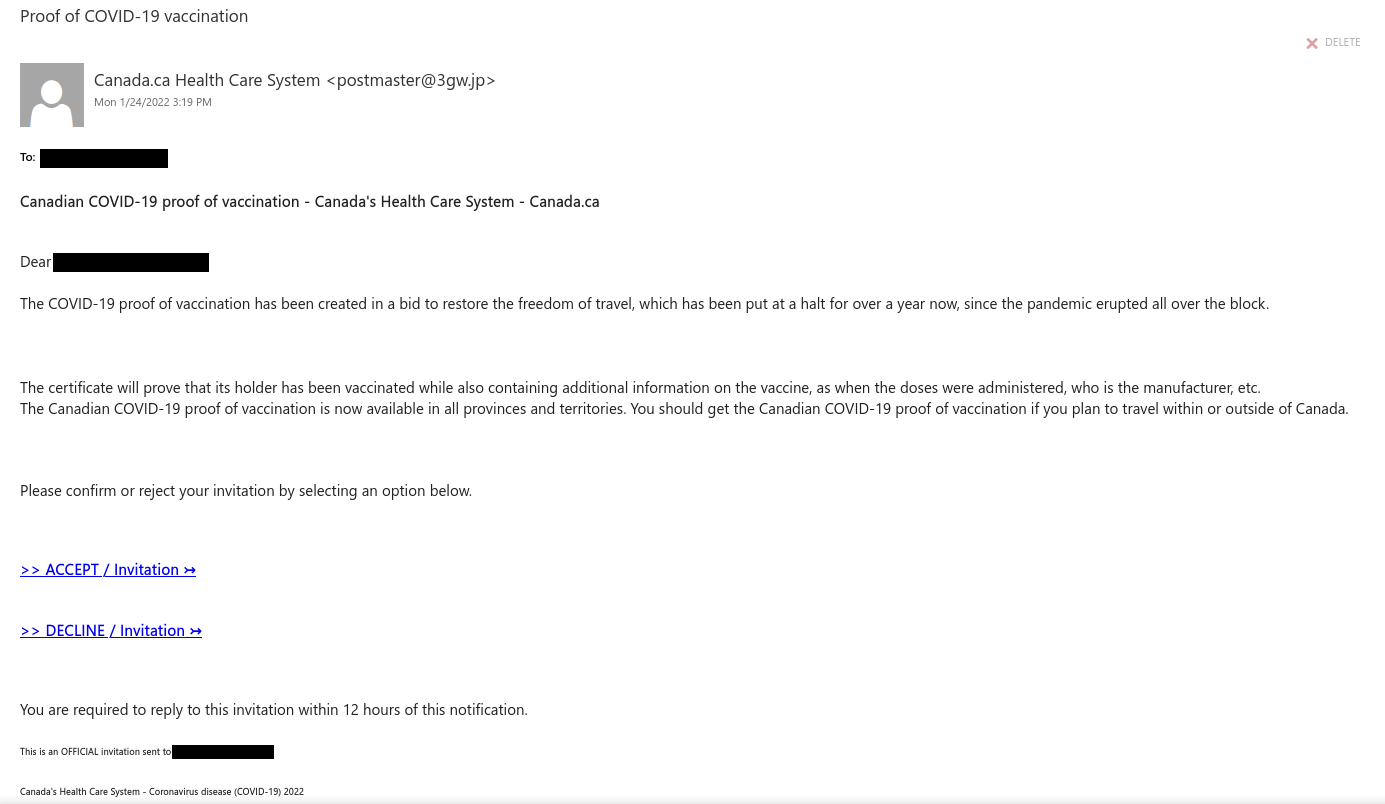
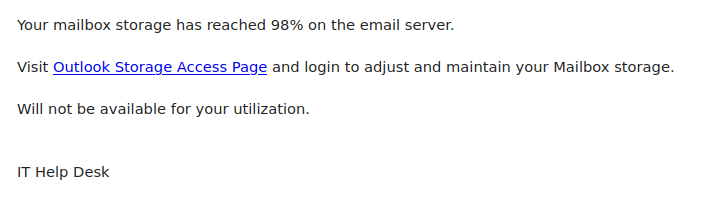
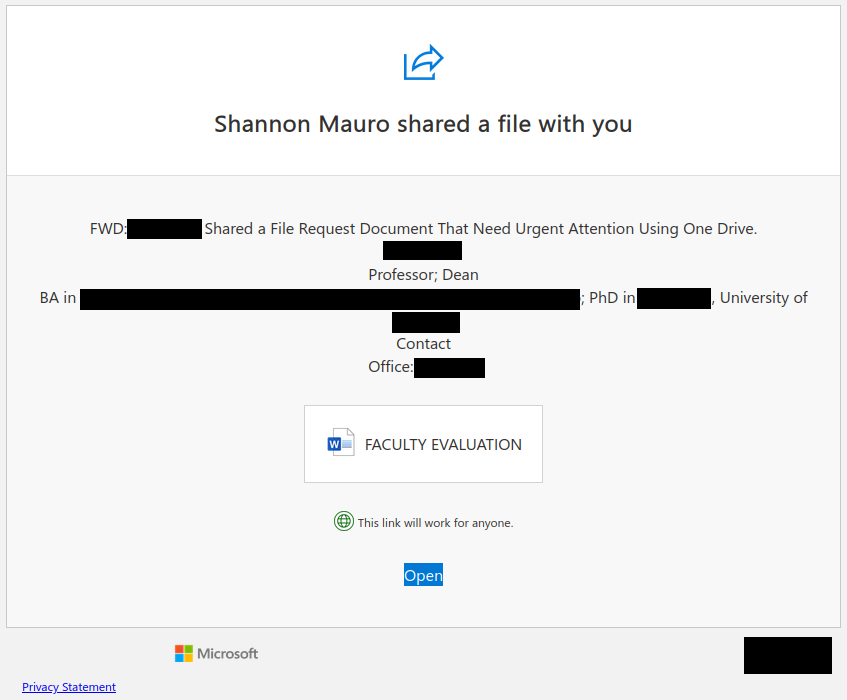
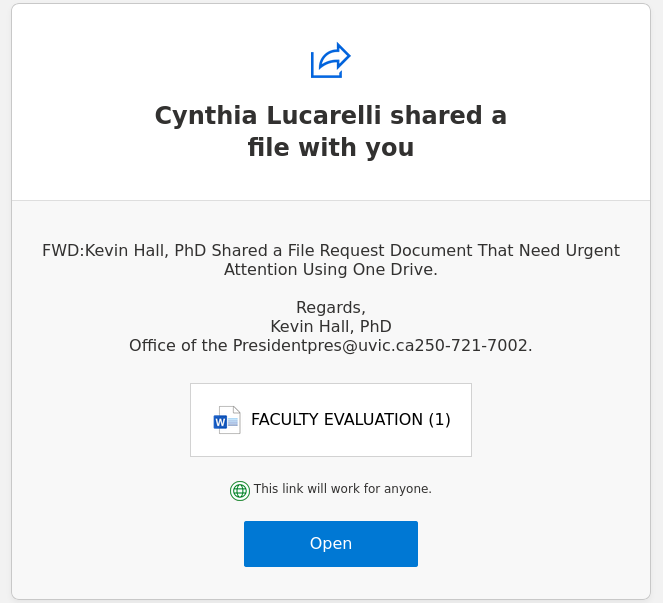
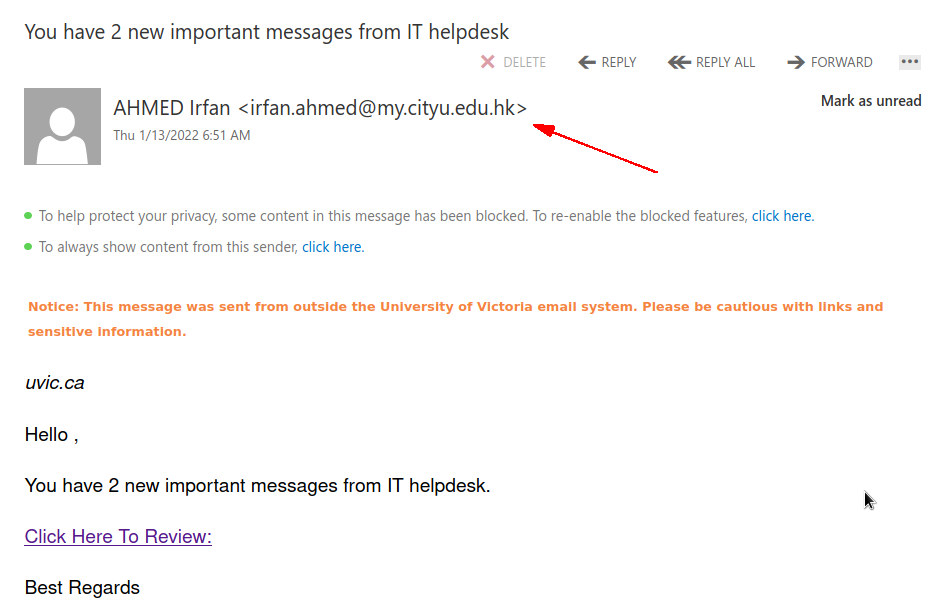
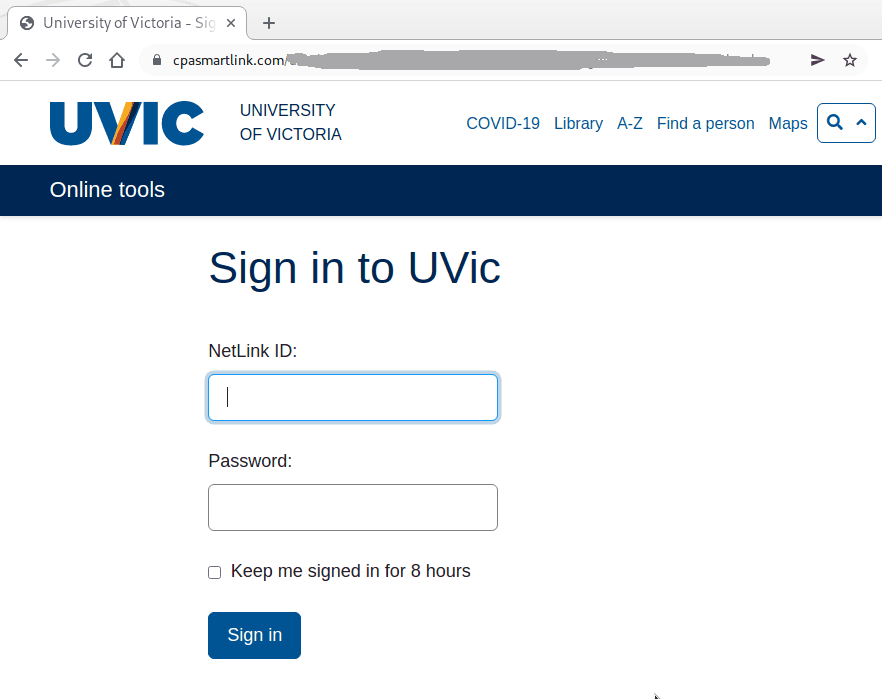
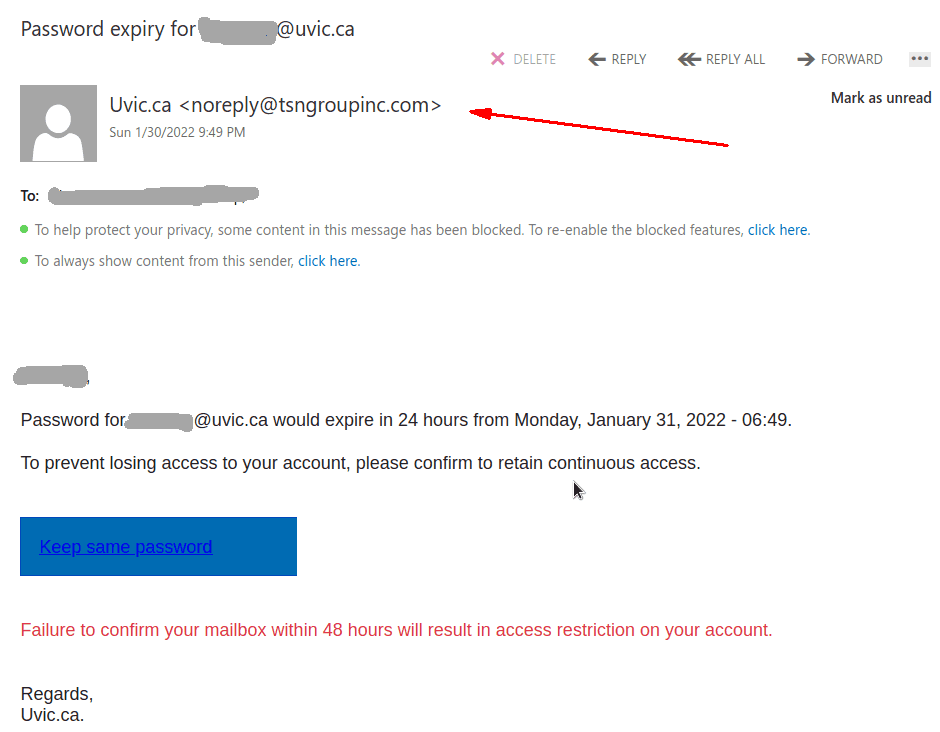
This phish was received by many UVic recipients today. The usual tactic is employed – to scary the recipient to act fast, otherwise their password (allegedly) would expire. We don’t send such emails.
Note also the sender address — clearly external.
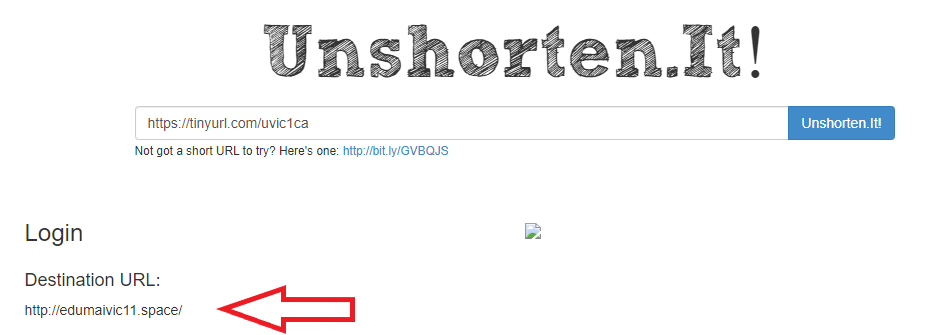
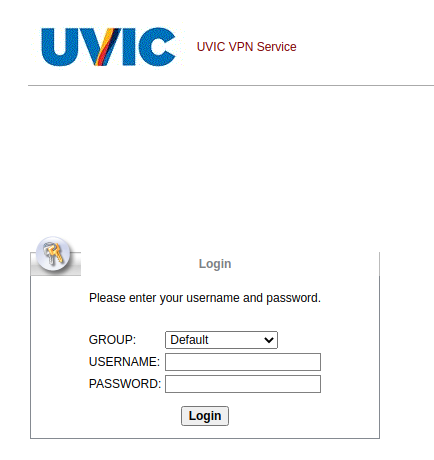
If you hover the mouse over the link (without clicking!) you will notice it is not a UVic address there. That link redirects to another which contains a CAPTCHA, to imply legitimacy, and after that you end up with the usual login page designed to steal your UVic credentials. The page contains your UVic email address thus implying you are at the right place. You are not.
=================================================================
This is how the fake page looks like:
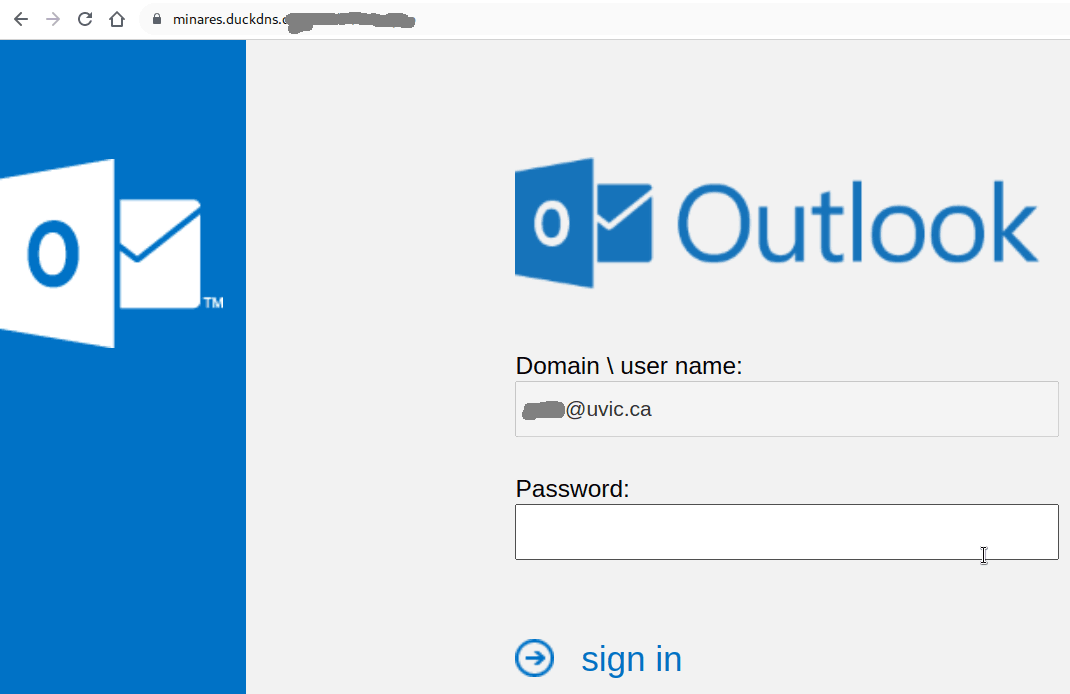
It is important to remember that in some cases just loading the web page may get your workstation infected. This is why we always suggest not to be curious and not to click on such links even for a quick look. Our experts open those in dedicated isolated environments.