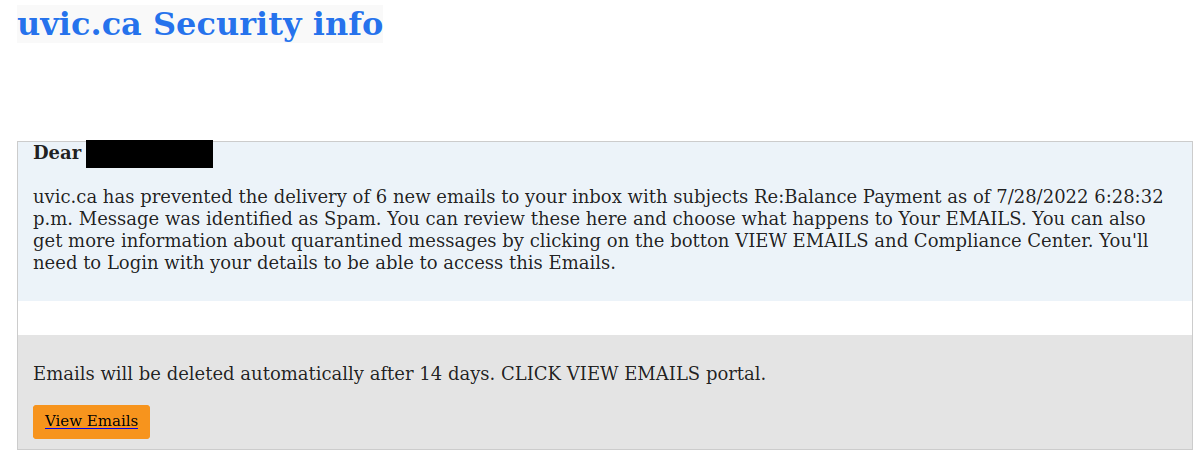
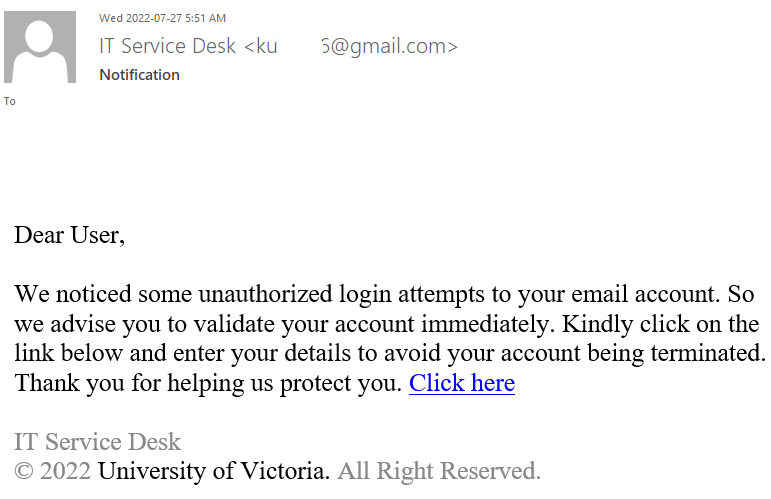
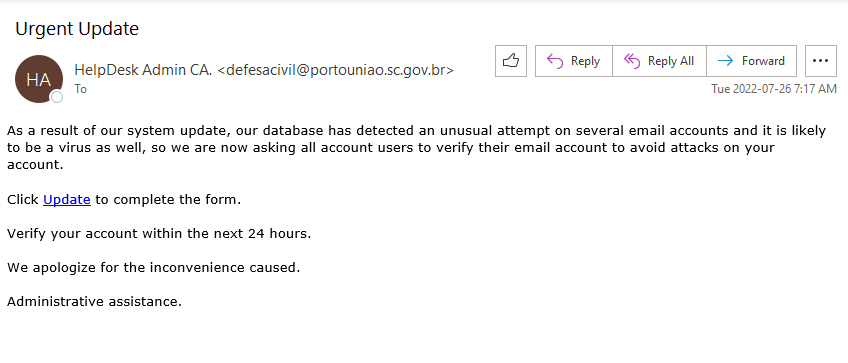
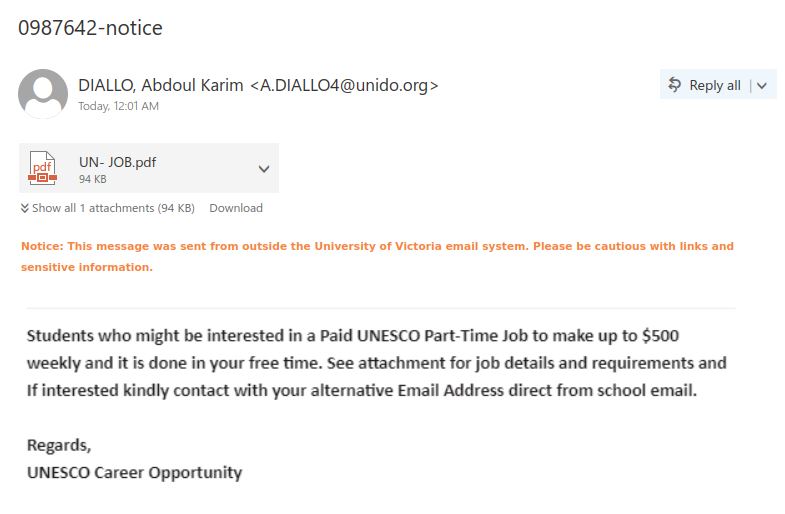
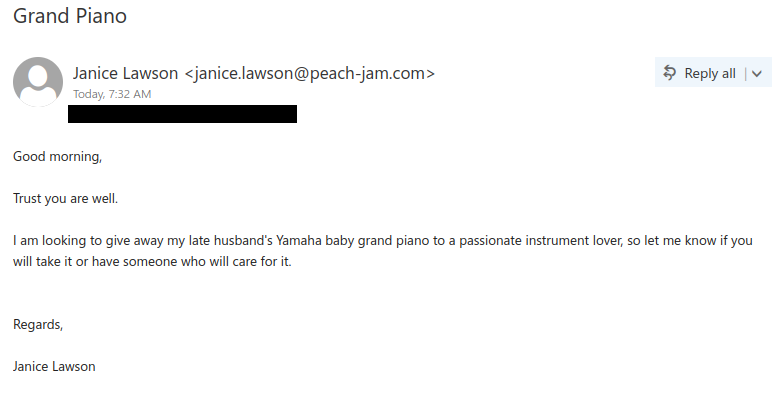
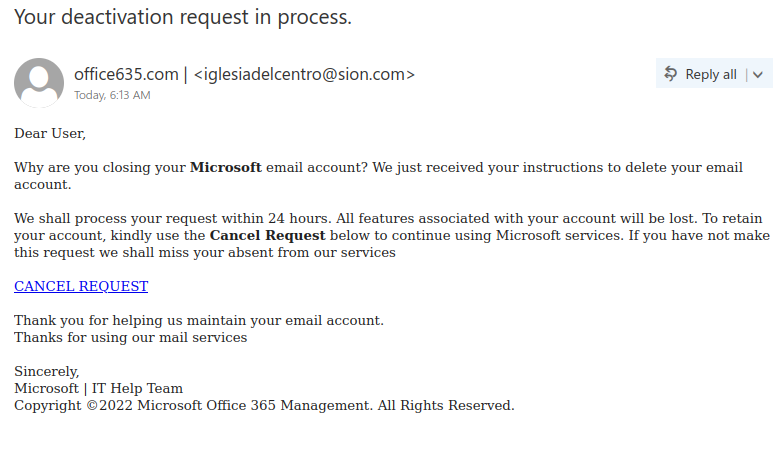
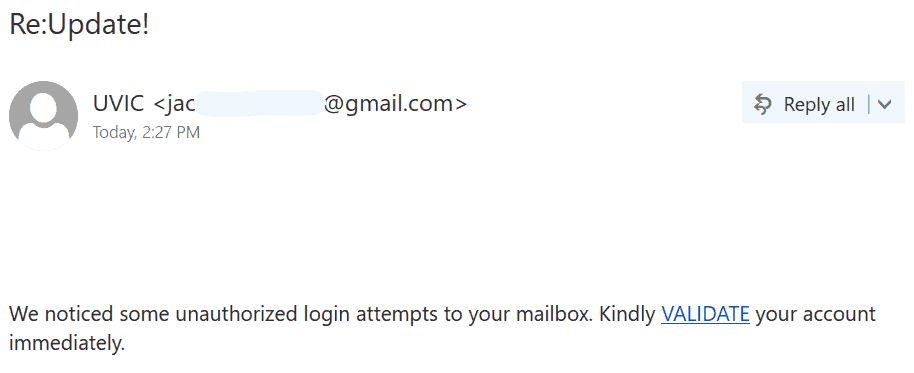
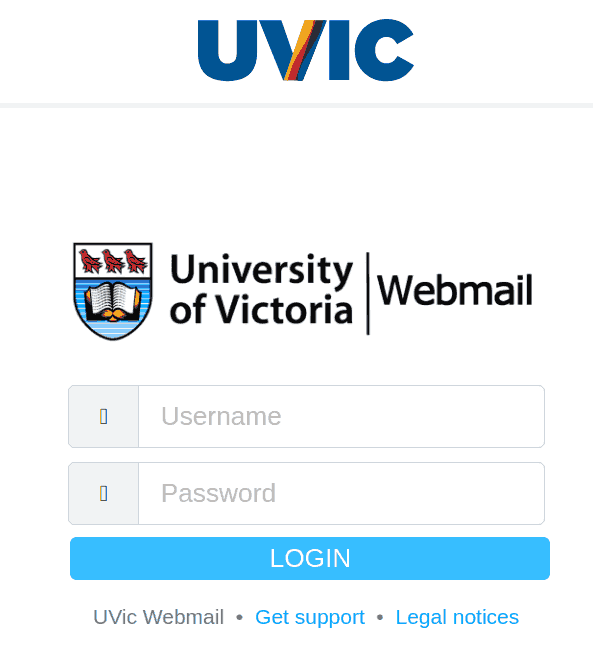
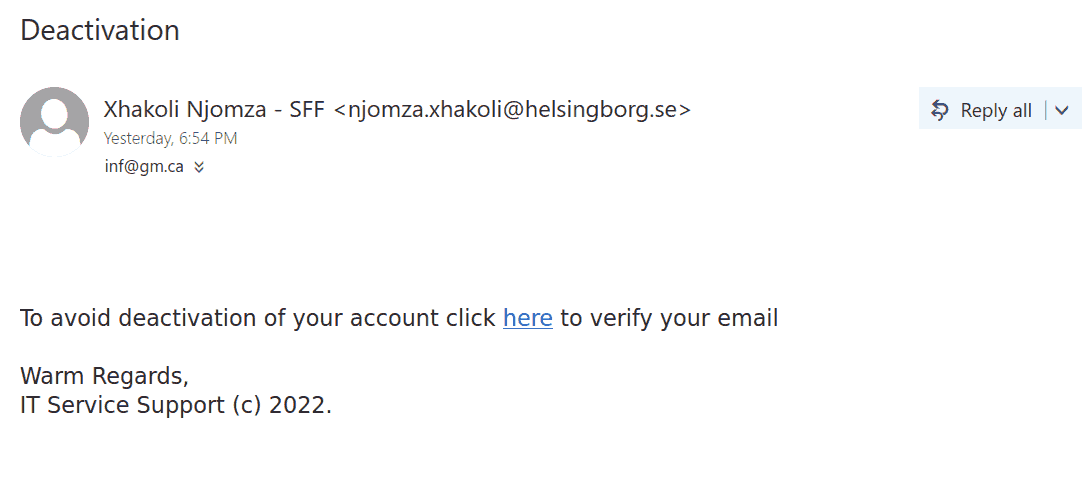
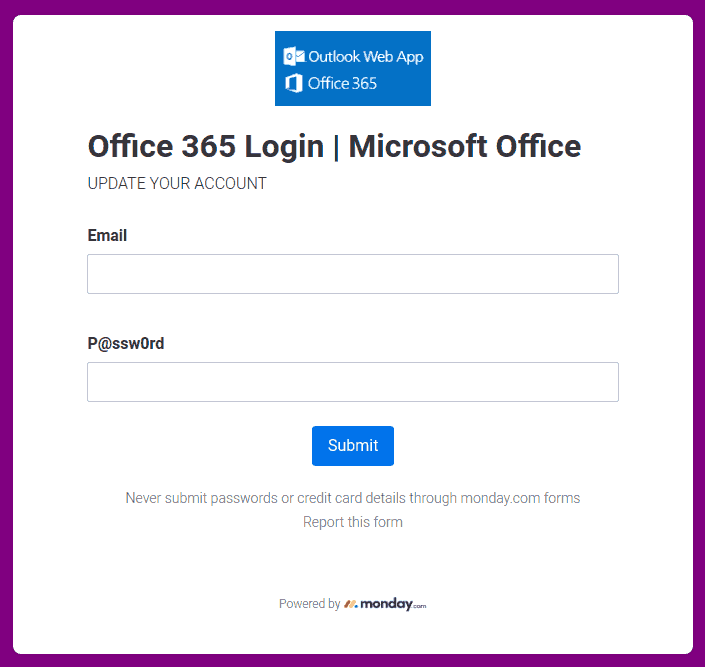
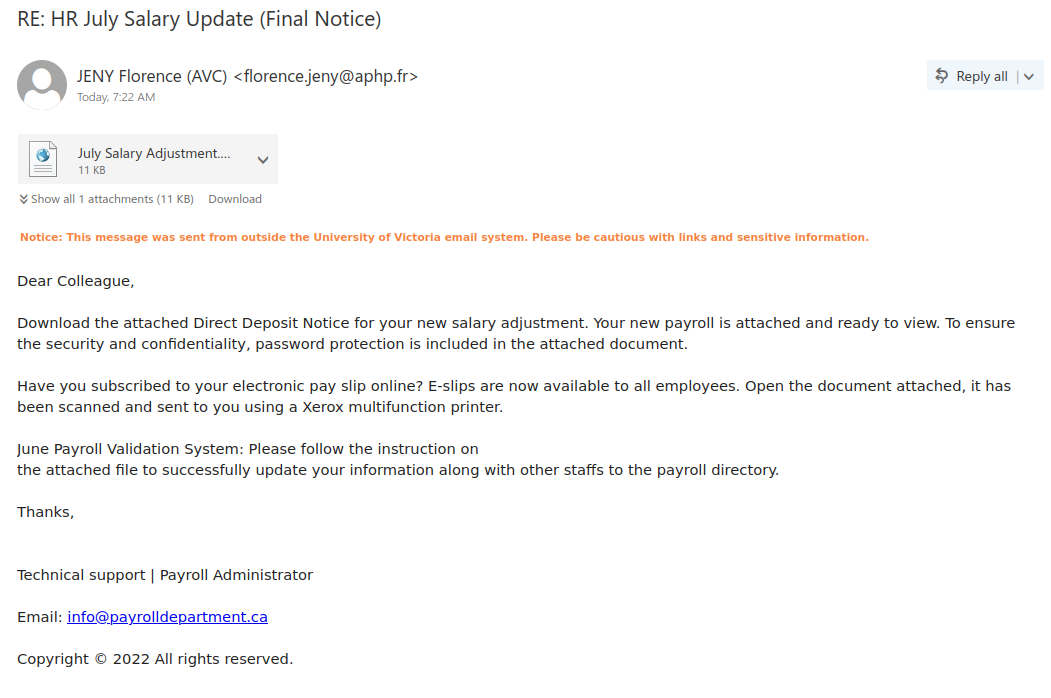
This email was mostly received by recipients in a particular department, hence could be a case of spear-phishing.
It had the usual tactics of creating a sense of urgency that your email account is about to expire so verify it by clicking on phisher’s link.
Warning signs: sender name is ‘Uvic Notification’ and sender email is external, vague signature ‘Web Administrator’ (not a UVic signature), if you hover over the link you would know the link is external (you will never be asked to verify a UVic account on a external domain).
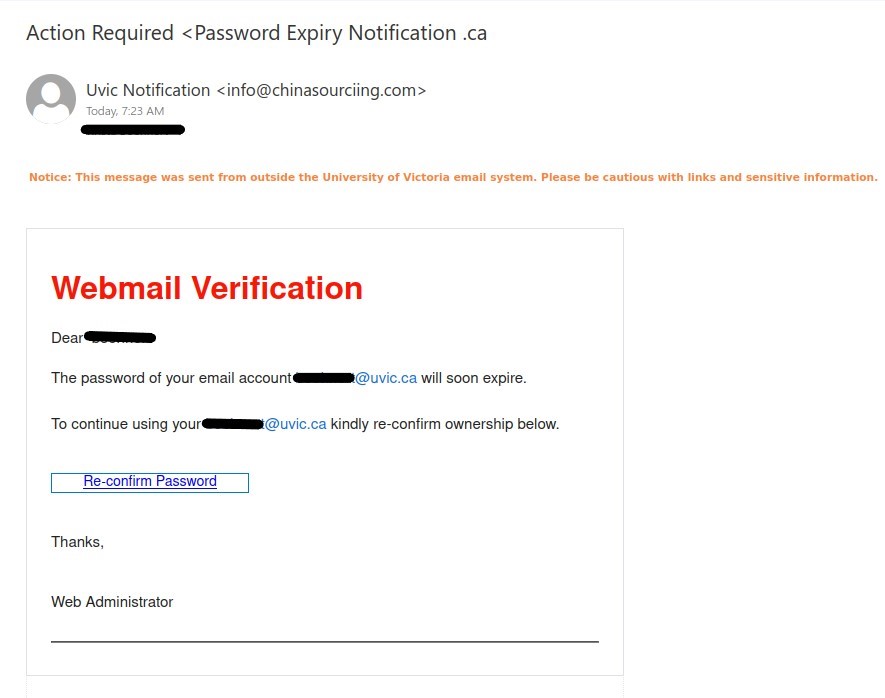
Whenever in doubt, you can contact your DSS support or helpdesk for confirmation. It is always best to be cautious than be curious.