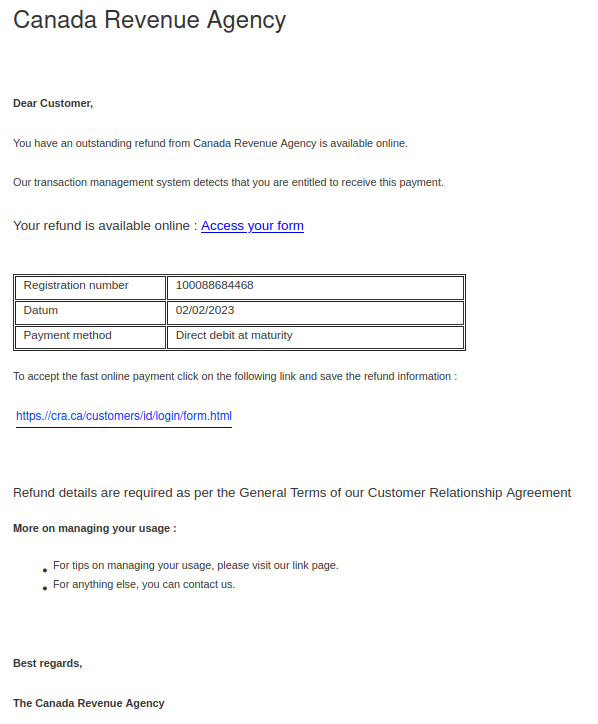
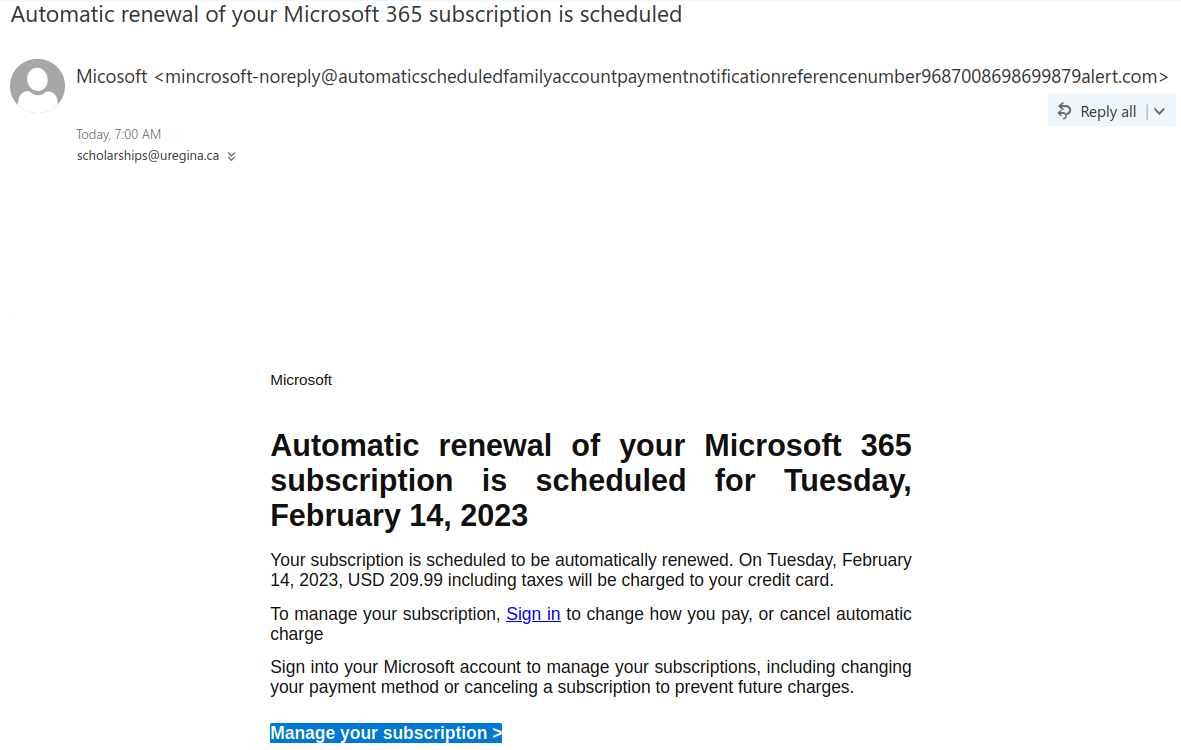
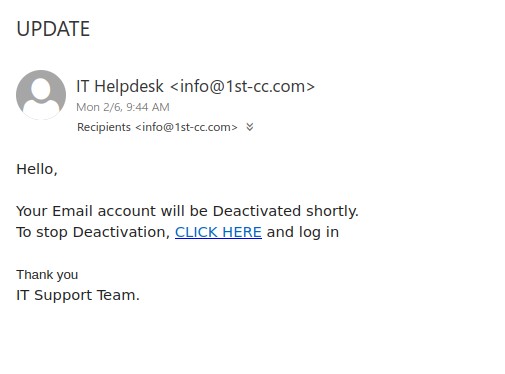
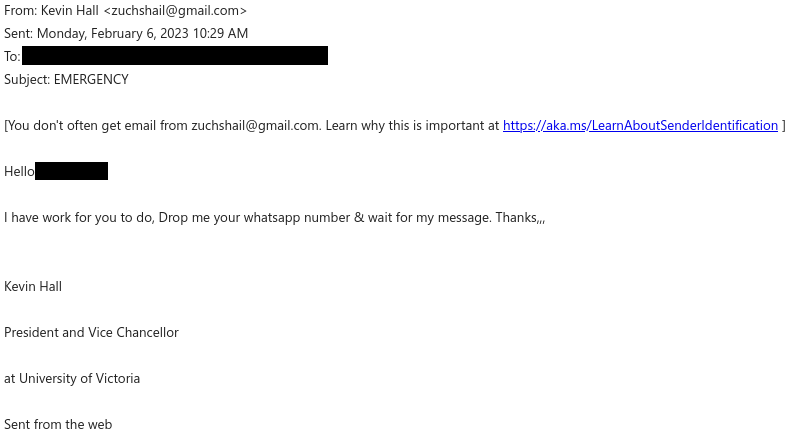
With income tax filing season approaching, it’s not surprising that phishers are sending emails pretending to be from the Canada Revenue Agency (CRA). The “From” addresses for these emails were not ones from canada.ca or a domain ending in .gc.ca, meaning the emails did not actually come from the Government of Canada. The samples reported to us had sender addresses from various Austrian domains.
There are several other signs that this is a phish in the message contents:
- The greeting is impersonal, and it seems odd for the CRA to address you as a customer when they’re a government agency.
- There are some grammatical errors and also weird extra spaces before colons.
- The use of “datum” instead of “date” is a word choice error.
- The text about “managing your usage” near the end of the message doesn’t make sense in this context.
The ultimate red flag: hovering over either link will reveal that they use TinyURL or some other link shortener. Be very suspicious of shortened links in emails, as phishers often use them to hide the true malicious destination of the link. We used a security scanner on these shortened URLs and can confirm that they do not go to the real CRA website.
Real CRA webpages are on either canada.ca or domains with names ending in .gc.ca. It’s also worth noting that cra[.]ca actually belongs to a market research company, not the CRA!
For more information, the Canada Revenue Agency also has a page with additional tips on how to protect yourself from fraud.