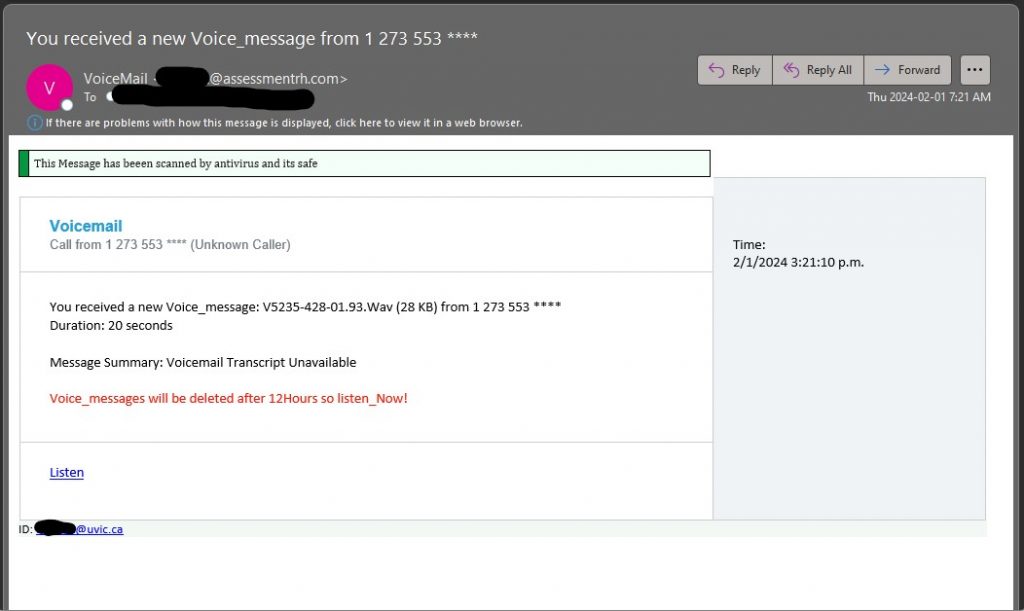
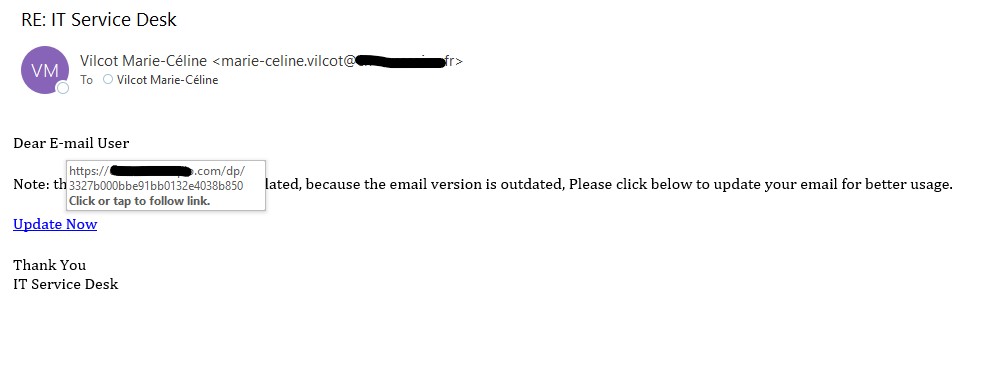
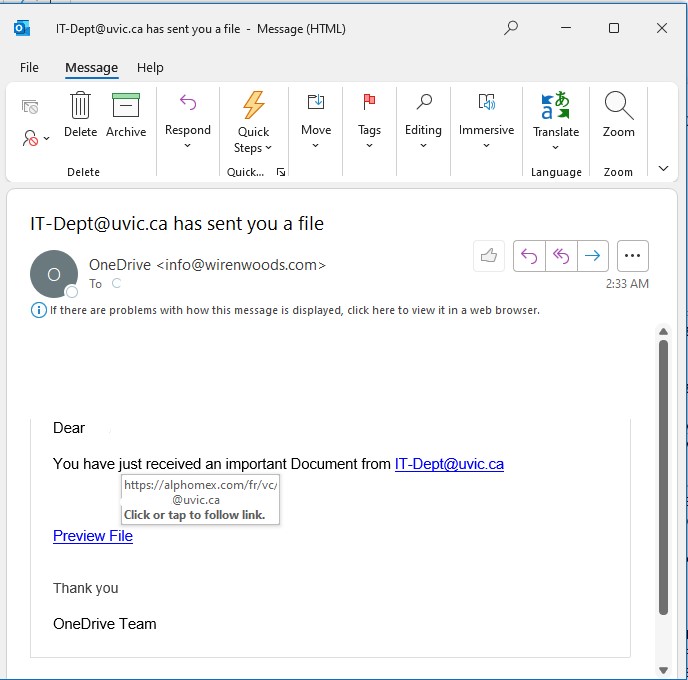
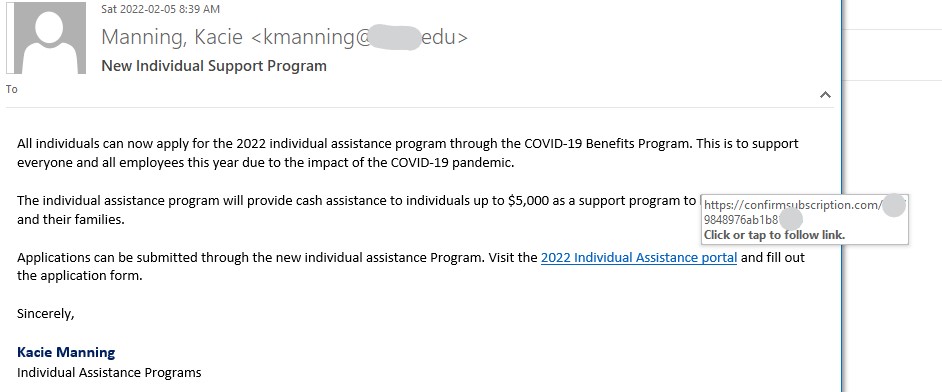
Some scammers are using Microsoft Sharepoint sites to send scam emails that appear very legitimate. The emails are very similar to legitimate emails from Microsoft, they do not have any malicious links and appear to come from Microsoft. The scammers want you to call the support number in the email and will then attempt to compromise your computer or steal money.
One red flag is whether you are expecting this email or not, however it is possible you have a personal M365 subscription matching the information. Microsoft advises they do not include support phone numbers in emails to clients. For emails where you are not sure and want to contact the company in question, it is best to look-up the contact information on the company’s official website.
Delete or report these emails as phishing; do not call the scam numbers. If you did call the number, please contact the Computer Help Desk or your department’s IT support staff immediately for assistance.
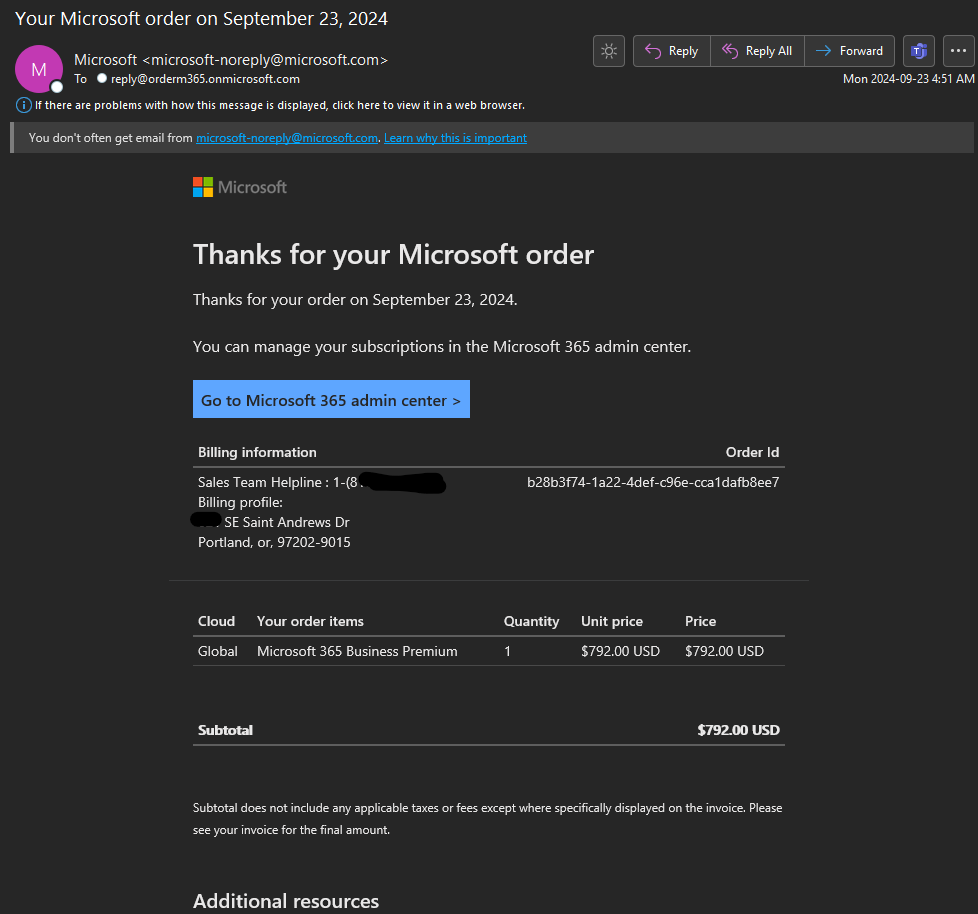
Transcript:
Subject: Your Microsoft order on September 23, 2024
Email body:
Thanks for your Microsoft order
Thanks for your order on September 23, 2024.You can manage your subscriptions in the Microsoft 365 admin center.
Go to Microsoft 365 admin center (link to admin center).
Billing information Order Id
Sales Team Helpline : 1-(818) redacted
Billing profile:
redacted SE Saint Andrews Dr
Portland, or, 97202-9015 b28b3f74-1a22-4def-c96e-cca1dafb8ee7
Table with
Global Microsoft 365 Business Premium, quantity 1, price $792.00 USD
Subtotal $792.00 USD