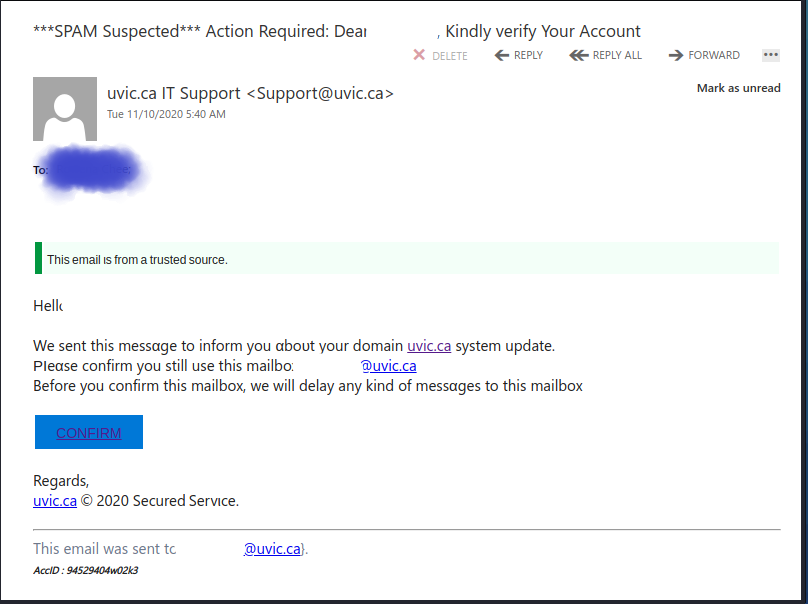
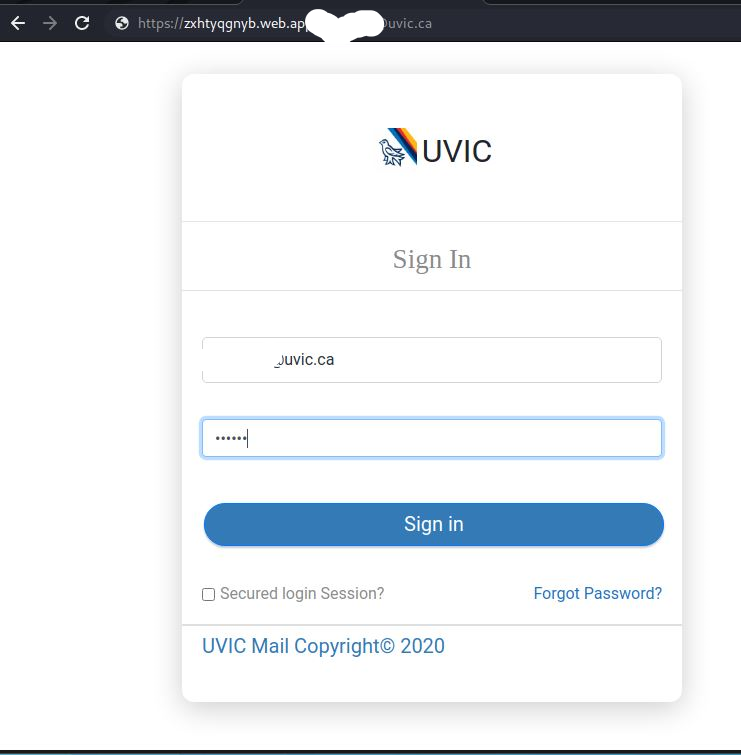
If you click on the Confirm option, you will be provided with a UVic logon expecting you to give away your credentials.
Fake UVic Logon:
Original email suggests a colleague has downloaded your files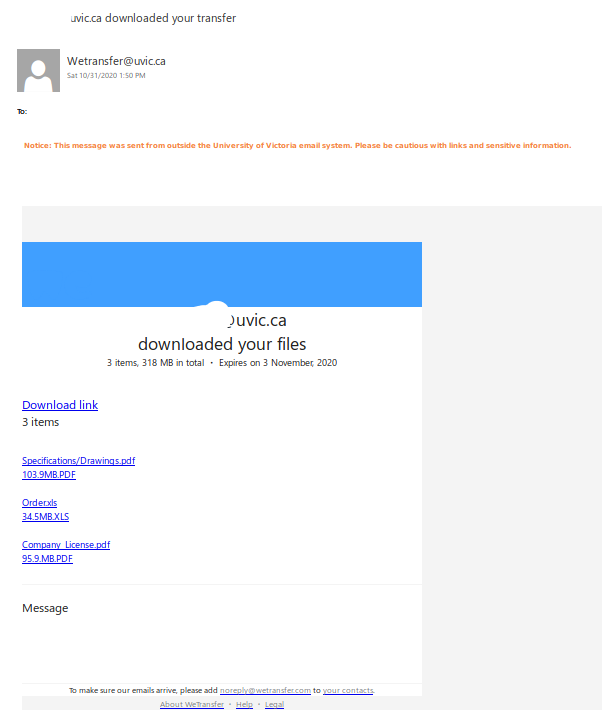
If you select to download them you are redirected to the fake WeTransfer page. It’s been customized for unique recipients: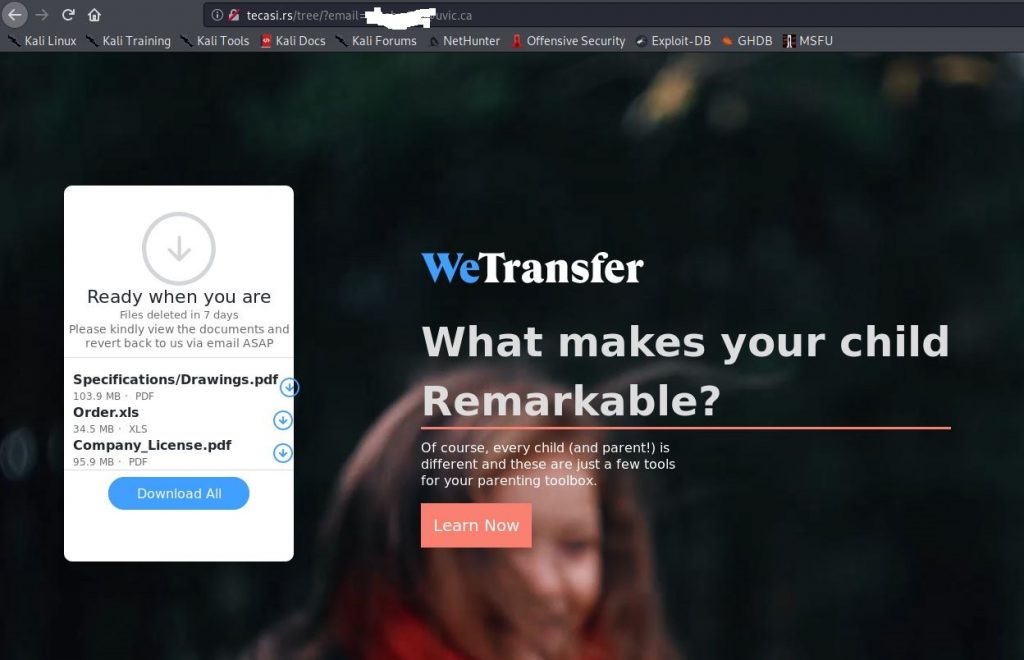 If you choose to select Download All, you will be prompted to login to do so:
If you choose to select Download All, you will be prompted to login to do so: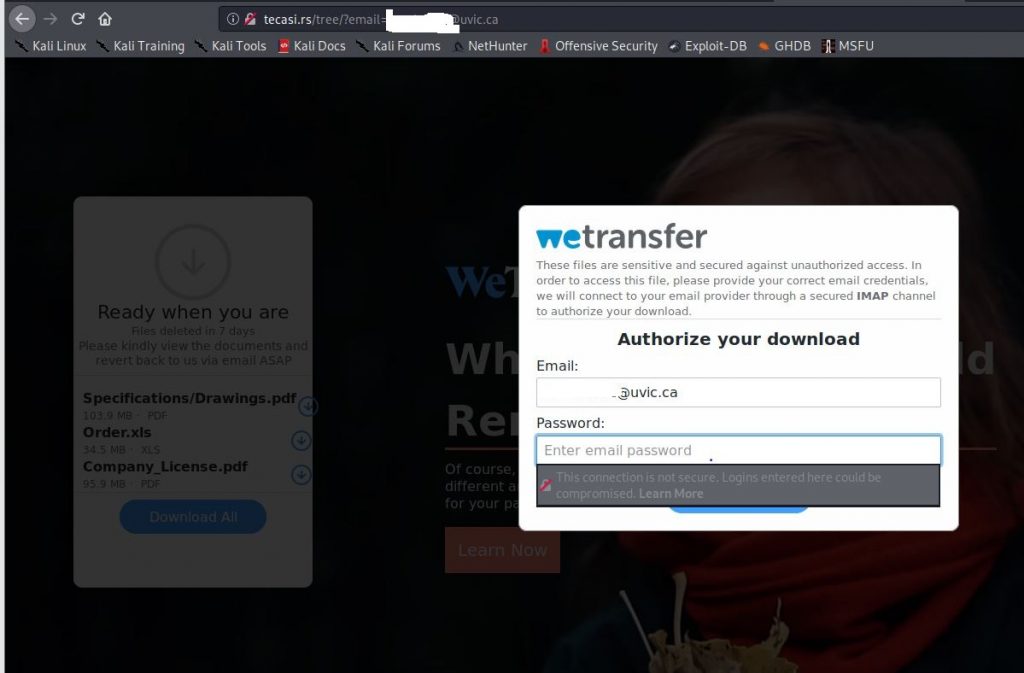
At which point, they will capture you username and password.
This payroll scam email resembles many we’ve seen the past. Note the non-UVic sender.
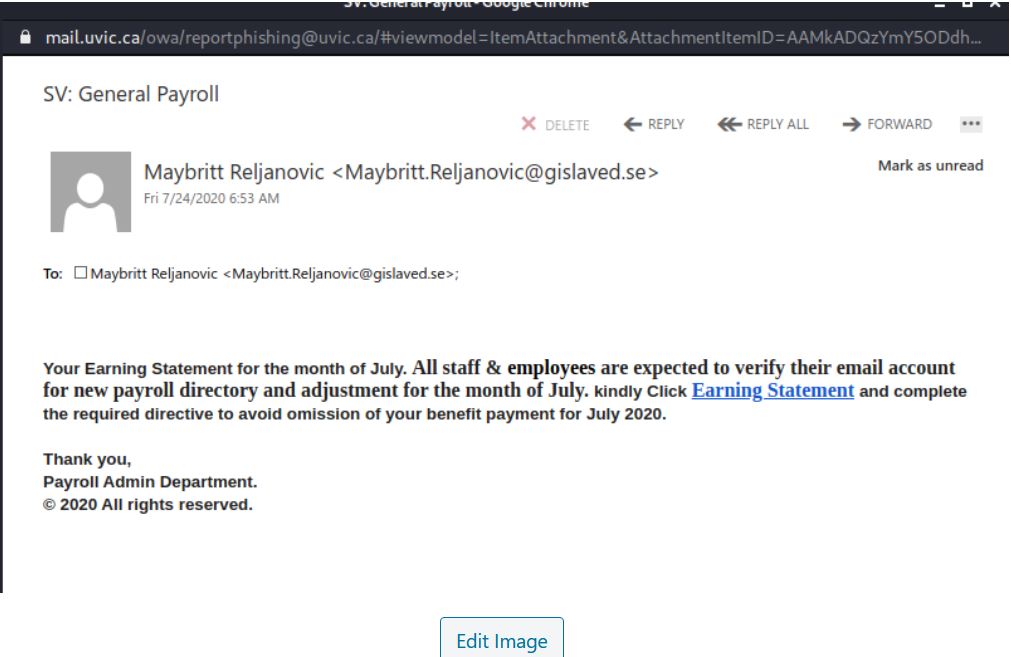
The link goes to a Fake OWA page that does not resemble any of our UVic services.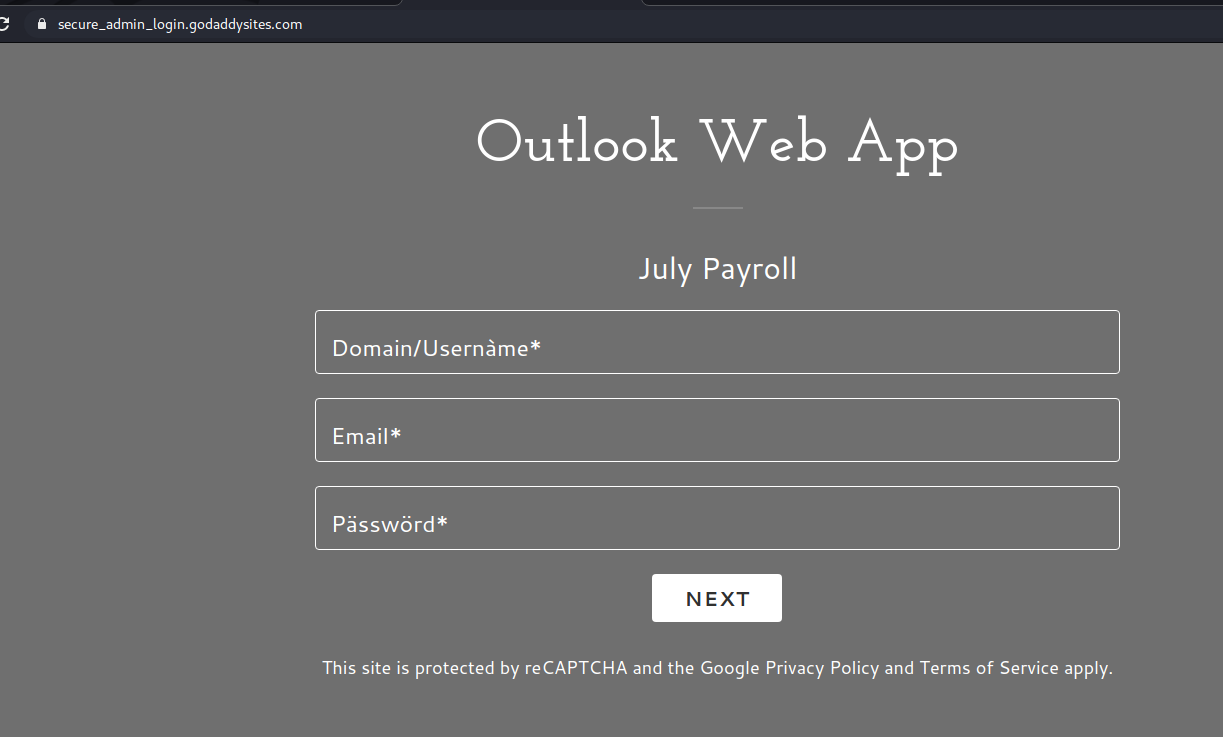
This has nothing to do with UVic. You’ll notice the godaddysite domain in the address bar.
Ignore and delete this email.