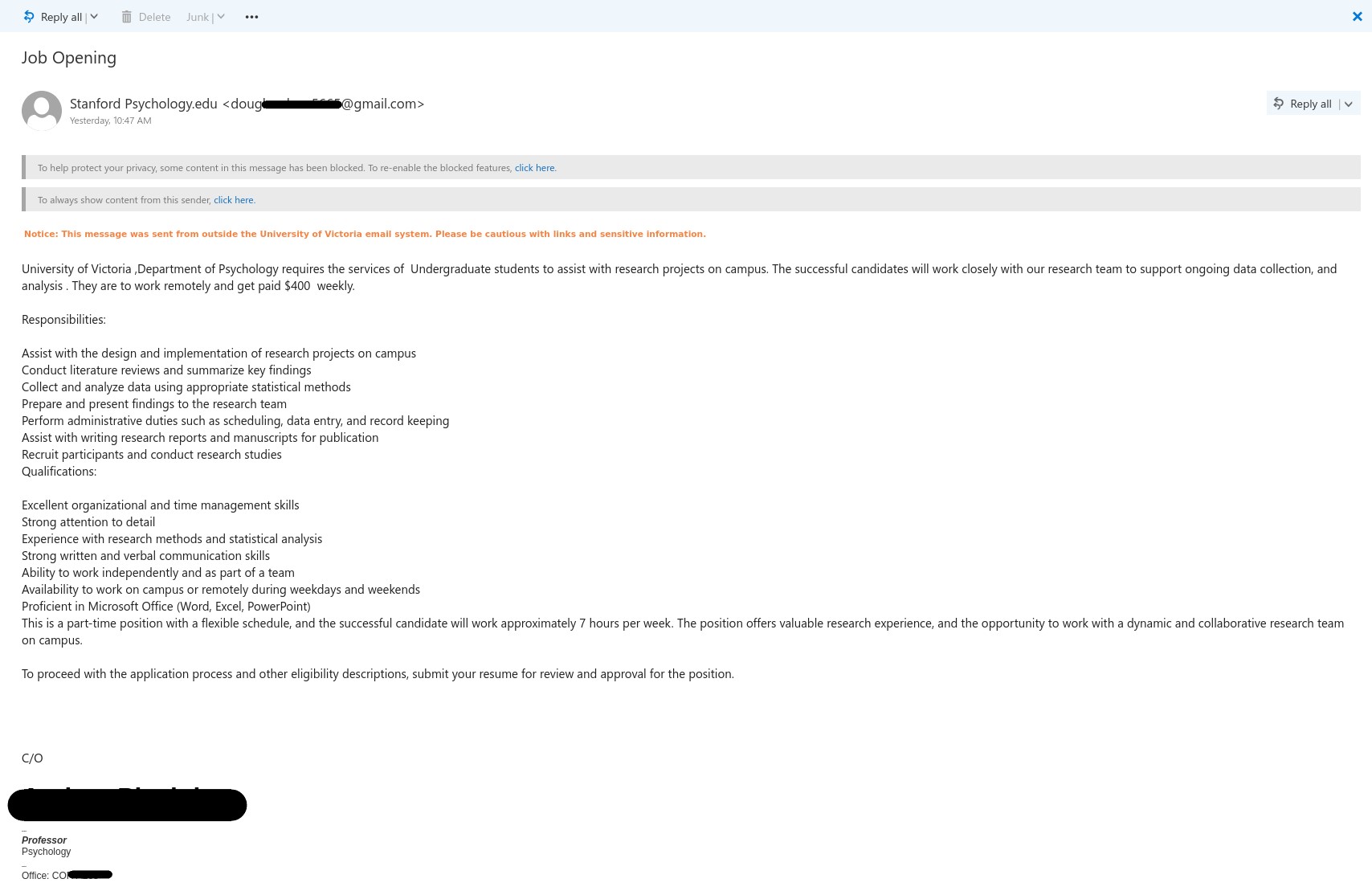
Job scammers are once again impersonating real UVic professors when they offer fake research job positions. The red flags that indicate this offer is not legitimate are the usual ones:
- The emails come from Gmail addresses. A legitimate UVic job offer should be announced from a UVic email address.
- The salary offered is too good to be true given the very small number of hours per week to be worked.
- The email contains errors in punctuation, spacing and capitalization.
- In some cases, the name of the sender may differ from the professor mentioned in the email. Inconsistencies like this can be a sign that something is not right about the email.
Do not reply to these emails with your information. If you did, cease contact with the scammer and reach out to the Computer Help Desk for assistance.
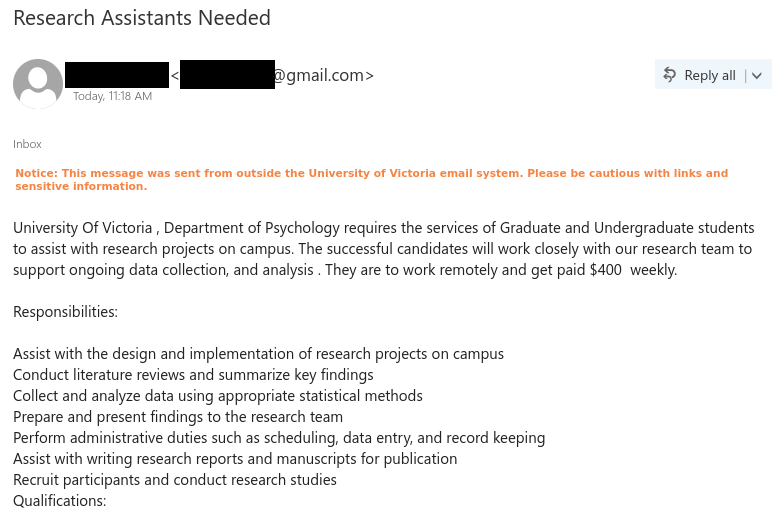
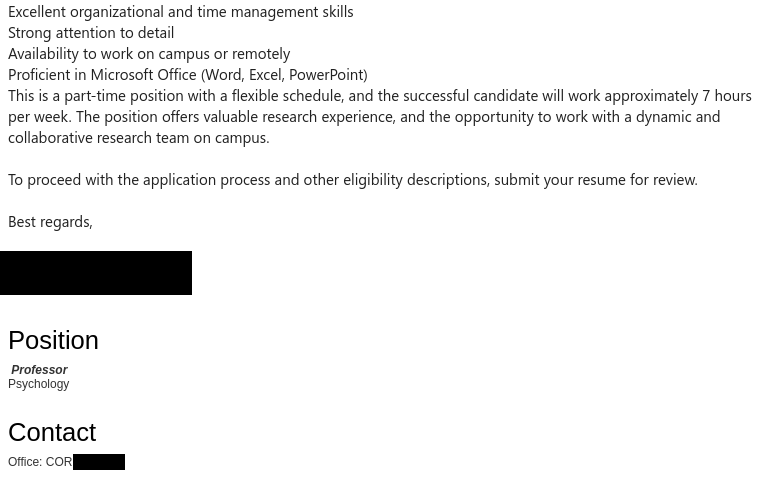
Subject: Research Assistants Needed
From: [professor name] <*******@gmail.com>Notice: This message was sent from outside the University of Victoria email system. Please be cautious with links and sensitive information.
University Of Victoria , Department of Psychology requires the services of Graduate and Undergraduate students to assist with research projects on campus. The successful candidates will work closely with our research team to support ongoing data collection, and analysis . They are to work remotely and get paid $400 weekly.
Responsibilities:
Assist with the design and implementation of research projects on campus
Conduct literature reviews and summarize key findings
Collect and analyze data using appropriate statistical methods
Prepare and present findings to the research team
Perform administrative duties such as scheduling, data entry, and record keeping
Assist with writing research reports and manuscripts for publication
Recruit participants and conduct research studies
Qualifications:Excellent organizational and time management skills
Strong attention to detail
Availability to work on campus or remotely
Proficient in Microsoft Office (Word, Excel, PowerPoint)
This is a part-time position with a flexible schedule, and the successful candidate will work approximately 7 hours per week. The position offers valuable research experience, and the opportunity to work with a dynamic and collaborative research team on campus.To proceed with the application process and other eligibility descriptions, submit your resume for review.
Best regards,
[Redacted]
Position
Professor
Psychology
Contact
Office: COR ****