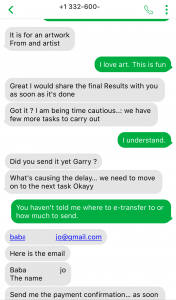
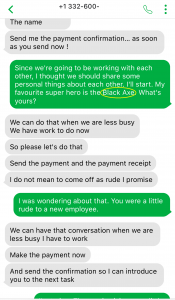
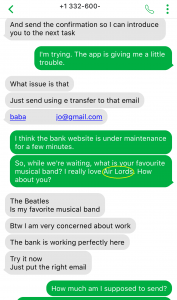
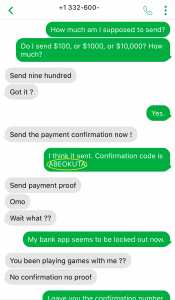
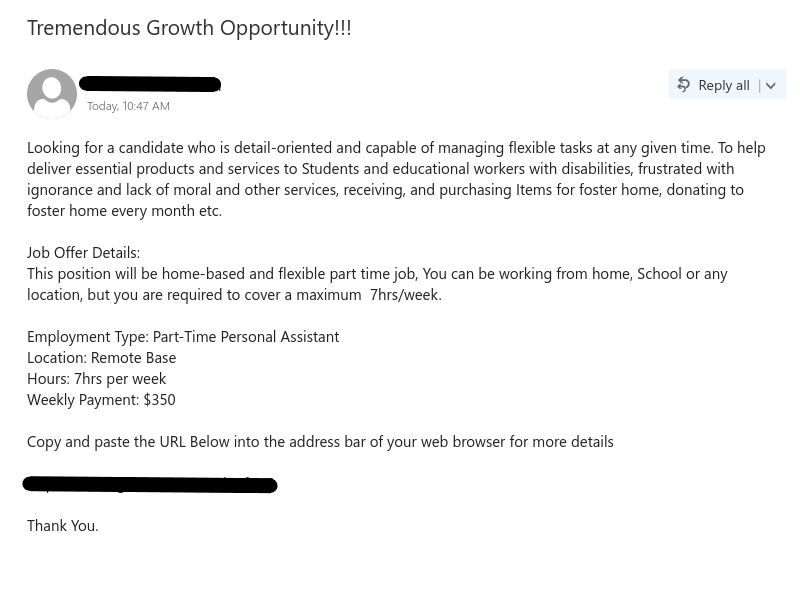
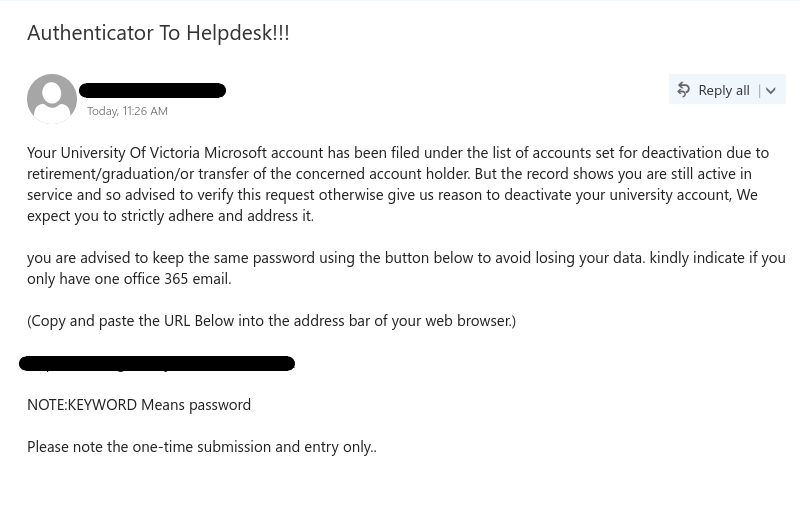
Job scams have become common these days, trying to attract victims looking for part-time jobs to support themselves, especially in today’s tough financial times. Scammers take advantage of prospective candidates/victims by offering higher than expected pay for the amount of work required. If an offer is too good to be true, then probably it is.
The following job scam impersonates STMicroelectronics, offering a part-time job for enormously high pay. No matter what type of job scam it is or which organization is impersonated, the questions to ask yourself to spot these scams remain the same:
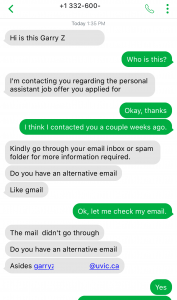
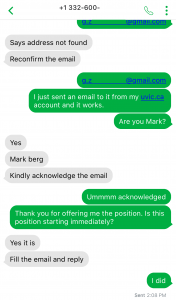
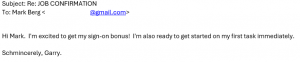
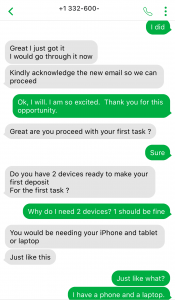
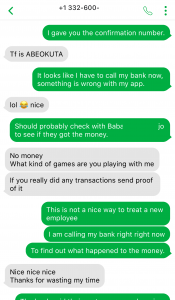
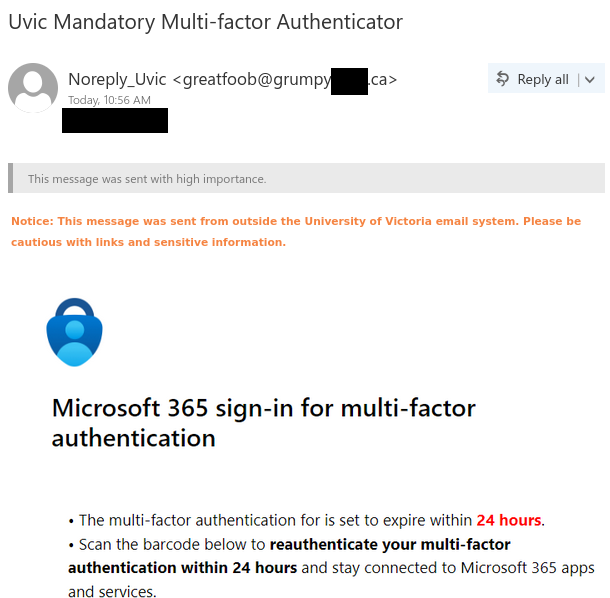
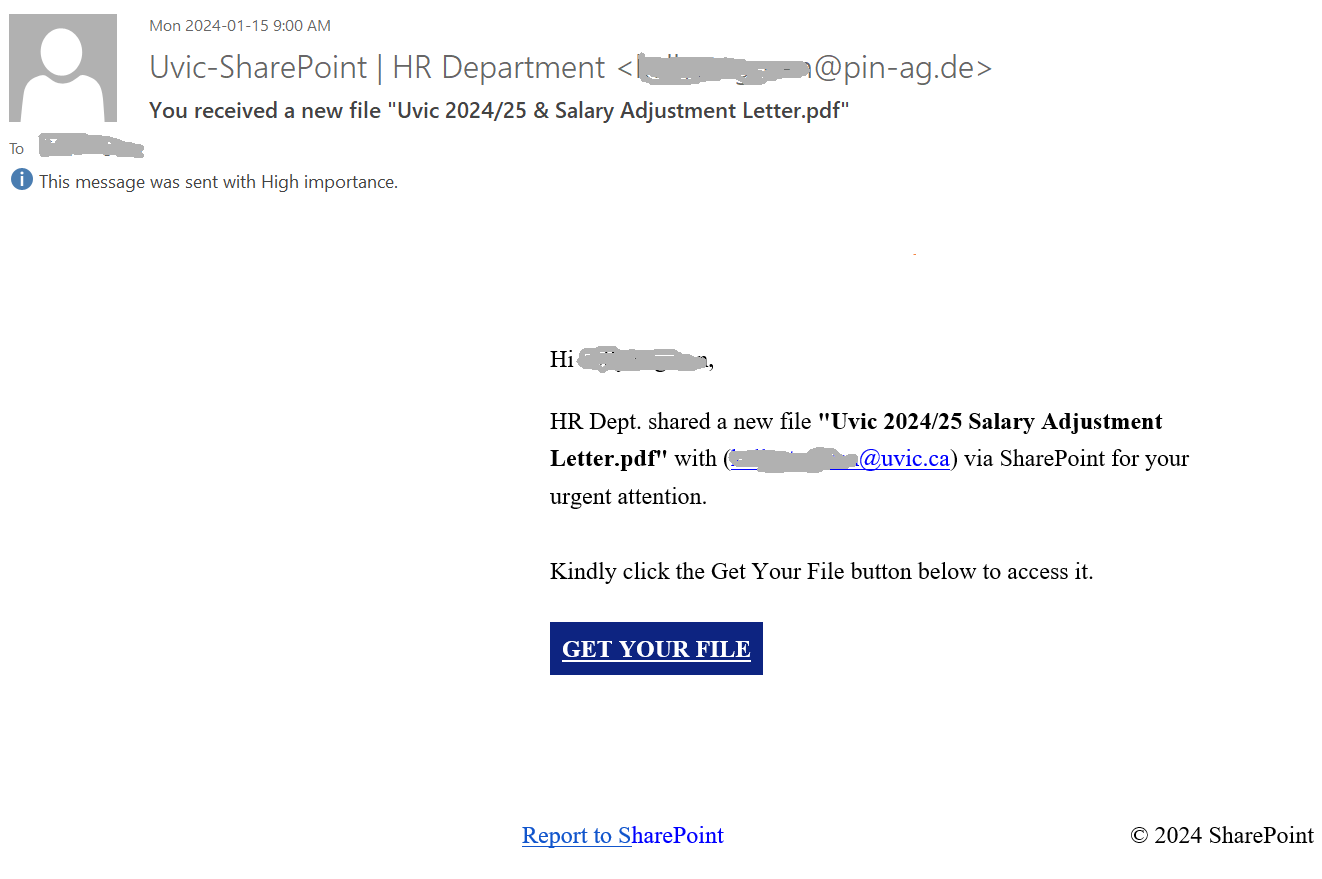
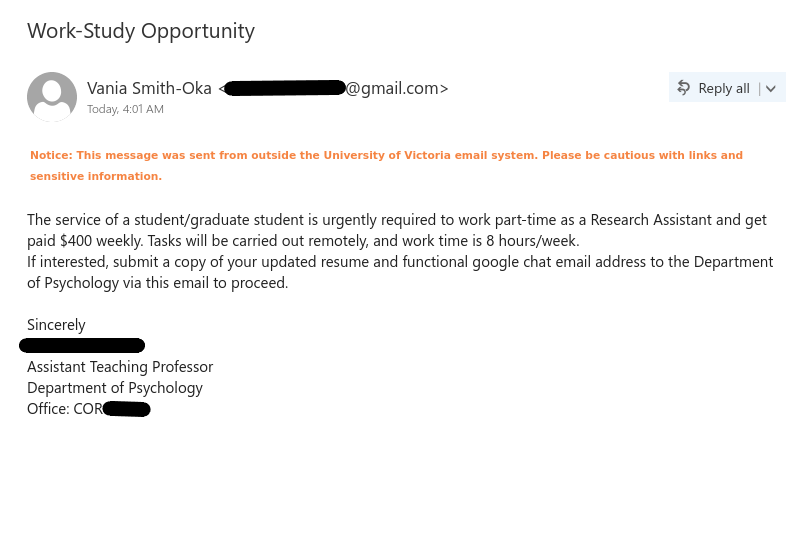
- Why are you receiving this email? Did you even sign up with this organization to send you job offers or did you ever apply with this organization? Try to think of a plausible explanation as to why did you get this email, if you don’t know then it is a scam.
- If you still somehow think of a reasonable reason to go beyond the first point, then look at the senders email address, which domain (domain is the part of the email address after the symbol “@”) is it coming from? Is it coming from the same domain as the organization claiming to send this job posting? Like, in this case, the domain should have been st.com but the sender email address is coming from a different one. One way of finding the real domain of an organization is to do a google search about it.
- Salary offered is also one of the strong indicators of spotting a scam. Generally, the salary offered would be much higher than the minimum wage for less amount of work than a regular part-time job. Why are they offering such a high salary? Obvious answer is, to scam you.
- Try reading the job description, are you able to make sense of what type of position is being offered? Usually, it is described in a very ambiguous manner, just giving you enough that it sounds like some job but not what the job is. And they ask you to reply with details first before revealing any more details. Should you be applying for a job where you don’t know what the job is?
- Generic salutation which is a sign of mass send email to unknown recipients, which further translates to whoever will take the bait. This ties back to the question in the first point, is there a legit reason for you to be receiving this mass send email? If not, it is a scam.
- Grammatical and spelling mistakes could be intentional by the scammers to dissuade the people who won’t eventually fall for the scam. If someone proceeds without spotting these mistakes would be their potential victims whom they can easily persuade. Sometimes these minor errors are made to make the email relatable or believable as humans are prone to errors. Should a legit job posting have such errors, especially coming from large organizations, wouldn’t it have been proofread?
- As is common with scams, they are always urgent. You need to urgently take action, as the people hiring are in urgent need. Such urgency is called upon so that victims don’t have time to think or question the legitimacy of the process. But you should always question yourself before being hasty, always allow yourself time to think before its too late.
Here’s hoping that the above questions would give you perspective on how to judge the legitimacy of job offers and easily spot job scams. If you replied to this scam, contact the Computer Help Desk or your department’s IT support staff immediately for assistance.
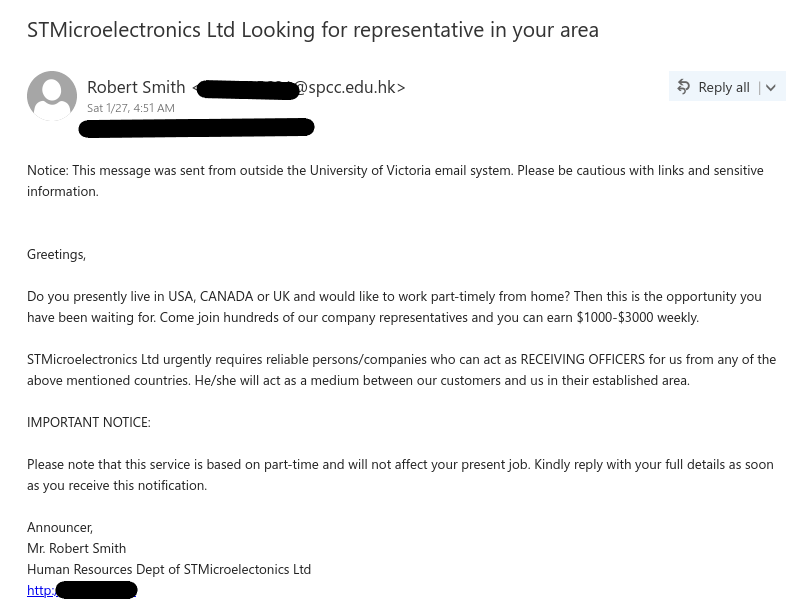
Subject: STMicroelectronics Ltd Looking for representative in your area
Sender: Robert Smith <****@spcc.edu.hk>Notice: This message was sent from outside the University of Victoria email system. Please be cautious with links and sensitive information.
Greetings,
Do you presently live in USA, CANADA or UK and would like to work part-timely from home? Then this is the opportunity you have been waiting for. Come join hundreds of our company representatives and you can earn $1000-$3000 weekly.
STMicroelectronics Ltd urgently requires reliable persons/companies who can act as RECEIVING OFFICERS for us from any of the above mentioned countries. He/she will act as a medium between our customers and us in their established area.
IMPORTANT NOTICE:
Please note that this service is based on part-time and will not affect your present job. Kindly reply with your full details as soon as you receive this notification.
Announcer,
Mr. Robert Smith
Human Resources Dept of STMicroelectonics Ltd
http:****