This document is designed to serve as the Primary Privacy Appendix for your grant application and your submission to the Information and Privacy Commissioner of Ontario (IPC). It bridges the gap between high-level policy and the “Hard Privacy” engineering provided by the University of Waterloo.
Privacy by Design (PbD) Summary: The Sovereign Dyad
Regulatory Framework: Freedom of Information and Protection of Privacy Act (FIPPA) & Municipal Freedom of Information and Protection of Privacy Act (MFIPPA). Auditing Authority: University of Waterloo Cybersecurity and Privacy Institute (CPI).
1. Principle: Hardware-Level Data Partitioning
Compliance Goal: FIPPA s. 10(1) (Custody or Control) To ensure that a student’s “Private Sanctuary” data does not become an institutional record, the hardware is physically incapable of mixing data streams.
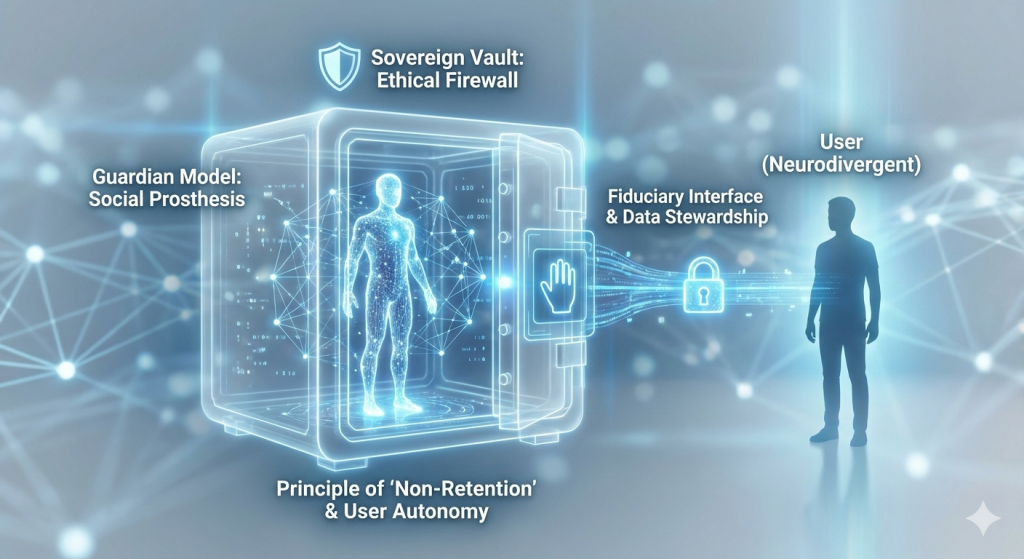
- Waterloo Verified Solution: The “Sanctuary Switch.” A physical analog interrupt that severs power to the microphone and camera. Unlike software “mute” buttons, this creates a verifiable state where no data can be collected, thus it cannot be under the “custody” of the school board.
- The “Vault” Architecture: On-device Edge AI processing ensures that raw biometric and vocal data are never transmitted to the cloud. Only high-level advocacy signals (the “Notice”) are communicated, satisfying the principle of Data Minimization.
2. Principle: Direct Collection & Transparency
Compliance Goal: MFIPPA s. 28(2) (Direct Collection) School boards are often restricted from collecting sensitive personal information indirectly.
- The E-Ink Notice: The chest-mounted e-ink display provides a “Clear and Plain Language” notice of collection at all times. This satisfies the requirement that the individual be informed of the legal authority and purpose of the collection.
- Zero-Knowledge Logs: The system is audited to ensure that logs generated for school advocacy do not contain identifiable personal information from the student’s home life, creating a “clean room” for institutional interactions.
3. Principle: The Resiliency Bypass (Security of Information)
Compliance Goal: MFIPPA s. 3(1) (Reasonable Security Measures) Standard school Wi-Fi is often a “Broken Portal”—it is either insecure or overly restrictive.
- Waterloo Verified Solution: The Dedicated 5G/LTE Node creates an encrypted tunnel directly to the Verified Human Node (Parent/Guardian). This bypasses the school’s network entirely, ensuring that the student’s Cognitive Sovereignty is protected from local network monitoring or “Man-in-the-Middle” attacks.
- Traffic Shaping: Waterloo researchers will implement traffic-shaping protocols to prevent metadata analysis (e.g., timing of packets) from revealing the student’s emotional state to network administrators.
4. PbD Compliance Matrix for School Board IT (YRDSB/OCDSB)
| PbD Requirement | Sovereign Dyad Feature | FIPPA/MFIPPA Satisfaction |
|---|---|---|
| Privacy as Default | On-Device Processing | No data exists in the cloud by default. |
| Embed Privacy into Design | Physical Sanctuary Switch | Privacy is a hardware reality, not a software preference. |
| Full Functionality | Resiliency Bypass Node | Safety is maintained even if school IT fails. |
| End-to-End Security | Zero-Knowledge Encryption | Only the user holds the “Private Key” to their Sanctuary. |
(Google; Sadownik, 2026)
5. Attestation of Sovereignty
By adopting this Waterloo-Verified hardware, the school board acknowledges that the robot is not an institutional tool, but a Secondary Nervous System for the student. Under FIPPA, this distinction is vital: the device is a “personal effect” protected by the same privacy expectations as a student’s diary or a physical medical aid.
Next Step for the User:
Incorporate this document into a “Policy Brief for School Board Trustees” that explains why this hardware-first approach reduces their legal liability compared to traditional tablets or laptops.