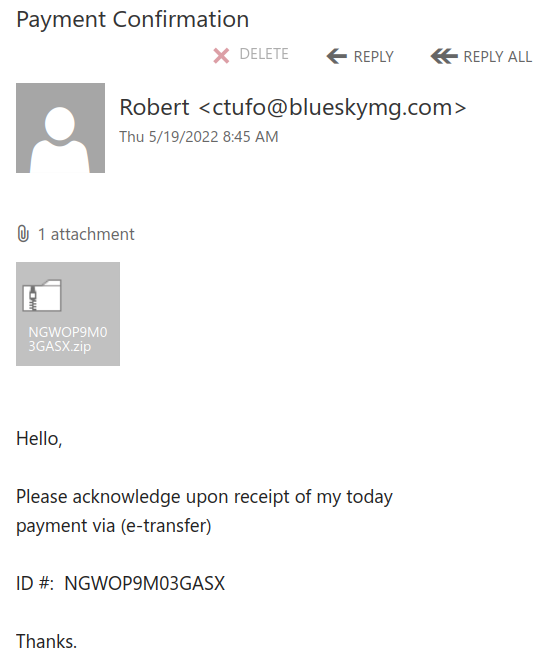
An email with a subject “payment confirmation” is circulating today. To avoid detection the malicious actors made a huge executable file (containing the malicious code) then put that executable file into a .iso file and then zipped that .iso.
The zip file is about 2Mb in size and attached in the email.
Please do not open these attachments! If in doubt, first ask your Desktop support person or the Helpdesk.
In the screenshot below it is shown the sender is an external one. As is usual for such campaigns they used many different sender addresses.