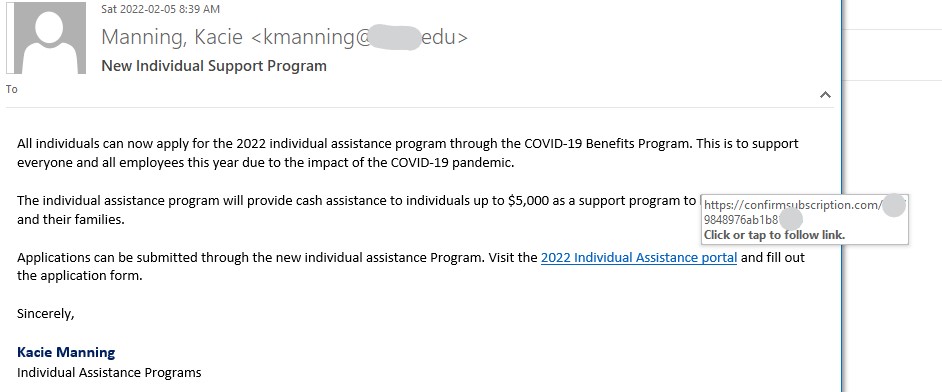
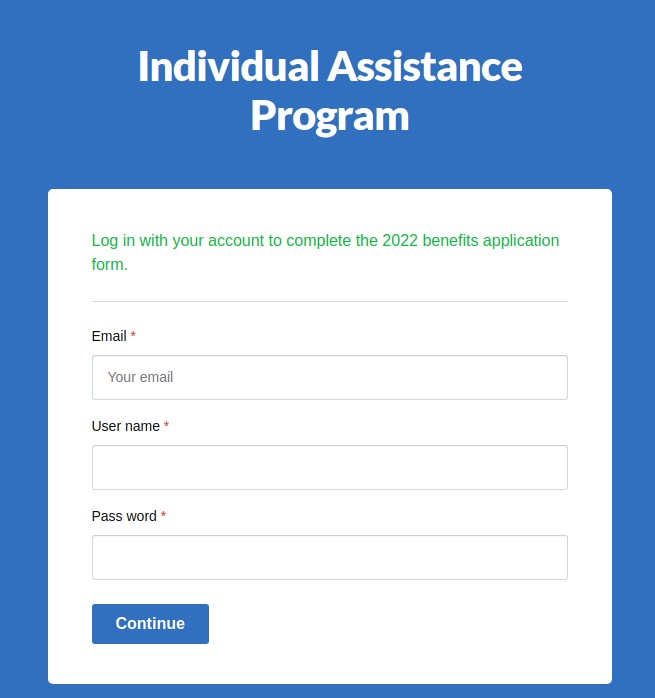
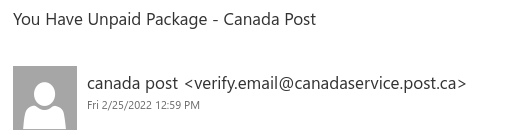
This Canada Post phish even includes a few links to real Canada Post websites at canadapost.ca canadapost-postescanada.ca to try and make the email look legitimate. However, the “Pay Here” link that you’re directed to click on is the one link in the email that does not go to a legitimate site. It actually goes to a completely different site with a phish form that imitates Canada Post branding and aims to trick you into providing your personal information.
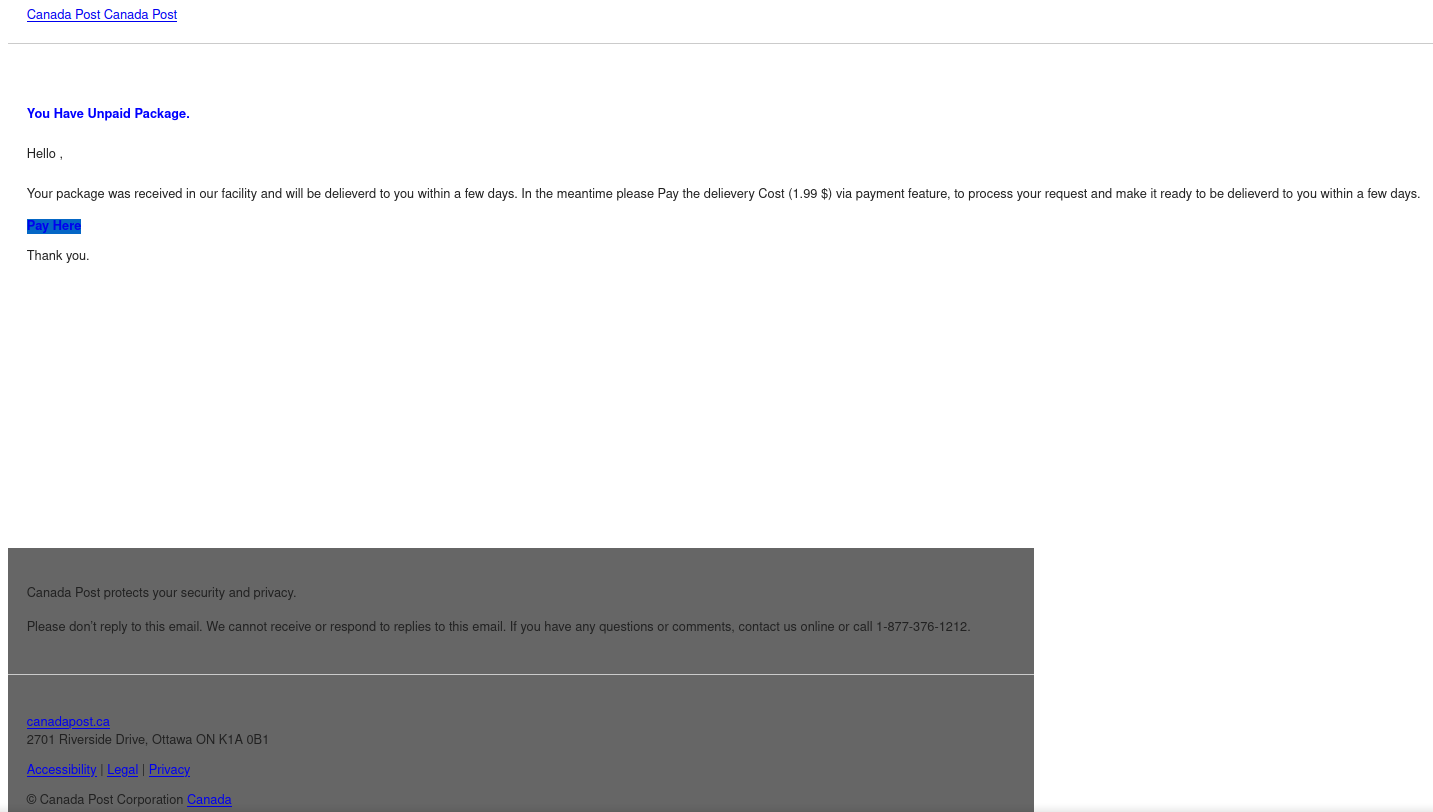
It’s worth noting that the sender was very cleverly crafted to look like it could be a Canada Post email address. But in reality, post[.]ca (to be safe, don’t go to that site) doesn’t actually belong to Canada Post.

 ——————————————————————————–
——————————————————————————– ———————————————
———————————————