Chat GPT for Chrome with GPT-5, Claude Sonnet & DeepSeek AI
AI Sidebar with Deepseek, ChatGPT, Claude and more.
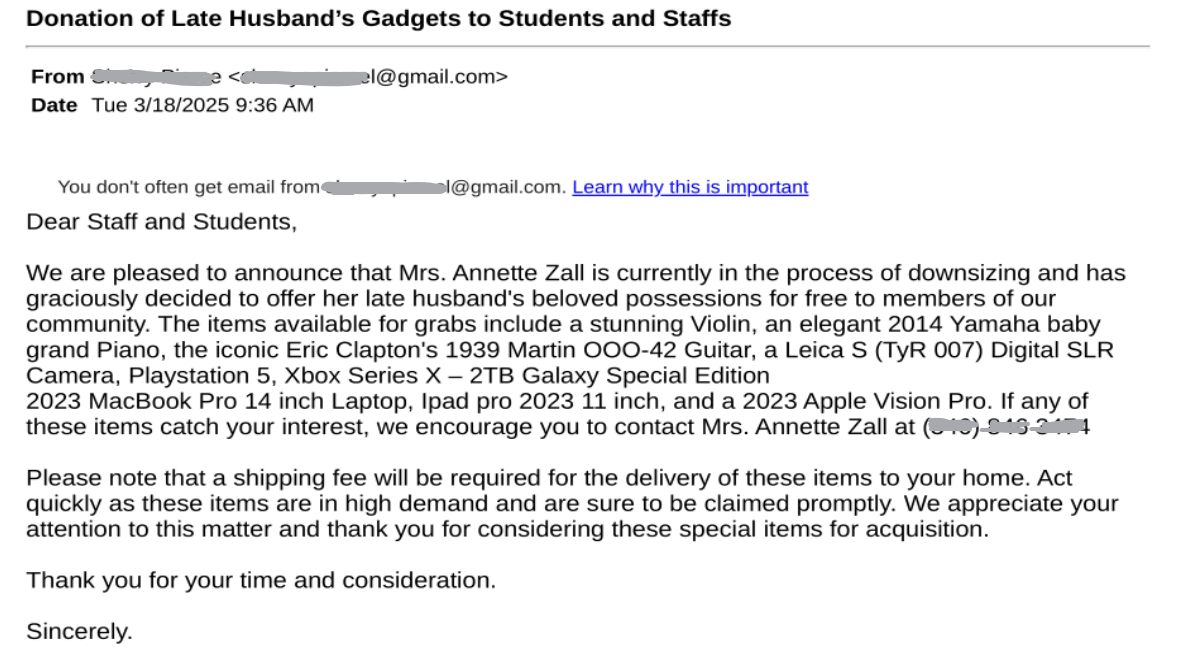
This is another example of threat actors weaponizing apps. These browser extensions were previously available for download in web stores (now removed). They pretend to be legitimate but were exfiltrating sensitive and personal ChatGPT, DeepSeek and browser related data once installed. If you have installed these or require assistance to establish the authenticity of an extension or app, reach out to the helpdesk or your IT support team.
- Note the icons are not the actual logo for any of those companies. Avoid installing unknown extensions, you can verify by checking on their website.
- Check the extension’s developer info before installing, verify that it is provided by the company it claims to be.
- Avoid uploading sensitive or personal information to chat models that are not the UVic compliant Copilot environment.
- Important information on the use of AI can be found here: https://www.uvic.ca/campus/artificial-intelligence/index.php