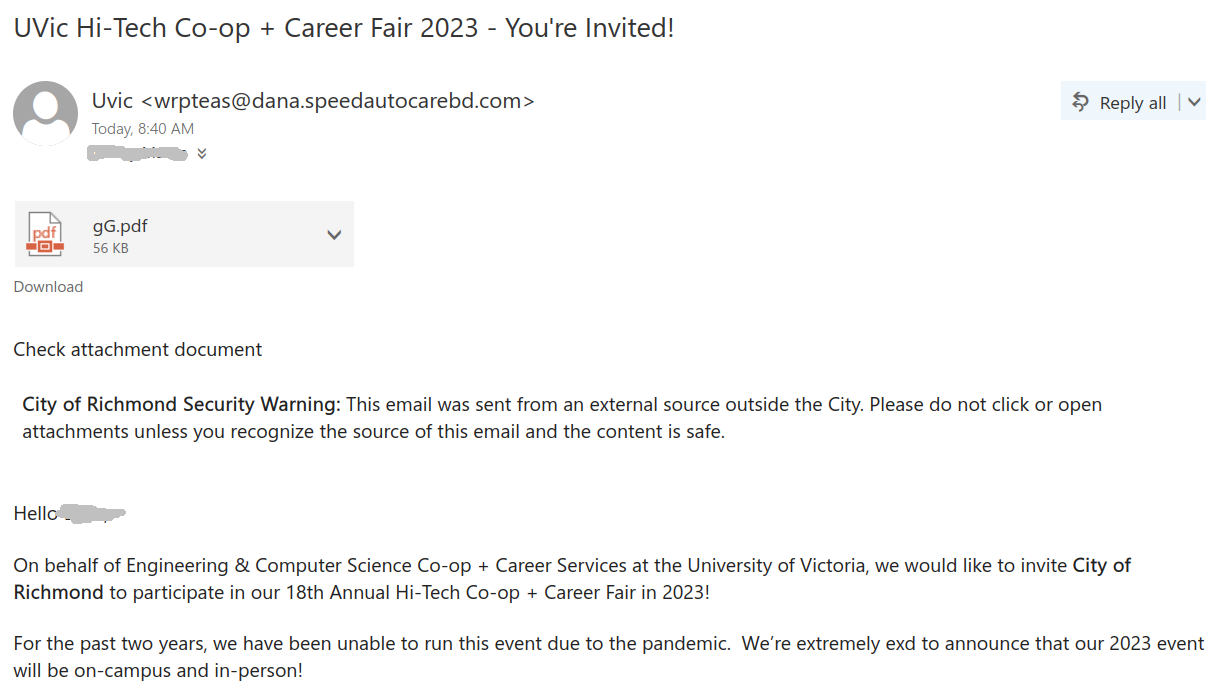
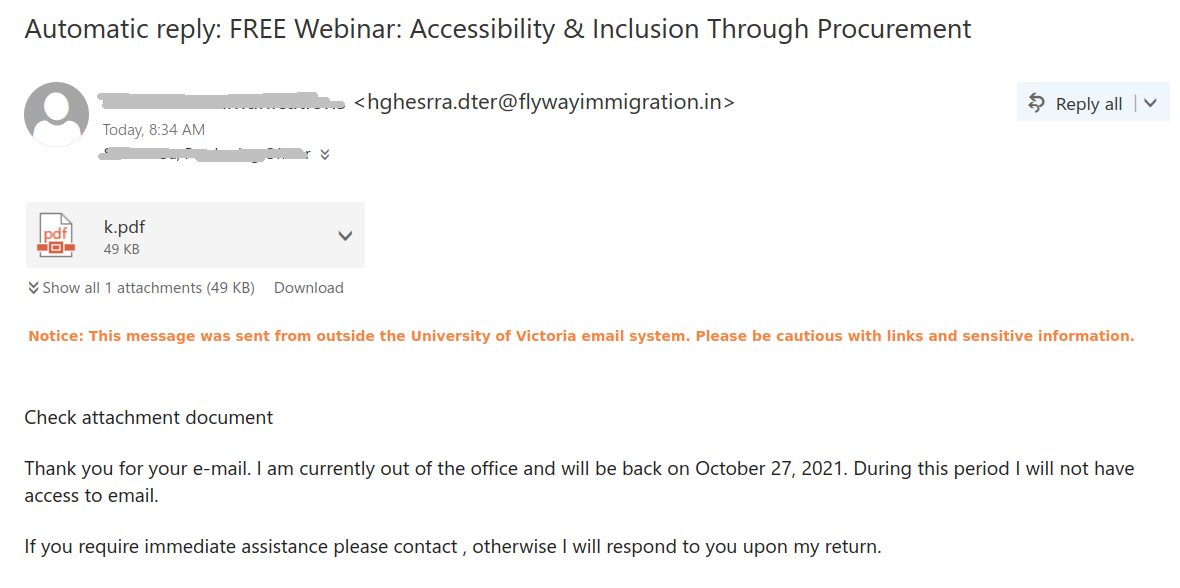
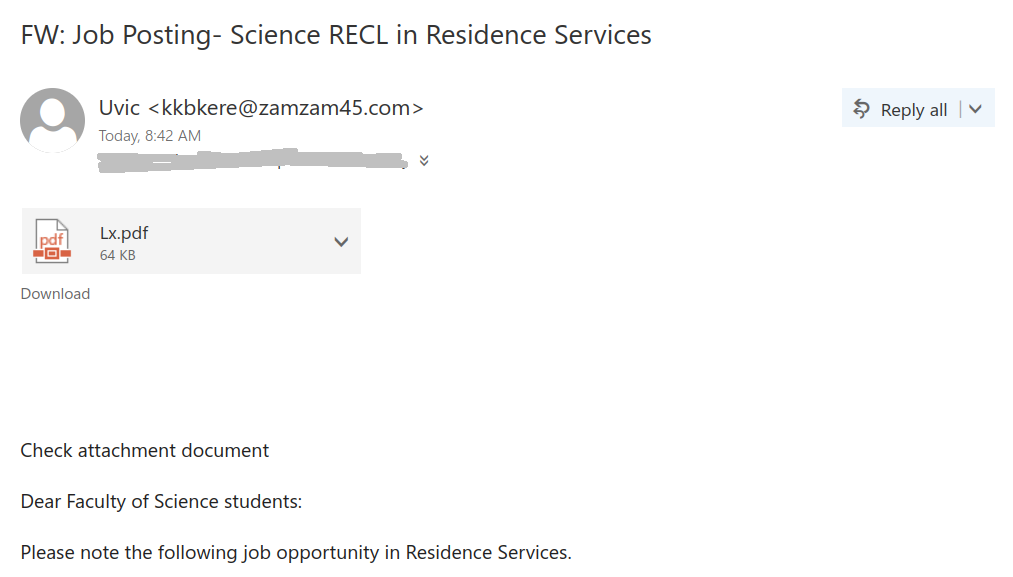
Malicious actors deployed a bunch of phish against UVic recipients today. The trick they apply is to use some authentic text sent by a UVic person. In some cases that’s a mass-mail sent a year ago to hundreds of recipients, in some cases it is just the out-of office message of somebody. In all cases they add a line of theirs on top of the legit text — “please check the attachment”. The sender address is different. The display name may copy a name from the original email thread. The attachment itself contains a link to the actual malicious content. A screenshots of a few examples are shown below. The pdf attachments are usually having a very short name – one or two characters. (however that doesn’t mean that every attachment with a long and meaningful name is legit). Be vigilant, apply common sense and don’t open attachments from suspicious emails (unknown sender, unsolicited, etc.).
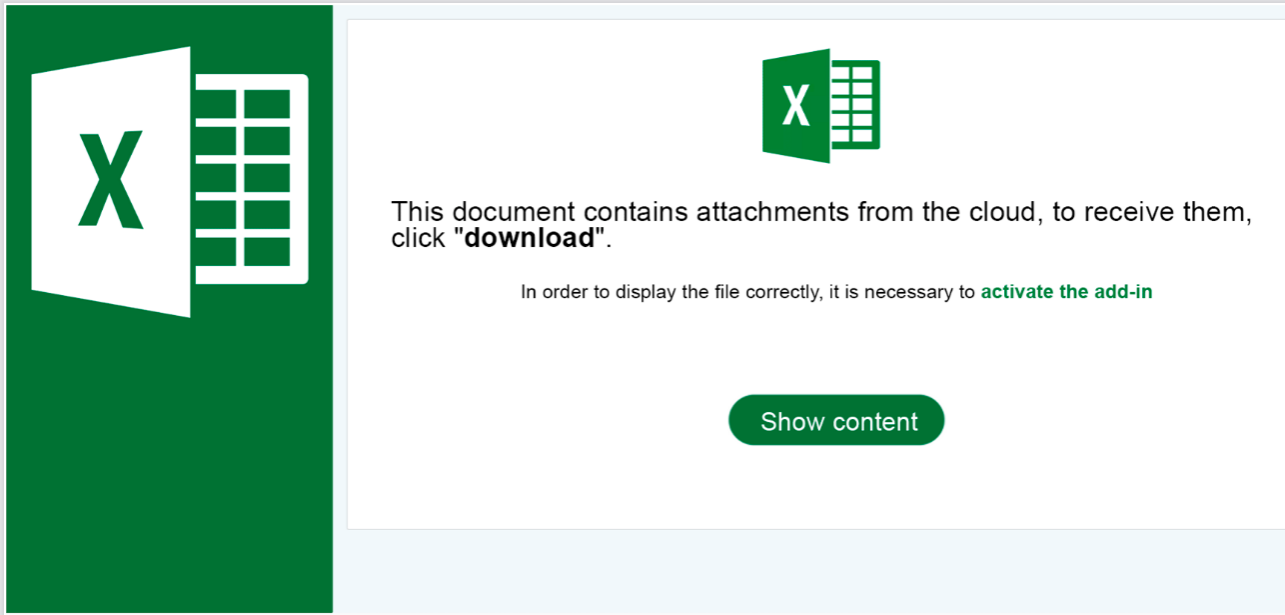
The PDF itself looks like this: