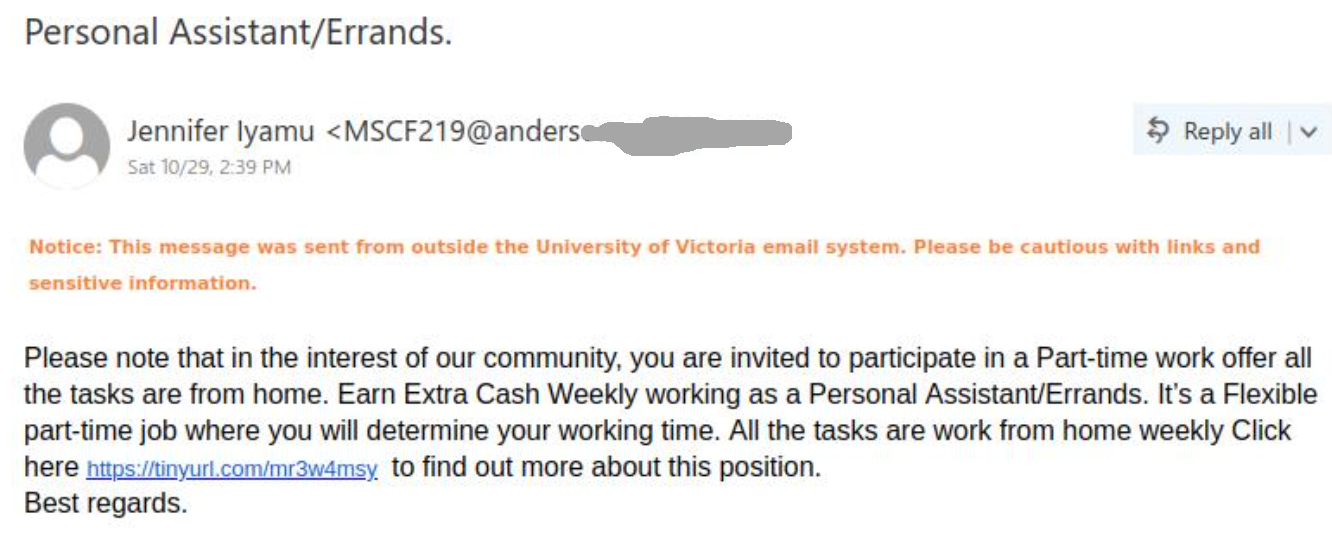
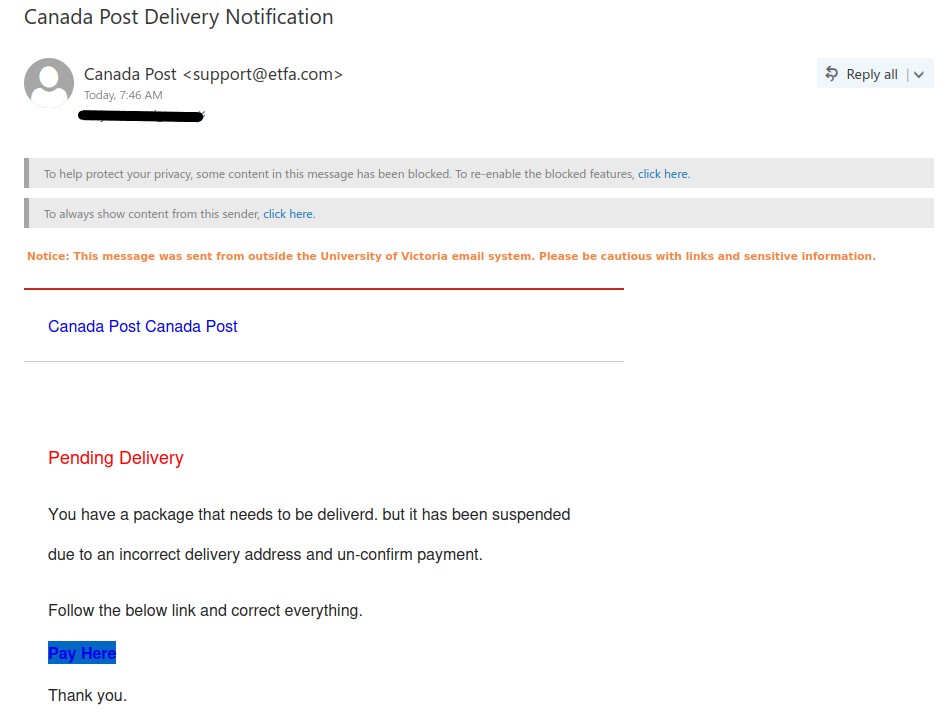
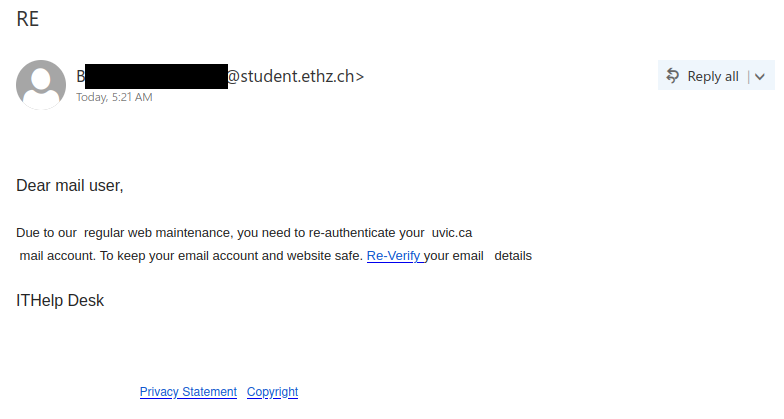
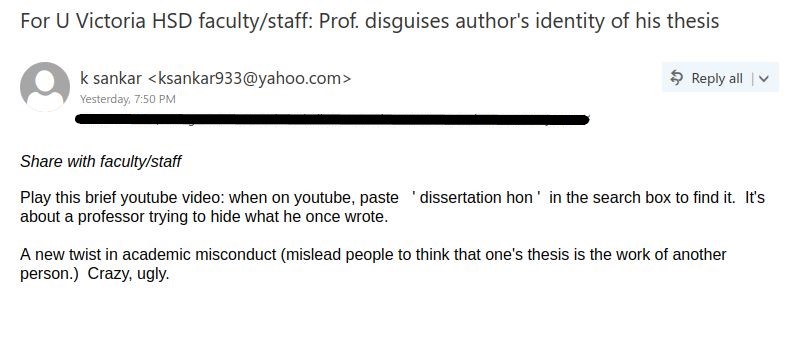
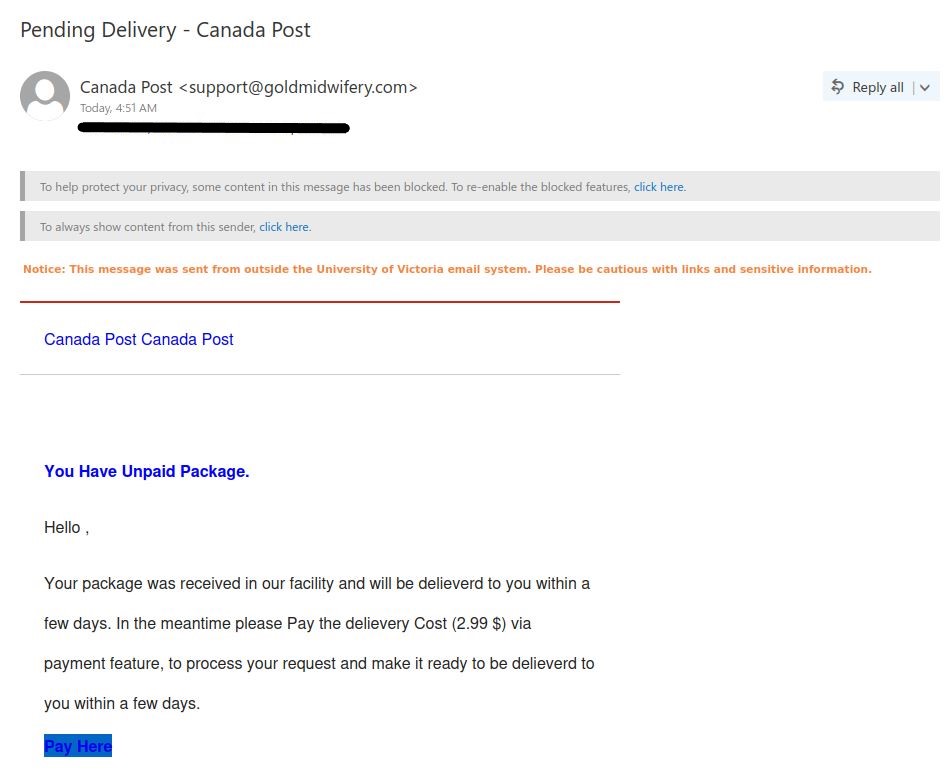
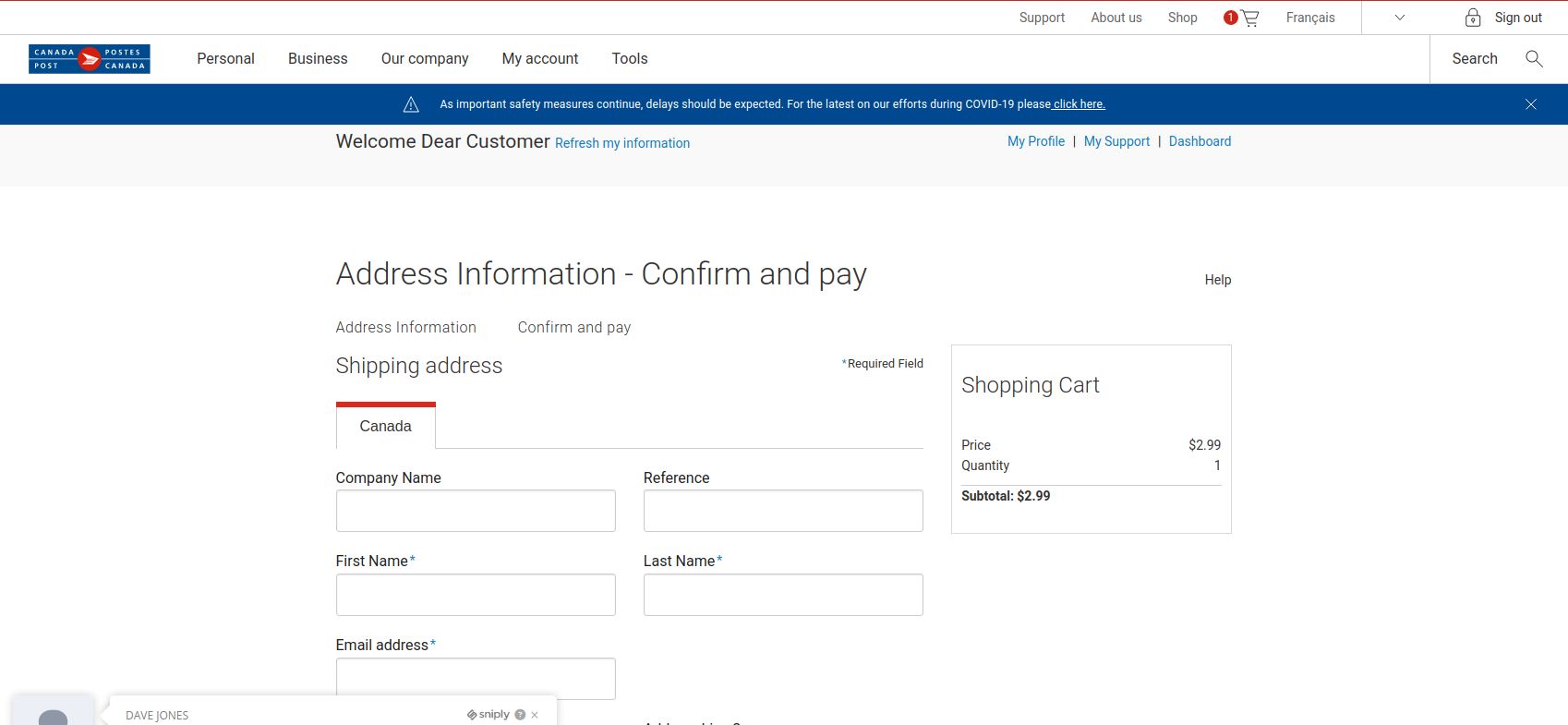
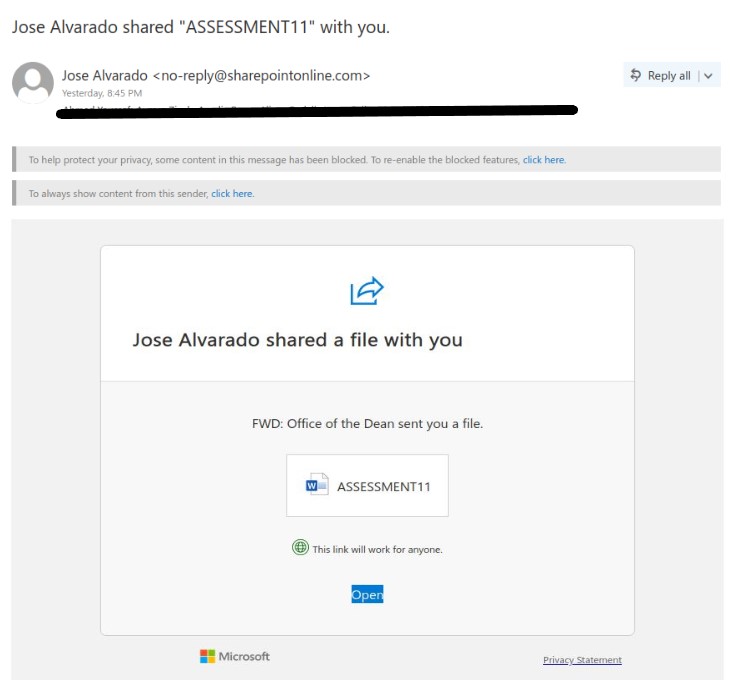
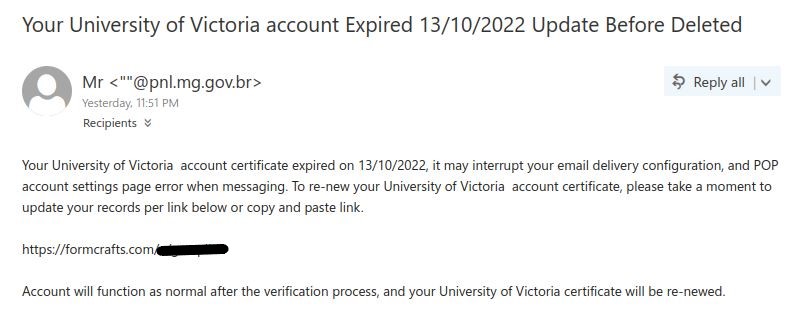
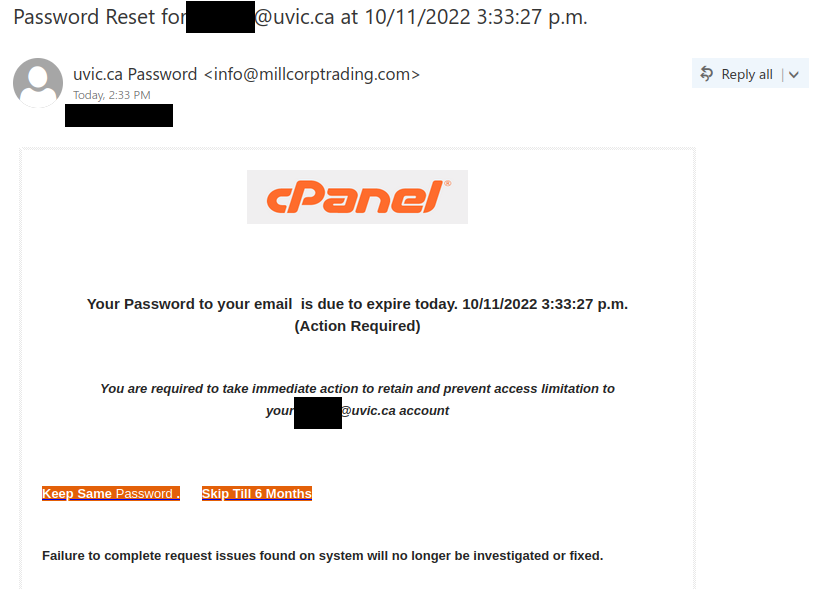
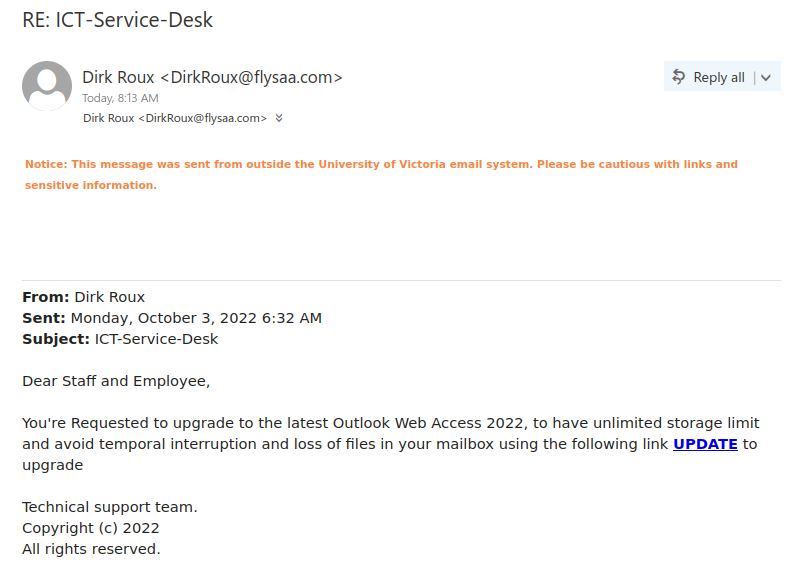
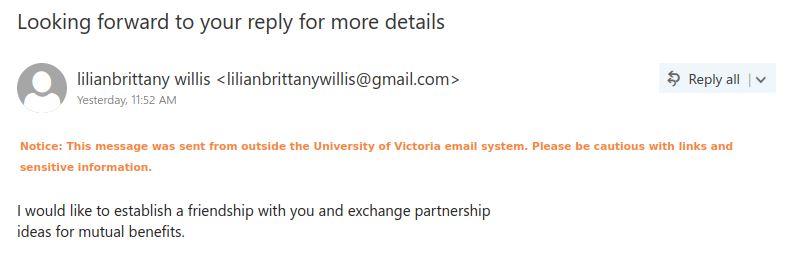
If you received this phish, with either of the above subjects, claiming to be from CRA please be cautious and do not click on the link provided. This phish has a usual tactic of phishers to give a too good to be true offer.
Some of the warning signs: Sender name is vague and fake, “Canada”, sender email address is not hosted on CRA domain, generic salutation (CRA know your name beyond just “client”), the link is external to CRA i.e., not hosted on CRA domain.
The best way to confirm such emails is either to call CRA directly or if you have an online account with CRA, sign-in to your CRA account (only on legit CRA website) and check emails or notices in the “Mail” section. Never fall for too good to be true offers, always question the possibility of such offers.
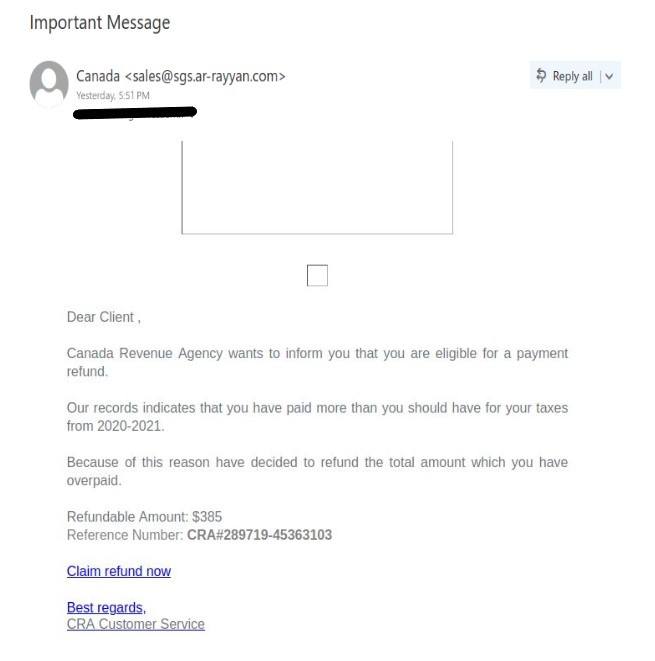
Note: sender address could be different, from the above image, in the phish you may have received.