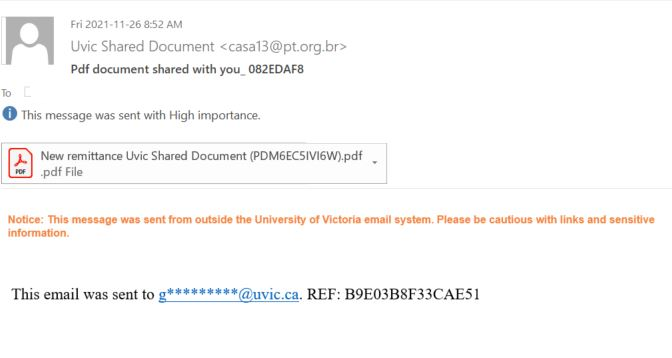
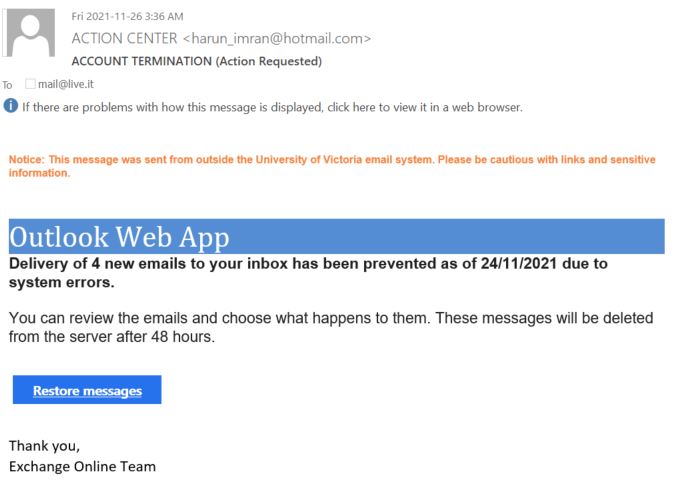
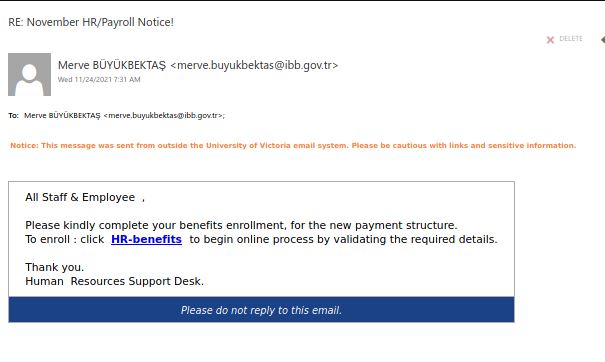
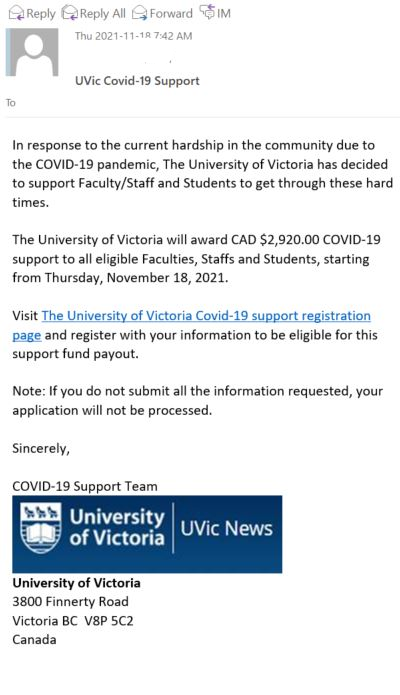
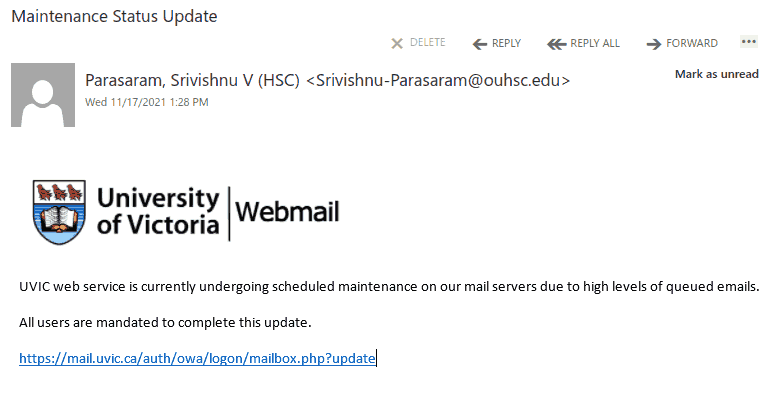
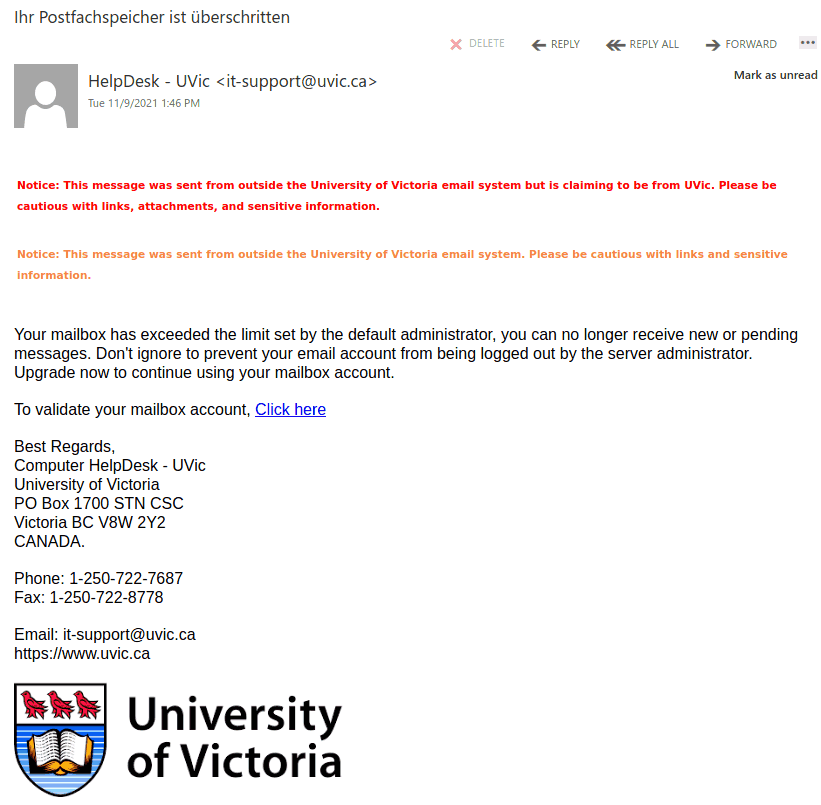
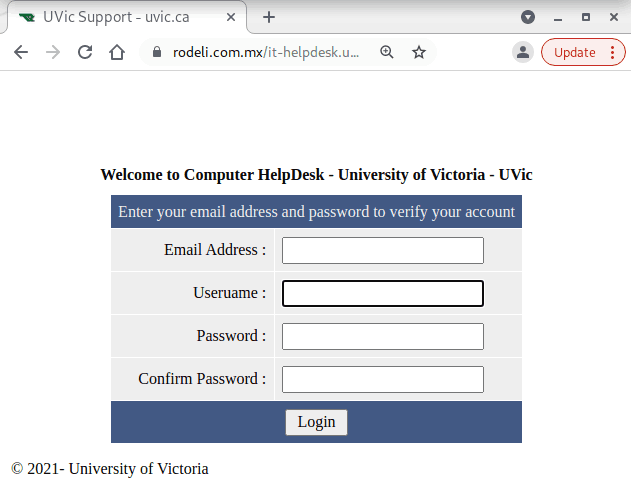
This phish is circulating today, but we have seen similar in the past and perhaps there will be more in the future. What is common — they contain a malicious .htm or .html attachment.
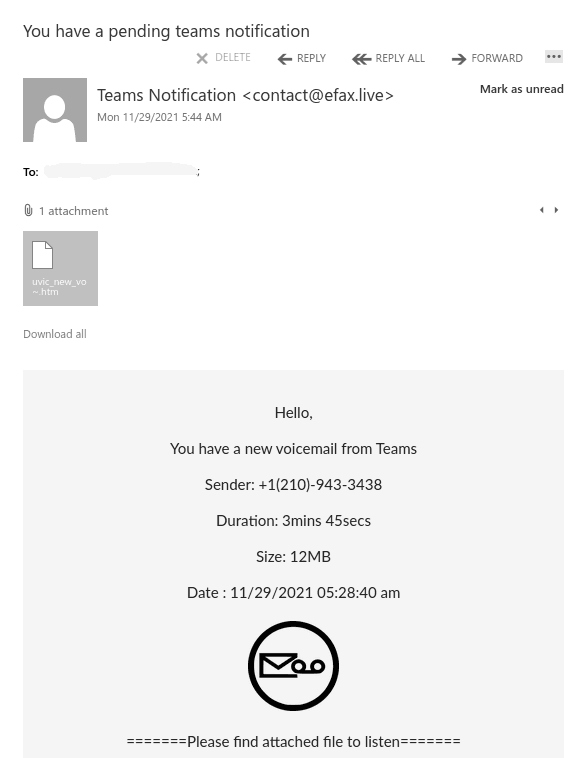
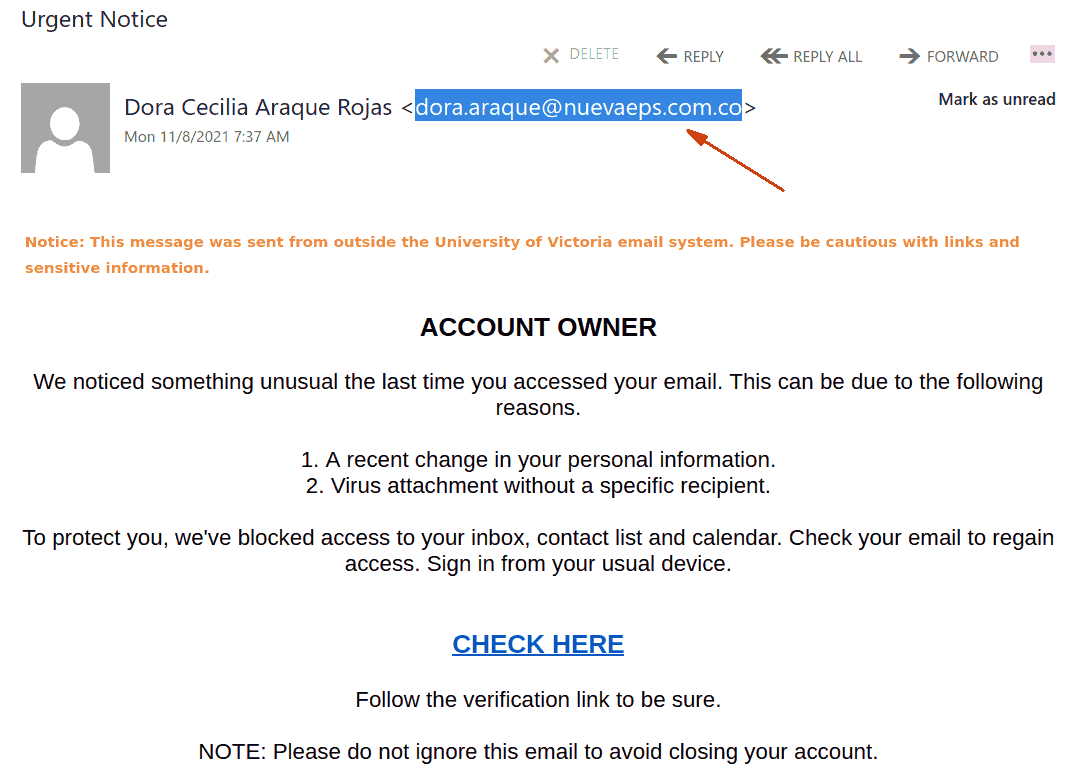
The one from today (see a screenshot below) raises too many red flags:
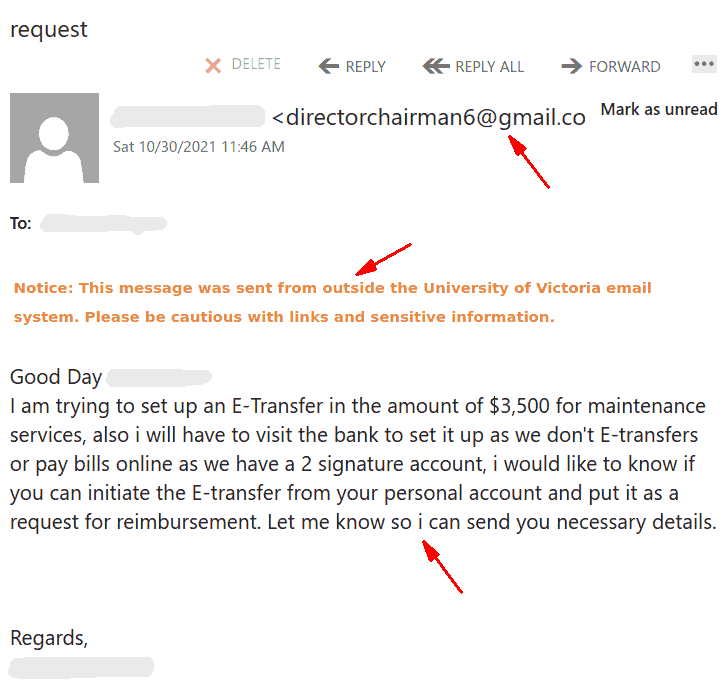
- It comes from some external sender.
- Voicemail from Teams???
- Claims the size to be 12Mb but it is actually very tiny.
- A voice recording wouldn’t come in a html file
Please ask the Helpdesk or your dedicated Desktop support person but never open these attachments if not sure about their legitimacy.
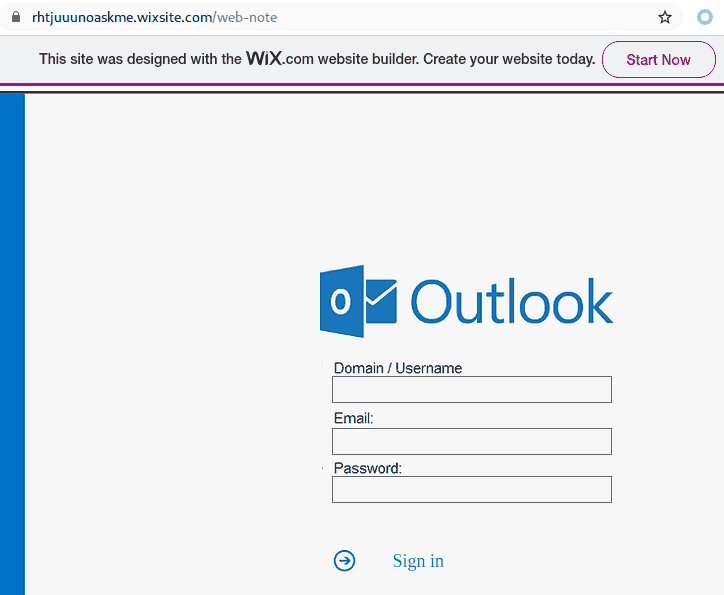
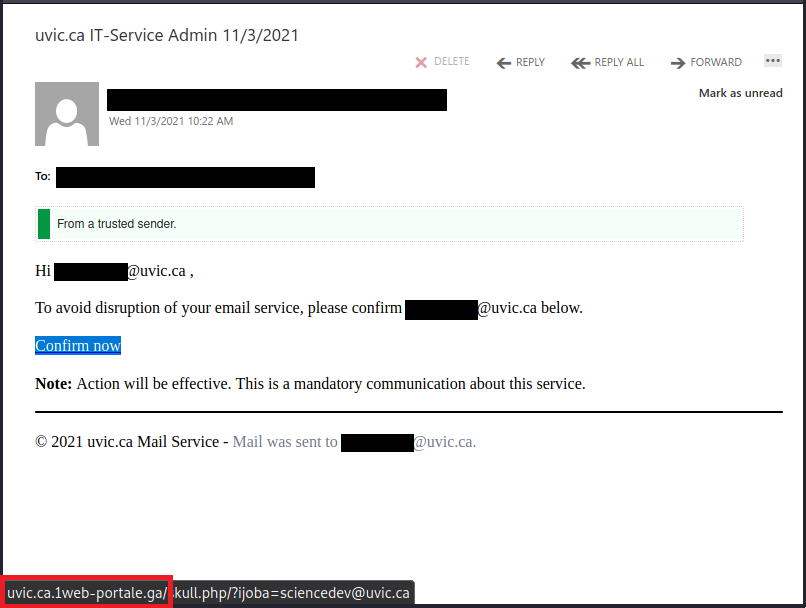
This one in paricular contains a link which loads up automatically in the browser when you open the attachment. That page contains scripts that start downloading malicious content onto your computer.