An email account at one of UVic’s suppliers was compromised. The attacker accessed the email account at the supplier and attempted to have staff at UVic send payment to a bank account owned by the attacker via wire transfer.
While the staff person in this particular department did not immediately suspect a fraud attempt, they eventually called the supplier contact and confirmed with the supplier that they did not send those emails. No payment was sent.
Below are redacted screenshots of emails sent by the attacker. If you receive similar emails, contact your supplier using a phone number you already have on file, inform UVic Accounting, and contact the Information Security Office.
This is the initial contact from the attacker:
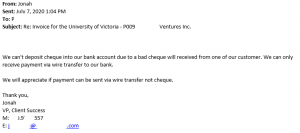
The attacker starts to get demanding here:

And finally, the attacker forgets that improper spelling and grammar is a strong indicator that something is wrong:

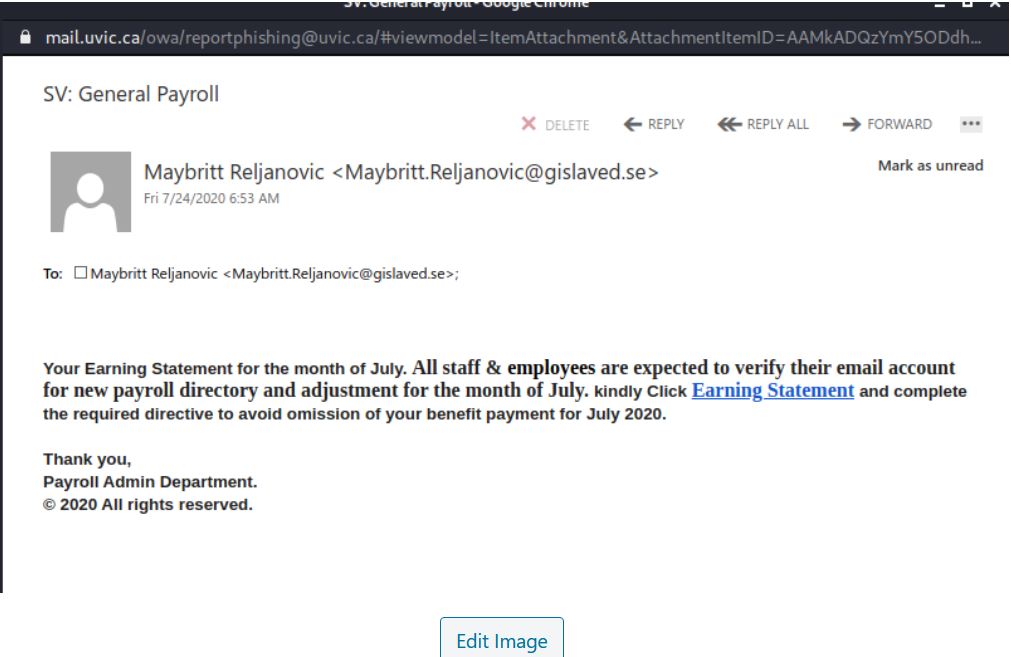

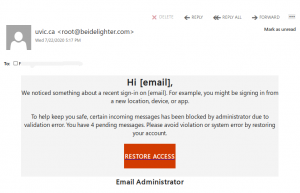
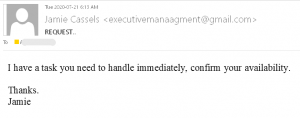 This is a typical start of a gift card scam. We wrote about those back in November:
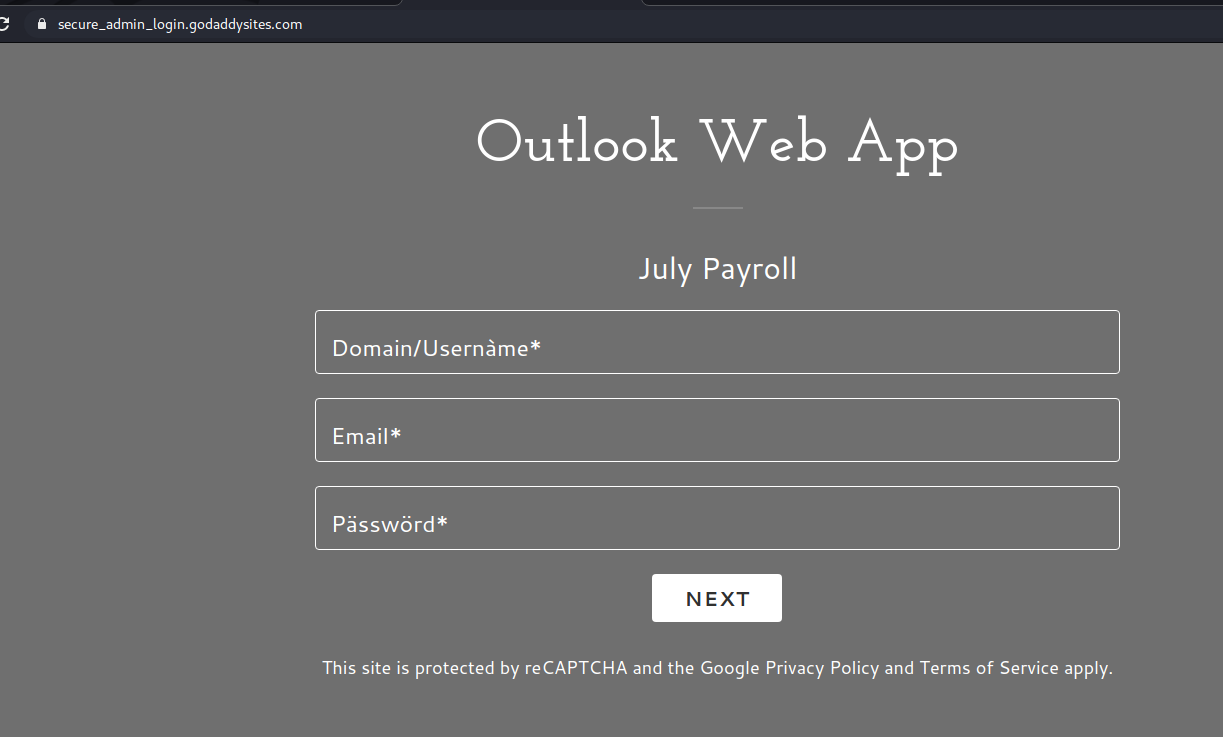
This is a typical start of a gift card scam. We wrote about those back in November: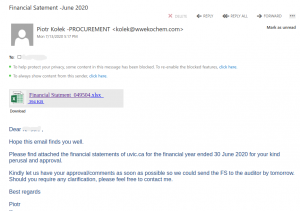 The actual attachment is a html file which redirects the victim to a UVic like OWA page:
The actual attachment is a html file which redirects the victim to a UVic like OWA page: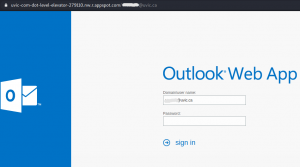 with the intention to steal your credentials. That page is clearly external – look at the address bar in the screenshot.
with the intention to steal your credentials. That page is clearly external – look at the address bar in the screenshot.

