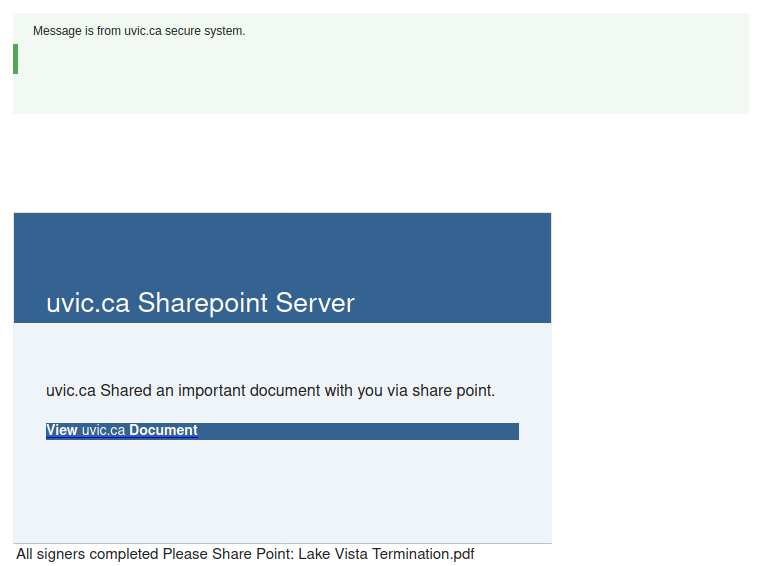
This one emphasizes the need to consider where you are accessing files from and how you expect them to be shared with you. UVic managed services are the only recommended way to share UVic work related documents.
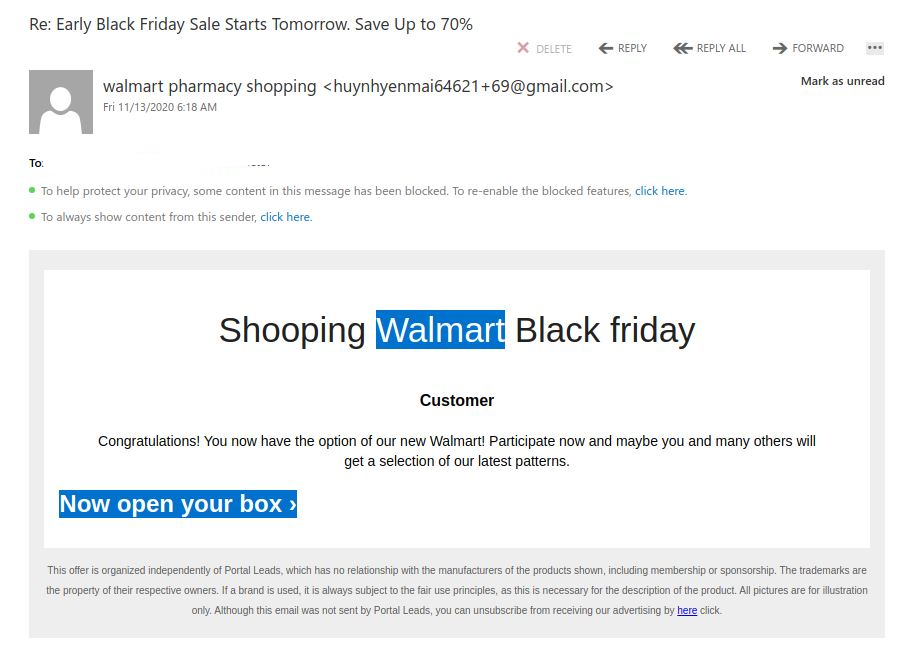
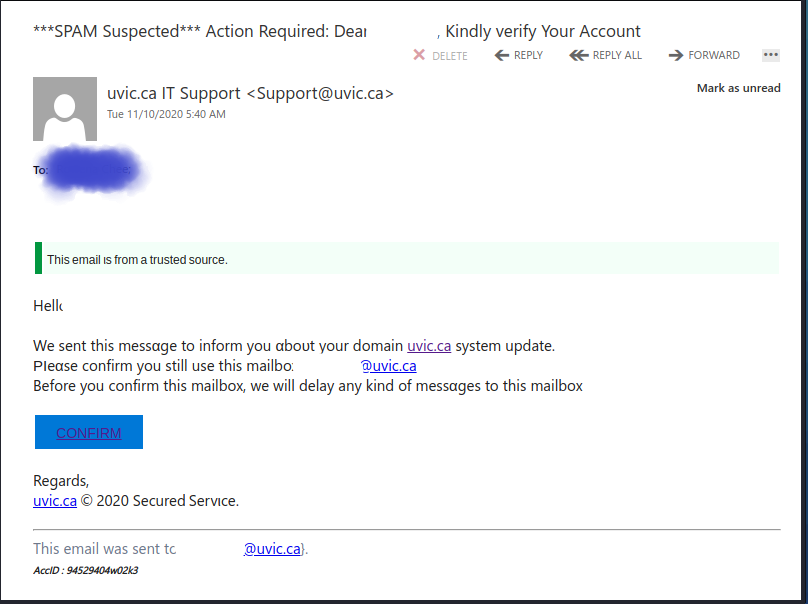
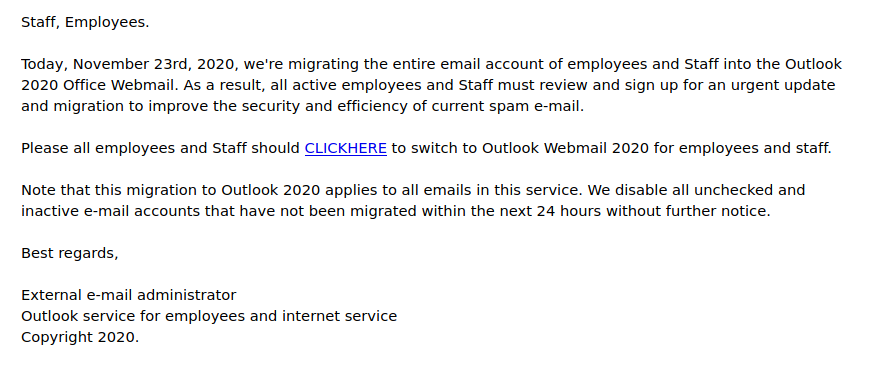
This one is tricky. You cannot rely on the visible senders here so much and of course there is some comfort in seeing they are using your legitimate name and email address. The supposed download also has Uvic in the name. NOT LEGIT.
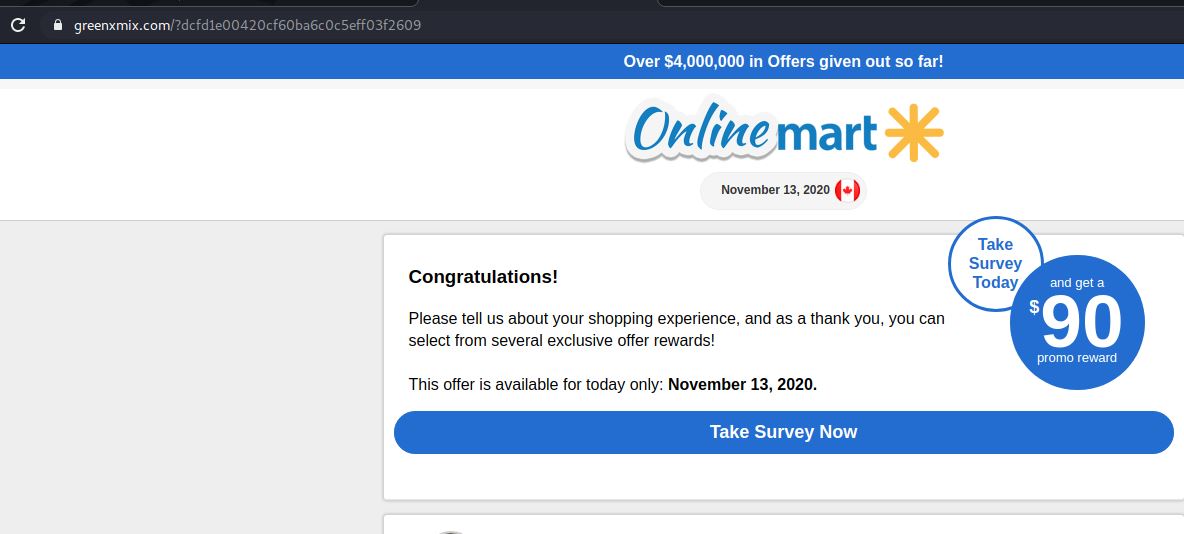
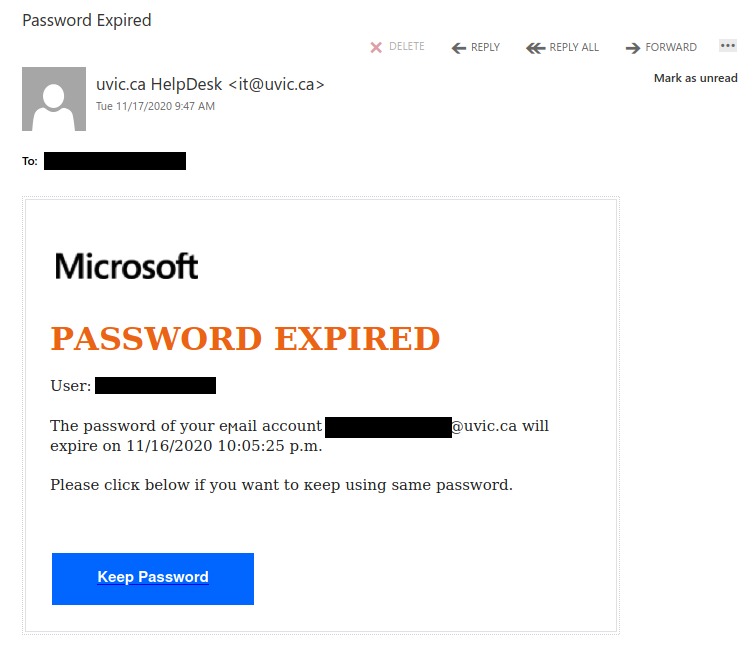
The caution here is, now that many of us are working from home and with the growth of cloud service use, specifically Microsoft and other big name products, we are becoming more comfortable with the idea that we may receive something legit from those sources. If you look at the body of this message, it does look phishy but it also looks as if it is coming from a known good Microsoft domain.
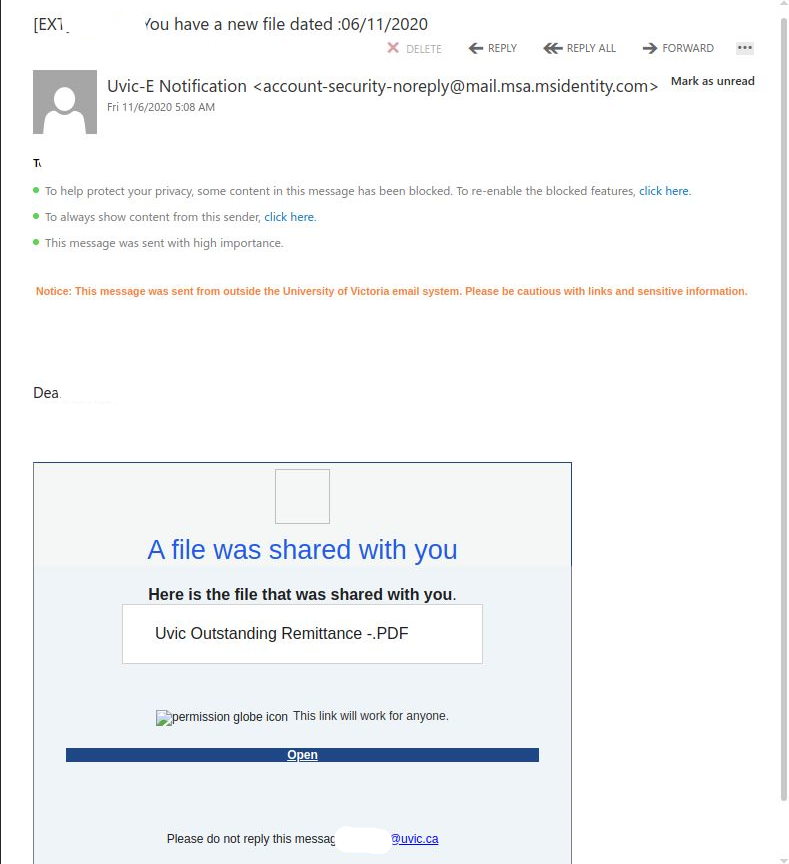
What you don’t see is a bad sender used/abused the Microsoft service to add a bit of authenticity to the message. This one was actually sent from a likely compromised .jp email address.
Question to ask yourself:
- Which services are UVic managed and offer sharing among your teams? How have you been sharing with your department all along? In most cases, they are accessible outside the email link reference and directly accessible via your UVic device or an application you use regularly.
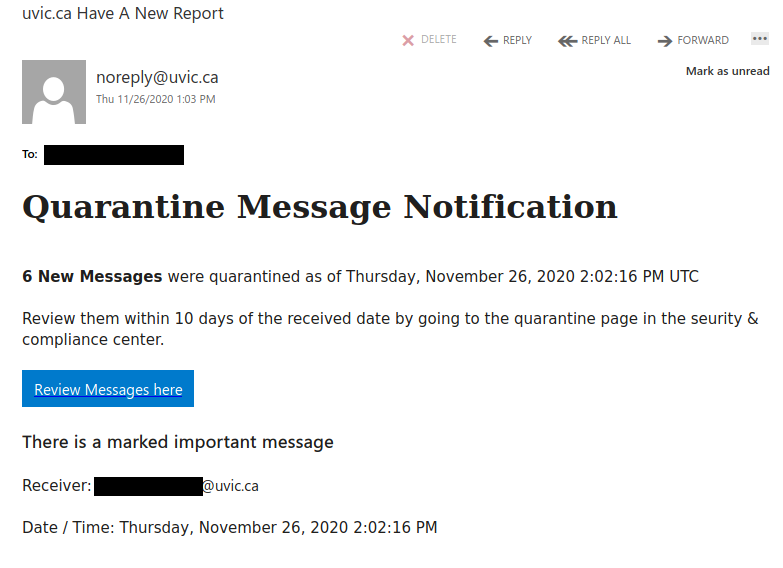
PAUSE.
Follow your gut.
There is no rush.
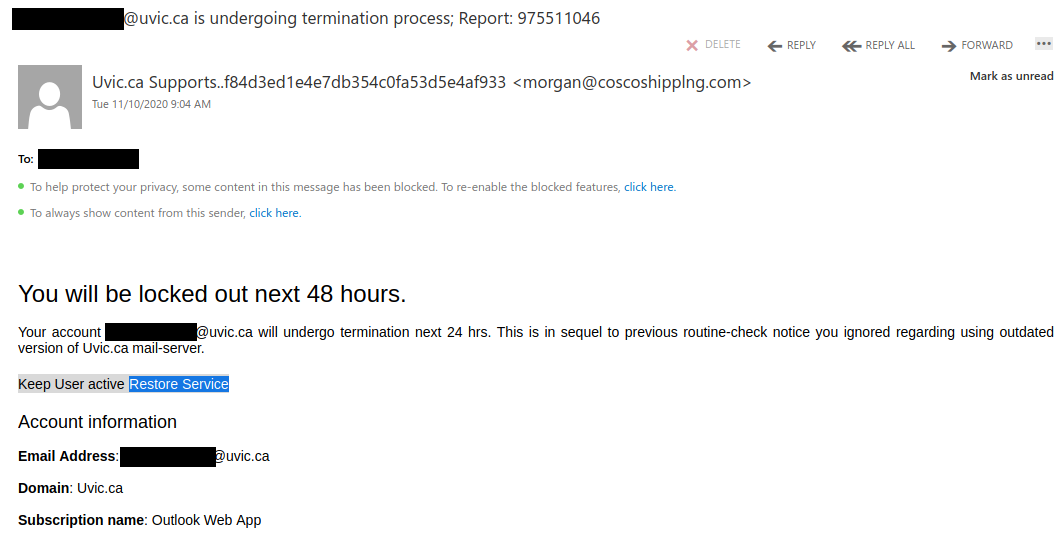
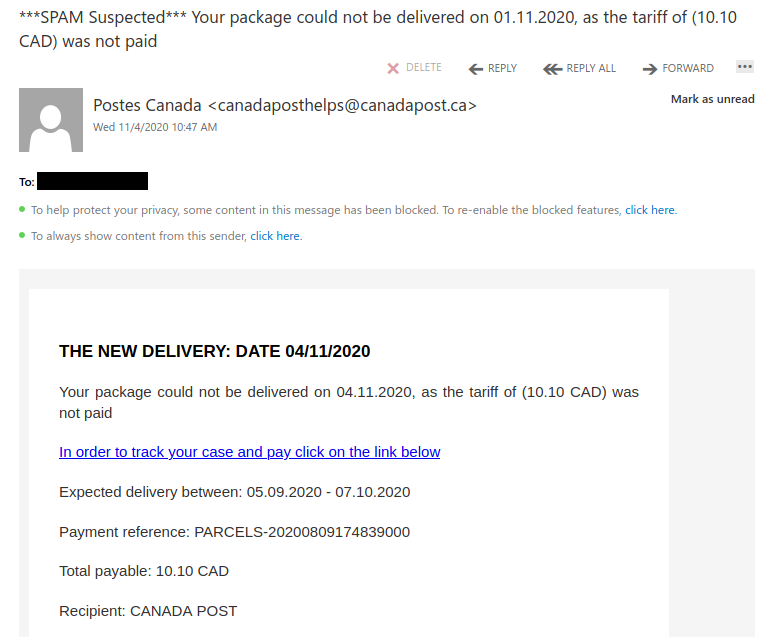
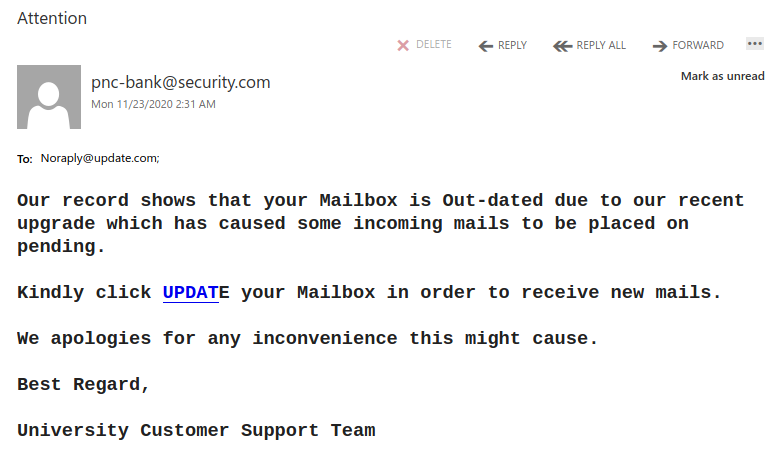
This one doesn’t include a known contact but oftentimes, you can call your colleague or contact them via a different known good method. eg. phone, and verify whether or not they have sent you something.
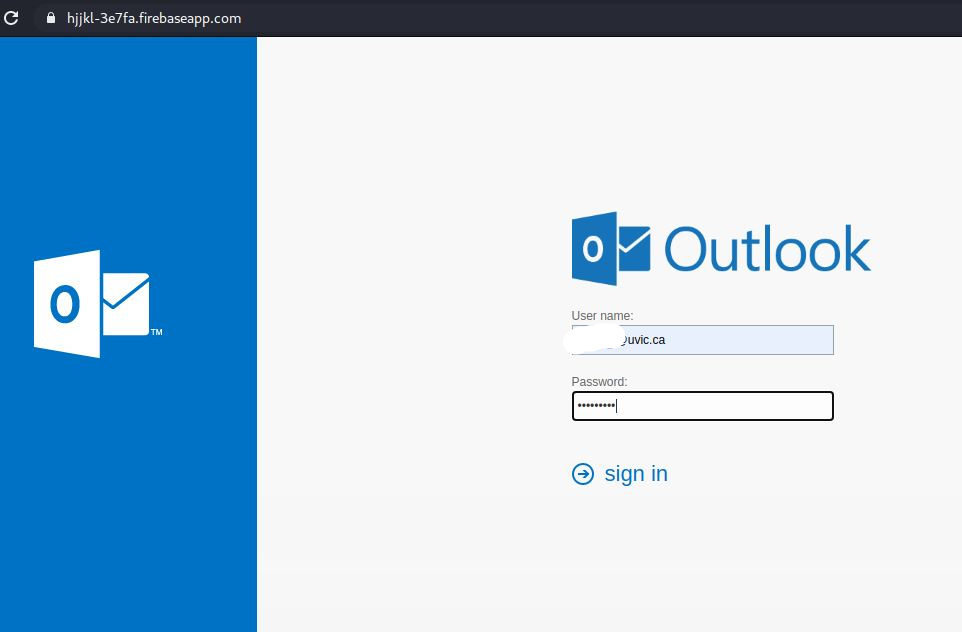
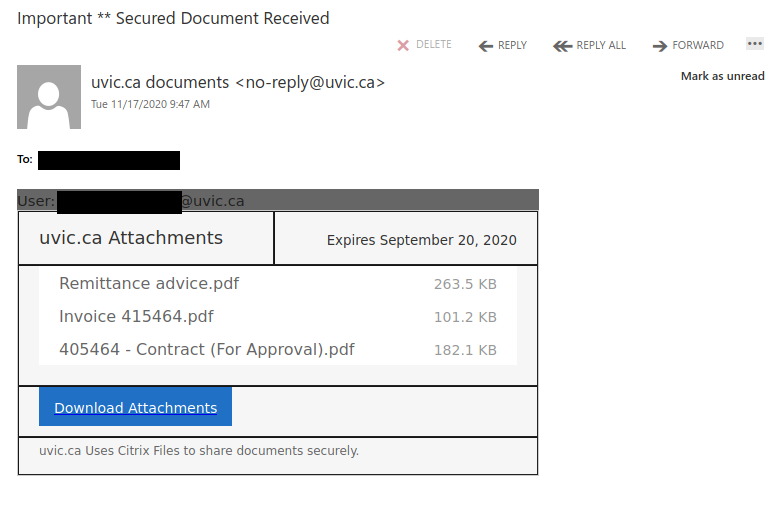
In addition to Microsoft service being abused here, if you hold your mouse over the PDF or the Open link, you’ll see they are also abusing a legit Google hosting service called firebase. The Firebaseapp is the legitimate Google service, the trailing link off the end goes to a website, that again, is NOT LEGIT.
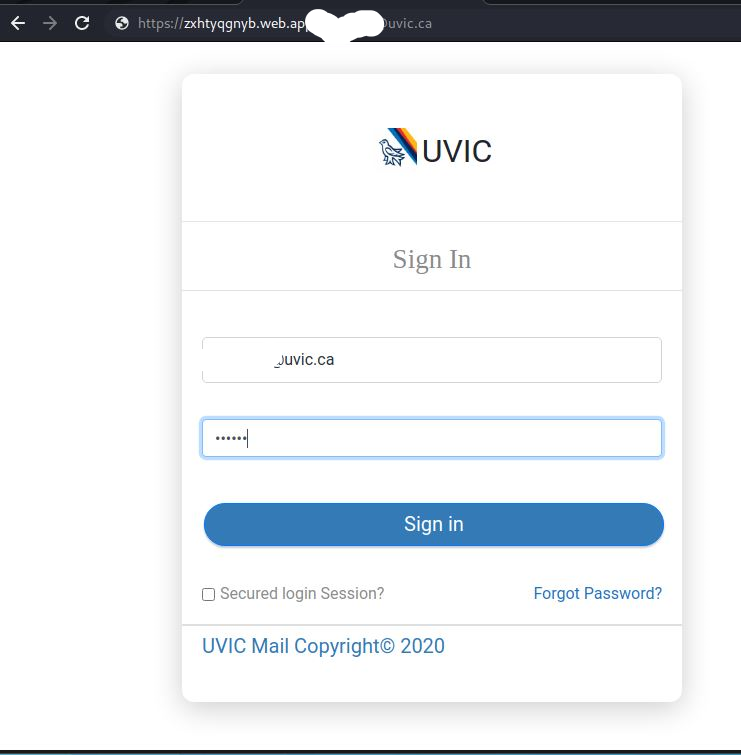
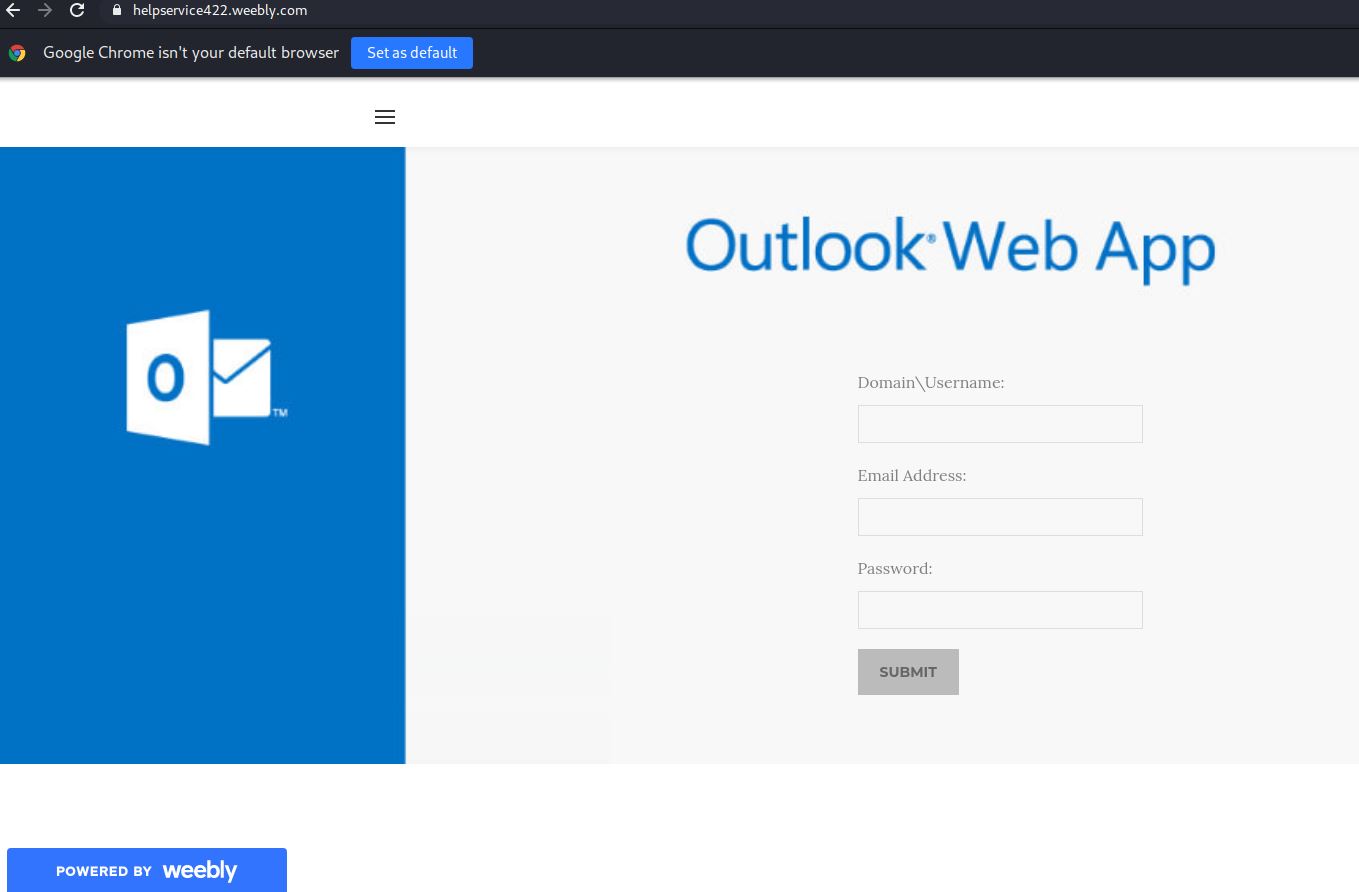
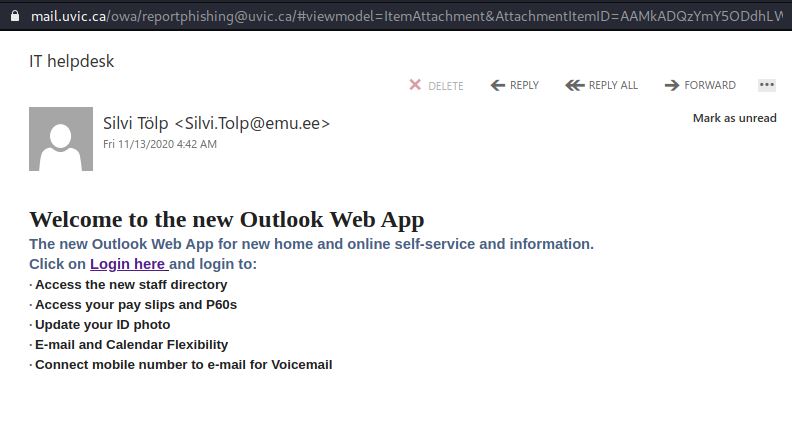
If you proceed to view the PDF or click on the Open Link you will land on a fake Outlook Web App page that you are used to seeing. Yes, it does not have the UVic logo in this case, but we often see that level of duplication. The key in this case again is to look at the Internet Address.
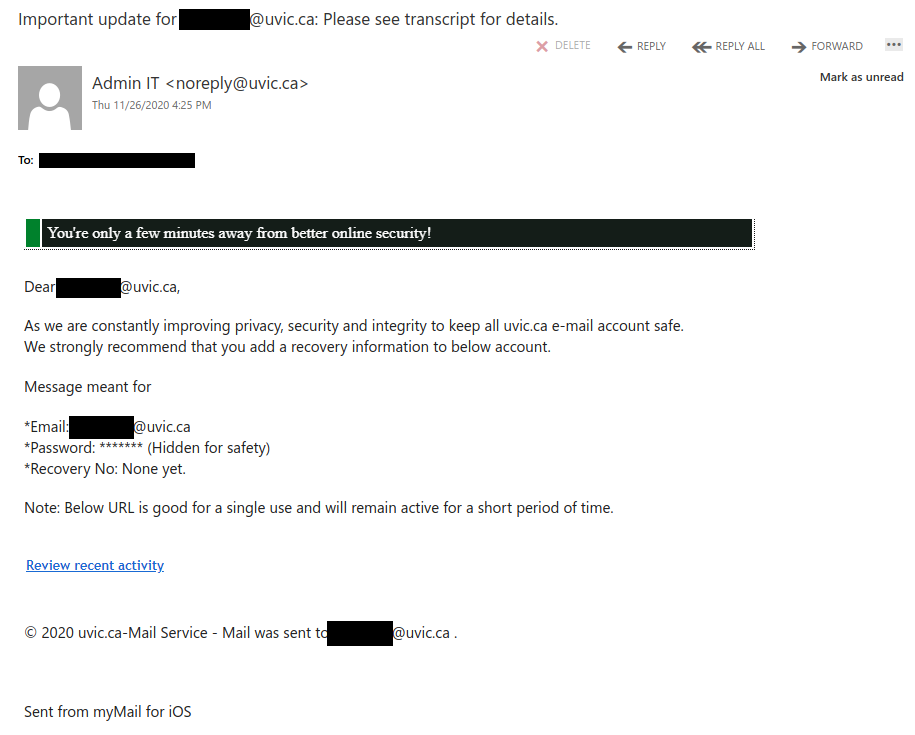
In my sample, I am not revealing the email address but these are also customized with your personal work email in the URL and already populated in the User name text box. If you provide your legitimate password, they will capture it for later use and then conveniently, will just sent you back to the main UVic logon page.
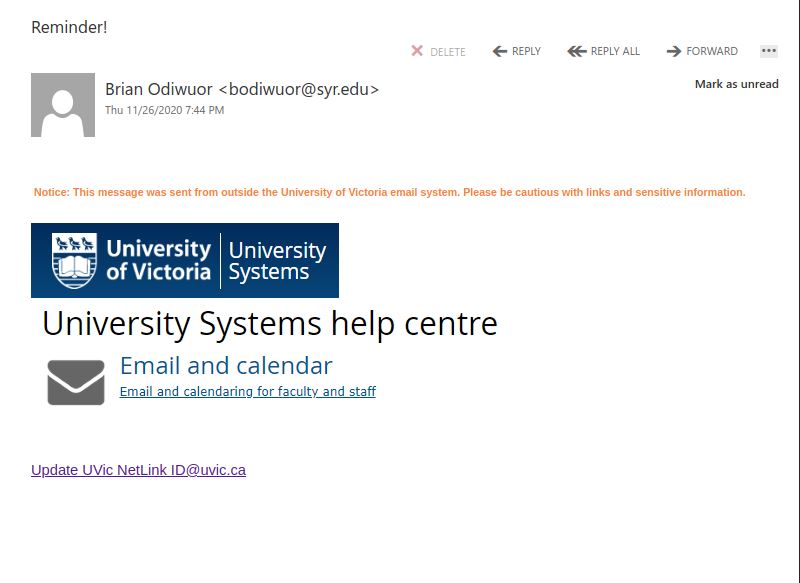
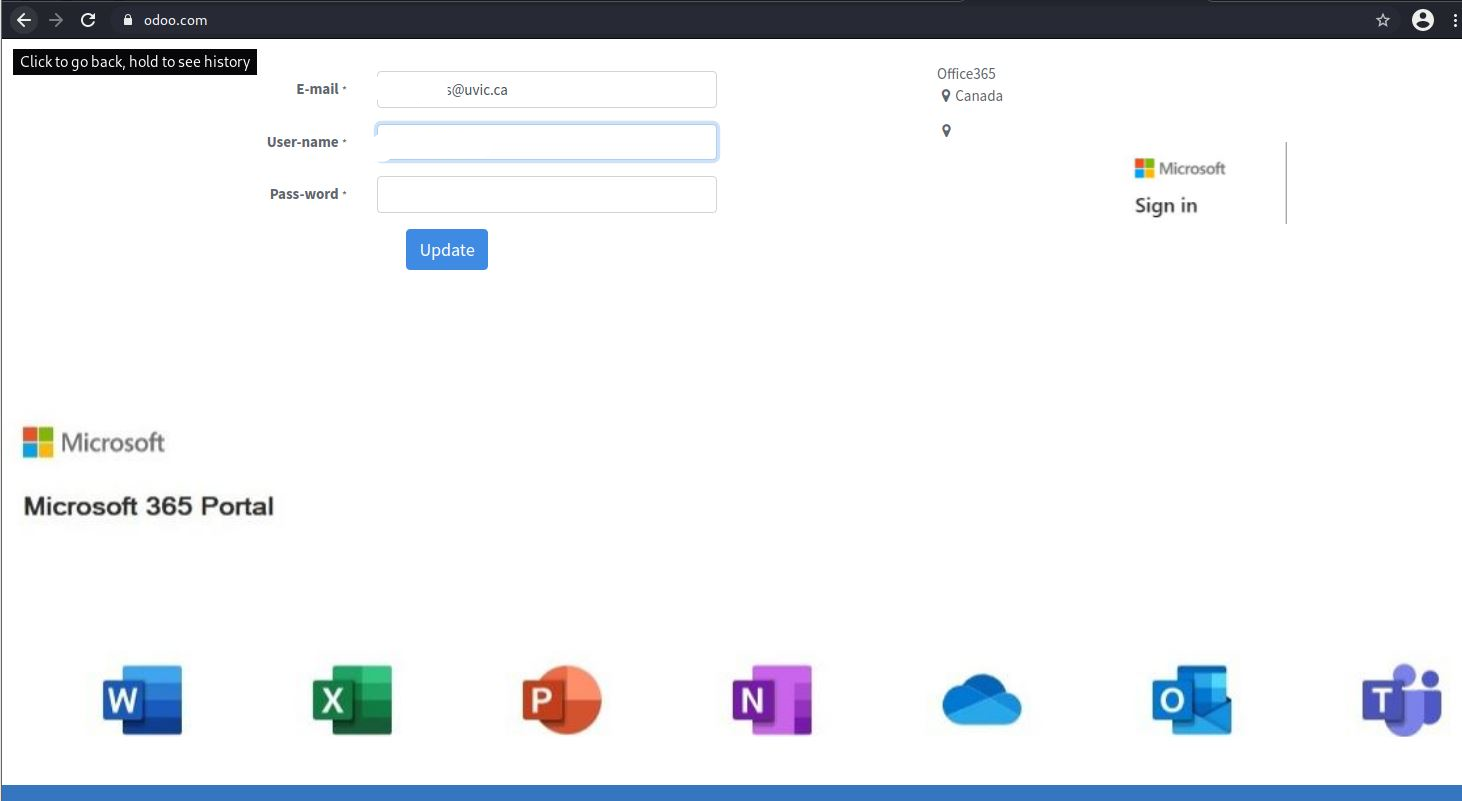



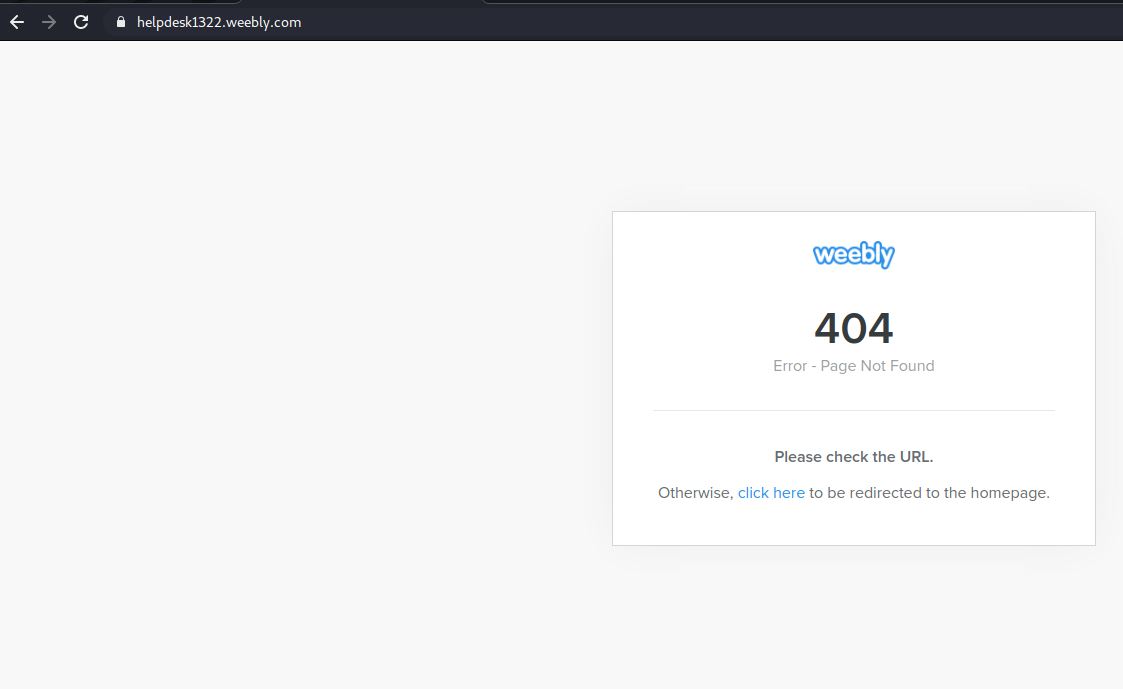
 Further deception here, they have also stolen the official Weebly 404 (page not found) page and are using it to make you think the page is down. They’ve simply assigned it to a new fake Internet Address. Check it out.
Further deception here, they have also stolen the official Weebly 404 (page not found) page and are using it to make you think the page is down. They’ve simply assigned it to a new fake Internet Address. Check it out.