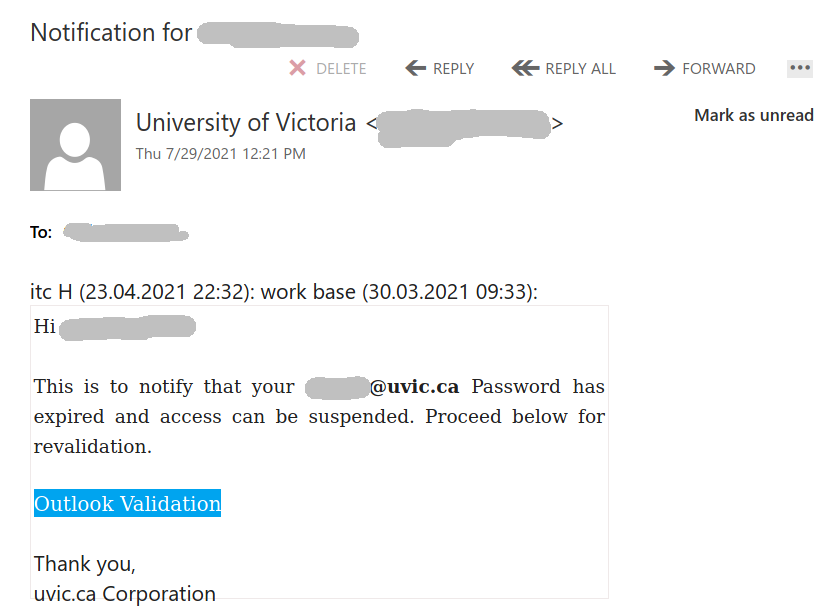
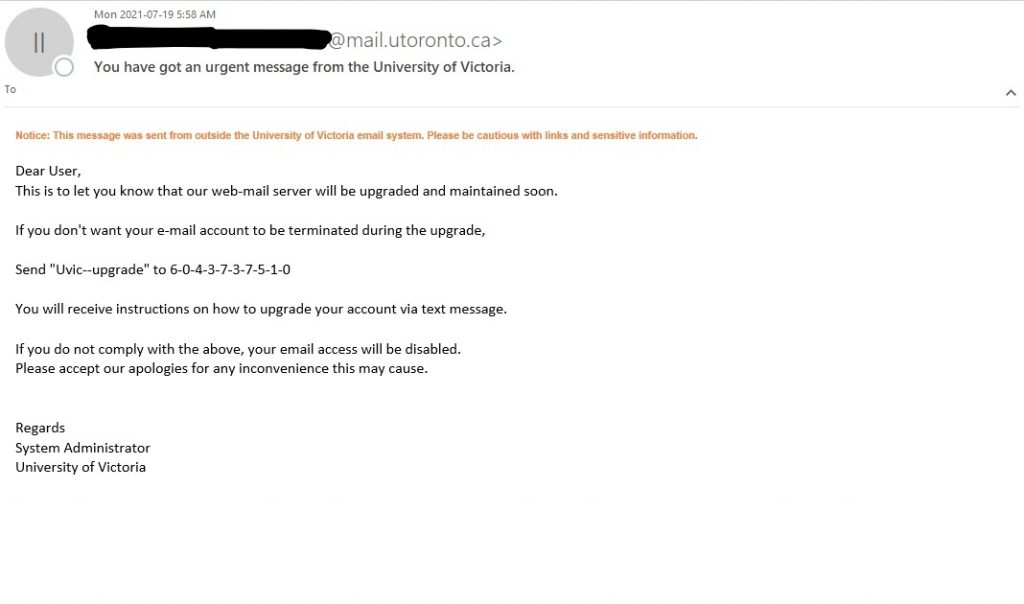
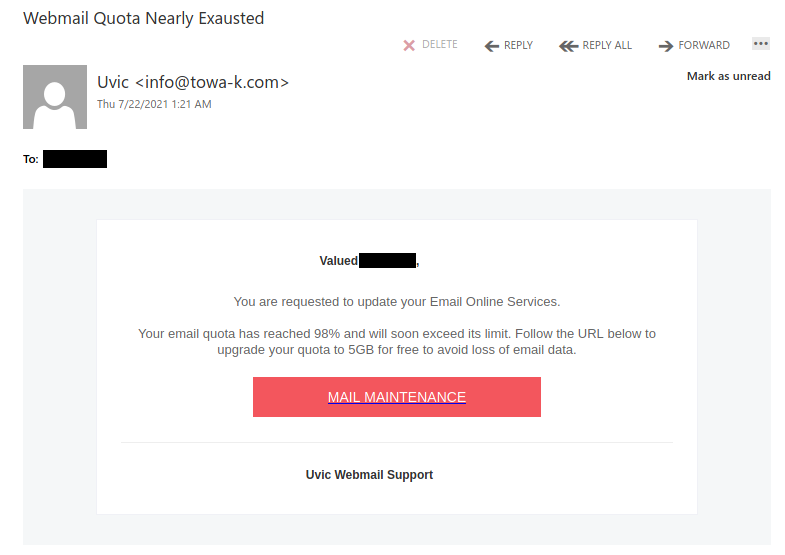
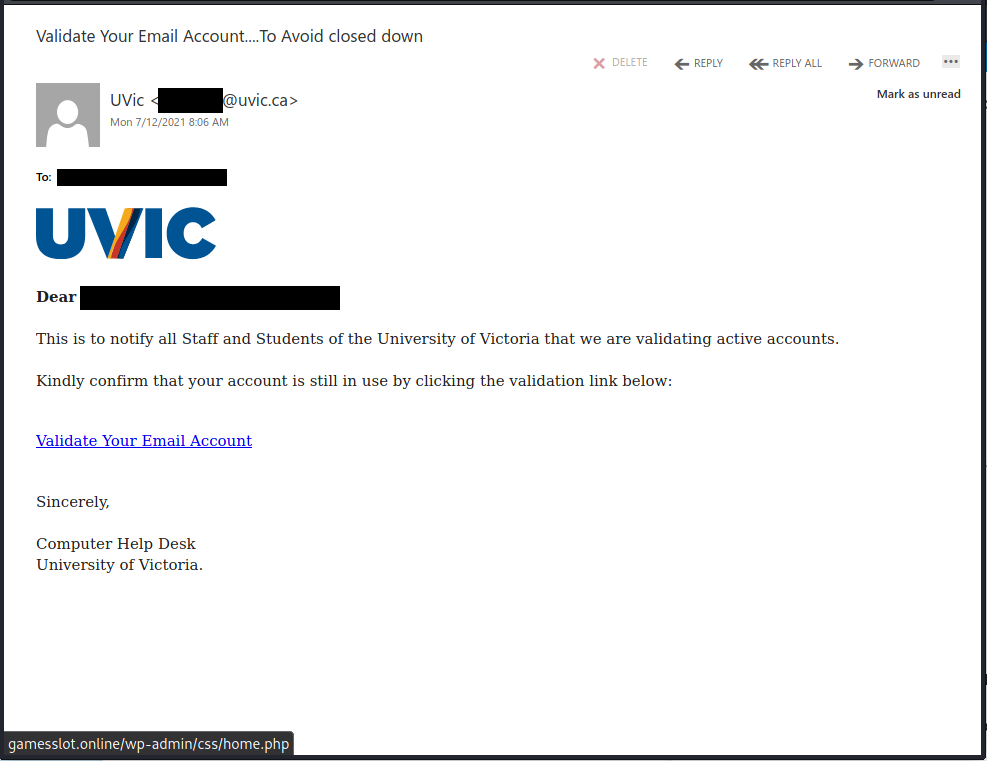
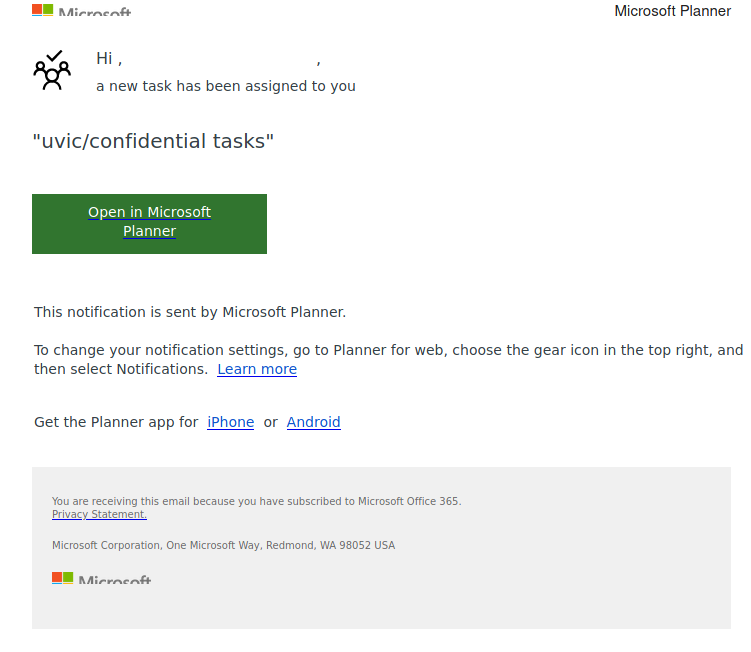
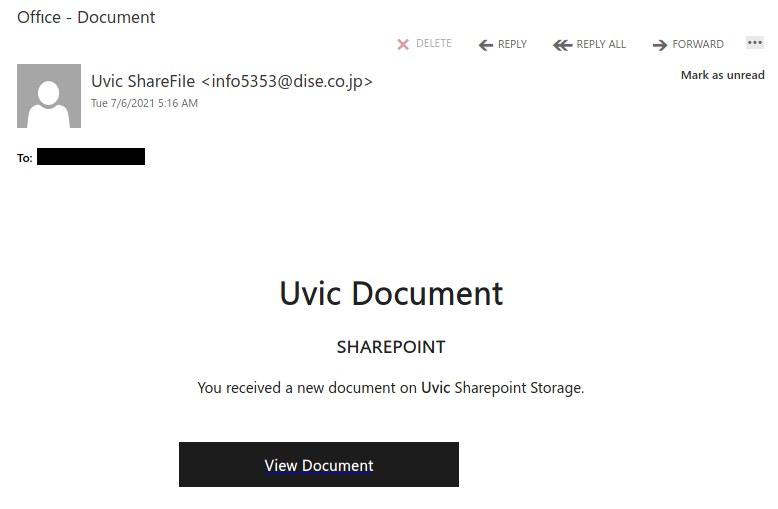
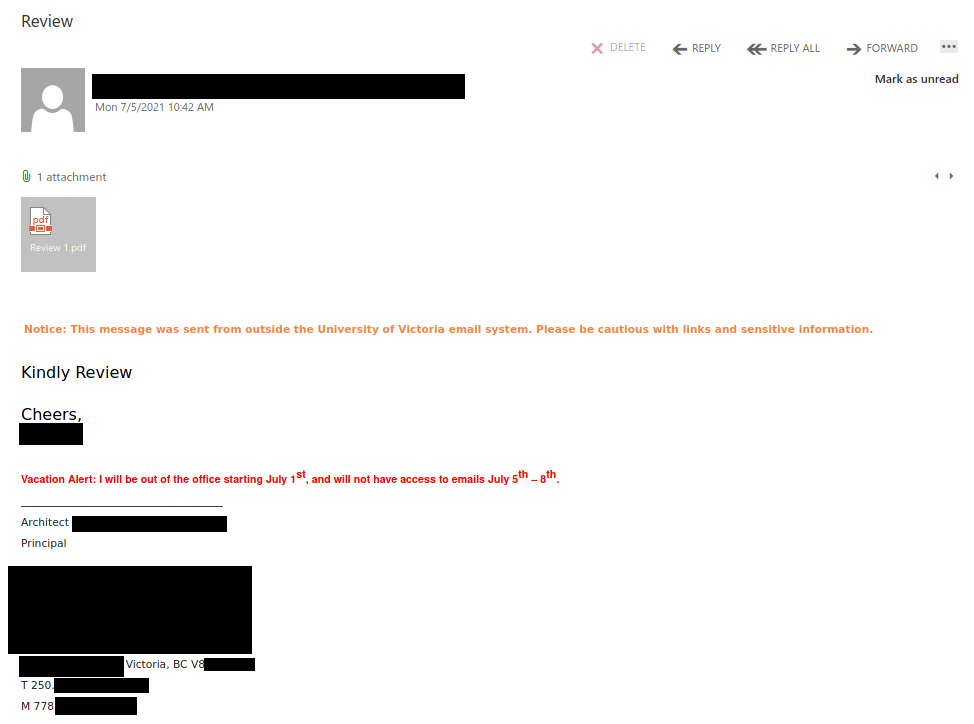
This is another phish circulating today July 29th.
Unlike the previous one, the sender obviously has nothing in common with UVic. But similarly to the previous one, their goal is the same – to steal your UVic credentials by pointing you to a fake Outlook Web Access page. Please do not be curious and do not click on the link. Sometimes those pages may contain malware and only by opening them, even for an instant, your computer may get compromised.