This is not a legitimate UVic email; it is yet another phish that spoofs a UVic email address. Replies actually go to a Hotmail address.
Reminder: legitimate UVic communications will never ask you to send your login information via email.
This is not a legitimate UVic email; it is yet another phish that spoofs a UVic email address. Replies actually go to a Hotmail address.
Reminder: legitimate UVic communications will never ask you to send your login information via email.

This phish tries to persuade the victim that they need to click a link to verify their account. It opens a page that pretends to belong to UVic and steals the credentials of the victim. Do not click on that link!
The email looks like this:
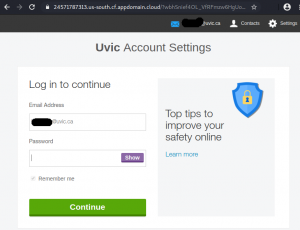
The page pretends to be UVic, but clearly is external (see the address bar)
This email was not sent by UVic; do not click on the link. The sender addresses of Outlook.Team@uvic.ca, Outlook-Web-App.Team@uvic.ca and Outlook.Web.App@uvic.ca have all been spoofed by the phisher to make the email look legitimate.
This is a spear phishing email pretending to be a notification related to UVic OWA. Subject lines are variable but all of them mention account migration. If you clicked on the link or entered your credentials, contact your department’s IT staff or the Computer Help Desk immediately.
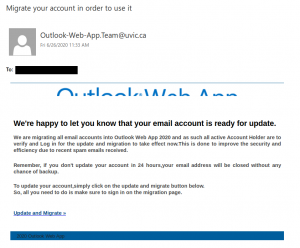
Note the fake trusted sender banner that the phisher added.
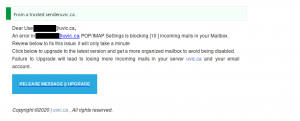
This message asks to click on a link to update your email “for increased security”. Note that we would never ask users to click on a link in order to update their email. Moreover with an obscure explanation like the below. Do not click on the link!
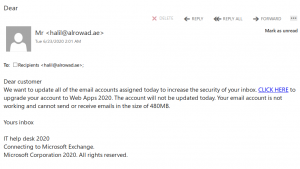
This message pretends to be coming from the helpdesk, while clearly it comes from a random gmail address. Apparently it was designed to target the UVic audience because it mentions the name of the UVic president. Do not click on the link.
Neither the Helpdesk, nor the president will send a document by using google drive.
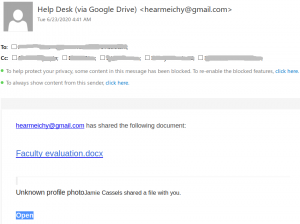
This phish tries to imitate the appearance of a Microsoft Teams notification and uses a randomly-generated spoofed UVic sender address. But if you hover over the links for “uvic.ca Teams”, “docs.uvic.ca” and “View | Approve Document”, you will find that those links go to suspicious URLs that are not associated with UVic’s Microsoft Teams service.
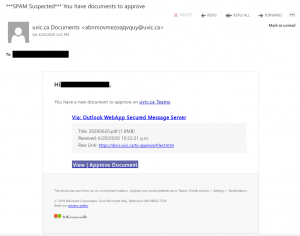
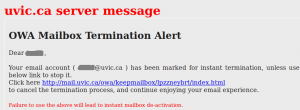
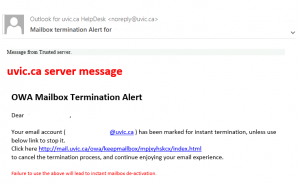
This Phish tries to persuade the victim their email account would be terminated. Clicking on the link opens an OWA page that is quite similar to that of UVic.
Do not click on that link.
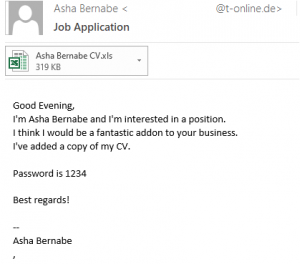
These emails often have varying subject lines ( for example, “Job Application”, “Regading position”, “Regarding job”, “Job Posting”). The also use random names in the body and attached filename. Do not open the attached Excel spreadsheet file, as it is malicious, and definitely is not related to any job posting or application.
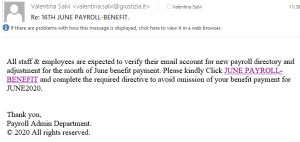
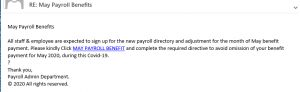
… but it’s June…!
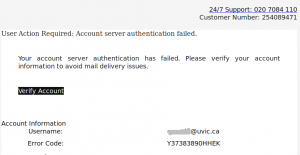
This one tries to fool recipients by saying “Message from Trusted server”. It also tries to appear legitimate by making the URL displayed look like a valid UVic Outook Web Access URL (mail.uvic.ca), but the real link goes to a malicious web page sporting a fake OWA login page.1
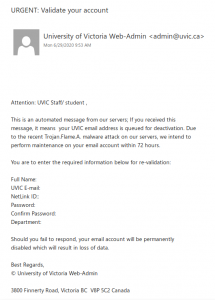
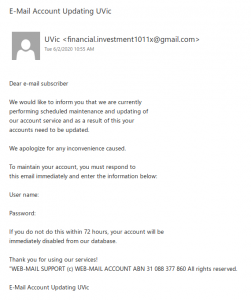
This phish tries to get the recipient to send their credentials by email rather than using a link to a phishing website.
Remember: legitimate UVic communications will never ask you to email your password. Passwords should never be sent via email since it is not a secure method of communicating or storing them.
This email pretends to provide “additional security” to trick the user to enter their credentials. Clearly the sender is not the UVic Helpdesk, it is an external sender.
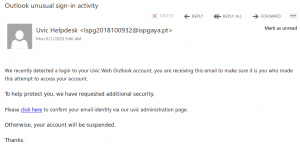
Also the link points to an external site:
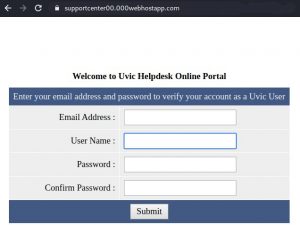
Please report similar phish by using the phish button. Do not click on the links.