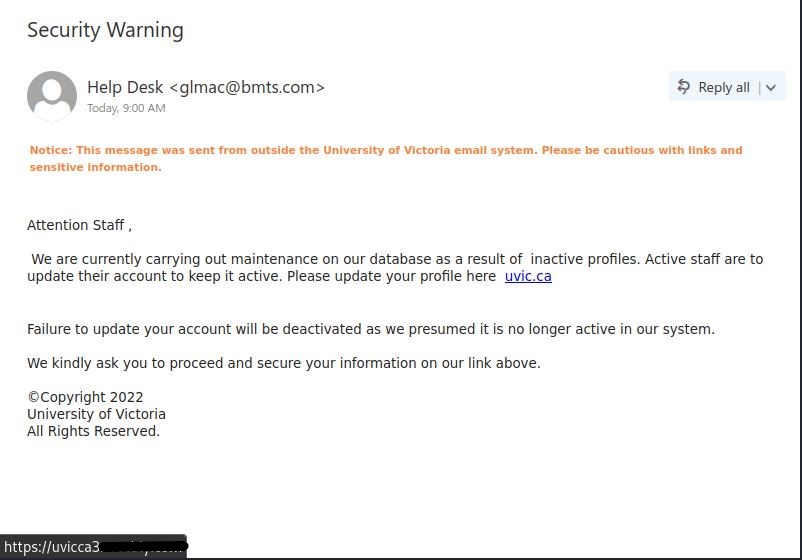
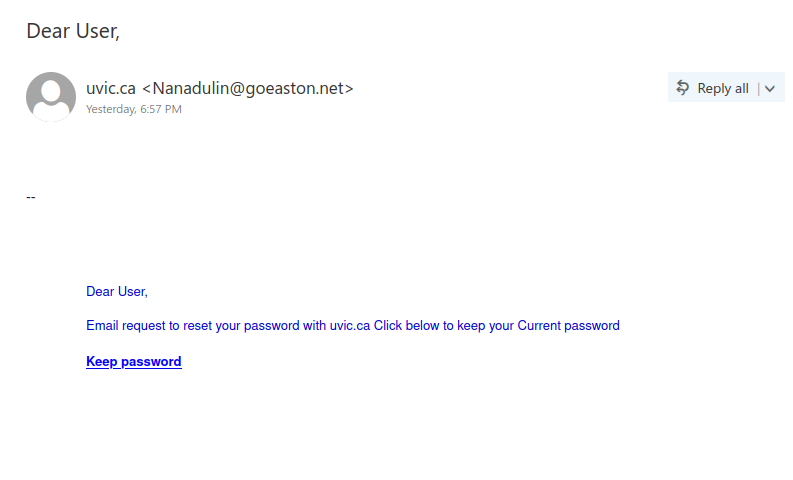
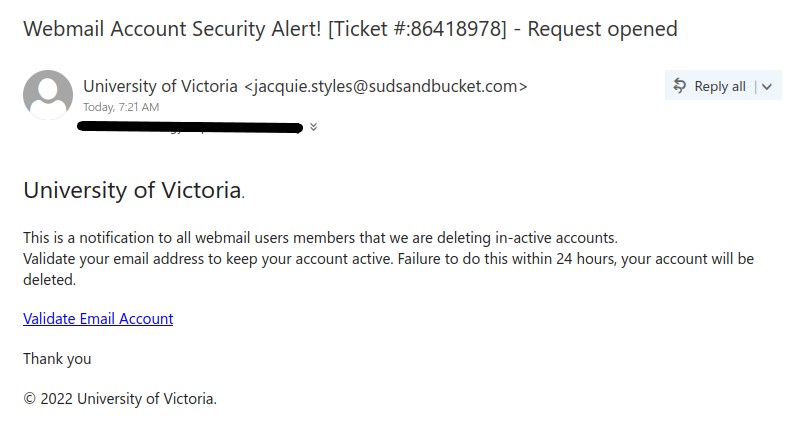
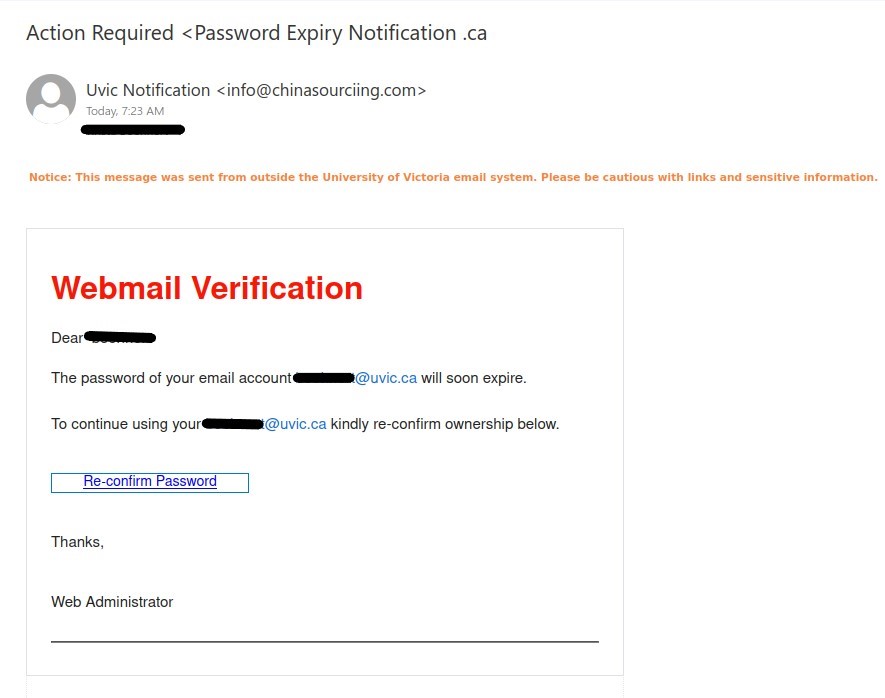
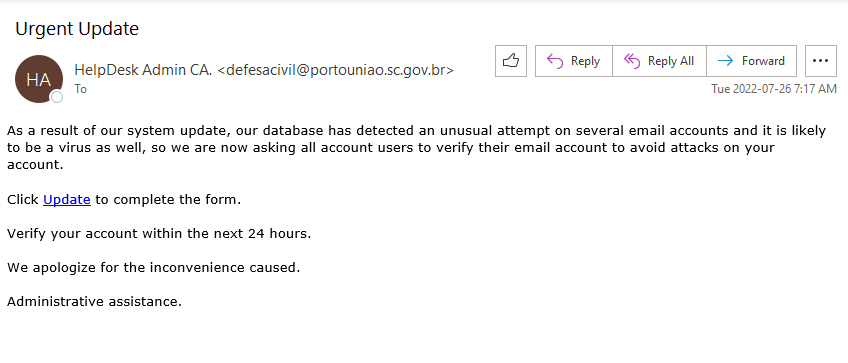
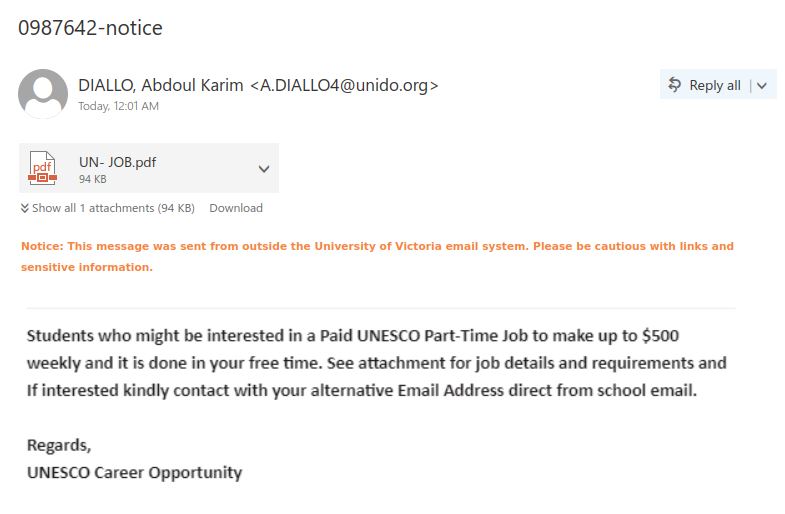
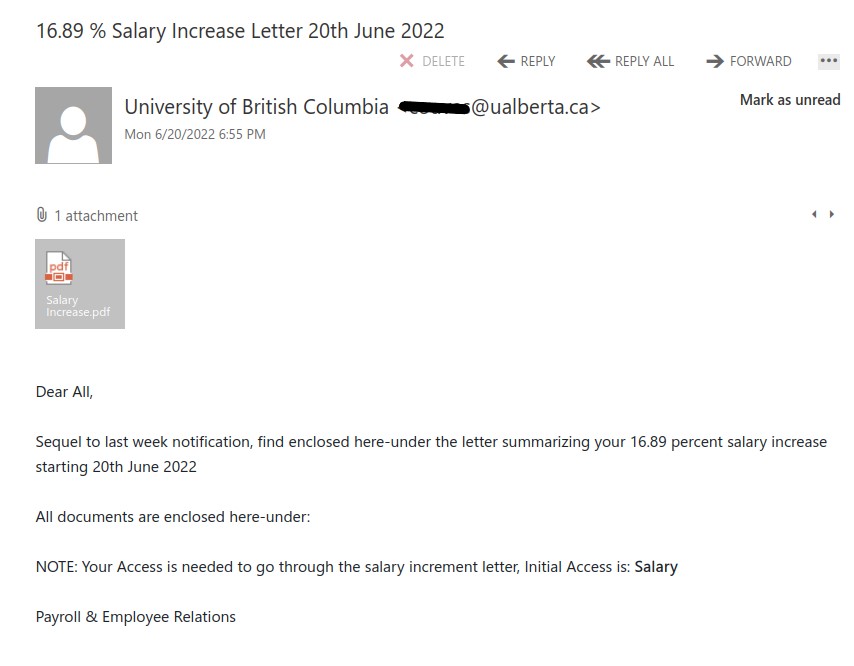
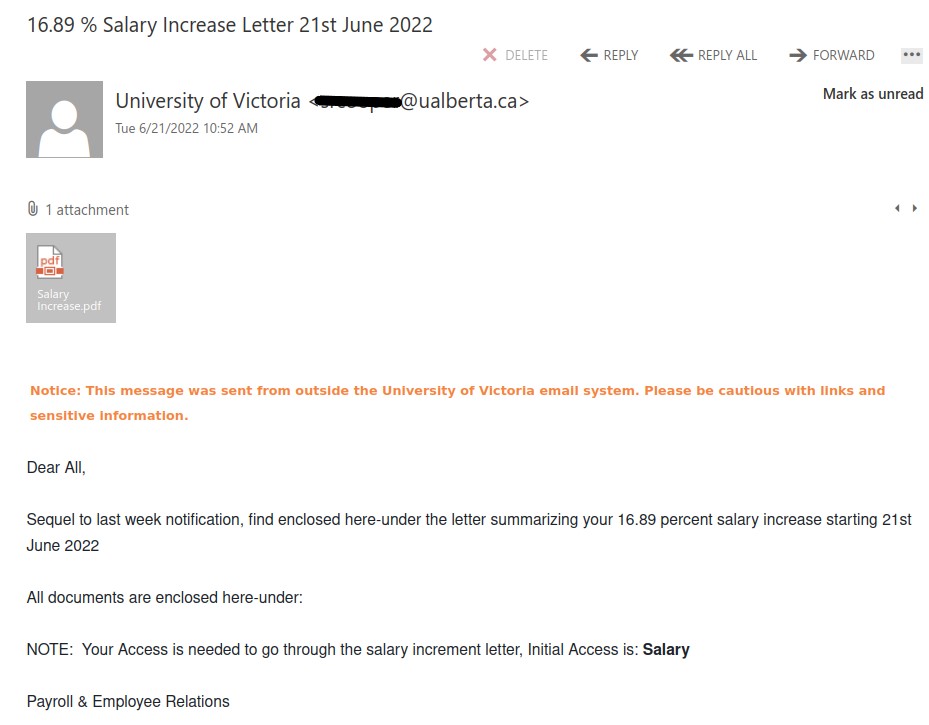
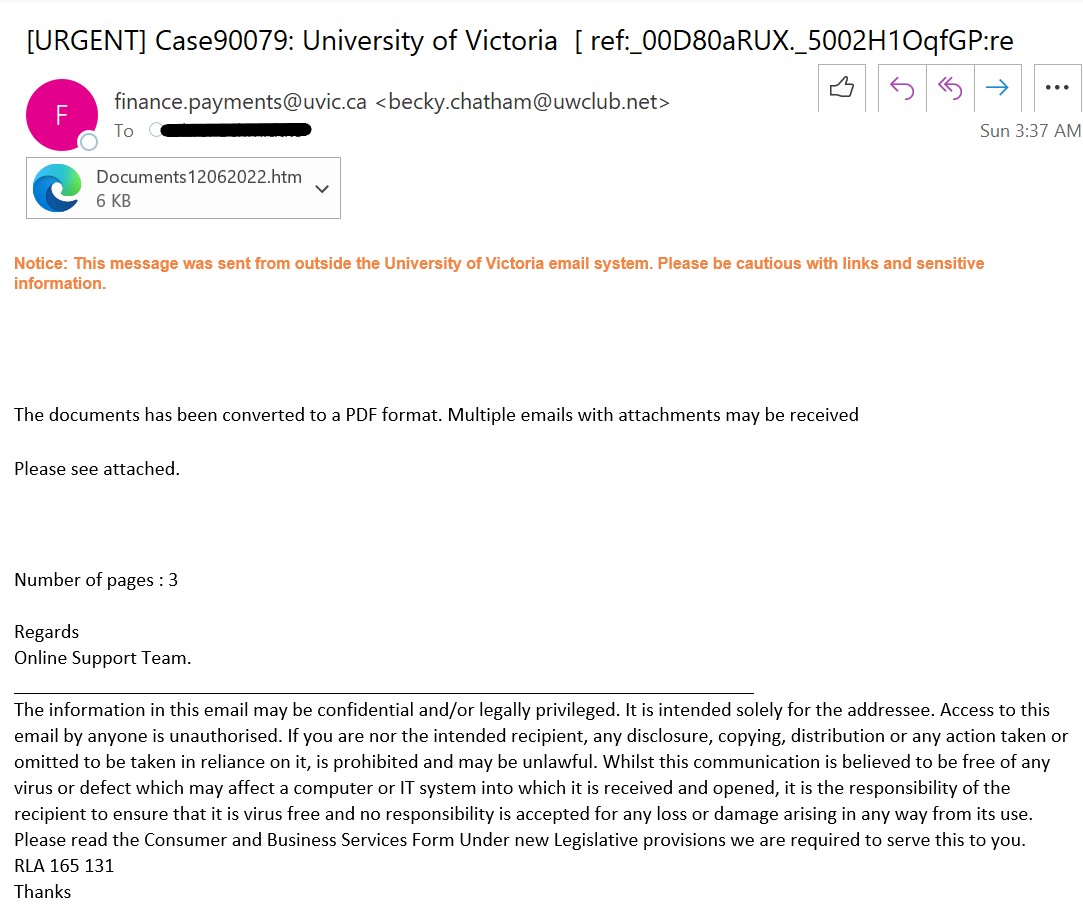
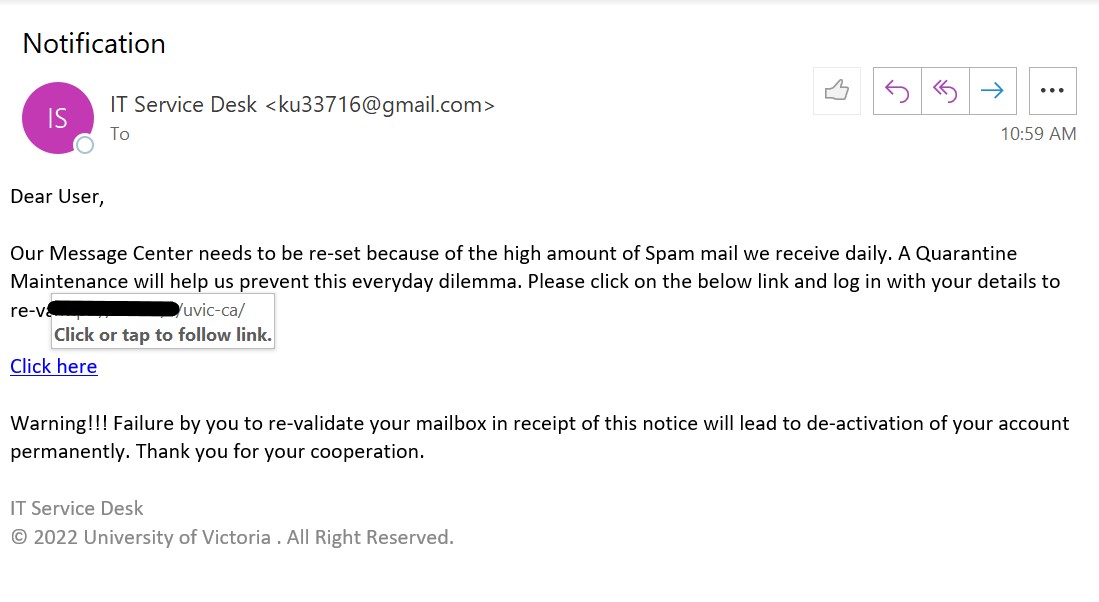
As we were looking forward to the weekend, phishers were looking forward to phishing. This phishing email has the usual telltale signs:
- External sender, why would an external sender be involved in updating UVic’s privacy policy.
- The UVic mark in the email is just to trick the recipient’s into believing that it is coming internally from UVic.
- Threatening in a polite way, if you do not update you would face login interruptions.
- No salutation or signature.
Don’t be in a hurry to click on links or taking actions suggested by the phisher. Always take a moment to think and look for phishing signs. If in doubt, you can always confirm with help desk or your DSS support.